Services on Demand
Article
Indicators
Related links
-
 Cited by Google
Cited by Google -
 Similars in Google
Similars in Google
Share
SAIEE Africa Research Journal
On-line version ISSN 1991-1696
Print version ISSN 0038-2221
SAIEE ARJ vol.108 n.1 Observatory, Johannesburg Mar. 2017
A ranking method for rating the performances of permutation codes
K. OgunyandaI; T.G. SwartII
IDepartment of Electrical and Electronic Engineering Science, University of Johannesburg, Auckland Park, 2006, South Africa. Email: ogunyanda@gmail.com
IIDepartment of Electrical and Electronic Engineering Science, University of Johannesburg, Auckland Park, 2006, South Africa. Email: tgswart@uj.ac.za
ABSTRACT
Minimum Hamming distance, dm, has been widely used as the yardstick for the performance of permutation codes (PCs). However, a number of PCs with the same dmand cardinality can have different performances, even if they have the same distance optimality. Since PC is a robust channel coding scheme in power line communications applications, we present a simple and fast ranking method that predicts the relative performance of PCs, by using the information extracted from their Hamming distance distributions. This tool is useful for selecting an efficient PC codebook out of a number of similar ones.
Key words: Channel coding, Hamming distance distribution, Permutation coding, Power line communications, Ranking method.
1 INTRODUCTION
Power line communications (PLC), which involves information transmission through the existing power network, is now a popular technology that may be used for home internet access, data distribution, networking, smart metering and electric vehicle-to-charging stations. The major setback of this technology is the performance degradation posed by the various noise types present in the communication channel (i.e. power line). These noise types include background noise, impulsive noise and narrowband interference [1, 2]. These noise types are inherent in the channel, because the main purpose of the power line network is not for communication applications. In order to make the channel conducive for communications, it may be helpful to use higher transmission power or distortion-free frequencies in the communication system. There are, however PLC communication standards that enforce constraints on the range of power and frequencies that are useable [3-5]. As such, in order to achieve effective PLC systems, a robust channel coding scheme is a crucial component to consider.
The channel coding scheme of interest in this work is permutation coding (PC). This is motivated based on the foundational work on PCs reported by Vinck, who was the first to suggest its usage for PLC applications [1]. According to Vinck, PCs in combination with MFSK are capable of handling the types of noise associated with narrowband PLC channels. This then gave inspiration for more research works on PCs, some of which are reported in [6-16].
There have been some approaches to the generation of PC codebooks with different minimum Hamming distances and cardinalities. The term dm refers to the minimum Hamming distance between any two distinct codewords in a codebook, C, while \C\ is the cardinality, which is the total number of possible codewords in the codebook. However, how one selects the best codebook out of a number of competitive PC codebooks with similar characteristics, is a challenging problem that we have attempted to solve in this study. The quality of a communication system can be greatly impaired if a poor code design is used.
In coding, dm is usually used to determine the strength of a code in handling errors. According to [2], a PC is able to detect t symbol errors provided that:

Moreover, in terms of error correcting capability, a PC is able to correct t/2 number of errors. However, apart from the dm in a given codebook, other distances greater than dm also feature, when the distance relationships between every distinct codeword are computed. All of these distances have a cummulative contribution in the performance of any given codebook. This notion was used by Viterbi in [19], when he demonstrated that various possible distances, resulting from every remerging path in the trellis-code representation of a convolutional code, contribute to its error probability. A similar approach was used in [20-22] to determine the distance spectrum used for comparing the performances of convolutional codes with similar constraint lengths and decoding complexities. We thus employ a similar approach in the ranking method presented in this study. However, instead of using it in the context of convolutional codes, it is used in the context of non-binary PC schemes. Also, Hamming distance distribution is what we have used in this study, instead of the distance spectrum used in convolutional code, which is a binary code. As such, this study is centered on determining the cumulative effects of all the possible distances, including dm, on the error detecting capability of any given PC.
Other work done in repect of PCs' performance tools include the one reported in [23], where a probabilistic approach was used to determine PC decoders' performances. However, this is not related to the work presented here, in that our approach is not decoder-dependent, as opposed to the work in [23], which is based on the type of decoding algorithm used in the design.
In addition, instead of using cardinality and Hamming weight distribution, Hamming distance distribution (HDD), which takes into consideration the contribution of every possible distance, is employed in our work. The reason for this is discussed later in this paper. To the best of our knowledge, this is the first time a method such as this is employed for PCs.
