Services on Demand
Article
Indicators
Related links
-
 Cited by Google
Cited by Google -
 Similars in Google
Similars in Google
Share
SAIEE Africa Research Journal
On-line version ISSN 1991-1696
Print version ISSN 0038-2221
SAIEE ARJ vol.109 n.3 Observatory, Johannesburg Sep. 2018
ARTICLE
Soft-output decision-based detection of SSK, Bi-SSK AND QSM
A. A. TijaniI; N. PillayII; H. XuIII
ISchool of Engineering, University of KwaZulu-Natal, Durban 4041, Republic of South Africa. E-mail: adekilekunmajeed@gmail.com
IISchool of Engineering, University of KwaZulu-Natal, Durban 4041, Republic of South Africa. E-mail: pillayn@ukzn.ac.za
IIISchool of Engineering, University of KwaZulu-Natal, Durban 4041, Republic of South Africa. E-mail: xuh@ukzn.ac.za
ABSTRACT
Space shift keying (SSK) modulation is a special case of conventional spatial modulation (SM), where the amplitude and/or phase modulation symbols are eliminated from the transmission process so as to reduce complexity. However, high spectral efficiencies are difficult to achieve with SSK. At the same time, the spectral efficiency of SM can be further improved. On this note, to further enhance the spectral efficiencies of both SM and SSK, quadrature SM (QSM) and Bi-SSK modulations, respectively, were proposed. In coded channels, typically soft-output detection coupled with soft-input channel decoding yields significant signal-to-noise ratio (SNR) gain. Hence, in this paper, we propose soft-output maximum-likelihood detectors (SOMLD) for SSK, Bi-SSK and QSM modulated systems. Monte Carlo simulation results demonstrate that the error performances of the proposed SOMLD schemes closely match with that of their hard-decision maximum-likelihood detector counterparts in uncoded channels; while, significant SNR gains are yielded in coded channels.
Key words: Bi-space shift keying, coded spatial modulation, quadrature spatial modulation, soft-output detection, space shift keying.
1. INTRODUCTION
Currently, much effort is being geared towards 5G in the research community [1]. The major demands of 5G networks are increased capacity and data rates, reduced latency, improved quality of service and energy efficiency [2]. Multiple-input multiple-output (MIMO) systems [3] hold the potential to meet these demands, but not without challenges. For example: the need for inter-antenna synchronization (IAS) between transmit antennas, increased form-factor allowing for ideal spacing of transmit and receive antennas, reduction of inter-channel interference (ICI) at the receiver and large computational complexity (CC) overhead. A number of schemes have recently been investigated to address these challenges, while exploiting the advantages of MIMO.
Mesleh et al. [4] proposed spatial modulation (SM). The key idea in SM is to employ the index of a single transmit antenna as an extra means to convey information. Information is divided into two parts. The first part is mapped to a chosen symbol from an amplitude and/or phase modulation (APM) signal constellation, while the remaining part determines the transmit antenna that is to be activated for transmission of the APM symbol. It should be noted that the dormant antennas transmit zero power during each and every transmission. As a result, SM completely avoids IAS, ICI at the receiver, and only requires a single radio frequency (RF) chain, which translates into a relatively low-complexity receiver [5-7]. Based on these merits, the SM scheme proves to be a good candidate for deployment in next generation wireless communication systems. However, options for decreasing its system complexity exist [8]. On this note, a variant of SM in the form of space shift keying (SSK) was proposed
[8]. In SSK, only the spatial domain of SM is exploited to relay information. The elimination of the APM results in lowered detection complexity, less stringent transceiver requirements, and simplicity [8]. A criticism of SSK is that large antenna arrays are required to achieve high data rates. In this regard, bi-space shift keying (Bi-SSK) [9] was proposed as an extension to SSK. Bi-SSK employs dual antenna indices (one associated with a real number and the other with an imaginary number) to carry information. This results in twice the achievable data rate of SSK, while preserving the advantages of the latter.
To improve the data rate of SM, quadrature SM (QSM) was proposed [10-12]. In QSM [10-12], the overall throughput of SM is enhanced by extending its spatial domain into in-phase and quadrature-phase dimensions. In order to allow this, the complex constellation symbol of SM is further decomposed into its real and imaginary parts. The in-phase and quadrature-phase spatial dimensions are orthogonal cosine and sine carrier signals and are used for conveying the real and imaginary parts, respectively, of the APM transmission symbol. This, consequently, allows for an additional base-two logarithm of the number of transmit antennas bits to be transmitted; while other SM advantages, such as the usage of single RF chain at the transmitting end, avoidance of ICI, and low-complexity receiver, are preserved [10, 11].
In practice, the majority of communication systems employ channel coding. Moreover, it has been demonstrated that a combination of soft-output detection with soft-input channel decoding results in a net coding gain compared to the conventional hard-decision detection/decoding [13-20]. On this note, a soft-input soft-output detector, based on a block minimum mean-squared error algorithm, was proposed for generalised SM (GSM) in [13]. In a similarly research, two soft-input soft-output algorithms that are based on the deterministic sequential Monte Carlo (SMC) technique are proposed for demodulation of GSM signals in [14]. These algorithms achieve near-optimal performances with low complexity. Moreover, turbo and recursive systematic convolutional (RSC) coded receiver are respectively employed to obtain better error performances for the GSM.
By exploiting the features of M-PSK and M-QAM constellations, an efficient transmission scheme for SM systems with soft-decision aided detector was presented in [15]. The error correction ability of channel coding is exploited and low-density parity-check code is employed. Results show that the PSK and QAM-based soft-output detectors achieve the same performance as Max-Log-LLR algorithm with reduced CC. Furthermore, a study of the benefits of nonlinear frequency domain turbo equalizer (FDTE) in single-carrier-SM systems was carried out in [16]. With a RSC coded receiver, the FDTE is aided by a time-domain soft-decision feedback (TDSDF) such that the equalizer operates on a frame-by-frame basis and is designed based on the minimum block-averaged mean-square error (MBMSE) criterion. Simulation results show that the proposed equalizer outperforms conventional linear FDTD.
