Services on Demand
Article
Indicators
Related links
-
 Cited by Google
Cited by Google -
 Similars in Google
Similars in Google
Share
South African Computer Journal
On-line version ISSN 2313-7835
Print version ISSN 1015-7999
SACJ vol.31 n.2 Grahamstown Dec. 2019
http://dx.doi.org/10.18489/sacj.v31i2.788
LETTER TO THE EDITOR
Stefan Gruner
Department of Computer Science, University of Pretoria, South Africa. sg@cs.up.ac.za
Dear editor of SACJ and academic colleagues,
As SACJ is the 'house journal' of the SAICSIT community, and as the annual SAICSIT conference papers are published in the ACM's digital library (ACM-DL, https://dl.acm.org/) since many years, the following bibliometric information might perhaps be interesting for several of your readers.
On the 5th of October 2019 I browsed the ACM-DL's database with the search key 'South Africa' in the 'conference location' field such as to obtain all ACM-DL-listed conference papers which were at any time presented in South Africa. This search yielded (inter alia) all SAICSIT papers. My search was motivated by my desire to know how well these papers are received by the international ICT (informatics and computer science) scholarly community. For this purpose I used the ACM-DL's sorting function to rank the retrieved SAICSIT papers by their citation numbers.
Though I know many cases in which 'Google Scholar' finds more citations per paper than the ACMl-DL -SAICSIT papers included- I did not extend my citation search to the 'Google Scholar' database for these two reasons:
• Convenience: Alas the 'Google Scholar' search mask does not offer any specific 'conference' or 'location' field, such as any 'Google Scholar' search specifically for SAICSIT papers would have become very tedious and time-consuming, whereas I wanted to 'produce' this letter to the editor as swiftly as possible.
• As the ACM-DL is the 'house' of the SAICSIT papers, I was particularly interested in seeing how well these papers are received by their very own 'house community', i.e.: the ACM.
For the sake of convenience (and swift production of this letter to the editor) I also refrained from checking how many of each SAICSIT paper's citations were self-citations (by the same authors) or in-house citations (by authors' close collaborators or colleagues from within the same academic institutions).
In spite of these above-mentioned shortcomings, I believe that my search results are sill interesting enough to justify the writing of this letter. Most of the SAICSIT papers did not receive any ACM-DL-registered citation at all so far - however there was also one paper with the respectable number of #33 ACM-DL-registered citations. In order to make the retrieved results more interesting for your community of readers, I have ranked all positively cited SAICSIT papers according to the following method:

whereby
• r is a paper P's ranking value (the larger the better);
• c > 0 is P's #number of ACM-DL-registered citations (5th of Oct. 2019);
• a := (2019 - y) > 0 is P's current age with y as P's year of publication.
Thus, in case that c(P) = c(P') for two different papers P, P', my ranking gives a higher rank to the younger paper, which is only fair since the older paper would have had 'more time' to 'gather' citations.
In the cases of r(P) = r(P') for two different papers P, P', I sorted them first by numbers of citations (c(P) > c'(P')), then lexicographically (alphabetically) by the words of their titles, (t, t'). All in all, in this manner it should be interesting to see more or less at once glance what have been the most successful research themes of SAICSIT since this conference's papers have been stored in the ACM-DL.
The ranking, so prepared, is shown in the following long enumerated list ('best first'), whereby each list item n for a SAICSIT paper P(n) has the following structure:
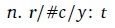
1. 3.33/#20/2013: A case study in the gamification of a university-level games development course
2. 3.00/#33/2008: Predicting technology acceptance and adoption by the elderly: a qualitative study
3. 2.00/#10/2014: Designing Social Media for Community Information Sharing in Rural South Africa
4. 1.50/#18/2007: A comparative study of two usability evaluation methods using a web-based e-learning application
5. 1.45/#16/2008: Scientific computing using virtual high-performance computing: a case study using the Amazon elastic computing cloud
6. 1.43/#10/2012: Symbolic execution of programs with strings
7. 1.42/#17/2007: Modelling the factors that influence mobile phone adoption
8. 1.30/#13/2009: Evaluation criteria for assessing the usability of ERP systems
9. 1.18/#13/2008: Investigating the use of Grounded Theory in information systems research
10. 1.17/#7/2013: Design-based research - the educational technology variant of design research: illustrated by the design of an m-learning environment
11. 0.82/#9/2008: Automatic marking with Sakai
12. 0.78/#7/2010: The evaluation of an adaptive user interface model
13. 0.75/#3/2015: The use ofFacebook by a Community Policing Forum to combat crime
14. 0.71/#5/2012: Audio pacemaker: walking, talking indigenous knowledge
15. 0.70/#7/2009: Glaserian and Straussian grounded theory: similar or completelydifferent?