It is however worth noting that the ranking method presented here is only evaluated based on combined background noise (modeled as AWGN) and impulsive noise channel conditions. As such, a representation of AWGN+IN channel model is involved in this work. In order to study the performance of data transmission over a PLC channel, the authors in [24] used Middleton's model to model the transmission channel using a binary symmetric channel, whose transmission error probability ε is dependent on the impulsive noise variance. In our proposed ranking method, we represent the channel model as a composite channel, comprising of the modulator, demodulator and the PLC channel. This composite setup is appropriate, in order to be able to analyse channel codings [25]. The ε of this channel setup is derived from Middleton's noise model for impulsive noise.
Our contribution in this work therefore further promotes the use of PCs in PLC-related applications, by providing a good ranking tool that can be used to rate the performances of PC schemes of similar characteristics, without the need to perform performance simulations. Having to perform performance simulations for a multitude of codebooks, where each simulation could take a considerable time to complete, would mean that the process of choosing the best codebook will be extremely time consuming. In practical terms, this tool can be handy, when the best codebook is to be chosen out of a number of competitive codebooks. In [17] and [18], various PC codebooks of the same | C| and dmwere presented which had the same distance optimality, but their performances are seen to be slightly different when simulated. The method proposed here is therefore able to determine the best PC codebook in such situations. Hence, this work can be viewed as an extension of the work reported in [17] and [18].
We briefly describe what PC entails in Section 2. Section 3 gives a brief background to the HDD of a codebook, which is then used to propose the PC ranking method in Section 4. In Section 5, we present the HDDs of some known PCs and use the proposed method to analyse and predict their performances. Some simulation results are presented in Section 6 to validate the analysis performed in Section 5, after which a concluding note is given in Section 7.
2 INTRODUCTION TO PERMUTATION CODING
As stated in [9], a PC mapping maps binary data sequences to codewords of non-binary permutation sequences. A PC codebook is usually denoted as C(n,M,η), where n is the number of bits being mapped onto M symbols, while η determines the mapping type. Each codeword is of length M, and its symbols are chosen from {0,1,...,M - 1}. An example of a PC, with codeword length M = 4, where n = 2 bits are mapped to the PC symbols [9], is:
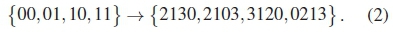
Another example with M = 4 and n = 4 is [18]:
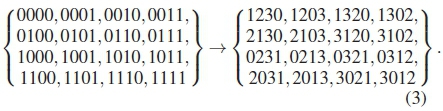
If the distances between the binary and permutation sequences are compared, three types of PC mappings can be defined, namely distance-conserving mappings (DCMs), distance-increasing mappings (DIMs) and distance-reducing mappings (DRMs). For instance, the binary sequences in (2) have dm = 1, while their corresponding permutation sequences have dm = 2. With this, η = 1. Hence, such a PC mapping is a DIM. By definition, a DIM ensures that the distances of the permutation sequences have some increase above the those of the binary sequences; a DCM ensures that the distances of the binary sequences are at least maintained in their corresponding permutation sequences; and a DRM ensures a controlled distance loss between distances. These three mapping types are collectively referred to as distance-preserving mappings [17,26].
A number of PC mapping and decoding algorithms are available in the literature. However, since we are only focusing on analysing PCs' relative performance, the simulations done in this work have considered the simple PC mapping and decoding algorithm presented in [9]. Therein, information bits are grouped into n bits, and these grouped bits are in turn mapped to corresponding codewords of length M, based on the grouped bit sequences. On the decoding side, a codeword having the closest Hamming distance to the received codeword is selected as the decoded codeword.
3 HAMMING DISTANCE DISTRIBUTION
We define HDD as the amount of contribution each possible Hamming distance has in the performance of a given PC codebook. Let Hamming distance k be represented by dk. Given a codebook C, with M and dm, all the possible distances dk in C are given by:
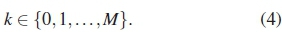
If the minimum distance is dm, (4) therefore reduces to
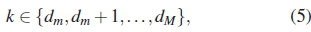
If the distance relationship between every distinct codeword in C is computed, a \C\x\C\ dimensional distance matrix E is generated. This matrix E consists of elements ei,jthat represent the distance between every pair of distinct codewords xiand xj in the codebook, where i, j = 1, 2,...,\C \ and is defined as:
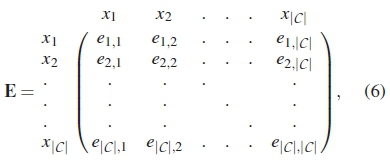
where eitj = 0, for i = j.