In [17-19], soft-output detection algorithms for orthogonal frequency division multiplexing based SM (SM-OFDM) and space-time block coded SM were proposed, and significant signal-to-noise ratio (SNR) gains were demonstrated. However, no such detectors have been proposed for the more recent variants of SM. Hence, to address the demands of 5G, SSK, Bi-SSK and QSM also hold the potential for unleashing the benefits of MIMO. 5G systems will most certainly be adaptive (based on channel conditions). But certain modes will utilize channel coding. In these modes, the error performance may be boosted by employing soft-output detection coupled with soft-input channel decoding for any of the schemes, such as SSK, Bi-SSK and QSM. Meanwhile, the schemes could also be easily extended to LTE-advanced systems, such as in [21].
Hence, in this paper, we are motivated to propose soft-output detectors for SSK, Bi-SSK and QSM modulated signals. Summarily, the contributions of the paper are as follows: a) SOMLD for SSK is formulated, b) Bi-SSK enhances the spectral efficiency of SSK; hence, the corresponding SOMLD for Bi-SSK is proposed, c) the SOMLD for QSM is formulated, and d) corresponding Monte Carlo simulations for the proposed detectors are demonstrated. The remainder of the paper is organized as follows: Section 2 presents the system models of the SSK, Bi-SSK and QSM schemes. The proposed soft-output detectors are presented in Section 3, analysis of the CCof the new detectors in Section 4, simulation results and discussions are given in Section 5, and finally, conclusions are drawn in Section 6.
Notation: Matrices are denoted with bold italics uppercase letters, vectors with bold italics lowercase letters and scalars with regular letters. (·)τ is used for transpose, (·)Η for Hermitian and 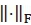 for the Frobenius norm of a vector or matrix.
for the Frobenius norm of a vector or matrix.  and
and  are used to represent the real and imaginary parts of a complex number,
are used to represent the real and imaginary parts of a complex number, 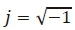 is a complex number and argmin f(x) for argument of the minimum, which returns a set of values of χ for which the function f(x) attains its smallest value.
is a complex number and argmin f(x) for argument of the minimum, which returns a set of values of χ for which the function f(x) attains its smallest value.
2. SYSTEM MODELS
2.1. Space shift keying (SSK)
The system model for SSK modulation is depicted in Fig. 1. Compared to SM, SSK eliminates the transmission of APM symbols, leaving only the antenna indices to relay information. This ensures that the advantages of SM are preserved, while the hardware complexity is significantly reduced [8]. Given an array of Nttransmit antennas/elements, a set of mSSK = log2(Nt) source bits is mapped to the  antenna, where
antenna, where 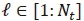 . The
. The 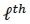 antenna is then activated in the subsequent signalling interval to transmit the symbol xt= 1 [8]. Accordingly, the Nt x 1 SSK transmit vector can be written as [8]:
antenna is then activated in the subsequent signalling interval to transmit the symbol xt= 1 [8]. Accordingly, the Nt x 1 SSK transmit vector can be written as [8]:
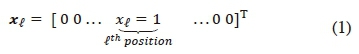
The Nr X 1 received signal vector is given as [8]:
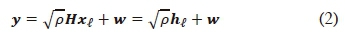
where ρ is the average SNR at each receive antenna, Η is the Nr x Ntchannel matrix, and w is the Nr x 1 additive white Gaussian noise (AWGN) vector. The entries of both Η and w are independent and identically distributed (i.i.d.) according to CN(0,1). From (2), it is observable that the column indices of Η are used as sources of information, i.e. xtis fixed and set to unity, while  changes according to the incoming symbols, thus representing the actual constellation symbols for SSK.
changes according to the incoming symbols, thus representing the actual constellation symbols for SSK.
The optimal maximum-likelihood (ML) detector for SSK, therefore, has the objective of obtaining only the antenna index that was employed at the transmitter, and is given as [8]:
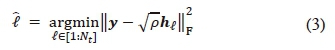
2.2. Bi-space shift keying (Bi-SSK)
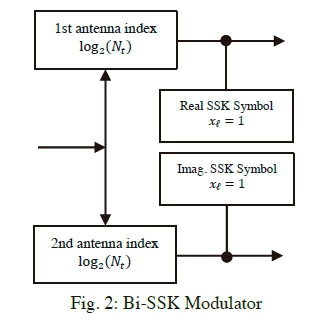
Fig. 2 illustrates the modulator for Bi-SSK [9], which can be inserted in place of the SSK modulator, shown within the dotted lines in Fig. 1, to obtain a simple model of Bi-SSK transmission. Note that for Bi-SSK, the mapper in Fig. 1 has two inputs, as will be discussed. The key idea involves dividing the set of information bits into 2 blocks of length log2Nt. Each of the blocks are mapped into an SSK transmit vector  and are represented as
and are represented as  and
and 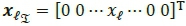 , where
, where  , as in SSK, for both real and imaginary
, as in SSK, for both real and imaginary  . The corresponding transmit antenna/s are then activated accordingly for transmission. Hence, a set of mBi_SSK = 2 xlog2(Ntt) bits, is mapped into a Bi-SSK transmit vector
. The corresponding transmit antenna/s are then activated accordingly for transmission. Hence, a set of mBi_SSK = 2 xlog2(Ntt) bits, is mapped into a Bi-SSK transmit vector 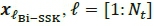 defined as:
defined as:
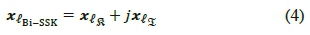
where 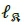 represents the active real transmit antenna index and
represents the active real transmit antenna index and  represents the active imaginary transmit antenna index.
represents the active imaginary transmit antenna index.
An example of the mapping process for Bi-SSK modulation, is tabulated in Table 1, considering Nt= 4 . In the example, the total number of transmitted information bits per time slot can be calculated as 2 x log2(Nt) = 2 x log2(4)= 4 bits. In accordance with the mapping rules of Bi-SSK; the set of 4 bits (b3 b2 b1 b0) are equally grouped into two parts (b3 b2 and b1 b0) and each group is used to select one of the Nt= 4 transmit antennas that are available for transmission - one for the real symbol and the other for the imaginary symbol. In other words, it can be said that each group is used to modulate separate SSK symbols, which are added together in a complex manner to form the Bi-SSK symbol.
