Servicios Personalizados
Articulo
Indicadores
Links relacionados
-
 Citado por Google
Citado por Google -
 Similares en Google
Similares en Google
Compartir
South African Journal of Libraries and Information Science
versión On-line ISSN 2304-8263
versión impresa ISSN 0256-8861
SAJLIS vol.89 no.1 Pretoria 2023
http://dx.doi.org/10.7553/89-1-2113
Aderinola Ololade DunmadeI; Adeyinka TellaII; Uloma Doris OnuohaIII
IDeputy Director of Computer Services and Information Technology at the University of Ilorin, Nigeria. derin_d@unilorin.edu.ng ORCID: 0000-0002-7745-0494
IIProfessor of Library and Information Science at the University of Ilorin, Nigeria and Research Fellow at the University of South Africa. tella.a@unilorin.edu.ng ORCID: 0000-0002- 5382- 4471
IIIProfessor of Library and Information Science at the University of Ilorin, Nigeria. onuoha.uloma@adelekeuniversity.edu.ng ORCID: 0000-0003-0830-0035
ABSTRACT
This study examined cyberethics awareness and implications on library and information science(LIS) educators in selected universities in South-west Nigeria. A quantitative method was adopted along with a descriptive survey design; while 35 LIS educators drew through total enumeration from two universities in South-west Nigeria to represent the sample for the study. A questionnaire adapted from the previously related validated scales was used for the data collection. The research questions were developed and answered. The findings revealed that the LIS educators were aware of cyberethical issues, and the awareness is also very high. The LIS educators regularly participated in training on cyber technology, internet policy issues, cyber security and cyberethics. The LIS educators were very familiar with various types of cyberethical issues including intellectual property, fair use, illegal downloads and wrong copies of files and text, respecting others' opinions, and privacy concerns in the cyber environment. Based on the findings, the study recommends that the deliberate adoption of cyberethics as a stand-alone distinct course that will be part of the curriculum of LIS should be encouraged to further enhance the awareness of students.
Keywords: cyberethics, cyberethical behaviour, cyber security, cyberspace, LIS educators, Nigeria
1 Introduction
Information and communications technologies (ICTs) are exploding. After exposing both adults and children to the usage of electronic devices to facilitate processes and procedures in every part of life, ICTs and many of their fundamental components have brought up previously unheard-of issues. The potential and benefits of ICTs cannot be understated. For instance, the growth of ICTs has a significant potential to transform economies and societies in several ways, including by lowering information and transaction costs, developing new collaborative models to boost worker efficiency, encouraging innovation, and enhancing access to basic services and education. According to Arellano and Cámara (2017), innovation appears to be present in every aspect of consumer life, as well as the processes used to produce goods and services in business and the public sector. In education, ICTs have made education more interactive and have improved the teaching and learning process offered in educational institutions (Naaj & Nachouki 2021).
According to Mata et al. (2020), using the Internet and ICTs for interpersonal contact via various social media platforms and email systems offers a variety of chances and benefits. They claimed that the university community has benefited greatly from the advantages brought about by the use of this technology. The implementation of academic activities has undergone a paradigm shift as a result of the new technologies, including the establishment of a more effective and inclusive teaching-learning process, the design and development of research projects, and the production of academic articles. The expansion of various negative elements has, however, accompanied these good advances. These include plagiarism, fraud, academic dishonesty, and other shady activities. The pandemic of unethical Internet use today undermines the basic foundation of the fabric of the academic setting. This emphasises how crucial it is to give nearly every individual and professional in society, especially the LIS educators, sufficient cyberethics training.
Every person has the intrinsic impulse to choose from a predetermined list of behaviours when presented with a certain situation. These decisions, which are referred to as an individual's implicit ethos and are founded on that person's sense of right and wrong as a result of internal and external forces dictating that person's actions, are referred to as ethics. According to Ramluckan et al. (2020), cyberethics is the study of ethical concerns in environments with Internet access. As a result of the development of ICTs, which enable remote connection with others in real-time, cyberethics is described as involvement in an online environment, during interaction with other people. Cyberethics, according to Petrie-Wyman et al. (2021; 2022), is the study and analysis of moral principles and conundrums as well as a look at the laws, norms, and regulations that control behaviour in cyberspace and the cyber realm. Cyberethics education could reduce the perceived cognitive distance (PCD), the justification culture that rationalises immoral behaviour online, the lack of individual and group accountability, and the absence of comprehensive regulations controlling data curation in the cyber realm.
