Services on Demand
Article
Indicators
Related links
-
 Cited by Google
Cited by Google -
 Similars in Google
Similars in Google
Share
Acta Commercii
On-line version ISSN 1684-1999
Print version ISSN 2413-1903
Acta Commer. vol.19 n.1 Johannesburg 2019
http://dx.doi.org/10.4102/ac.v19i1.612
ORIGINAL RESEARCH
An exploration of supply chain risk management in the South African third-party logistics industry
Arno Meyer; Wesley Niemann; Gerhard Uys; Déan Beetge
Department of Business Management, University of Pretoria, South Africa
ABSTRACT
ORIENTATION: The management of supply chain risks, disruptions and vulnerabilities has become a significant issue in supply chain management research in recent times.
RESEARCH PURPOSE: The purpose of this study was threefold, namely to (1) determine whether there is a clear understanding of supply chain risk management (SCRM) within the South African third-party logistics service providers (3PL) industry, (2) investigate the primary sources that lead to disruptions and vulnerabilities within the supply chains of South African 3PL organisations and (3) establish the current tools or methods used by supply chain practitioners to mitigate supply chain risks within the 3PL industry in South Africa.
MOTIVATION FOR THE STUDY: Supply chain risks are ever increasing and evolving which may have a substantial influence on organisational and supply chain performance.
RESEARCH DESIGN, APPROACH AND METHOD: A generic qualitative research method was used to gather data. A total of 20 purposively selected participants drawn from 20 3PL organisations with headquarters located in Gauteng province participated in semi-structured interviews.
MAIN FINDINGS: The findings indicate a juxtaposition regarding South African 3PL supply chain practitioners' understanding of SCRM compared to literature, as the participants were found to only identify certain tenets of SCRM with no single participant comprehensively describing SCRM according to the literature. External disruptions, namely customer- and supply-side disruptions within the South African 3PL industry were found to be the primary sources of supply chain disruptions. The findings further indicate that supply chain vulnerabilities emanate predominantly from labour strikes and cyberattacks
PRACTICAL/MANAGERIAL IMPLICATIONS: The implementation of SCRM is constrained by the high costs of implementation, the unwillingness of supply chain partners to buy into SCRM, power imbalances in supply chain relationships and other uncontrollable factors between different supply chain members.
CONTRIBUTION/VALUE-ADD: Supply chain practitioners in the 3PL industry should realise the significance of effective SCRM practices, as well as the positive impact proactive SCRM practices could have on their organisations as well as on supply chain partners.
Introduction and problem statement
As organisations seek to improve and strengthen their supply chains to be more effective and efficient, their actions may also result in more vulnerability towards risks and disruptions (Ho et al. 2015:5047; Jüttner 2005:121). Disruptions will happen; it is a matter of when it will happen (Agigi, Niemann & Kotzé 2016:1; Pettersen & Asbjørnslett 2016:4). As a result, supply chain risk management (SCRM) has become a critical concern for organisations (Asian & Nie 2014:1136; Costantino et al. 2014:4; Kakabadse & Khan 2016:1; Kilubi 2016a:663; Trkman, Oliveira & McCormack 2016:1061). Supply chain risk management is defined by Jüttner (2005:124) as 'the identification and management of risk for the supply chain, through a coordinated approach among supply chain members, to reduce supply chain vulnerability as a whole' (Ho et al. 2015:5036; Lavastre, Gunasekaran & Spalanzani 2014:3384). Supply chain vulnerability can be explained as exposure to primary disruptions that occur from supply chain risks and, as a result, influence the supply chain's capability to successfully attend to the target market (Jüttner 2005:124; König & Spinler 2016:127; Kurniawan et al. 2017:6). A supply chain disruption is an event that causes a disruption or inhibits the flow of goods, or services, within a supply chain (Ambulkar, Blackhurst & Grawe 2015:111; Bode & Wagner 2015:216; Costantino et al. 2014:5; Kim, Chen & Linderman 2015:44).
Literature accentuates the importance for organisations to understand what is implied by SCRM, disruptions and vulnerabilities, as well as the impact it may have on the organisation (Ho et al. 2015:5036; König & Spinler 2016:127; Oke & Gopalakrishnan 2009:168; Sodhi, Son & Tang 2012:2). Scholten and Schilder (2015:471) state that even though collaboration, integration and information sharing between organisations are core tenets of SCRM, the available literature lacks empirical insights beyond focal organisation's analysis regarding SCRM. Furthermore, organisations tend to focus on internal countermeasures used to mitigate supply chain disruptions, instead of investigating key supply chain partners, such as third-party logistics service providers (3PLs) to assist with SCRM (Marley, Ward & Hill 2014:143).