Note that some 11 other possible values of "Bits" have been omitted. Generally, this is done intentionally to save spaces, and because the omitted possibilities can easily be obtained from the given table. For example, when Bits = [0 0 0 1]; the "Real Bits (Real Tx Index)" is "00 (1)" and this can be inferred from rows 3 and 5 of Table 1, where the same bits, "00", have been considered for Real Bits. In the same way the "Imag. Bits (Imag. Tx Index) which is "01 (2)", and can be inferred from rows 2 of the table.
The received signal vector for Bi-SSK may then be defined as [9]:
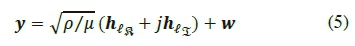
where μ is a scaling factor for the average SNR p, such that = 1 for a single transmit antenna and = 2 when the bits are mapped to two transmit antennas.
Given 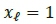 for both real and imaginary
for both real and imaginary  is the channel gain vector associated with the transmission of the real symbol and
is the channel gain vector associated with the transmission of the real symbol and 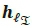 is the channel gain vector associated with the transmission of the imaginary symbol. This effectively means that the changing channel columns of act as the Bi-SSK random constellation points. Once again, the entries of both Η and w are i.i.d. according to CN(0,1). The optimal hard-decision ML detector (HDMLD) for the Bi-SSK system is defined as [9]:
is the channel gain vector associated with the transmission of the imaginary symbol. This effectively means that the changing channel columns of act as the Bi-SSK random constellation points. Once again, the entries of both Η and w are i.i.d. according to CN(0,1). The optimal hard-decision ML detector (HDMLD) for the Bi-SSK system is defined as [9]:
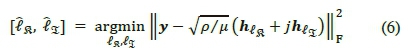
2.3. Quadrature spatial modulation (QSM)
The rule governing the transmission of QSM stipulates that a group of m.QSM = log2(Nt2M) information bits can be transmitted simultaneously [10, 11]. A model of the QSM transmitter may also be depicted as Fig. 1, if the SSK modulator is replaced by the QSM modulator of Fig. 3 and two inputs are sent to the mapper. The source information bit sequence is partitioned into three parts, such that log2(Nt) bits are used to select the real antenna index 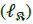 , another log2(Nt) bits are used to select the imaginary antenna index
, another log2(Nt) bits are used to select the imaginary antenna index 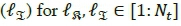 .
.
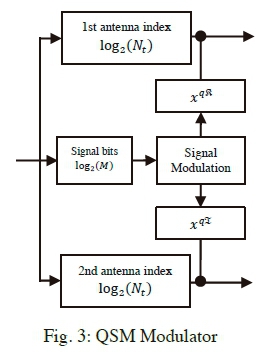
The remaining log2 (M) bits are used to select an M-ary quadrature amplitude modulation (MQAM) constellation symbol 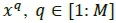 . The selected symbol xqof the complex constellation is further decomposed into its constituent real and imaginary parts
. The selected symbol xqof the complex constellation is further decomposed into its constituent real and imaginary parts  , respectively, and transmitted by the respective antennas. Thus, the signal vector of QSM can be represented as:
, respectively, and transmitted by the respective antennas. Thus, the signal vector of QSM can be represented as:
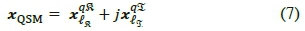
where and  are Nt x 1 vectors, with
are Nt x 1 vectors, with 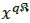 and
and 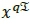 , respectively, representing the non-zero entry placed at the
, respectively, representing the non-zero entry placed at the 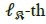 and
and 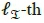 positions.
positions.
Table 2 illustrates a typical mapper for a 4 b/s/Hz QSM transmission with Nt= 2 and Μ = 4. Note again that; in the table, some 12 other possible values of "Bits" have been omitted, intentionally. As earlier said, this is done to save spaces, and because the omitted possibilities can be obtained from the given table.
At the output of the channel, the received signal vector may be defined as [10-12]:
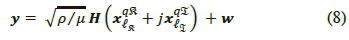
where μ is the scaling factor for the average SNR, such that when  , and when
, and when 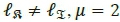 Η is the wireless channel with a complex channel matrix of dimension NrX Nt in the presence of AWGN represented as
Η is the wireless channel with a complex channel matrix of dimension NrX Nt in the presence of AWGN represented as 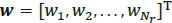 . The entries of Η and w are assumed to be i.i.d. according to CV(0,1). The received signal may be simplified as:
. The entries of Η and w are assumed to be i.i.d. according to CV(0,1). The received signal may be simplified as:
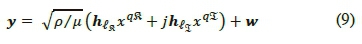
where  represents the NrX 1
represents the NrX 1 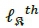 column of Η and
column of Η and 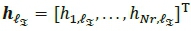 represents the
represents the  column of H.
column of H.
Assuming perfect knowledge of the channel at the receiver, the received signals are processed by the optimum ML detector, which searches jointly across all the available antenna combinations and APM symbols. The detector jointly estimates  , which are used to recover the original message. The detector is given in [10-12] as:
, which are used to recover the original message. The detector is given in [10-12] as:
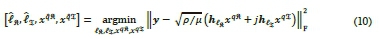
3. PROPOSED SOFT-OUTPUT DETECTORS
It is desired that next generation communication systems provide users with high data rates, in addition to ensuring reliability and power efficiency. To achieve this, practical communication systems commonly employ channel coding such that errors induced by noise and unreliable channels are reduced. It has been demonstrated in the literature that soft-output detection coupled with soft-input channel decoding maximizes the coding gain achievable [20, 23]. In [18, 19] soft-output detection has been investigated for SM and space-time block coded SM. No such investigation has been performed for the more recent SSK, Bi-SSK or QSM schemes, which maintain several advantages over SM.
Based on this motivation, we propose SOMLDs for the SSK, Bi-SSK and QSM schemes. To arrive at the targeted improvements in the error performances of the respective systems due to coding gain, the system model of Fig. 1 is extended to include channel coding and decoding. For each of the proposed detection schemes, we assume that:
(i) antenna indices and data symbols (if applicable) are uncorrelated;
(ii) data symbols (if applicable) are independent and generated with equal probability;
(iii) antenna bits are independent and generated with equal probability, and;
(iv) full channel knowledge is available at the receiver.