According to Dunmade et al. (2019), moral behaviour in cyberspace has to be monitored. Vereccio (2016) identified a range of computer ethics problems, including child pornography, fraud, digital libel, identity theft, and hacking. Others include spamming, copyright and software theft, digital plagiarising, espionage, cybersex, cyber-squatting, domain-squatting, financial theft, cyberstalking, cyberbullying, and cyber-squatting. All ICT users have a moral and ethical obligation to make sure that their online behaviour does not put other people's lives in danger.
As mentioned earlier, the LIS educators are among the citizens and professionals who need instruction on cyberethics. Teachers in LIS have a unique perspective on higher education. They educate information professionals who will eventually hold jobs distributing information and knowledge to those who use libraries to meet their informational needs. This has a direct multiplying impact since grounded students will impart these qualities when they carry out their everyday work tasks as professionals. Therefore, it is important to provide a suitable level of awareness for these people. According to Adetimirin (2017), LIS doctorate students should be cognisant of cyberethics while they access online resources for information, such as journal websites, databases, and other sources.
Students need to be aware of the proper citation practices when using these resources to prevent plagiarising work or breaching other people's intellectual property. They can only use the information resources lawfully and morally when they are aware of and have the necessary cyberethics knowledge. According to Rahman et al. (2020), students in the present day must learn about the dangers of engaging in online activity. Although there are obstacles to this awareness, teachers can use the significance of a cybersecurity curriculum to make sure that students are well-versed in this field.
As mentors of the next generation of people who want to work in information services, LIS educators are in a unique position. They employ ICTs for a wide array of tasks in education and research. Therefore, educators who are aware of ethical use in online activities will pass this knowledge forward to and affect their students either explicitly or implicitly. The LIS educators must be knowledgeable about cyberethics since they will be better equipped to educate and inform students about the risks associated with plagiarism and other cyber-unethical behaviour. An instructor will lack the necessary understanding if they haven't had enough exposure to the nature of cyberethical issues.
ICTs are used by LIS educators to access the information they need for their research and other academic tasks. Rules govern how ICTs should be used, and users' knowledge and understanding of these guidelines will support their adherence to those guidelines. The LIS educators serve as information custodians and gatekeepers who are responsible for gathering, organising, and distributing information to users while also upholding ICT usage ethics. Their awareness and understanding of the ethics governing the use of ICTs, often known as cyberethics, will determine how closely they adhere to those ethics. Going by the anecdotal records of accessible linked studies, it is unfortunate that the knowledge of the LIS educators at Nigerian universities concerning cyberethics has not been extensively researched. It is noted that the majority of the studies were conducted outside Nigeria and Africa. The related studies from Nigeria have concentrated on awareness of cyberethics by doctoral students and not LIS educators (Adetimirin, 2017), cyber behaviour of university students (Aderibigbe & Owolabi, 2020), awareness and knowledge of cyberethics by the pre-service teachers, and cyberethics awareness and knowledge by the pre-service teachers (Milton et al., 2021). The study's authors now believe it is crucial to carry out a similar study with a focus on LIS educators in Nigeria to collect data on cyberethics from the population of Nigerian LIS educators. As a result, this study looked at the perceptions of cyberethics and their effects on librarians and information scientists in a few universities in South-west Nigeria.
2 Objectives of the study
The specific objectives are to:
• examine the awareness of LIS educators on cyberethics in selected universities in South-west Nigeria.
• ascertain the participation of LIS educators in South-west Nigeria in the contemporary online training and awareness programmes on cyberethics.
• Determine the extent of familiarity with cyberethical issues among LIS educators in selected universities in South-west Nigeria.
3 Literatu rereview
The core of cyberethics is derived from the study of ethics, which is a subfield of philosophy. As a result, philosophy has a methodology for examining ethical questions as well. Cyberethics is a subfield of applied ethics that studies moral, legal, and social problems that arise when computers and ICTs are used together (Dunmade,2022). Cyberethics is the study of ethical issues and moral quandaries caused by the development of digital technology and global virtual worlds. Thus, problems over privacy, property, security, accuracy, accessibility, and censorship emerged with the advent of the Internet. When a person is in an online environment and has the chance to connect with others, many motivations and mental processes are described in cyberethics (Blanchette & Ellington, 2017; Liywalii, 2020). It is the philosophical study of computer usage ethics that includes user behaviour and how that behaviour affects people and society.