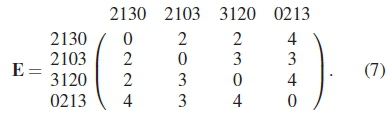
The total number of occurrences of each dkcan then be determined from the elements in matrix E. For instance, the distance matrix for the codebook in (2) is given by:
Let δk denote the number of times that dk appears in the distance matrix. We can then express the HDD, Δ, of all the possible δkas
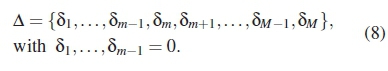
Using a probabilistic approach, the contribution of each dk, given its 5k, is given by:
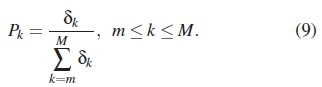
To illustrate this, the HDD and distance probabilities of the example codebook given in (3) are respectively given by:
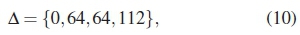
and
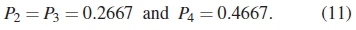
According to (11), it is clear that the codebook's performance mainly depends on d4, since it has the greatest probability. The significance of the δk values (i.e., the HDD) in determining the strength of a PC can be understood by considering Viterbi's findings in [19]. In the trellis diagram of a convolutional code, any arbitrary path leading to a given node is associated with a distance, which is computed by determining the bitwise differences between the code sequences along such a path and the expected code sequence. In order to detect the optimum path, all the distance information, which are dependent on the channel transition probability, need to be computed [19].
Similar to convolutional codes where numerous different codes, with varying performance, can be obtained for the same parameters, various mappings from binary sequences to permutation sequences can be obtained, all having the same dmand satisfying the distance preserving property. Thus a method was needed to determine which of these mappings would perform the best. The work in [17] and [18] addressed this by introducing the concept of distance optimality derived from distance matrix E like the one defined in (6). By denoting the sum of all distances in matrix E by 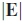 , a PC is considered distance optimal if
, a PC is considered distance optimal if  is maximised. It was shown that an upper bound on
is maximised. It was shown that an upper bound on  exists, and that any PC codebook attaining the bound would perform better than those that do not.
exists, and that any PC codebook attaining the bound would perform better than those that do not.
This clearly showed that all the distance contributions affect the performance of a given PC codebook. However, this approach is unable to distinguish between some codebooks with the same  , dm and maximised
, dm and maximised 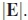 Hence, we investigate the proposed PC ranking method that goes further in analysing the HDD, to enable us to distinguish between such codebooks.
Hence, we investigate the proposed PC ranking method that goes further in analysing the HDD, to enable us to distinguish between such codebooks.
In HDD, the diagonal elements of E is not considered, because this would amount to comparing a codeword with itself. Hamming weight distribution on the other hand, is the number of codewords with Hamming distance k from an all 0's reference codeword. This however holds for binary codes. For non-binary codes such as PCs, a reference origin codeword, which may or may not be in C, is compared with each codeword, in order to determine the weight distribution [23]. One could state that HDD and weight distribution are the same, if the comparison is done with reference to an origin codeword. However, this is only valid for a linear code. Since PC is a non-linear code, to get accurate results every distinct codeword must be compared with all other codewords.
4 RANKING METHOD
In the context of this work, the term ranking refers to the order of performances of a given set of codewords, when being compared. The ranking method proposed in this study entails using the HDD discussed above to determine the probability of undetected symbol errors of a given codebook C. Since the PCs considered in this study are non-binary codes, this necessitates the use of non-binary modulation, such as phase shift keying (PSK) modulation. In order to evaluate the error probability of a PC system using such modulations, we employ the composite channel setup in Fig. 1 as the transmission channel.
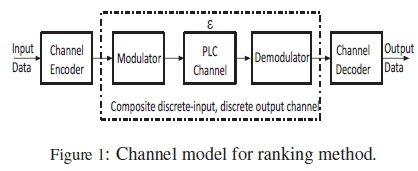
The PLC channel block is a combiation of impulsive noise and additive white Gaussian noise (AWGN). Since the modulator employs non-binary waveforms and the detector makes hard decisions, we can say that the composite channel has a discrete-time non-binary input sequence X = {0,1,...,MDP- 1}, where MDPis a modulation order whose value is a power of 2, and a discrete-time non-binary output sequence. Each input symbol has a probability 1/MDP of being received at the output. The probability of receiving an incorrect symbol is ξ = ε/ (MDP- 1), while ( 1 - ε) is the probability of correctly receiving a symbol at the detector's output, where ε is the transmission error probability.
If φ and α respectively denote a modulated and a demodulated symbol from the system, where φ e (0,1,...,M - 1) and α e (0, 1,...,Mdp - 1), the following expression therefore holds, based on the above composite channel setup:
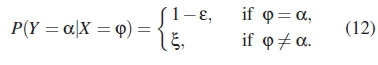
Also, as stated in (1), a PC has a symbol error detecting capability of (dm - 1), which can be generalised for each dkas
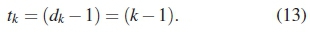
Since each dk has its number of appearances δk, the probability of a PC detecting δknumber of errors is dependent on the value of δk. The contribution of dk in the probabilty Puof undetected errors is based on the cummulative error probabilities of other distances > dkto yield a correct symbol and on the probabilities of dkand those of other distances < dkto yield an incorrect symbol (as defined in (12)). This is mathematically expressed as:
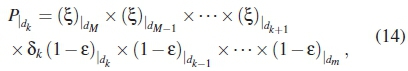
where (.)\ is the computation of (.) due to distance dk.