3.1. SOMLD for SSK Modulation
The codewords from the channel encoder are transmitted by SSK modulation, such that the input to our proposed demodulator is given as (2). The a-posteriori log-likelihood ratio (LLR) [18] for the α-th transmit antenna bit may be formulated as:
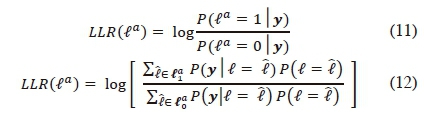
where 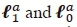 are vectors of the antenna indices with ' 1' and '0', respectively, at the α-th antenna bit position.
are vectors of the antenna indices with ' 1' and '0', respectively, at the α-th antenna bit position.
On application of Bayes' theorem, the demodulator output of (12) can be defined as:
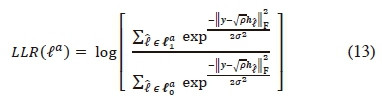
where σ2 is the variance of the AWGN.
3.2. SOMLD for Bi-SSK Modulation
The Bi-SSK modulated signals are represented as (5). At the receiver, the proposed demodulator independently calculates the LLR for the real and imaginary antenna index bits using the received coded Bi-SSK. Therefore, the a-posteriori LLR for the α-th real transmit antenna bit can be expressed mathematically as:
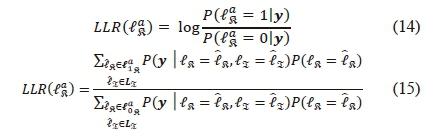
where  are vectors of the real antenna indices with '0' and '1', respectively, at the α-th antenna bit position, and
are vectors of the real antenna indices with '0' and '1', respectively, at the α-th antenna bit position, and 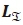 is a set representing all possible
is a set representing all possible 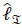 .
.
On application of the Bayes' theorem, the demodulator output in (15) can be defined as:
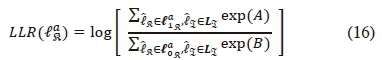
where 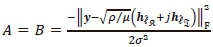 and σ2 is the variance of the AWGN.
and σ2 is the variance of the AWGN.
Similarly, the a-posteriori LLR for the α-th imaginary antenna bit is formulated as:
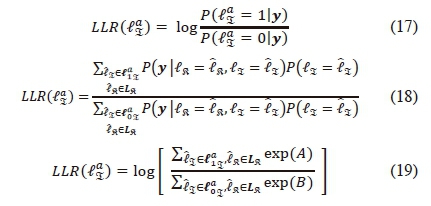
where 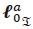 and
and  are vectors of the imaginary antenna indices with '0' and '1', respectively, at the α-th antenna bit position, and
are vectors of the imaginary antenna indices with '0' and '1', respectively, at the α-th antenna bit position, and  is a set representing all possible
is a set representing all possible 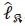 .
.
3.3. SOMLD for QSM Modulation
For QSM, the proposed SOMLD demodulator independently calculates the LLR for the α-th real antenna bit 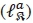 , α-th imaginary antenna bit
, α-th imaginary antenna bit 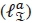 , b-th real symbol bit
, b-th real symbol bit  and b-th imaginary symbol bit
and b-th imaginary symbol bit 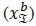 . The a-posteriori LLR may be formulated as follows:
. The a-posteriori LLR may be formulated as follows:
Considering demodulation of the α-th real transmit antenna bit:
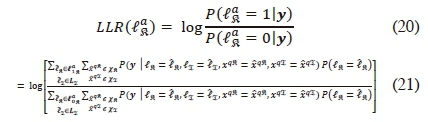
where  are vectors of the real antenna indices with '0' and '1', respectively, for the α-th antenna bit position, and
are vectors of the real antenna indices with '0' and '1', respectively, for the α-th antenna bit position, and 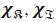 represents the set of all possible
represents the set of all possible  and
and  , respectively.
, respectively.
On application of the Bayes' theorem, the demodulator output in (21) can be formulated as:
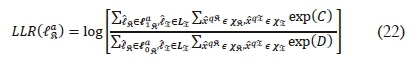
where  , with σ2 the variance of the AWGN.
, with σ2 the variance of the AWGN.
Similarly, the α-th imaginary antenna bit is computed and expressed as:
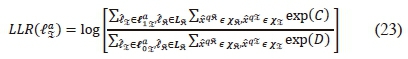
where 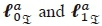 are vectors of the imaginary antenna indices with '0' and '1', respectively, at the α-th antenna bit position.
are vectors of the imaginary antenna indices with '0' and '1', respectively, at the α-th antenna bit position.
Furthermore, the b-th real symbol bit is computed as:
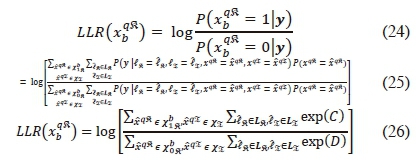
where and are vectors of the real data symbols with '0' and ' 1', respectively, at the b-th data bit position.
Similarly, the b-th imaginary symbol bit is computed as:
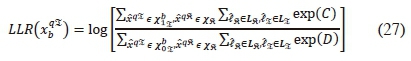
where  are vectors of the imaginary data symbols with '0' and '1', respectively, at the b-th data bit position.
are vectors of the imaginary data symbols with '0' and '1', respectively, at the b-th data bit position.
The proposed soft-output detectors achieve an improvement in error performance when the output is fed into a soft-input Viterbi channel decoder [17-19] and estimates of the transmitted messages are obtained.
4. COMPARISON OF COMPUTATIONAL COMPLEXITIES
In this section, the computational complexities (CCs) for the proposed SOMLD for SSK, Bi-SSK and QSM systems are evaluated. For fair comparison, we also present complexities of their respective HDMLD counterparts. Particularly, in our analyses of the imposed CCs of the proposed SOLMDs, we make the following assumptions:
i. only complex additions and multiplications are considered to have impacts on the complexity of the detectors. This approach is consistent with the approaches in [7, 19]
ii. we consider the complexity imposed by all metrics, including those that only need to be solved once and stored for future computations. Thus, precomputed results are available such that redundant computation is not required. This approach is consistent with [5, 7, 19].
iii. Finally, the computation of the logarithm functions, present in the LLRs of the detectors, are approximated via the use of a look-up table (LUT)-based method presented in [22] and therefore impose no additional complexity.