Thus, the combination of the aforementioned concerns relating to cyber technology is cyberethics. A group of new media-based digital technologies, such as virtual reality, social networks, and multimedia, as well as mobile computing, are collectively referred to as "cybertechnology."(Dunmade, 2022) From standalone computers to connected or networked computing and communication technologies, it includes a broad spectrum of computing and communication equipment. It examines social policies and legislation that have been created in reaction to problems brought on by the development and usage of cybertechnology, with a focus on the effects of cybertechnology on social, legal, and moral systems. Cyberethics is all about the principles that govern the moral application of technology, and understanding it necessitates awareness. In the social sciences, awareness is a well-established and precisely defined concept. Kim and Park's (2014) definition of cyberethics awareness served as a foundation for this research. Enlightenment is created through a variety of techniques that are available and well-researched. The techniques include attending seminars and workshops, as well as pedagogical and non-pedagogical awareness-creation techniques and ICT-based techniques. Therefore, the authors of this study aimed to examine the effects of cyberethics awareness on LIS educators in Nigeria.
4 Theoretical framework
Immanuel Kant's deontological theory of ethics, informed this work (1774-1804). The term "deontology" comes from the Greek word "deos," which means "obligation" or "feeling of commitment." The foundation of deontological ethics theory is the idea that behaviour results from a person upholding a moral obligation or following moral laws. It implied that genuine actions are those that result from duty and are consistent with moral codes because it was presupposed that people are reasonable, trustworthy, and responsible people who have the desire to fulfil their duties and give this the utmost importance from their point of view without external coercion (Koçyigit&Karadag, 2016; Osterberg, 2019). According to deontology, individuals should fulfil their commitments and duties when making decisions, which implies that they will honour their duties to other people or society because doing so is regarded as morally right (Raymond 2020). Deontological ethics aims to focus on the inherent rightness or wrongness of an action or activity rather than the rightness or wrongfulness of the action's consequences (consequentialism) or the character traits or nature of the person acting (character or virtue ethics).
This theory is pertinent to this study because it relates how individuals regard the use of ICTs, which is a duty and obligation that should not be taken lightly, to how aware the LIS instructors are of issues related to computer ethics. The ability to avoid misusing or abusing resources or people in a cyber environment depends on one's awareness, knowledge, moral background, and behaviour. Also upheld are moral requirements to treat others with respect. It will also be avoided engaging in undesirable behaviours including hacking, computer fraud, cyberstalking, plagiarism, revenge pornography, cybercrimes, and cybersecurity breaches. Having said that, the degree to which people follow the deontological theory will determine the degree of adherence to cyberethics.
5 Related studies
Studies on cyberethics, cyberethical behaviour, cyber security, and similar topics are offered both internationally and locally. Through the introduction of a collaborative cyberethics leadership paradigm and the development of a cyber ethics training intervention dubbed the Cyberethics Education Accelerator, Petrie-Wyman et al. (2022) addressed some of the cyber problems encountered in the United States. According to the study, neither teachers nor students were ready for the distance learning environment. It was difficult to share knowledge between higher education institutions, businesses, and schools since underlying frameworks for cooperative collaborations were typically missing.
During the COVID-19 pandemic in the United Arab Emirates (UAE), Naaj and Nachouki (2021) concentrated on perceptions of cyberethics among university undergraduate students. The study examined the relationship between many characteristics and awareness of cyberethics, including gender, education level, grades or Cumulative Grade Point Average (CGPA), and major. The study used an online survey to gauge the level of cyberethics awareness among university students at a university in the United Arab Emirates, which included 322 undergraduates majoring in information technology and other fields. The findings indicated that respondents were generally knowledgeable of cyberethics. It was discovered that awareness of cyberethics was specifically influenced by gender and education level, but major and grades have no statistically significant influence.
Milton et al. (2021) investigated the understanding of cyberethics that pre-service teachers have in three different European nations. Pre-service teachers from Malta, Norway, and Spain provided 1,131 replies to the study's online survey, which was completed. The aspects of cyberethics covered in this study were responsible online behaviour, privacy protection, copyright observance, getting friends' permission before uploading photos or videos to social media sites, and taking into account their professional identity as future teachers when posting online. The results showed that pre-service teachers in Norway and Malta reported better levels of knowledge and awareness than their Spanish counterparts, while pre-service teachers in Spain reported approximately similar levels of competence in implementing copyright and respecting privacy standards.