Third-party logistics service providers can be defined as the supply chain partners who move and/or store goods through the supply chain, from point of origin to point of consumption, on behalf of shippers or sellers and customers or buyers (Grant et al. 2014:214). As 3PLs are responsible for handling the movement of goods and information between multiple members of the supply chain, they play a vital role in the collaboration, integration and information sharing between supply chain partners (Zhang & Okoroafo 2015:40). One of the top reasons for establishing strong relationships with 3PLs is to mitigate supply chain risks (Langley 2012:26). As a result, enhanced partnerships between an organisation and their 3PLs may enable the organisation to become more resilient to supply chain risk and thereby enhance SCRM (Zhang & Okoroafo 2015:39). Third-party logistics service providers therefore have an important involvement in the implementation of effective SCRM initiatives. The logistics industry constitutes 11.8% of South Africa's gross domestic product (Stellenbosch University 2016), which emphasises the significant impact of the 3PL industry in the South African economy. This study therefore centres on 3PLs as many disruptions might occur during logistics outsourcing (Klibi, Martel & Guitouni 2010:287).
Supply chain risk management is still a relatively new and evolving topic of study and has drawn substantial attention in recent times (Ho et al. 2015:5033; Prakash, Soni & Rathore 2017:75). Supply chain risk management studies often entail theory construction, rather than theory verification (Jüttner 2005:139; Prakash et al. 2017:78). The extent of research conducted on SCRM in developing countries, such as South Africa, is scant compared to research conducted in developed countries (Prakash et al. 2017:78). Furthermore, the majority of the SCRM research is conducted using quantitative research methodologies, with limited studies being qualitative, according to Ho et al. (2015:5052). This study therefore responds to calls for qualitative research within the 3PL industry (Selviaridis & Spring 2007:141; Wu et al. 2017:219).
The purpose of this generic qualitative study was threefold, namely to (1) determine whether there is a clear understanding of SCRM within the South African 3PL industry; (2) investigate the primary sources that lead to disruptions and vulnerabilities within the supply chains of South African 3PL organisations; and (3) establish the current tools or methods used by supply chain practitioners to mitigate supply chain risks within the 3PL industry in South Africa.
The following research questions guided the study:
-
How do South African 3PL supply chain practitioners understand the concept of SCRM?
-
What are the perceived sources of supply chain disruptions within the South African 3PL industry?
-
What are the perceived sources of supply chain vulnerabilities within the South African 3PL industry?
-
What practices are currently used to mitigate supply chain risks within the South Africa 3PL industry?
-
What are the constraints 3PLs experience when implementing SCRM?
This study contributes to the current body of knowledge on SCRM by exploring the supply chain practitioners' understanding of SCRM in the 3PL industry, more specifically in a developing country such as South Africa. The study identifies the contemporary supply chain risks experienced by 3PL organisations within South Africa. Academics and practitioners gain insight into the industry-specific sources of supply chain disruptions, vulnerabilities, mitigation efforts and constraints. The findings of the study can assist practitioners to develop appropriate context-specific SCRM strategies to mitigate against supply chain disruptions and vulnerabilities.
The article is structured as follows. Firstly, the literature review discusses SCRM, supply chain disruptions, supply chain vulnerabilities and supply chain risk mitigation strategies. Secondly, the research strategy and methods are described. Thirdly, the findings are presented. Lastly, the study's contributions, implications (both theoretically and managerial), limitations and suggestions for future research are discussed.
Literature review
Supply chain risk management
Supply chain risk management is a strategic process to address supply chain-specific risks that may occur within an organisation's supply chain (Kilubi 2016a:662). Two major strategies utilised to prevent supply chain risks include reactive and proactive approaches (Grötsch, Blome & Schleper 2013:2842). Reactive SCRM is when actions are implemented after the events have happened (Grötsch et al. 2013:2842; Olsson & De Verdier 2017:2), while proactive SCRM requires planning by identifying possible supply chain losses, determining the probability that it could occur and establishing strong countermeasures to address risks before they occur (Grötsch et al. 2013:2842). Implementing action plans and preparing in advance ensures a swift response when a crisis occurs. Consequently, damage can be minimised when managing safety stocks and redundancies proactively (Grötsch et al. 2013:2842). To ensure that organisations successfully operate on a global level, it is imperative to have a clear understanding of SCRM and to use this strategic process as a competitive advantage (Trkman et al. 2016:1062).
Sources of supply chain risks
The literature shows that supply chain risks emerge from the following three sources of risk, namely supplier risk, internal risk and customer risk as shown in Figure 1 (Habermann, Blackhurst & Metcalf 2015:493; Wagner & Silveira-Camargos 2012:54).