4.1. SSK-HDMLD vs SSK-SOMLD
To formulate the CC of the SSK-SOMLD, the complexity imposed by detecting the α-th real antenna bit is analysed. Upon inspection, the numerator and denominator in (13) can further be expressed as  and
and 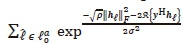 , respectively. From this, the computation of
, respectively. From this, the computation of 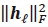 is equivalent to
is equivalent to 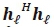 and requires Nr complex multiplications for each I. Considering the numerator,
and requires Nr complex multiplications for each I. Considering the numerator,  requires a total of
requires a total of  complex multiplications. It is evident that
complex multiplications. It is evident that 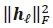 would require
would require 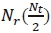 complex multiplications at the denominator for
complex multiplications at the denominator for 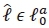 . Going by assumptions (ii) and (iii), the computation of the logarithm functions present in the LLR can be ignored and computational results can be stored and reused in order to avoid redundancy. On this note, the summation of complex multiplications at both numerator and denominator gives the total CC of the SSK-SOMLD, expressed as:
. Going by assumptions (ii) and (iii), the computation of the logarithm functions present in the LLR can be ignored and computational results can be stored and reused in order to avoid redundancy. On this note, the summation of complex multiplications at both numerator and denominator gives the total CC of the SSK-SOMLD, expressed as:
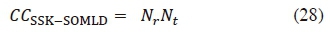
Meanwhile, the CC of the SSK-HDMLD is given in [4] as ccssk-hdmld= NrM. Note that Nt = Μ in the SSK modulation.
4.2. Bi-SSK-HDMLD vs Bi-SSK-SOMLD
The individual complexity imposed by each of the two processes of detecting the α-th real antenna bits and α-th imaginary antenna bits are analysed to determine the total Bi-SSK-SOMLD complexity. On expansion of the Frobenius norms, A and Β in (16) and (19) can be expressed as  . Considering the numerator (i.e. A) in (16) the computation of the first term
. Considering the numerator (i.e. A) in (16) the computation of the first term 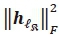 , is equivalent to
, is equivalent to 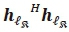 and requires Nr complex multiplications for each
and requires Nr complex multiplications for each 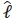 , such that
, such that 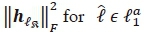 requires a total of
requires a total of 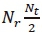 complex multiplications. The second term would also require
complex multiplications. The second term would also require 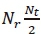 .
.
Since this has already been computed for the first term, we assume that the second term imposes no additional complexity and the result of the first term is reused. The third term,  , requires
, requires 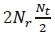 complex multiplications for
complex multiplications for  . Evidently, the computation of the forth term
. Evidently, the computation of the forth term 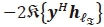 , requires
, requires  . The summation of these gives the total CC imposed by the computation of the numerator of (16), which is expressed as
. The summation of these gives the total CC imposed by the computation of the numerator of (16), which is expressed as 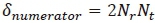 . A proper observation of the denominator (i.e. ) in (16) reveals that the denominator would impose a total complexity of 2NrNt complex multiplication which can be ignored because it has been pre-computed for the numerator ( ). This simply implies that the detection of the -th real antenna bit imposes a total complexity of 2NrNtcomplex multiplications on the SSK-SOMLD receiver. Using a similar approach, while taking note of the stated assumptions, it can be shown that the CC imposed by the estimation of the α-th imaginary antenna bit (
. A proper observation of the denominator (i.e. ) in (16) reveals that the denominator would impose a total complexity of 2NrNt complex multiplication which can be ignored because it has been pre-computed for the numerator ( ). This simply implies that the detection of the -th real antenna bit imposes a total complexity of 2NrNtcomplex multiplications on the SSK-SOMLD receiver. Using a similar approach, while taking note of the stated assumptions, it can be shown that the CC imposed by the estimation of the α-th imaginary antenna bit ( 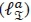 in (19) will not impose any further complexities. Consequently, the total computation complexity of our proposed Bi-SSK-SOMLD detector is calculated as:
in (19) will not impose any further complexities. Consequently, the total computation complexity of our proposed Bi-SSK-SOMLD detector is calculated as:
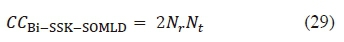
On the other hand, a clear consideration of Bi-SSK-HDMLD, given in (6), shows that the number of multiplications involved are twice of what is obtainable for SSK-HDMLD (3). Thus; without any loss of generality, the Bi-SSK-HDMLD total CC can be given as CCBi-ssk-hdmld = 2NrNt
4.3. QSM-HDMLD vs QSM-SOMLD
To formulate the CC of the QSM-SOMLD, the individual complexity imposed by each of the four detection processes of detecting the α-th real antenna bit, a-th imaginary antenna bit, b-th real symbol bit and b-th imaginary symbol bit, is analysed. With the expansion of the Frobenius norms in (22), (23), (26) and (27), C = D = 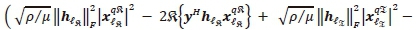
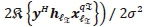 .Here we first consider the CC of [C/D] as the common factor to all the detection processes to the QSM-SOMLD.
.Here we first consider the CC of [C/D] as the common factor to all the detection processes to the QSM-SOMLD.
Considering the first term of the C (as the numerator), 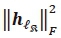 is equivalent to
is equivalent to 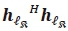 and requires 2Nr complex multiplications for each
and requires 2Nr complex multiplications for each 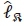 . Thus, computing
. Thus, computing 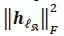 for
for 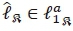 requires
requires 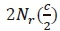 complex multiplications, while the computation of
complex multiplications, while the computation of 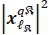 requires only Μ complex multiplications. Therefore, the CC imposed by the first term is given by
requires only Μ complex multiplications. Therefore, the CC imposed by the first term is given by  consideration of the second term shows that the computation of
consideration of the second term shows that the computation of 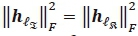 , therefore, we ignore the computation of
, therefore, we ignore the computation of  and use the stored result. This means that the computation of the seconds term
and use the stored result. This means that the computation of the seconds term 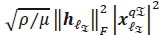 is dependent only on the computation of
is dependent only on the computation of 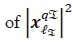 which is given by M. The third term requires 2 Nr complex multiplications for
which is given by M. The third term requires 2 Nr complex multiplications for 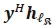 and a further Μ complex multiplications for
and a further Μ complex multiplications for 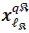 , for each of the 2 antenna-pair combinations; making a total of
, for each of the 2 antenna-pair combinations; making a total of  . Obviously, the computation of the forth term will be equivalent to
. Obviously, the computation of the forth term will be equivalent to 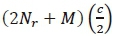 . Hence, the CC imposed by the numerator is the sum of:
. Hence, the CC imposed by the numerator is the sum of: 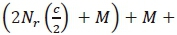
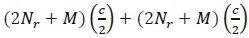 . This equivalent to:
. This equivalent to: 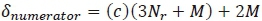
Next, we consider D (as the denominator). It is evident that the computation of the first term depends only on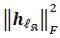 for
for 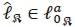 which requires
which requires 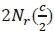 complex multiplications. This is in line with the assumption that results can be stored and reused in future computations so as to avoid redundant computations. For the same reason, the second term does not impose any further complexity.