Norway and Malta were the two countries with the highest percentages of participants who said they had always thought about how putting material online may affect their professional teaching career. The majority of pre-service teachers who said they rarely or never considered this impact on their teaching career were from Spain. The study found that there is a lack of understanding of cyberethical behaviour, which involves acting honourably in a more public and professional setting online. The results also showed the importance of emphasising cyberethics knowledge for pre-service teachers during Initial Teacher Education (ITE), particularly during a time when their professional identities are being formed. There was a noticeable discrepancy between the declared practices of some pre-service teachers and the recognised knowledge or competence concerning cyberethics knowledge in this study. The study suggested that all ITE programmes should integrate digital competence and cyberethics components in their curricula based on its findings. To meet the challenges of becoming teachers in the twenty-first century, pre-service teachers would be able to develop new professional and technological capabilities.
Aderibigbe (2021) gave a review of the empirical literature on cyberethics difficulties in a classroom setting, with a focus on young people's online behaviour. While the institutional and societal urge for informational inclusion and knowledge development is aided by digital media, users' ethical practices and behaviours have called into question whether they are aware of the consequences of ethical infractions in cyberspace. Utilising technology could offer important theoretical paradigms for comprehending how information technology-driven worldwide variations in digital media acceptance and diffusion can occur. The study examined the literature on the development of cyber technology ethics, personal traits, awareness levels, impediments to students' cyberethics behaviour, and the crucial role policy plays in bolstering or supporting ethical behaviour. This paper provided current information on awareness of Cyberethics, teaching and research on information ethics and related domains.
Aderibigbe and Owolabi (2020) investigated the cyberethical conduct of undergraduates at the Federal University of Agriculture in Abeokuta, Nigeria, and the University of Zululand, South Africa. The study utilises a triangulation strategy between quantitative and qualitative studies and adapts the Theory of Planned Behavior of Ajzen (1991; 2011). Data gathering tools or instruments included an interview guide and a questionnaire. Based on information gathered from 380 students using the proportionate random sample technique, it can be seen that students in South Africa and Nigeria have more advanced knowledge of cyber technology and have been using it for around seven years, respectively. In the two colleges, students' attitudes regarding cyberethical issues are generally typical.
The subjective norms among students regarding cyberethical issues vary significantly between South Africa and Nigeria, and this suggests that students are being controlled by their friends, peers, and the academic environment and administration. Additionally, there is little understanding and awareness of cyberethical issues among students. The results of this study also revealed a substantial difference between South Africa and Nigeria in the prevalence of a few specific cyberethical behaviours, with Nigeria showing a greater degree of prevalence. The results demonstrated that subjective norms perceived behavioural control, and attitudes toward, perceptions of, and understanding of cyberethical concerns are all significant factors that may affect real cyber conduct among students in South Africa and Nigeria.
A study on the awareness of 157 university postgraduate students in Ghana was conducted by Paapa and Boakye in 2017. The study's approach was quantitative; data was gathered through descriptive research using a questionnaire. The results showed that most students had sufficient knowledge of information ethics and had shown conformity with information ethics standards. As the units of analysis, the writers explored information ethics concerning the idea of plagiarism, computer ethics, legislation against indiscriminate photocopying, and fair use. Additionally, there is broad agreement regarding what constitutes ethical or unethical behaviour. Students have been found to engage in a variety of information ethics violations even when they were aware that they were doing so.
Most students admitted that having access to the Internet, being afraid of failing, having access to electronic databases, and wanting to do well on tests were some of the things that drove them to violate information ethics. The study suggested making information ethics a stand-alone course to raise awareness of the topic. Similar to this, 65 PhD students in LIS from two Nigerian institutions participated in an Adetimirin (2017) study on awareness and knowledge of cyberethics. A questionnaire was employed as the data collection tool in a descriptive survey design. The results showed that Nigeria has a high level of cyberethics awareness and knowledge. The survey also revealed the necessity of providing cyberethics education to encourage adherence to cyberethics among the LIS doctoral students in Nigerian universities.
While instances of cyberethical misbehaviour are quite frequent, it is evident from the deluge of reviewed literature that studies into this area is typically lacking in Africa and Nigeria in particular. Similar to this, few pieces of research, if any, appear to concentrate especially on LIS educators' knowledge and experience with cyberethical behaviour. Therefore, this study examined the awareness of cyberethics and its consequences for librarians and information scientists at two South-west Nigerian universities.