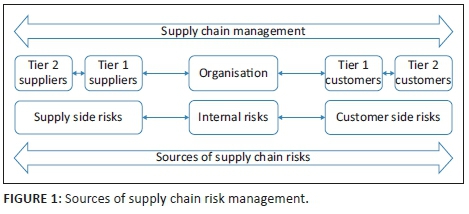
Supply-side risks are defined as any disruption that occurs on the supplier, or inbound side, of the supply chain (Kilubi 2016b:614). The supply-side complexity comprises three dimensions (Bode & Wagner 2015:218; Wagner & Silveira-Camargos 2012:54). The first dimension is horizontal complexity, which is determined by the first-tier suppliers. This complexity directly impacts manufacturing operations, even though they have a shorter reaction time for deliveries. The buyer is also subjected to risks because if one member in the chain does not adhere to their side of the agreement, it will cause a delay in the entire manufacturing process. During a disturbance, a minor rework or an entire operation stoppage could occur (Bode & Wagner 2015:218; Wagner & Silveira-Camargos 2012:54).
The second dimension comprises vertical complexity. The problem is a lack of transparency among the buyers, which could become a potential risk, especially when filter mapping among the tiers becomes problematic (Bode & Wagner 2015:218; Wagner & Silveira-Camargos 2012:54). The third dimension is spatial complexity, which is defined as the distance between first-tier suppliers and their manufacturing sites (Bode & Wagner 2015:218; Wagner & Silveira-Camargos 2012:54). It can be concluded that the smaller the distance between the supplier and buyer, the smaller the risk for the buyer. Sourcing globally (suppliers across borders) therefore, increases the vulnerability of the risks from the supply side (Bode & Wagner 2015:218; Wagner & Silveira-Camargos 2012:54).
Internal disruptions occur within an organisation's facilities (Kırılmaz & Erol 2017:56). The primary disruption driver is the lack of organisational discipline (Wagner & Silveira-Camargos 2012:55). Employee discipline within an organisation is significantly important when wanting to implement lean production systems because of decentralised decision making (Agigi et al. 2016:5; Wagner & Silveira-Camargos 2012:55). Delegating tasks to inexperienced employees within the related field simultaneously increases the responsibility of each. Discipline is therefore essential, as minor mistakes can lead to major interruptions in the manufacturing process (Wagner & Silveira-Camargos 2012:55).
Customer-side risks arise from the customer or outbound side of the organisation (Habermann et al. 2015:495; Kilubi 2016b:614). Examples of customer-side risks are pioneer products, organisational reputation risks, product shortages or recalled products (Kilubi 2016b:614). Two major drivers of risk arise from customers, namely configuration flexibility and abrupt volume oscillations (Wagner & Silveira-Camargos 2012:55). Configuration flexibility refers to the extent to which customers are allowed to adjust their request within 14 days before production commences (Obayi et al. 2017:344). This implies that the supply base needs to be responsive to these configurations within the short period to effect necessary changes and deliver the product timeously to avoid the supply chain becoming more vulnerable (Wagner & Silveira-Camargos 2012:55). Volume oscillations could become a potential risk in different ways (Purvis, Gosling & Naim 2014:105) because all the parties within a supply chain network are interrelated.
Supply chain disruptions
The complexity of an organisation's operations provides a foundation for its supply chain to become more susceptible to disruptions that, if not managed correctly, can lead to great loss of turnover and profit (Ambulkar et al. 2015:111; Asian & Nie 2014:1139; Foulds 2015:24). Disruptive events delay or prevent supply processes for a period and cause decreased profitability and share value, which negatively impact on investor relations (Asian & Nie 2014:1139). Disruptive events can thus be seen as a realised supply chain risk (Habermann et al. 2015:494).
The impact of the disruption is measured in the length of time it takes to mitigate the disruption and its frequency (Christopher & Holweg 2017:15; Habermann et al. 2015:494). Supply chain disruption problems are interrelated, implying that, if one disruption occurs, it could cause a chain reaction (Habermann et al. 2015:494). Disruptions mostly stem from the external environment and can be from the supplier side or customer side of the supply chain. However, supply chain disruptions can also stem from within the organisation itself (Costantino et al. 2014:3; Prakash et al. 2017:80).
Disruptive events are categorised by Ho, Li and Holloway (2013:98) as natural events (storms, floods or earthquakes), transportation disruptions (road closures and closed bridges), accidents (such as equipment failures, fires and power outages) and man-made events (considered as terrorism, labour strikes, wars and bankrupt suppliers). Examples of additional supply chain-related events are categorised as supply disruptions (late shipments from suppliers which consists of inbound materials), logistical disruptions (truck drivers who were to pick up the products later than arranged), internal disruptions (machine breakdowns) and hazards (includes illegal reuse and sterilisation of products that were only meant to be used once, introducing a potential hazard) (Ambulkar et al. 2015:116).