complex multiplications. This is in line with the assumption that results can be stored and reused in future computations so as to avoid redundant computations. For the same reason, the second term does not impose any further complexity.
The third term imposes 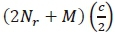 complex multiplications, while the forth term similarly requires
complex multiplications, while the forth term similarly requires  complex multiplications. Therefore, the CC of the denominator is calculated as
complex multiplications. Therefore, the CC of the denominator is calculated as 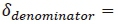
 .
.
Following the assumption (iii) and in accordance with the analyses above, the CC imposed by estimating the α-th real antenna bit  in (22) is given by the addition of
in (22) is given by the addition of 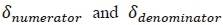 which is
which is 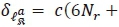
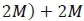 . Using a similar approach, it can be shown that the CC imposed by the estimation of the α-th imaginary antenna bit
. Using a similar approach, it can be shown that the CC imposed by the estimation of the α-th imaginary antenna bit 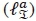 , b-th real symbol bit
, b-th real symbol bit 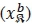 , and b-th imaginary symbol bit
, and b-th imaginary symbol bit 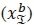 will not impose any further complexities as stored results can reused in order to avoid redundant computations. Hence, the CC of our proposed detector, in terms of complex multiplications, can be written as:
will not impose any further complexities as stored results can reused in order to avoid redundant computations. Hence, the CC of our proposed detector, in terms of complex multiplications, can be written as:
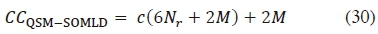
Meanwhile, in terms of complex multiplications involved in the detection process, the complexity imposed by jointly detecting 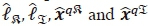 in (10) can be analysed, on assumptions in (i) and (ii). Let, (10) be represented as
in (10) can be analysed, on assumptions in (i) and (ii). Let, (10) be represented as 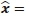
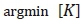 such that
such that 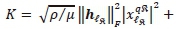
 . Thus, the CC of the QSM-HDMLD detector can be evaluated based on as the total complexities imposed by the joint detection of
. Thus, the CC of the QSM-HDMLD detector can be evaluated based on as the total complexities imposed by the joint detection of  , in terms of complex multiplications. Here, the overall CC is estimated and given as
, in terms of complex multiplications. Here, the overall CC is estimated and given as 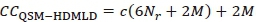 which is similar to
which is similar to 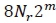 as given in [10].
as given in [10].
In the above, we present the CCs for HDMLDs and the proposed SOMLDs in the cases of SSK, Bi-SSK and QSM systems, respectively. A critical comparison of these CCs shows that HDMLD and the proposed SOMLD have the same CCs in each case. It can therefore be concluded that the proposed SOMLDs, despite their impressive performances, impose no additional computational complexity compared to their conventional HDMLD counterparts. Remarkably; when compared with traditional polynomial/rational-function algorithms [24, 25], the LUT - which we have employed in the CC analyses of the proposed SOMLDs, is faster - because it requires less work in the approximation steps, more accurate - because the rounding error made in the approximation is usually tiny, and amendable to tight error analysis [22]. However, we note that logarithm functions are usually computed by using a Taylor series or another iterative algorithm - which takes up valuable clock cycles; hence, for the LUT method, the space complexity can be maintained at the cost of only a minimal increase in hardware.
5. NUMERICAL RESULTS AND DISCUSSION
Monte Carlo simulations of the proposed detectors were executed in the Matlab environment and are in terms of the average bit error rate (BER) as a function of the average SNR. The termination criterion for simulations was the number of bit errors, set at 1,200. Simulations were run until a BER of 10-6. For all simulations, Rayleigh frequency-flat fading channels and the presence of AWGN is assumed. We assume 4 antennas are employed at the receiver. For all coded cases, a ½ rate convolutional encoder was employed to encode the information bits under the constraint length 9 with code generator matrices g1= (561)octal; g2 = (753)octal[18, 19]. At the respective receivers, the proposed detectors are employed and their outputs are fed into a soft-input Viterbi channel decoder [20, 23], in order to obtain estimates of the transmitted messages.
In the following investigations, two spectral efficiencies are considered, viz. 6 b/s/Hz and 4 b/s/Hz. For each of these spectral efficiencies we choose a configuration, such as to satisfy: mSSK = log2(Nt), mBi_SSK= 2 X log2(Nt) and mQSM= log2(Nt2M). Note; if no channel coding is employed, then we expect the SOMLD to match that of the HDMLD. This is expected because both detectors are based on the ML principle and there is no additional coding gain that may be exploited, hence reducing to the same solution [20, 23]. This is also a means of validation.
In Fig. 4, the error performances of HDMLD and SOMLD detectors are evaluated, both for coded and uncoded channel conditions for 6 b/s/Hz SSK systems. For uncoded channels, simulation results demonstrate that the proposed SOMLD scheme matches identically with the HDMLD. Hence, the soft-output demodulator has no effect, unless employed in a coded channel and coupled with a soft-input decoder at the receiver [19]. In the same figure, it is evident that the coded SOMLD detector yields significant SNR gains. For example, at a BER of 10-6, an SNR gain of approximately 4.2 dB is achieved over coded HDMLD. Hence, the advantage of soft-output demodulation followed by soft-input decoding is demonstrated. Moreover, for illustrative purposes, by the use of coding, the proposed SOMLD achieves an SNR gain of approximately 8.0 dB over the uncoded HDMLD/S OMLD scheme, at the same BER. This large gain is expected, since we are comparing a coded and uncoded system in this instance.