By computing all the Pdk values for every possible dkdefined in (5), the expression in (14) reduces to a generalised expression for the probability of undetected errors Pu in a PC system as:
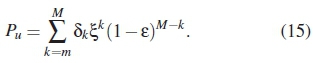
The expression in (15) can work for every type of channel, provided that ε, associated with such a channel, can be computed. The computation of ε is what gives the characteristics of the communication channel. If ε for a PLC channel can be obtained, it can be substituted into (15), thereby providing a means of analysing the performance of any PC codebook C(n,M,η) over a PLC channel, provided its HDD is known. This shall therefore lead us to the computation of ε for a PLC channel impaired with impulsive noise, which is one of the most notorious noise types in PLC.
Impulsive noise has a broadband power spectral density (PSD), which sometimes affects frequency components of the transmitted data for a particular length of time. According to the approximated form of Middleton's class A noise model, it has a strength Γ, which is the relationship between its variance  and that of additive white Gausian noise (AWGN)
and that of additive white Gausian noise (AWGN)  ,, given by
,, given by  . The smaller Γ is, the more severe the impulsive noise effect becomes. If A is the probability of impulsive noise affecting a symbol, the general form of error probability for an MPSK system is modified to account for the combination of AWGN and impulsive noise effects as follows:
. The smaller Γ is, the more severe the impulsive noise effect becomes. If A is the probability of impulsive noise affecting a symbol, the general form of error probability for an MPSK system is modified to account for the combination of AWGN and impulsive noise effects as follows:
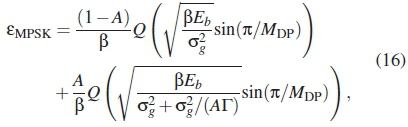
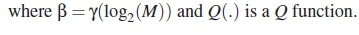
For a PLC system impaired with impulsive and background noise, ε in (15) is substituted with εMPSK. The value of γ, given by γ = n/ M is for coding rate compensation.
5 HDDs OF SOME KNOWN PCs AND THEIR PERFORMANCE RANKINGS
In order to validate the authenticity of the proposed ranking method, we adopt a number of codebooks from the available literature on PCs. As a form of evaluation, the expression in (16) was used to generate transmission errors for the expression in (15), which in turn, was used to simulate performance ranking curves for each codebook evaluated. An impulsive noise probability A = 0.01 was used, with varying strength Γ from 0 to 0.3.
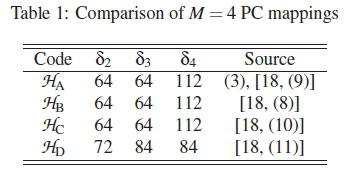
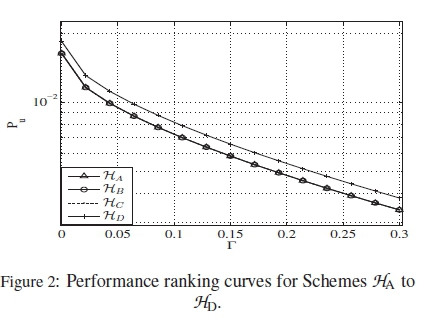
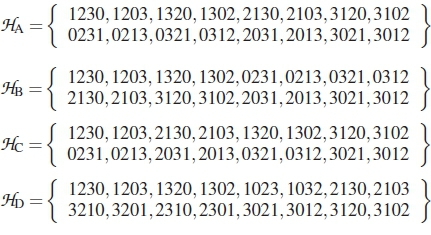
According to [18], (3) and two other codebooks were proven to be distance optimal. We therefore consider another non-optimal PC of M = 4 and \C\ = 16 (i.e., (8) from [18]), in comparison with the optimal ones. Table 1 gives their HDDs, while their performance ranking curves, simulated from (15) and (16), are as shown in Figure 2.
According to Figure 2, code HHD, has the worst performance. Of course, HA, HHBand HHCare expected to have overlapping performances, as their ranking curves clearly show, although their codewords are different. This agrees with the findings in [18]. This shall also be validated in our simulation section.