Resilience is defined as the ability of an organisation to withstand or absorb the impact of a disruptive event without altering the supply chain mission, therefore by not preventing the event, but rather facing the consequences (Agigi et al. 2016:2; Berle, Norstad & Asbjørnslett 2013:254). This implies that a supply chain will turn back to its original state after being disrupted. However, by implementing resilience and robustness, mitigation of potential threats can be ensured (Brandon-Jones et al. 2014:58). Brandon-Jones et al. (2014:55) provide empirical evidence that the visibility of a supply chain acts as the origin of resilience. Supply chain visibility refers to the ability to get access to viable (timely, accurate and purposeful) information, which provides a sound description of supply and demand (Williams et al. 2013:545; Yu & Goh 2014:125).
Supply chain vulnerabilities
As the complexity of an organisation's supply chain increases for it to remain competitive, the risks increase (Vilko, Ritala & Edelmann 2014:3). This leads to vulnerabilities in the flow of interconnected information, funds and materials within the organisation (Bode & Wagner 2015:216; Habermann et al. 2015:493). An organisation's supply chains tend to be more vulnerable to the effect of external disruptions over which practitioners have no control, for example, natural disasters (Costantino et al. 2014:3; Prakash et al. 2017:80).
Vulnerabilities can be mitigated by implementing one of two strategies. Firstly, Berle et al. (2013:257) recommend making use of robustness, which refers to supply chains that build resistance against any threat without making use of excess resources. Secondly, Berle et al. (2013:257) recommend reconfiguring the available resources through implementing flexibility. Encouraging collaborative partnerships enables supply chain flexibility, enhances visibility across supply chains and improves the relationship between supply chain members (Hsu et al. 2013:165; Kilubi 2016b:615; Kurniawan et al. 2017:3). This indicates that collaborative partnerships between supply chain members enable practitioners to generate alternatives to effectively respond to a disturbance (Lavastre et al. 2014:3382).
Previous research has generated different strategies that can be used to mitigate vulnerabilities. These strategies include supply chain flexibility and visibility, inventory control and the supplier development (Kurniawan et al. 2017:7). Supply chain flexibility allows practitioners to predict uncontrollable factors arising internally or externally to the organisation's supply chain (Kurniawan et al. 2017:8; Shao & Dong 2012:202). The flexibility of a supply chain enables the organisation to become more efficient and competitive, which simultaneously decreases the vulnerability of a supply chain (Christopher & Holweg 2017:15; Kurniawan et al. 2017:8). Supply chain visibility is essential because it enables customers and suppliers to access information about the organisation (Brandon-Jones et al. 2014:55).
Without proper visibility, uncertainty can arise from suppliers or customers. This can eventually lead to a chain of reactions and result in the supply chain becoming ineffective. Inventory control as a vulnerability mitigation strategy is important because it addresses inventory cost reduction (decrease inventory holding costs), enables better adaptation to demand fluctuations and enables the organisation to have a quicker response to consumer demands (Kurniawan et al. 2017:8). Supplier development enables the organisation to increase value-added activities; it enables the manufacturers to respond more effectively to consumer demands and enables better use of their resources (Kurniawan et al. 2017:8).
Supply chain risk management mitigation
Lavastre et al. (2014:3396) identified various risk mitigation methods. These methods are grouped into four categories. The first category is the management of information flows (Brandon-Jones et al. 2014:55). The subcategories of information flow management are: (1) exchange and cooperation on forecasts with a specific partner; (2) information and communication exchange; (3) collaborative information systems; (4) accurate exchange forecasts; (5) centralised decision making; (6) implementing an advanced planning system to conduct activity planning; (7) the supply chain management should be reactive and responsive and (8) a risk manager specialised in supply chain management should be appointed (Grötsch et al. 2013:2842).
The second category that Lavastre et al. (2014:3396) identified is targeting physical flows (Bode & Wagner 2015:215). The subcategories comprise (1) external security stock owned by the vendor; (2) internal security stock; (3) dual manufacturing or dual sourcing; and (4) centralised production, stocks and distribution (Shao & Dong 2012:202). The third category is to establish an industrial relationship with partners (Lavastre et al. 2014:3396). The subcategories of an industrial relationship with partners include (1) assistance to suppliers towards performance improvement; (2) continuity in relation with the partners to ensure longevity; (3) ensuring geographical proximity of the partners; (4) introduction of strict and formal procedures that should be consistently respected; (5) cultural proximity to partners; (6) rewards if there were no forms of misconduct or faults; (7) penalties and sanctions for faults or misconduct; (8) fewer suppliers used; and (9) the presence of a focal firm that conducts the coordination of the supply chain (Kurniawan et al. 2017:6). The fourth category is monitoring the relationships and risks (Lavastre et al. 2014:3396). Monitoring relationships and risks subcategories include (1) establishing indicators for monitoring the evolution of risk without the presence of the partners; (2) establishing indicators to jointly monitor the risk associated with the specific partners; and (3) establishing indicators to measure SCRM effectiveness (Grötsch et al. 2013:2843; Habermann et al. 2015:494).