16. 0.67/#2/2016: A System for a Hand Gesture-Manipulated Virtual Reality Environment
17. 0.67/#2/2016: Domestication of Free Wi-Fi Amongst People Living in Disadvantaged Communities in the Western Cape Province of South Africa
18. 0.67 / #2 / 2016: Validating Mobile Phone Design Guidelines: Focusing on the Elderly in a Developing Country
19. 0.60/ #6/ 2009: Exploring the African Village metaphor for computer user interface icons
20. 0.60/#6/2009: Plagiarising of source code by novice programmers a cry for help?
21. 0.60/#6/2009: Usability evaluation methods: mind the gaps
22. 0.58/#7/2007: Examining the influence of demographic factors on internet users' information privacyconcerns
23. 0.56/#5/2010: Mobile phone adoption: do existing models adequately capture the actual usage ofolder adults?
24. 0.56/#5/2010: Mobile user experience in a M-learning environment
25. 0.55/#6/2008: Towards a taxonomy of network scanning techniques
26. 0.50/#4/2011: Mobile phones and digital divide in East African countries
27. 0.50/#4/2011: Providing media download services in African taxis
28. 0.50/#4/2011: Understanding culturally distant end-users through intermediary-derived personas
29. 0.50/#3/2013: A conceptual framework for delivering cost effective business intelligence solutions as a service
30. 0.50/#3/2013: Crowd computing: a literature review and definition
31. 0.50/#3/2013: First year student performance in a test for computational thinking
32. 0.50/#2/2015: SPLicing TABASCO: Custom-Tailored Software Product Line Variants from Taxonomy-Based Toolkits
33. 0.50/#1/2017: Agile and hackathons: a case study of emergent practices at the FNB codefest
34. 0.50/#1/2017: Challenges to the successful implementation of social media in a South African municipality
35. 0.50/#1/2017: Investigating the effects various compilers have on the electromagnetic signature ofa cryptographic executable
36. 0.50/#1/2017: Morphological cluster induction of Bantu words using a weighted similarity measure
37. 0.45/#5/2008: Agile systems development and stakeholder satisfaction: a South African empirical study
38. 0.45/#5/2008: An application of genetic algorithms to the school timetabling problem
39. 0.44/#4/2010: Critical success factors for information systems outsourcing management: a software development lifecycle view
40. 0.44/#4/2010: Is tilt interaction better than keypad interaction for mobile map-based applications?
41. 0.43/#3/2012: Effects of application type on the choice of interaction modality in IVR systems
42. 0.43/#3/2012: Hardware and software for skateboard trick visualisation on a mobile phone
43. 0.43/#3/2012: Moses: method for selecting senior mobile phones: supporting design & choice for the elderly
44. 0.42/#5/2007: An ontology-based, multi-modal platform for the inclusion of marginalized rural communities into the knowledge society
45. 0.40/#4/2009: A lightweight methodology to improve web accessibility
46. 0.40/#4/2009: The adoption ofopen source software in business models: a Red Hat and IBM case study
47. 0.40/#4/2009: Towards an artificial neural network-based simulator for behavioural evolution in evolutionaryrobotics
48. 0.40/#2/2014: Abstracting and Narrating Novice Programs Using Regular Expressions
49. 0.40/#2/2014: Employee perceptions ofBYOD in South Africa: Employers are turning a blind eye?