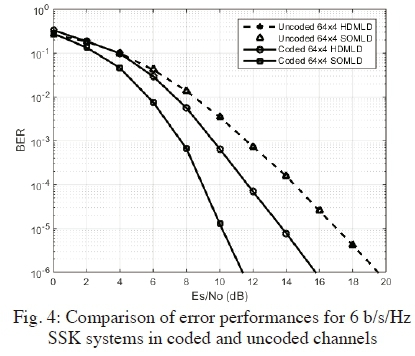
The BER performances of the Bi-SSK system are presented in Fig. 5. As expected, the 6 b/s/Hz 8x4 Bi-SSK system with conventional HDMLD shows a performance that is matching closely with the proposed SOMLD, in uncoded channels. Meanwhile, in coded channels, the proposed SOMLD for the Bi-SSK system performs better than the HDMLD, with an SNR gain of approximately 4.2 dB at a BER of 10_6. Furthermore, it is evident that the coded SOMLD outperforms the uncoded conventional HDMLD with an SNR gain of 10.2 dB, at the same BER.
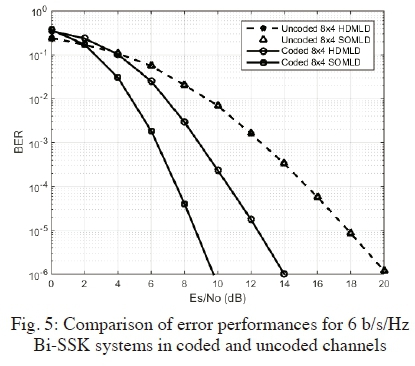
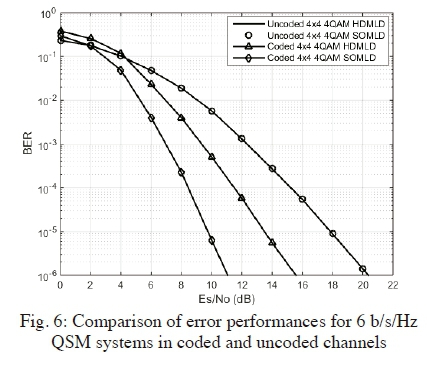
Fig. 6 presents the error performances of a 6 b/s/Hz QSM system with Nt= 4, Nr= 4 and Μ = 4. The proposed SOMLD in coded channels achieves an SNR gain of 8.5 dB over the uncoded conventional HDMLD detector for QSM, at a BER of 10-6. At the same BER and with channel coding an SNR gain of approximately 4.7 dB is evident between the proposed SOMLD and the HDMLD. As expected, for uncoded channels, the QSM system with HDMLD demonstrates identical error performance as the proposed SOMLD.
In Fig. 7, Fig. 8 and Fig. 9; we present the error performances of 4 b/s/Hz SSK (16x4), Bi-SSK (4x4) and QSM (2x4) systems, respectively. The results are demonstrated under the proposed soft-output detectors as compared to the existing HDMLDs in coded and uncoded channels. Similar behaviour as shown for 6 b/s/Hz is evident, in all the cases of SSK, Bi-SSK and QSM respectively.
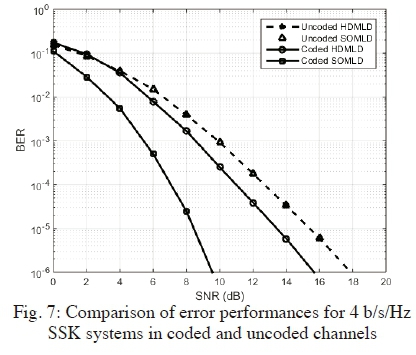
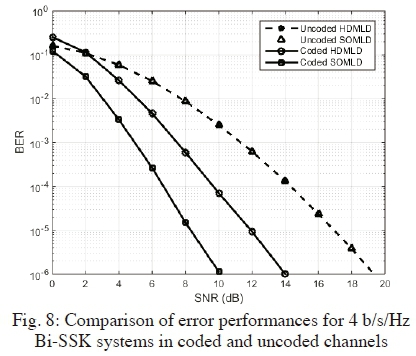
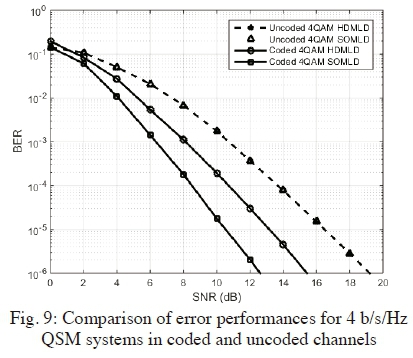
In all instances, as shown in the graphs - Fig. 7, Fig. 8 and Fig. 9 - for SSK, Bi-SSK and QSM, respectively; the uncoded HDMLD and SOMLD curves are identical. When coding is employed, HDMLD yields an SNR gain of 2.2 dB, 5.1 dB and 3.9 dB, for SSK, Bi-SSK and QSM, respectively. The proposed SOMLDs further enhance the SNR gain by 6.1 dB, 4 dB and 2.5 dB for SSK, Bi-SSK and QSM, respectively. The smaller gain realized for QSM is due to the use of only two transmit antennas
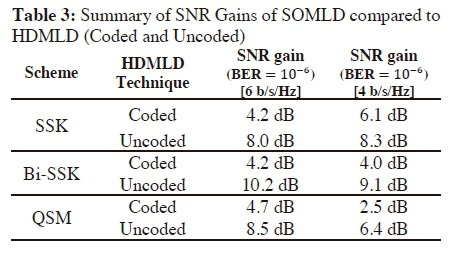
A detailed summary of the SNR gains achieved in the investigations is presented in Table 3. As stated earlier, the SNR gains achieved by the proposed coded SOMLDs for 6 and 4 b/s/Hz systems of SSK, Bi-SSK and QSM over their uncoded HDMLD schemes, are due, not only to the coding introduced, but also to the effectiveness of the soft-decision over the hard decision techniques.