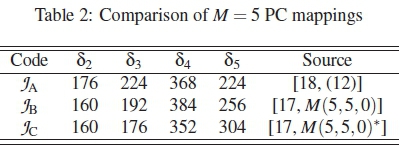
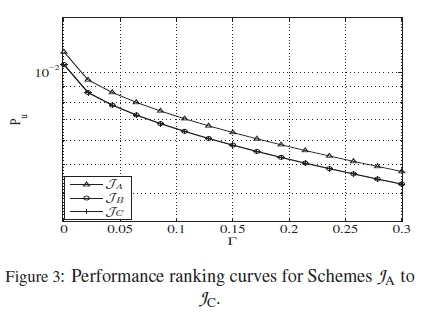
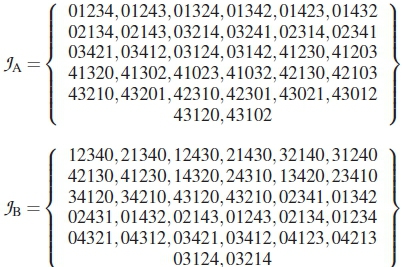
We proceed to consider PCs of M = 5. Here we adopt the codebook in (12) of [18] and two other similar codebooks M(5,5,0) and M(5,5,0)* from [17, Appendix B.1] and denote these three codebooks as JA, JB and JC. These codebooks all have M = 5 and \ C\ = 32. According to the distance optimality approach in [17] and [18], none of these codebooks are optimal, but JC is near optimal. However, what makes JBand JC different from JA is the fact that they have some repeating permutation symbols in some of their codewords. The HDDs of these codebooks are as shown in Table 2, with their ranking curves in Figure 3.
The curves in Figure 3 show that JA should have the worst performance compared to the others, which agrees with the claims in [17] and [18]. Although the findings in [17] show that JC is closer to optimal than JB, this analysis however shows that JBand JC should have overlapping behaviours, which shall later be validated in the simulation section.
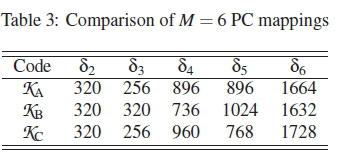
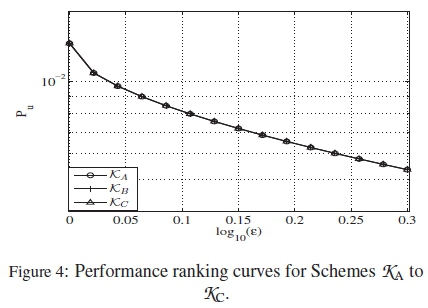
Next, we consider the three near-optimal codebooks, with M = 6, dm= 2 and \C\ = 64, presented in [17]. As observed in [17], these codebooks have the same level of optimality. Their HDDs are presented in Table 3, as schemes KKA, ·% and while Figure 4 presents their ranking curves.
Based on the curves in Figure 4, all the three codebooks !% and % should have relatively overlapping performances. This is because their Puvalues in Figure 4 are the same. This finding actually corroborates the notion of the optimum distance approach presented in [17].
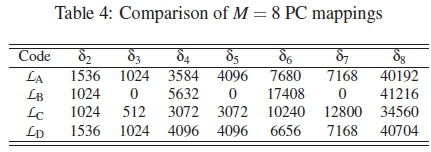
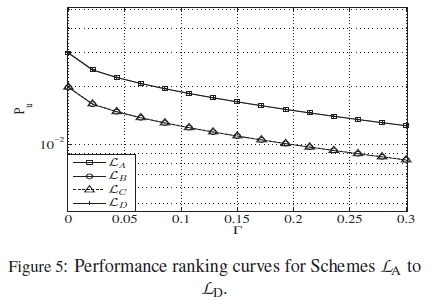
Another set of codebooks to be considered are the four optimal codebooks, with M = 8, dm = 2 and \ C\ = 256 in [17]. Their HDDs and ranking curves are presented in Table 4 and Figure 5, respectively.
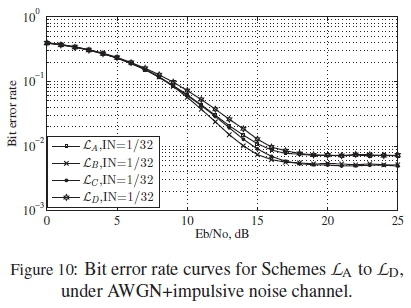
According to the ranking curves of these codebooks, we see that LA and LDhave overlapping curves, hence their real performances should follow a similar trend. Also, for LB and LC, the same applies because of their overlapping performance ranking curves. Despite the fact that the four codebooks are declared optimal, our ranking method is able to determine the best from these sets of codebooks of the same class.