50. 0.40/#2/2014: Intrinsic Relations between Data Science, Big Data, Business Analytics and Datafication
51. 0.40/#2/2014: Measuring Method Complexity of the Case Management Modeling and Notation (CMMN)
52. 0.38/#3/2011: A domain-specific language for URDAD based requirements elicitation
53. 0.38/#3/2011: Browser-based software for technology transfer
54. 0.38/#3/2011: Evaluating web conferencing tool effectiveness
55. 0.38/#3/2011: ICT career track awareness amongst ICT graduates
56. 0.36/#4/2008: An analysis of representations for hyper-heuristics for the uncapacitated examination timetabling problem in a genetic programming system
57. 0.36/#4/2008: Guidelines for secure software development
58. 0.36/#4/2008: Usability context analysis for virtual reality training in South African mines
59. 0.33/#4/2007: A probabilistic movement model for shortest path formation in virtual ant-like agents
60. 0.33/#3/2010: A mobile commerce application for rural economy development: a case study for Dwesa
61. 0.33/#3/2010: A study into the use of hyper-heuristics to solve the school timetabling problem
62. 0.33/#3/2010: An informed genetic algorithm for the high school timetabling problem
63. 0.33/#3/2010: Comparing and analyzing the computational complexity ofFCA algorithms
64. 0.33/#3/2010: Design and evaluation of a multimodal interface for in-car communication systems
65. 0.33/#2/2013: Cooperating to buy shoes: an application of picking cycles in directed graphs
66. 0.33/#2/2013: Ease of use and usefulness ofwebinars in an open distance learning environment: an activitytheoryperspective
67. 0.33/#1/2016: Can I Have Your Attention, Please? An Empirical Investigation ofMedia Multitasking during UniversityLectures
68. 0.33/#1/2016: FINCHAN: A Grammar-based Tool for Automatic Comprehension of Financial Instant Messages
69. 0.33/#1/2016: Persuasive Design for Behaviour Change Apps: Issues for Designers
70. 0.30/#3/2009: GPU packet classification using OpenCL: a consideration of viable classification methods
71. 0.29/#2/2012: An exploratory survey of design science research amongst South African computing scholars
72. 0.29/#2/2012: How can usability contribute to user experience?: a study in the domain of e-commerce
73. 0.29/#2/2012: The adoption ofe-Learning in corporate training environments: an activity theorybased overview
74. 0.29/#2/2012: Towards a framework for decision making regarding IT adoption
75. 0.27/#3/2008: An investigation into the implementation of open source software within the SA government: an emerging expansion model
76. 0.27/#3/2008: Investigating the impact of the external environment on strategic information systems planning: a qualitative inquiry
77. 0.27/#3/2008: Planning as model checking: the performance ofProB vs NuSMV
78. 0.25/#3/2007: Assessment ofa framework to compare software development methodologies
79. 0.25/#2/2011: A sketch-based articulated figure animation tool
80. 0.25/#2/2011: Enhancing identification mechanisms in UML class diagrams with meaningful keys
81. 0.25/#2/2011: Issues of adoption: have e-learning management systems fulfilled their potential in developing countries?