6 Methodology
A quantitative research approach was adopted along with a descriptive survey design. The population was the LIS educators in South-west Nigerian universities. These LIS educators are full-time lecturers of the Department of Library and Information Science, as well as Academic librarians in the University library who render teaching services on an adjunct basis. It also included academic librarians who taught on a part-time basis.
The sample for the study was taken from two universities in two states of South-west Nigeria. The total enumeration method was used to involve the entire 35 LIS educators in the two universities. A questionnaire developed by the researcher was used as an instrument for data collection. The items in the questionnaire were adapted from Supavai (2014) Computer and Internet Activity Questionnaire (CAIQ) on moral reasoning in an online environment, the Privacy, Accuracy, Property and Accessibility (PAPA) Framework propounded by Mason (1984), and The Ten Commandments of Computer Ethics" by the Computer Ethics Institute. The questionnaire had a Cronbach Alpha value of 0.764, which indicated that the questionnaire has an acceptable value of internal reliability.
Regarding the procedure of data administration, thirty-five (35) copies of questionnaires were distributed to the respondents; that is, twenty copies (20) to Adeleke University (AU) and 15 to Ladoke Akintola University (LAUTECH). Out of the 35 copies of questionnaires administered, 21 copies were returned and valid for data analysis which gave a 60% return rate. The instrument adopted in this study was divided into three sections.
The first section comprised of items on demographic characteristics which included institutional affiliations, gender, age, level of education and rank. The second section featured items on the extent of participation and engagement of LIS educators in contemporary online training and awareness programmes on cyberethics. Data was collected based on a 5-point Likert Scale, ranging from 1 (Never), 2 (Infrequently), 3 (Sometimes), 4 (Regularly) and 5 (Extremely Frequently). The third section comprised statements focusing on respondents' awareness of computer ethics bearing in mind both the PAPA Framework propounded by Mason (1984) and the Computer Ethics Institute Laws of computer ethics. It required the respondents to indicate their awareness of the 10-item measures on computer ethics. These items were based on the code of ethics designed on the published ethical guidelines titled "The Ten Commandments of Computer Ethics" by the Computer Ethics Institute. The section adopted a 4-point Likert Scale, ranging from 1 (Very Aware), 2 (Aware), 3 (Unaware) to 4 (Very Unaware). A descriptive method was used to conduct the data analysis using SPSS v23.0.
7 Results or findings
7.1 Demographic data of respondents
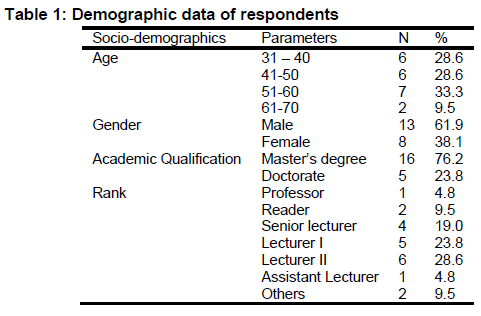
Table 1 reveals that Ten (10) respondents (47.6%) were from Adeleke University, Ede, Osun State while 11 (52.4%) came from LAUTECH Ogbomosho, Oyo State. The result also shows that more respondents are in the third quartile (51-60 years). There were also more males (61.9%) than females (38.1%) see Table 1 that took part in the study. Sixteen (16) (76.2%) respondents were Master's degree holders, while 5 (23.8%) had doctorate degrees in LIS
7.2 Awareness of Cyberethical Issues among LIS Educators in Selected Universities in South-west Nigeria
To achieve this objective, respondents were asked to indicate their awareness of cyberethical issues. The results are presented in Table 2.
A 96.2% of respondents were either aware or very aware of cyberethical issues, based on the units of analysis that were used for assessment. Only 4.8% of respondents stated that they were not aware that they should not use the resources of others or copy files on their system without the approval or consent from the owner of the files or device. Looking at the results in Table 2, it is evident that the percentage of respondents who were very aware of the items listed in the table on cyberethical issues is more than those who were very unaware of the cyberethical issues. There is also the reflection that the awareness level is high going by the percentage of very agree and agree which is 96%. This implies that LIS educators who are the respondents in this study are aware of cyberethical issues, and the awareness is also very high.
7.3 LIS Educators' Engagement/participation in Training on Cyberethical Related issues
To achieve this objective, respondents were asked to indicate their extent of engagement and participation in the training of cyberethical related issues. The results are presented in Table 3.