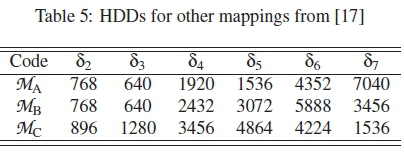
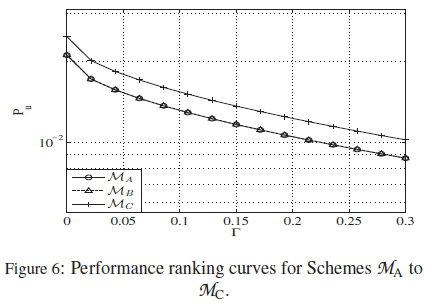
Further analyses carried out on some other mappings adopted from [17], are presented in Table 5 and Figure 6, based on the proposed ranking method.
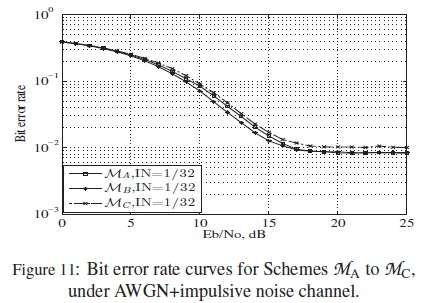
Scheme Ma is the M(7,7,0) DPM with M = 7, dm = 2 and\C\ = 128 from [17, Appendix B.1]. Schemes Mb and MCfrom [17, Appendix C.1] are also of the same class with this M(7,7,0) mapping. According to [17], MAis more optimal than the rest of these mappings, while MC is the least optimal. However, according to their ranking curves presented in Figure 6, MAand MBshould have overlapping performances in reality, because their curves overlap, while MC should perform worse than the rest.
6 SIMULATION RESULTS AND DISCUSSION
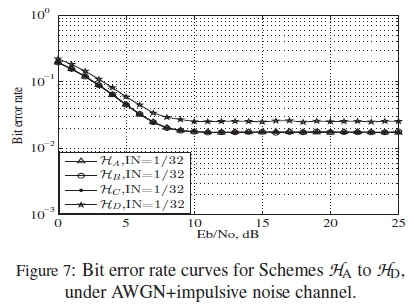
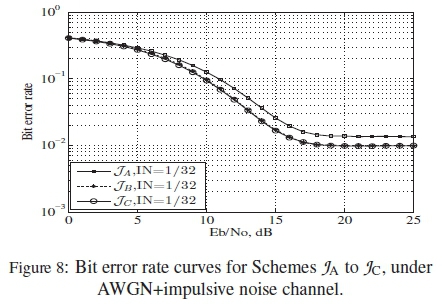
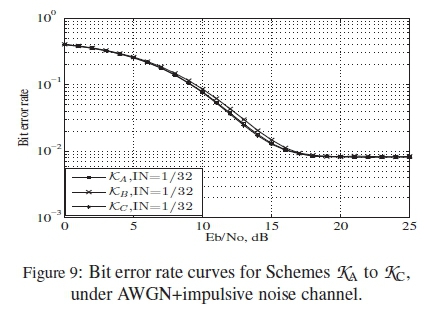
With a view to validating the proposed ranking method, all the schemes whose HDDs and ranking curves have been presented in Tables 1 to 5 and Figures 2 to 6, were simulated under combined AWGN and impulsive noise associated with PLC channels. The input data is composed of 9600 random bits. In order to model the effect of impulsive noise on the transmitted information, we assumed a Gilbert-Elliot model, where probabilities of moving from the bad state to good state and from the good state to bad state are defined. The probability that a transmitted symbol is hit by impulsive noise, in a bad state was assumed to be IN = 1/32, while a good state was assumed to be free of impulsive noise. Details about this model is available in [6]. The Eb/Noconsidered in the channel ranges from 0 to 25 dB.
The results shown in Figures 7 to 10 are for all the codebooks considered in our evaluations. As displayed in these figures, all the simulation results agree with the predicted performance rankings presented in Section 5. As predicted in Figure 2, Scheme HHDhas the worst curve, which is the reason why it has the worst performance according to Figure 7. Also, the performance curves of Schemes HA, HHBand HHCare seen to overlap, which is in line with the prediction of the proposed ranking method. The fact that these four schemes have the same dm does not mean they have the same performance. With the use of the proposed ranking method, we are able to know that Scheme HHDis not to be used in a transceiver design when codes such as HHA, HHband HHCare available.
The behaviours of Schemes JAto JCare also in the order of their ranking curves, with JCand JBbeing the best, while JAis the worst, as the results in Figure 8 show. More so, as shown in Figure 9 the similarities in the performances of Schemes KKA to % also obey the predicted rankings presented in Figure 4.
In line with the predicted rankings in Figure 5, Schemes LAand LDare seen to have closely overlapping curves, especially at Eb/No > 15 dB, as shown in Figure 10. Schemes LBand LCalso have similar patterns of behaviour, as predicted by the ranking method.