82. 0.25/#2/2011: Successful ICT service delivery: enablers, inhibitors and hygiene factors: a service provider perspective
83. 0.25/#2/2011: The influence of gender and internet experience on the acceptability of smell as interaction modality
84. 0.25/#2/2011: Towards a framework for the adoption of business intelligence in public sector organisations: the case ofSouth Africa
85. 0.25/#1/2015: CAPP: A C++Aspect-Oriented Based Framework for Parallel Programming with OpenCL
86. 0.25/#1/2015: ContextualizingBYOD in SMEs in developing countries
87. 0.25/#1/2015: Contributor Motivation in Online Knowledge Sharing Communities with Reputation Management Systems
88. 0.25/#1/2015: Developing a Conceptual Model for Facilitating the Issuing of Digital Badges in a Resource Constrained Environment
89. 0.25/#1/2015: On the prioritization of data quality challenges in e-health systems in South Africa
90. 0.25/#1/2015: SpotMal: A hybrid malware detection framework with privacy protection for BYOD
91. 0.25/#1/2015: The User Experience Landscape of South Africa
92. 0.25/#1/2015: Toward a framework for ontologymodularity
93. 0.25/#1/2015: Use of the Alice visual environment in teaching and learning object-oriented programming
94. 0.25/#1/2015: Using Business Intelligence to Support Strategic Sustainability Information Management
95. 0.22/#2/2010: Deriving a digraph isomorphism for digraph compliance measurement
96. 0.22/#2/2010: Determining requirements within an indigenous knowledge system of African rural communities
97. 0.22/#2/2010: Investigating the feasibility factors of synthetic sign language visualization methods on mobile phones
98. 0.22/#2/2010: Parallel packet classification using GPU co-processors
99. 0.22/#2/2010: The complementary role of two evaluation methods in the usability and accessibility evaluation ofa non-standard system
100. 0.20/#2/2009: A framework and methodology for knowledge management system implementation
101. 0.20/#2/2009: An analysis of the international discourse about women in information technology
102. 0.20/#2/2009: An evaluation of techniques for image searching and browsing on mobile devices
103. 0.20/#2/2009: The revised developmental approach to the uncapacitated examination time-tabling problem
104. 0.20/#1/2014: An Ant-based Mobile Agent Approach to Resource Discovery in Grid Computing
105. 0.20/#1/2014: Applying design-based research for developing virtual reality training in the South African mining industry
106. 0.20/#1/2014: Mobile-Health Tool Use and Community Health Worker Performance in the Kenyan Context: ATask-TechnologyFit Perspective
107. 0.20/#1/2014: The Effects of Mother Tongue and Text Difficulty on Gaze Behaviour while Reading Afrikaans Text
108. 0.18/#2/2008: A model for eliciting user requirements specific to South African rural areas
109. 0.18/#2/2008: Comparison of the effects of professional and pedagogical program development environments on novice programmers
110. 0.18/#2/2008: Using adaptive interfaces to improve mobile map-based visualisation
111. 0.17/#2/2007: A model to assess the benefit value of knowledge management in an IT service provider environment
112. 0.17/#2/2007: Agile software development: a contemporary philosophical perspective
113. 0.17/#2/2007: Constraint-based conversion of fiction text to a time-based graphical representation
114. 0.17/#2/2007: Criteria used in selecting effective requirements elicitation procedures
115. 0.17/#1/2013: A new mapping function to improve the accuracy of a video-based eye tracker
116. 0.17/#1/2013: Categorizing the provision of mobile centric information access and interaction for higher educational institutions
117. 0.17/#1/2013: Effectiveness with EEGBCIs: exposure to traditional input methods as a factor of performance
118. 0.17/#1/2013: Evaluating the acceleration of typical scientific problems on the GPU
119. 0.17/#1/2013: Evaluating performance of long short-term memory recurrent neural networks on intrusion detection data
120. 0.17/#1/2013: Numerical verification of bidirectional reflectance distribution functions for physical plausibility
121. 0.17/#1/2013: Personally identifiable information leakage through online social networks
122. 0.17/#1/2013: The usability of collaborative tools: application to business process modelling
123. 0.17/#1/2013: Using machine learning to predict the driving context whilst driving
124. 0.14/#1/2012: A longitudinal analysis of ICT project success
125. 0.14/#1/2012: ABox abduction in ALC using a DL tableau
126. 0.14/#1/2012: Are mobile in-car communication systems feasible? a usability study
127. 0.14/#1/2012: Automated coverage calculation and test case generation
128. 0.14/#1/2012: CaptureFoundry: a GPU accelerated packet capture analysis tool
129. 0.14/#1/2012: Changing career choice factors as the economic environment changes
130. 0.14/#1/2012: Internet use and expatriate adjustment: understanding the degree of isolation experienced in kingdom ofSaudi Arabia
131. 0.14/#1/2012: Monte-Carlo tree search parallelisation for computer go
132. 0.14/#1/2012: Performance assessment of dead-zone single keyword pattern matching
133. 0.14/ #1 / 2012: What is software architecture?