The results in Table 3 reveal that LIS educators regularly and always participate in training related to cyberethical issues. This is reflected in the percentage of those who regularly and always participated in the programmes greater than those who sometimes participated. The result implies that LIS educators regularly and always participated in training on cyber technology, internet policy issues, cyber security and cyberethics.
7.4 LIS Educators' Familiarity with Cyberethical Issues in Selected Universities in South-west Nigeria
To achieve this objective, respondents were asked to indicate their extent of familiarity with cyberethical related issues. The results are presented in Table 4.
The results in Table 4 show that the LIS educators who are very familiar with and familiar are more than those who are not familiar with any of the types of cyberethical issues. Of course, none of the respondents indicated non-familiarity with cybersecurity. This implies that the LIS educators are very familiar with various types of cyberethical issues including intellectual property, fair use, and illegal download and wrong copy of files and text, respecting others' opinions, and privacy concern in the cyber environment.
8 Discussion of findings
This study examined cyberethics awareness and implications on LIS educators in selected universities in South-west Nigeria. Based on the results the study demonstrated that the LIS educators were aware of cyberethical issues, and the awareness is also very high. The LIS educators regularly participated in training on cyber technology, Internet policy issues, cyber security and cyberethics. The LIS educators were very familiar with various types of cyberethical issues including intellectual property, fair use, illegal downloads and wrong copies of files and text, respecting others' opinions, and privacy concerns in the cyber environment.
The first result of this study revealed that the LIS educators were aware of cyberethical issues, and the awareness is also very high. This result was not unexpected because it agrees with the findings of previous related studies (Adetimirin, 2017; Aderibigbe and Owolabi, 2020; Milton et al., 2021). The finding of the study conducted by Naaj and Nachouki (2021) which reported generally that respondents were aware of cyberethics corroborated the finding or result of the current study. Also in agreement with the results of the current study is the report by Milton et al. (2021) which revealed a lack of awareness of cyberethical behaving in an exemplary manner online in a more public and professional capacity by the pre-service teachers across three European countries. However, the results contradicted Petrie-Wyman et al. (2022) report that both educators and students were unprepared for the remote cyberethics learning environment. The variation in the findings of the current study and that by Petrie-Wyman (2022) might be due to what the two studies focused.
The Petrie- Wyman et al. (2022) study addressed the cyber challenges experienced in the United States through the presentation of a collaborative cyberethics leadership framework and the gaps in training and sharing of best practices; the current study examined awareness of cyberethics and its implications on the LIS educators in universities in South-west Nigeria. Moreover, the two studies are also differentiated in terms of country and context. The former was conducted in the United States of America among schools while the latter was conducted in Nigeria and among universities.
The LIS educators regularly participated in training on cyber technology, internet policy issues, cyber security and cyberethics. Participation in training on cyberethics depends on the availability of information to be provided for the trainees. This lends credence to Aderibigbe's (2021) report that the provision of current information on awareness of cyberethics teaching and research on information ethics are related domains. They are related domains in the sense that one helps the other and without the former, the latter cannot be achieved. That is without readiness to participate in cyberethics training by LIS educators, the training information cannot be provided.
The results in this study also indicated that the LIS educators were very familiar with various types of cyberethical issues including intellectual property, fair use, illegal downloads and wrong copy of files and text, respecting others' opinions, and privacy concern in the cyber environment. This is also not surprising because findings from the previous related studies have reported something similar. For instance, Adetimirin (2017) revealed that there is a high level of awareness and knowledge about cyberethics in Nigeria. Also, following the current results in this study is the report by Paapa and Boakye (2017) that maintained that the majority of the students had adequate knowledge about information ethics and also demonstrated compliance with information ethics practices.
This is the demonstration of familiarity and the discussion of the cyberethical issues they were familiar was also listed as the concept of plagiarism, computer ethics, laws against indiscriminate photocopying, and fair use as the units of analysis all of which corresponded with the results in the current study. Also, there is a high consensus on what is deemed as ethical or unethical, that students sometimes engaged in diverse information ethics violations, they knew they were indulging in unethical or very unethical use of information. However, this current result is contrary to the finding on computer ethics reported by Jamil et al (2013) that the majority of students in Pakistan did not have any knowledge or were not completely familiar or almost familiar with computer ethics. The authors thought of the fact that the majority of the students had not received any training on computer ethics, thus making it very obvious for conscious and deliberate teaching of cyberethics as a course in the university or other institutions of higher learning.