The results of the simulations done on Schemes MA, MB and MCare presented in Figure 11. According to this figure, MA is seen to overlap with Mb, but at high Eb/No values, while MC is seen to be the worst performing scheme. This is in agreement with the predicted rankings presented in Figure 6, based on the proposed ranking method.
In the above simulation results, it is worth noting that the probability IN used in the impulsive noise model is considered very high. That is why the performances of all the codebooks presented are relatively poor. With the aid of interleaving and concatenated outer codes, such as Reed-Solomon codes, the performances will definitely improve. Although the codebooks evaluated have a dm = 2, it does not mean that the proposed ranking method is limited to such cases. The method can be applied to any codebook category. Also, the significance of the different behaviours of all the schemes considered, are best observed at high Eb/Novalues.
7 CONCLUSION
Permutation coding has emerged as a promising channel coding scheme in PLC related applications. With a view to contributing to this field, we have presented a fast and simple way of ranking the relative performance of PC codebooks with similar properties. This method computes the Hamming distance distribution of the PC codebook and uses the information therein to compute the probability Pu of undetected error, which can, in turn, be used to compare the codebook to other codebooks with similar properties. A codebook with lower Pu values has better performance than any codebook with higher Pu values.
The method was validated using various known PC codebooks adopted from literature. The results of the simulations carried out agree with our claims, when the proposed method was used as a performance ranking tool. This tool is useful, when an efficient codebook is to be selected out of a number of similar codebooks. More so, it can be incorporated when exhaustive search for codebooks is done. It should however be noted that the computation of Pu considers only AWGN and impulsive noise effects.
An extended work in this area of study can be centered on including the effects of other types of PLC noise, such as narrowband noise in the computation of probability Pu. This, however remains a challenge as there is no link found between its PSD and that of AWGN.
ACKNOWLEDGEMENT
This work is based on research supported in part by the National Research Foundation of South Africa (UID 77596).
REFERENCES
[1] A.J.H. Vinck and J. Haring. "Coding and modulation for power-line communications," in Proceedings of the 2000 IEEE International Symposium on Power Line Communications and its Applications, Limerick, Apr. 2000, pp. 265-71.
[2] H.C. Ferreira, H.M. Grove, O. Hooijen and A.J.H. Vinck, "Power line communication," Wiley Encyclopedia of Electrical and Electronics Engineering, 2001.
[3] eRDF, PLC G3 Physical Layer Specification, 2013.
[4] CENELEC, 50065 part 1: Signalling on low voltage electrical installations in the frequency range 3 kHz to 148.5 kHz, general requirments, frequency bands and electromagnetic disturbances, 1992.
[5] PRIME, PRIME Technology, whitepaper: PHY, MAC and Convergence layers, 21st Ed., 2008.
[6] V.N. Papilaya, T. Shongwe, A.J.H. Vinck and H.C. Ferreira, "Selected subcarriers QPSK-OFDM transmission schemes to combat frequency disturbances," in Proceedings ofthe 2012 IEEE International Symposium on Power Line Communications and its Applications, Beijing, Mar. 2012, pp. 200-5.
[7] H.C. Ferreira, A.J.H. Vinck, T.G. Swart and I. de Beer, "Permutation trellis codes," IEEE Transactions on Commununications, Vol. 53, pp. 1782-9, Nov. 2005. [ Links ]
[8] T.G. Swart and H.C. Ferreira. "Decoding distance-preserving permutation codes for power-line communications," in Proceedings of IEEEAFRICON, Windhoek, Sept. 2007, pp. 1-7.
[9] K. Ogunyanda, A.D. Familua, T.G. Swart, H.C. Ferreira and L. Cheng, "Evaluation and implementation of cyclic permutation coding for power line communications," in Proceedings ofthe 2014 IEEE International Conference on Adaptive Science & Technology (ICAST), Ota, Oct. 2014, pp. 1-7.
[10] P.J. Dukes, "Coding with injections," Designs, Codes and Cryptography, Vol. 65, pp. 213-22, Dec. 2012. [ Links ]
[11] F.H. Hunt, S. Perkins and D.H. Smith, "Decoding mixed errors and erasures in permutation codes," Designs, Codes and Cryptography, Vol. 74, pp. 481-93, Feb. 2015. [ Links ]
[12] S. Huczynska and G.L. Mullen, "Frequency permutation arrays," Journal of Combinatorial Designs, Vol. 14, pp. 463-78, Jan. 2006. [ Links ]
[13] R.F. Bailey, "Error-correcting codes from permutation groups," Discrete Mathematics, Vol. 309, pp. 4253-65, 2009. [ Links ]
[14] K. Ogunyanda, A.D. Familua, T.G. Swart, H.C. Ferreira and L. Cheng, "Permutation coding with differential quinary phase shift keying for power line communication," in Proceedings ofthe 2014 IEEE PES Innovative Smart Grid Technologies European Conference, Istanbul, Oct. 2014, pp. 1-6.