134. 0.13/#1/2011: Adoption ofGreen IS in South Africa: an exploratorystudy
135. 0.13/#1/2011: Contextual factors influencing strategic information systems plan implementation
136. 0.13/#1/2011: Day labour mobile electronic data capture and browsing system
137. 0.13/#1/2011: Empirical comparison of four classifier fusion strategies for positive-versus-negative ensembles
138. 0.13/#1/2011: Proposed stages of a rural ICT comprehensive evaluation framework in ICT for rural development projects
139. 0.13/#1/2011: The accreditation of ICT degree programs in South Africa
140. 0.13/#1/2011: The impact of sensor fusion on tilt interaction in a mobile map-based application
141. 0.13/#1/2011: Using information visualization to support web service discovery
142. 0.13/#1/2011: Using mass video notification methods to assist deaf people
143. 0.13/#1/2011: Using N-grams to identify mathematical topics in MXit lingo
144. 0.11/#1/2010: Afour-way frameworkfor validating a specification
145. 0.11/#1/2010: A South African perspective of the international discourse about women in information technology
146. 0.11/#1/2010: A virtual VLSI architecture for computer hardware evolution
147. 0.11/#1/2010: An intelligent frameworkfor mobile devices
148. 0.11/#1/2010: A-POInter: an adaptive mobile tourist guide
149. 0.11/#1/2010: Integrated security framework for low cost RFID tags
150. 0.11/#1/2010: IT moderation going green
151. 0.11/#1/2010: Motivation and learning preferences of information technology learners in South African secondaryschools
152. 0.11/#1/2010: Ontology goes postmodern in ICT
153. 0.11/#1/2010: Panopticon: a scalable monitoring system
154. 0.11/#1/2010: PH2: an hadoop-based framework for mining structural properties from the PDB database
155. 0.11/#1/2010: Quality metrics for mashups
156. 0.11/#1/2010: Sweetening the medicine: educating users about information security by means ofgame play
157. 0.11/#1/2010: The impact of accents on automatic recognition of South African English speech: a preliminaryinvestigation
158. 0.11/#1/2010: Toward a service creation framework: a case of intelligent semantic services
159. 0.10/#1/2009: Ahybrid neural network and Minimaxalgorithm for zero-sum games
160. 0.09/#1/2008: Contemplating systematic software reuse in a project-centric company
161. 0.09/#1/2008: Designing technology for young children: what we can learn from theories of cognitive development
162. 0.09/#1/2008: Development and implementation of an institutional repository within a science, engineering and technology (SET) environment
163. 0.09/#1/2008: Do online buying behaviour and attitudes to web personalization vary by age group?
164. 0.09/#1/2008: Java Micro Edition and Adobe Flash Lite for arcade-style mobile phone game development: a comparative study
165. 0.09/#1/2008: Maintaining customer profiles in an e-commerce environment
166. 0.09/#1/2008: Usability evaluation ofthe South African National Accessibility Portal interactive voice response system
167. 0.09/#1/2008: Using mobile preference-based searching to improve tourism decision support
168. 0.08/#1/2007: Supporting CS1 with a program beacon recognition tool
169. 0.08/#1/2007: Generic process model structures: towards a standard notation for abstract representations
170. 0.08/#1/2007: KernTune: self-tuning Linux kernel performance using support vector machines
Just by chance this list of positively cited papers currently has the 'round' number of 170 elements (if I have not forgotten anything from what I retrieved from the ACM-DL).
For further illustration I plotted each of these 170 paper's two-dimensional (r, c) value in Figure 1: some 'clustering' is clearly visible. The different colours in Figure 1 represent the diferent event years (2007-2017; created with the MS PowerPoint software package).
It is up to your readers to infer their own conclusions (e.g.: what are 'attractive' research topics?) by their own methods (e.g.: 'Wordle' word frequency analysis) from the information which I have provided in this letter as a service to the SACJ/SAICSIT community. Most concerning is perhaps what is invisible in this letter, namely the large number of SAICSIT papers for which the ACM-DL says: "0 citations" -which includes all SAICSIT conferences before the year 2007, and so far also SAICSIT'2018- in spite of the ACM-DL's global visibility and accessability (though, as mentioned above, more citations are likely to be found with help of other tools such as 'Google Scholar').
With kind regards: Stefan Gruner