9 Conclusion and recommendations
This study examined cyberethics awareness and implications on the LIS educators in selected universities in South-west Nigeria. Based on the results the study concludes that the LIS educators were aware of cyberethical issues, and the awareness was also very high. The LIS educators regularly participated in training on cyber technology, internet policy issues, cyber security and cyberethics. The LIS educators were very familiar with various types of cyberethical issues including intellectual property, fair use, illegal downloads and wrong copies of files and text, respecting others' opinions, and privacy concerns in the cyber environment.
The study recommends that LIS educators should consciously impress upon their students and other informational professionals who were not part of the study the need to consider being of upright moral character and full consideration of the feelings of others while online.
It is not the only method revealed in this study that the LIS educators acquire and develop skills, knowledge and familiarity with cyberethics. The LIS educators should consciously seek out various other methods. The LIS educators should be encouraged and sensitised to pursue additional online capacity-building programmes. Various free and moderately priced Internet-based courses are available using non-conventional teaching methods such as open and distance learning courseware programmes, as well as leveraging various social media platforms as aids to learning cyberethics. This can be done to expand the frontiers of knowledge, as well as refresher courses to keep up with the latest trends in LIS. Also, the deliberate adoption of cyberethics as a stand-alone distinct course that will be part of the curriculum of LIS should be encouraged to further enhance the awareness of students.
There is a need for the LIS educator's knowledge of cyberethics to be prioritised during their initial training as information professionals, particularly at such a time when their professional identity is being shaped. This will enable them to transfer the knowledge to the students they are teaching who are the future information professionals.
10 Implications of the study
The importance of awareness of cyberethics cannot be underestimated in an online environment. Awareness of cyberethics will ensure that users maintain the highest levels of concern and respect for other individuals, seeing it as a necessary duty when they surf the Internet to carry out their day-to-day information-seeking activities. While this is true for the generality of ICT users and netizens, it has even greater relevance to LIS educators who occupy a vantage position in the training of coming generations of LIS professionals. This is because adequate awareness by educators will result in the imbibing of all aspects of cyberethical issues by individuals who will acquire a greater level of security online and a greater level of acceptance of others. Cyberethics is presently one of the cutting-edge and front-burner issues in Information Sciences. There is a need for Nigerian cyberspace to also be a safe environment for all to use without fear from any individual or group of persons.
11 Limitations and suggestions for further studies
This study was limited in terms of the small sample from which data was collected. This was due to the observation of Covid-19 pandemic protocol especially social distancing which made many respondents reject participation in the exercise. Even among the small number that accepted, 14 of them still did not turn in their responses. Also, only the LIS educators from two South-west Nigeria universities participated in the study. This is considered very limited going by the number of universities in the South-west region which is just a geo-political zone out of the six geopolitical zones that make up Nigeria. There are other universities even in South-west Nigeria, and many more in the remaining five regions of the country.
Therefore, extending the study to universities in the remaining five geopolitical zones will bring worthwhile and valuable results generalisable to universities in the entire Nigeria nation. Therefore, future researchers should consider looking into this. Data in the study was collected using a self-reported instrument, a questionnaire. Therefore, future researchers should consider using a combination of instruments to enable triangulation and collection of data from various sources.
References
Aderibigbe, N.A. and Owolabi, K.A. 2020. Cyberethical behaviour of university students: an overview of university of Zululand, South Africa and federal university of agriculture, Abeokuta, Ogun state, Nigeria. Journal of Applied Information Science and Technology, 13(1), 86-106. [ Links ]
Aderibigbe, N.A. 2021. Synopsis on cyberethics behaviour: a literature review. Inkanyiso, Journal of Humanities and Social Science, 13(2), 273-290. [ Links ]
Adetimirin, A. 2017. Awareness and knowledge of cyberethics by library and information science doctoral students in two Nigerian universities. International Journal of Technology Policy and Law,3(1), 43-55. [ Links ]
Arellano, A. and Cámara, N. 2017. The importance of ICT in society's needs: An empirical approach through Maslow's lens. BBVA Research, Financial Inclusion Document, August. Retrieved from: https://www.bbvaresearch.com/wp-content/uploads/2017/09/maslow_pyramid_en.pdf
Blanchette, K. L. and Ellington, L. 2018. Strategic leadership in a global virtualreality. Strategic Leadership, 99 -124. [ Links ]
Dunmade, A.O., Tomori, A.R.andOlatunbosun-Adedayo, A. 2019. Cybercrime in Nigeria: An Overview of Laws and Ethics from the Information Technology (IT) Professional's Perspective. Proceedings of the 22nd iSTEAMS Multidisciplinary SPRING Conference. Aurora Conference Centre, Osogbo, Nigeria. 17th - 19th December 3-20.