Methodology
Research design
A descriptive qualitative research design was adopted. The reason therefore is that it was the most appropriate design to address the research questions, as it examines the views, understandings, perceptions or opinions of people relating to their own understanding of incidents in the external environment (Caelli, Ray & Mill 2003:2; Sandelowski 2000:335). The nature of the research aims to examine the views, understanding, perceptions or opinions of specific individuals relating to incidents in the external environment (Percy, Kostere & Kostere 2015:78). The current research also aims to address this gap by responding to the 'why' and the 'how' questions associated with qualitative research and contribute towards the body of knowledge relevant to SCRM research. Descriptive qualitative research is conducted by investigating multiple participants' perspectives through semi-structured interviews. The primary objective of descriptive qualitative research is to generate in-depth and detailed descriptions of what the candidates have experienced regarding a particular phenomenon at a specific point in time (Percy et al. 2015:78). This is applicable to the current research as the findings by Prakash et al. (2017:78) state that the knowledge gap is rather in theory constructing than theory verification in the SCRM research.
Sampling
The units of analysis for the study was supply chain practitioners within the South African 3PL industry. All the participating organisations have regional offices in Gauteng. A total of 20 3PL organisations participated in the study and one supply chain practitioner from each organisation was interviewed. Inclusion criteria were set to ensure that the researchers obtain high-quality, credible data. The criteria included that the participants had to have at least 3 years industry-specific experience and occupy a middle- to a senior-management role within their respective organisations. The rationale behind this inclusion criteria is that participants with sufficient work experience and more senior roles can give more credible data from their experience. The interviewed supply chain practitioners' positions typically comprised the chief operating officer, managing director, procurement managers, operations managers, logistics managers and other supply chain-specific related managers. No specific age or gender requirements were stipulated. The primary focus was on the participants' experience and position within the 3PL industry. When referring to organisations' perspectives, it is most appropriate to apply a homogenous sampling method, more specifically, purposive sampling strategy (Plano Clark & Creswell 2015:334; Polit & Beck 2012:518). This sampling method was the most appropriate for this study because it enabled the researchers to purposefully select the 3PL organisations and eliminate those that are not relevant to the research. Table 1 provides additional information on the profiles of the participants who were interviewed.
Data collection
Data were collected by conducting semi-structured, face-to-face in-depth interviews. Semi-structured interviews allow researchers to gather a deeper insight about the phenomenon or explore the attitudes, facts, processes, experiences, predictions or behaviours of participants (Cooper & Schindler 2014:153; Rowley 2012:260). A pretest was conducted with a participant who met all the inclusion criteria to ensure that the discussion guide was in an open-ended, conversational tone. The participant included in the pretest was also included in the main study because no major changes to the discussion guide were required. Only one of the 20 semi-structured interviews was conducted telephonically as a result of geographical constraints, while the rest were conducted at the participants' offices. One telephone interview was conducted because the participant was not available at the Gauteng offices during the data collection period. Literature states that when three consecutive interviews do not generate any new information, data saturation may likely be reached (Charmaz 2006:113; Francis et al. 2010:1234). All codes were generated after the 17th interview because no new themes emerged. The researchers conducted three additional interviews and then concluded the data collection process.
Data analysis
Thematic analysis was used to analyse the data. Thematic analysis is used to describe responses that form a pattern, whereby codes are features that relate to the respective study's research questions (Braun & Clarke 2012:60). Coding was used to categorise groups, families, themes and codes (Creswell 2012:236-253). Themes and codes were identified as interviews and data collection progressed. Clearly defined themes and codes started to appear after the 12th interview. All researchers were independently involved in the coding process in an alternating manner to corroborate each other's analysis of the data continuously. All interviews were recorded on a digital recording device. The recordings were sent to a professional transcription service provider on completion. Upon receiving the completed transcripts, the transcripts were compared to the actual recordings, and any necessary changes were made to ensure a verbatim account of the interviews that took place. The length of the interviews varied from 25 to 62 min, the average being 35 min. The specific details recorded for each interview are presented in Table 1.
Trustworthiness
For a research study to acquire trustworthiness, one should ensure confirmability, transferability, credibility and dependability (Polit & Beck 2012:585; Shenton 2004:64). This was done by including a rich description of the participants, methodology and sites and context as to ensure the transferability and authenticity of the research. Additionally, the findings of the analysed data were compared to the literature review. Triangulation was used to authenticate the responses. The researchers worked together to search for a correlation between the data collected and the literature (Polit & Beck 2012:588). The participants were informed that the information acquired from the interview would be kept strictly confidential and that there are no right or wrong answers. This improved the credibility of the study in that the responses of the participants were considered to be honest and true (Shenton 2004:66). Dependability was strengthened by following an established qualitative research design, as well as in the manner in which the interviews were conducted and how the data were analysed. Academic experts in the field of supply chain management were consulted throughout the research process to ensure that all reliability issues were timeously identified and corrected (Creswell 2007:208; Polit & Beck 2012:594).