[15] H.C. Ferreira and A.J.H. Vinck, "Interference cancellation with permutation trellis codes," in Proceedings ofthe 2000 IEEE Vehicular Technology Conference, Boston, MA, Sep. 2000, pp. 2401-7.
[16] Y.M. Chee, H.M. Kia, P. Purkayastha and C. Wang, "Importance of symbol equity in coded modulation for power line communications," in Proceedings of the 2012 IEEE International Symposium on Information Theory, Cambridge, Jul. 2012, pp. 661-5.
[17] T.G. Swart, "Distance-preserving mappings and trellis codes with permutation sequences," Ph.D. t dissertation, University of Johannesburg, 2006. [ Links ]
[18] T.G. Swart, I. de Beer and H.C. Ferreira, "On the distance optimality of permutation mappings," in Proceedings of the 2005 IEEE International Symposium on Information Theory, Adelaide, Sept. 2005, pp. 1068-72.
[19] A.J. Viterbi, "Convolutional codes and their performance in communication systems," IEEE Transactions on Communications Technology, Vol. 19, pp. 751-72, Oct. 1971. [ Links ]
[20] G.A. Alexandre, M. Guido and B. Sergio, "A new approach to the construction of high-rate convolutional codes," IEEE Communications Letters, Vol. 5, pp. 453-5, Nov. 2001. [ Links ]
[21] B.F. Ucha-Filho, R.D. Souza, C. Pimentel and M. Jar, "Further results on convolutional codes based on a minimal trellis complexity measure," in Proceedings of the 2006 IEEE International Telecommunication Symposium, Fortalez, Sept. 2006, pp. 123-8.
[22] Y. Bian, A. Popplewell and J.J. O'Reilly, "New very high rate punctured convolutional codes," Electronics Letters, Vol. 30, pp. 1119-20, Jul. 1994. [ Links ]
[23] T. Wadayama and M. Hagiwara, "LP-decodable permutation codes based on linearly constrained permutation matrices," IEEE Transactions on Information Theory, Vol. 58, pp. 5454-70, Aug. 2012. [ Links ]
[24] V.B. Balakirsky and A.J.H. Vinck, "Potential limits on power-line communication over impulsive noise channels," in Proceedings of the 2003 IEEE International Symposium on Power Line Communications and its Applications, Kyoto, Mar. 2003, pp. 32-7.
[25] J.G. Proakis, Digital Communications, McGraw-Hill, 4th edition, Chapter 7, pp. 364-412, 2001.
[26] T.G. Swart and H.C. Ferreira, "A generalised upper bound and a multilevel construction for distance-preserving mappings," IEEE Transactions on Information Theory, Vol. 52, pp. 3685-95, Aug. 2006. [ Links ]
[27] T. Shongwe, A.J.H. Vinck and H.C. Ferreira, "On impulse noise and its models," Proceedings of the 2014 IEEE International Symposium on Power Line Communications and its Applications, Glasgow, Mar. 2014, pp. 12-7.
APPENDIX
Codes for Schemes HHA to HD:
Codes for Schemes JA to JC:

Codes for Schemes % to KKC:
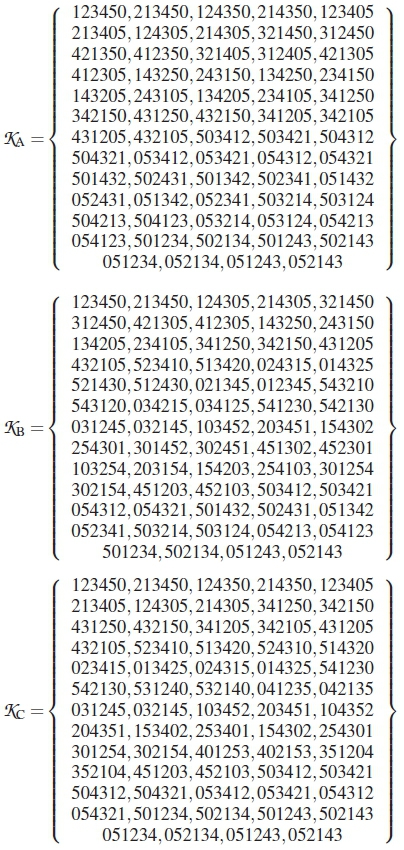
Codes for Schemes LA to LD:
Codes for Schemes MA to MD:

