Dunmade, A.O. 2022. Perception, Awareness and Attitude of female postgraduate students towards cyberethical behaviour in North-Central Nigeria universities. (Doctoral Dissertation, Adeleke University). [ Links ]
Jamil, M., Tariq, R. and Shah, H.J. 2013. Ethical attitudes towards the use of computer and information technology. International Research Journal of Arts and Social Sciences, 2(4), 72-78. [ Links ]
Kim, S. and Park, H. 2014. Intrinsic and extrinsic factors impacting individual cyber ethics awareness and behavior intention. The Journal of Information Systems, 23(1), 111-138. [ Links ]
Koçyiğit, M.and Karadağ, E. 2016. Developing an Ethical Tendencies Scale based on the theories of ethics. Turkish Journal of Business Ethics, 9, 297-307. [ Links ]
Liywalii, E. 2020.Analyzing the impact of ethical issues in e-government implementation: a case of Zambia. [Doctoral dissertation, The University of Zambia]. [ Links ]
Mason, R. O. 1986. Four ethical issues of the information age. MIS quarterly, 5-12. [ Links ]
Mâţă, L., Lazăr, I. M., & Ghiaţău, R. (2020). Exploring academic dishonesty practices among science education university students. Journal of Baltic Science Education, 19(1), 91-107. [ Links ]
Milton, J., Giæver, T.H., Mifsud, L.and Gassó, H.H. 2021. Awareness and knowledge of cyberethics: A study of pre-service teachers in Malta, Norway, and Spain. Nordic Journal of Comparative and International Education (NJCIE), 5(4), 18-37. [ Links ]
Naaj, M.A. and Nachouki, M. 2021. Evaluating students' cyber ethics awareness in a gender-segregated environment under the impact of COVID-19 pandemic. TEM Journal,10(3), 1248-1256. DOI: 10.18421/TEM103-31. [ Links ]
Österberg, J. 2019. Deontological ethics: Exposition. In Towards Reunion in Ethics (pp. 27-59). Springer, Cham.
Jamil, M., Tariq, R. and Shah, H.J. 2013. Ethical attitudes towards the use of computer and information technology. International Research Journal of Arts and Social Sciences, 2(4), 72-78. [ Links ]
Rahman, N. A., Sairi, I. H., Zizi, N. A. M. and Khalid, F. 2020. The Importance ofCybersecurity Education in School. International Journal of Information and Education Technology, 10(5), 20-30. [ Links ]
Ramluckan, T., van Niekerk, B. and Leenen, L. 2020. Cybersecurity and information warfare research in South Africa: Challenges and proposed solutions. Journal of Information Warfare, 19(1), 80-86. [ Links ]
Paapa, F. K. and Boakye, E. 2017. Information Ethics among Graduate Students of the University of Ghana. Philosophy and Practice (e-journal). 1698-1723. [ Links ]
Petrie-Wyman, J., Rodi, A., McConnell, R. and D'Ascenzo, P. 2022. The b-school knowledge sharing journey: how to inform and connect cyberethics education with the k-12 pipeline. Developments in Business Simulation and Experiential Learning, 49, 142-154. [ Links ]
Petrie-Wyman, J., Rodi, A. and McConnell, R. 2021. Why Should I Behave? Addressing UnethicalCyberBehavior through Education. In Developments in Business Simulation and Experiential Learning: Proceedings of the Annual ABSEL conference (Vol. 48).
Petrie-Wyman, J., Rodi, A. and McConnell, R. A. 2021. Where is the Justice? What We Don't Know about Cyber Ethics. The International Journal of Ethical Leadership, 8(1), 94-115. [ Links ]
Supavai, E. 2014. Measuring online moral reasoning: The development and psychometric properties of the Cyberethics Scale (Doctoral dissertation, Boston University). [ Links ]
The Computer Ethics Institute. 1992. The 10 Commandments of Computer Ethics. CEIOnline.
Verecio, R. L. 2016. Computer ethics awareness: Implication to responsible computing. International Journal of Education and Research, 4(3), 195-204. [ Links ]
Received: 24 January 2022
Accepted: 13 March 2023