Ethical considerations
The research was approved by the relevant research ethics committee at the University of Pretoria (ethical clearance number: 14031796/13029348/2017) before data collection commenced. A letter of consent was provided to all organisations and signed by every participant. This was done to ensure that the participants were aware that all information will be kept confidential and that participation in the research was completely voluntary. Pseudonyms (refer to Table 1) were provided for each participant, organisation and any other customer or supplier mentioned during the interview to ensure confidentiality.
Findings
Five themes were identified and extracted from the collected data. The themes included disruptions; vulnerabilities; mitigation methods, SCRM implementation constraints and SCRM intent. Each one of the themes has related sub-themes. Each of the primary themes and sub-themes were reviewed and a relevant quotation(s), as provided by the participants, were highlighted to compare their input with the literature. Figure 2 provides a summarised overview of the themes, sub-themes and frequencies related to the findings during data analysis.
Supply chain practitioners' understanding of supply chain risk management
As stated in the literature review, SCRM is defined by Jüttner (2005:124) as 'the identification and management of risk for the supply chain, through a coordinated approach among supply chain members, to reduce supply chain vulnerability' (Ho et al. 2015:5036; Lavastre et al. 2014:3384). Table 2 indicates the different tenets, as mentioned by the participants regarding their understanding of SCRM. The findings reveal that supply chain practitioners only mentioned the tenets of SCRM, with no single participant comprehensively describing SCRM according to the literature. Interestingly, the findings also revealed that only two participants mentioned the need to make an assessment of a supply chain risk, and only one participant indicated that SCRM is a collaborative effort between supply chain members in their specific supply chain. Based on these findings, it is evident that there is no clear or unified understanding of SCRM between South African 3PL supply chain practitioners.
Sources of supply chain disruptions
During the research process, it was evident that the participants were unable to distinguish between risks and disruptions. They stated that they understood the two concepts as having the same meaning. The three sources of disruptions were classified as customer-, internal- and supplier-related. A total of 16 of the 20 participants perceived that the supplier was responsible for the disruptions.
'So it will be a failure to procure goods and services on time due to a failure from the actual vendor or supplier to provide those goods.' (P13, Male, Campus Manager)
'So unfortunately for us, we've got a large number of suppliers that we rely on, and that then does make it a lot more difficult to manage those risks and mitigate them.' (P16, Male, Managing Director)
Internal disruptions occur within the boundaries of an organisation (Habermann et al. 2015:495). Thirteen of the 20 participants revealed that the disruptions originated internally within their organisations. However, this source of disruption was considered the least-mentioned source of disruption by the majority of the participants.
'Look, if there's insufficient training, then you're destined to fail because the mistake level or the error level causes non-compliance and that's where the problem kicks in.' (P15, Male, National Customs Manager)
'So we can still deal with internal disruptions. I think those are more manageable. But as soon as we start negatively impacting our client's operations that are deemed as a major disruption in our world.' (P3, Female, Commercial Executive)
Customer disruptions arise from the customers or the outbound side of the organisation (Habermann et al. 2015:495; Kilubi 2016b:614). All participants revealed that they experience disruptions stemming from the customer's segment of the supply chain.
'The business is fraught with customers who can't pay.' (P2, Male, Managing Director)
'That is a fact so unreliable forecasting from the client especially, and you know that the flow of information is critical in our operations.' (P13, Male, Campus Manager)
Sources of supply chain vulnerabilities
Most of the participants agreed that the disruptions mentioned corresponded to previous literature, such as those categorised by Ho et al. (2013:98), result in supply chain vulnerability. The sources of vulnerabilities are categorised into man-made, accidents, natural events and transportation disruptions. It is evident that man-made disruptions are a crucial concern for participants. The four causes of supply chain vulnerabilities categorised as man-made include crime and security, information technology communication (ITC), political and economic and socio-economic.
Crime and security include the theft, hijacking, fraud and/or corruption, and terrorist activities that influence an organisation's supply chain. Thirteen of the 20 participants revealed that crime and security are the major contributors towards supply chain vulnerability.
'The network is exposed to the criminal elements of the marketplace. So you would have syndicated crime, opportunistic crime….' (P12, Male, Group Supply Chain Executive)
'I had a pallet of laptops that got stolen out of the warehouse and were worth R250 000. Or there's a package that gets stolen out the warehouse; there's stock missing.' (P2, Male, Managing Director)
Information technology communication was identified as the second major concern. The primary concern that makes 19 of the 20 participant's organisations vulnerable is cyberattacks. One example is organisation 14, which was struck by a major cyberattack that had a massive impact on their ability to serve their end-customers. Consequently, the majority of the other organisations have become aware of the possible negative effect of cyberattacks on an organisation's supply chain.