6. CONCLUSION
In this paper, we have proposed SOMLDs for the SSK, Bi-SSK and QSM modulation schemes. In uncoded channels, the proposed detectors match the optimal error performance of their respective HDMLD. In coded channels, the proposed SOMLDs yield significant SNR gains over the corresponding conventional coded HDMLD. In comparison to the HDMLDs, the proposed SOMLDs impose no additional computational complexity, since a look-up table can be employed to compute the logarithm. Finally, we maintain that a possible future work is desired to determine analytical bounds for the proposed SOMLDs.
REFERENCES
[1] A. Gupta, R.K. Jha, "A Survey of 5G Network: Architecture and Emerging Technologies," IEEE Access, vol. 3, pp. 1206-1232, 2015. [ Links ]
[2] R.Q. Hu, Y. Qian, "An Energy Efficient and Spectrum Efficient Wireless Heterogeneous Network Framework for 5G Systems," IEEE Communications Magazine, vol. 52, no. 5, pp. 94-101, May 2014. [ Links ]
[3] E. Telatar, "Capacity of Multi-Antenna Gaussian Channels," European Transactions on Telecommunication, vol. 10, no. 6, pp. 558-595, November/December 1999. [ Links ]
[4] R. Mesleh, H. Haas, C.W. Ahn and S. Yun, "Spatial Modulation - A New Low Complexity Spectral Efficiency Enhancing Technique," in Proceedings of the First International Conference on Communications and Networking in China, pp. 1-5, October 2006.
[5] J. Jeganathan, A. Ghrayeb and L. Szczecinski, "Spatial modulation: optimal detection and performance analysis," IEEE Communications Letters, vol. 12, no. 8, pp. 545-547, August 2008. [ Links ]
[6] R.Y. Mesleh, H. Haas, S. Sinanovic, C.W. Ahn and S. Yun, "Spatial Modulation," IEEE Transactions on Vehicular Technology, vol. 57, no. 4, pp. 2228-2241, July 2008. [ Links ]
[7] N.R. Naidoo, H.J. Xu and T.A-M. Quazi, "Spatial modulation: optimal detector asymptotic performance and multiple-stage detection," IET Communications, vol. 5, no. 10, pp. 1368-1376, 2011. [ Links ]
[8] J. Jeganathan, A. Ghrayeb, L. Szczecinski and A. Ceron, "Space shift keying modulation for MIMO channels," IEEE Transactions on Wireless Communications, vol. 8, no. 7, pp. 3692-3703, July 2009. [ Links ]
[9] H-W. Liang, R.Y. Chang, W-H. Chung, H. Zhang and S-Y. Kuo, "Bi-Space Shift Keying Modulation for MIMO Systems," IEEE Communications Letters, vol. 16, no. 8, pp. 1161-1164, August 2012. [ Links ]
[10] R. Mesleh, S.S. Ikki and H.M. Agoune, "Quadrature Spatial Modulation - performance analysis and impact of imperfect channel knowledge," Transactions on Emerging Telecommunications Technologies, November 2014.
[11] R. Mesleh, S.S. Ikki and H.M. Agoune, "Quadrature Spatial Modulation," IEEE Transactions on Vehicular Technology, vol. 64, no. 6, pp. 2738-2742, June 2015. [ Links ]
[12] S. Naidu, N. Pillay, H. Xu, "A Study of Quadrature Spatial Modulation," in Proceedings of the South African Telecommunications and Network Applications Conference, September 2015.
[13] L. Xiao, P. Yang, Y. Xiao, J. Liu, S. Fan, B. Dong and S. Li, An Improved Soft-Input Soft-Output Detector for Generalized Spatial Modulation, IEEE Signal Processing Letters, vol.23, no. 1, pp. 30-34, January 2016. [ Links ]
[14] B. Zheng, X.Wang, M.Wen and F. Chen, Soft Demodulation Algorithms for Generalized Spatial Modulation Using Deterministic Sequential Monte Carlo, IEEE Transactions on Wireless Communications, vol. 16, no. 6, pp. 3953-3967, June 2017. [ Links ]
[15] C. Li, J. Wang, Y. Cheng and Y. Huang, Low-complexity soft-decision aided detectors for coded spatial modulation MIMO systems," EURASIP Journal on Wireless Communications and Networking, vol. 34, 2016. [ Links ]
[16] Y. Zhao, P. Yang, Y. Xiao, L. Xiao, B. Dong and W. Xiang, "An Improved Frequency Domain Turbo Equalizer for Single-Carrier Spatial Modulation Systems," IEEE Transactions on Vehicular Technology, vol. 66, no. 8, pp. 7568-7572, August 2017. [ Links ]
[17] S.U. Hwang, S. Jeon, S. Lee and J. Seo, "Soft-output ML detector for Spatial Modulation OFDM Systems," IEICE Electronic Express, vol. 6, no. 19, pp. 1426-1431, October 2009. [ Links ]
[18] Q. Tang, Y. Xiao, P. Yang, Q. Yu and S. Li, "A New Low-Complexity Near-ML Detection Algorithm for Spatial Modulation," Wireless Communications Letters, IEEE, vol. 2, no. 1, pp. 90-93, 2013. [ Links ]
[19] R. Govender, N. Pillay and H. Xu, "Soft-output Spacetime Block Coded Spatial Modulation," IET Communications, vol. 8, no. 16, pp. 2786-2796, 2014. [ Links ]
[20] T.K. Moon, "Error Correction Coding: Mathematical Methods and Algorithms," Wiley, June 2005.
[21] Q. Li, R.Q. Hu, Y. Qian, G. Wu, "Cooperative communications for wireless networks: Techniques and Applications in LTE-Advanced Systems," IEEE Wireless Communications, vol. 19, no. 2, pp. 22-29, April 2012. [ Links ]
[22] P.T.P. Tang, "Table-lookup algorithms for elementary functions and their error analysis," in Proceedings of the 10th IEEE International Symposium on Computer Arithmetic, pp. 232-236, June 1991.
[23] B. Sklar, "Digital Communications: Fundamentals and Applications," Prentice Hall, January 2001.
[24] W. Cody and W. Waite, "Software Manual for the Elementary Functions," Prentice Hall, Englewood Cliffs, N.J., 1980.
[25] J. F. Hart et al, "Computer Approximations," John Wiley and Sons, N.Y., 1968.