'Lately there has been a lot of attacks on companies' IT systems … if your information can't flow your goods can't flow …' (P18, Male, Solutions Manager)
'I think the biggest disruption we see currently is IT because we are relying a lot more and more on IT so we have just been … one of our biggest partners O14 and they just got that huge cyber-attack.' (P20, Male, Sea Freight Director)
Sixteen of the 20 participants revealed that political and economic concerns result in serious vulnerability to their supply chain operations. Examples include political instability, economic instability and change in legislation.
'That could be a change in legislation or regulations, you know, I'm talking more on the physical, but these are also real threats to the business….' (P8, Male, Sub-Sahara Africa Operations Manager)
'Politics is another massive disruption because politics affects exchange rates which obviously our whole business is based on the rand/dollar exchange rate.' (P2, Male, Managing Director)
Lastly, all 20 participants revealed that socio-economic factors such as labour unrest are the key sources of vulnerabilities.
'…labour strikes are normally a big thing, simply because it's one of the most difficult things to manage when and if it happens.' (P17, Male, Senior Solutions Developer)
'So risk that we have experienced, we could all talk about labour unrest. So that's probably our biggest risk.' (P3, Female, Commercial Executive)
Nineteen of the 20 participants revealed that accidents, whether on the road or internal to the organisation are the major reason why their organisation's supply chain becomes vulnerable. Examples include transportation accidents, failure of activities requiring electricity and mechanical breakdowns.
'Accidents are always a problem. Remember we are doing 2.4 million kilometres a month and so we've got huge exposure.' (P11, Male, Operations Manager)
'Somewhere on the route a truck is in an accident, and the goods are damaged.' (P19, Male, General Manager)
The participants also indicated that natural phenomena play a significant role in the vulnerability of their organisation's supply chain. This includes forces that are beyond the control of humans, such as natural disasters that include flooding.
'Other than that it will be, you know risk or the things that are outside of our control like natural disasters that will affect your ability to supply the services that you need to keep the supply chain going.' (P13, Male, Campus Manager)
'You can't control if Durban's harbour gets wind-bound and the ship is sitting out at sea for three days.' (P6, Male, Supply Chain Director)
Eighteen of the 20 participants revealed that concerns related to infrastructure for transportation play a significant role in the vulnerability of an organisation's supply chain. Examples of such concerns include fuel shortages, the lack of infrastructure and road closures, among others.
'…the supply of fuel is critical for our principals and for us. Because if our vehicles don't move, if the tyre's hit … if the tyre is not on top of tar, we don't make money.' (P3, Female, Commercial Executive)
'…the infrastructure is virtually non-existent, and your vehicles take a heavy pounding and your breakdowns on the vehicles increase….' (P13, Male, Campus Manager)
Mitigation methods of supply chain risks
The following four primary methods were suggested by the participants to mitigate the mentioned disruption(s):
Participants indicated four primary approaches that may be employed in mitigating the mentioned supply chain disruptions. These four approaches are collaborative planning, forecasting and replenishment (CPFR); long-term relationships; information systems; and internal business processes. During the interviews, all the participants elucidated that CPFR is an essential mitigation method. The majority of the examples participants provided fall under the CPFR approach. These examples include clear communication and collaboration between parties, visibility of operations and transparency.
'And the other thing for us is to have good flows of communication. So literally having that relationship where the customer was seen as a partner rather than just the service provider…' (P16, Male, Managing Director)
'So I think part of it was the BCP [Business Continuity Planning] discussion. And on a quarterly basis, we will review all risks, and we then determine whether alternative suppliers are available….' (P3, Female, Commercial Executive)
Acquiring and maintaining a healthy long-term relationship with supply chain partners was highlighted by 12 of the 20 participants. These long-term relationships enable supply chain partners to develop a better understanding of the emergence of uncontrollable disruptions.
'If you have a good relationship with someone, they tend to be more tolerable and more understanding of an event as opposed to if you don't.' (P3, Female, Commercial Executive)
'And the other thing for us is to have good flows of communication. So literally having that relationship where the customer is seen as a partner rather than just the service provider….' (P13, Male, Campus Manager)
The purpose of information systems is to improve the exchange of information throughout the supply chain. With increasing cyberattacks and the significant effect that it has on their operations, 16 of the 20 participants revealed that it is essential to implement sound information systems; for example, IT Security, IT integration platforms, Closed Circuit Television (CCTV) cameras, IT specialist intake and tracking systems.
'So obviously when we saw those cyber-attacks coming, we had an organisation, we actually … I think this week we're looking at their presentation we invite hackers onto our system, they've been playing around with our system and they're doing a presentation this week on what they've been able to do with our system and what information they've been able to steal.' (P20, Male, Sea Freight Director)
'…in terms of monitoring the vehicles, monitoring the warehouses, cameras, CCTV, that kind of, those are all tools as well.' (P9, Male, Chief Operational Officer)
Seventeen of the 20 participants revealed that the major internal business processes to mitigate risks are business continuity plans (BCP) and standard operating procedures (SOP). BCPs are plans set up to ensure that operations do not come to a standstill. SOPs are procedures that are implemented when a supply chain risk occurs. Internal business processes refer to any strategies, generated internally, that are used to mitigate supply chain risks. These procedures are constructed through previous experiences and take cognisance of other organisations' pitfalls.
'…we have been done in our BCP on this facility alone says that we will be back at 20, between 20 and 40% capacity in a matter of 10 days.' (P13, Male, Campus Manager)
'…you then still have an ultimate plan B or a backup plan to be able to mitigate the risk, that is a part of the business.' (P9, Male, Chief Operational Officer)
Supply chain risk management implementation constraints
The high cost that is incurred by implementing a comprehensive SCRM strategy is a constraint some of the participants experience. Five of the 20 respondents indicated that the high cost of implementing a SCRM strategy is a constraint. One of the major issues with implementing SCRM methods and its related high cost is because of supply chain complexity.
'…so again there are various ways that you can mitigate that risk, but that comes at a cost.' (P19, Male, General Manager)
Seventeen of the 20 participants revealed that the unwillingness of supply chain partners to buy into SCRM makes it difficult to implement SCRM strategies. This occurrence could be customer-, internal- and supplier-related. This also includes being resistant to the changes required to implement SCRM.
'But again, the skillset of our customers regarding logistics is, it's a huge problem…. Every time that something has gone wrong or has been disrupted, and it's not through, like an organised strike or organised theft or something like that, it's been where compliance has been neglected.' (P20, Male, Sea Freight Director)
Seventeen of the 20 respondents stated that the parties within supply chains are not receptive towards implementing SCRM strategies, because most of the responsibilities are transferred to the service provider (3PL). They ignore considering a strategic relationship and are only concerned with the expected service. The customers pay for the service provided. Therefore, it is assumed that they have more power, which indicates evident power asymmetry. This finding is consistent with the results of a research conducted by Meyer, Niemann and Kotzé (2017:3) regarding power asymmetry between buyers and suppliers of logistics services.
'But unfortunately customers don't care. They don't worry about anything. They need their product because they need to sell it.' (P2, Male, Managing Director)
'So it's one of those situations where as much as we try and work with them, we are a cork on the ocean. We are at their mercy. If they don't want to perform, they don't perform. You have agreements in place, you have all sorts of things in place, but at the end of the day, if you don't have somewhere else to go to, you're kind of tied down to them. So it's a big issue.' (P16, Male, Managing Director)
Sixteen of the 20 participants revealed that the presence of uncontrollable factors is one of the leading constraints to implementing SCRM methods. These are events that the supply chain managers have no control over.
'…problem for us in this industry is there's a lot of things that are beyond our control.' (P10, Male, Sales Executive)
'We've got that kind of risks which sometimes we've got absolutely no control over, yet they influence us.' (P16, Male, Managing Director)
Supply chain risk management intent
In the course of data collection and analysis, an additional theme emerged, namely SCRM intent. The researchers analysed the intent of the participants towards mitigating disruptions, which was coded as either being 'proactive' or 'reactive'. Proactive SCRM is the implementation of measures to mitigate disruptions before they occur (Grötsch et al. 2013:2842). Reactive SCRM refers to actions that are implemented after an emerging disruption has occured (Grötsch et al. 2013:2842; Olsson & De Verdier 2017:2). The findings revealed that 13 of 20 most participants use a proactive approach, while the other participants highlighted that they react to disruptions as they occur.
'Extremely proactive…. So, we'll have meetings, and as soon as there's a risk identified, then there is a responsible person, a plan of action, etcetera, to mitigate that risk.' (P6, Male, Supply Chain Director)
'Honestly, most of the time we're not. When it happens, it's like, you know, make a plan and figure out how to resolve it and only then….' (P7, Male, Head of Supply Chain Innovation)
'I think it's a difficult one to answer because the right answer would be to say it's a proactive approach, but I think that we still get caught short….' (P20, Male, Sea Freight Director)
Conclusion
Summary of the results
The purpose of this research was threefold, namely to (1) determine whether there is a clear understanding of SCRM within the South African 3PL industry; (2) determine the sources of disruptions and vulnerabilities within the South African 3PL industry; and (3) establish which methods participants implement to mitigate supply chain risks within the South African 3PL industry.
In answering its first research question, the study revealed that there is no standard shared understanding of SCRM among the participants. From the tenets mentioned in the SCRM definition by Jüttner (2005:124), all participants mentioned at least one tenet. The tenets that were highlighted the most by the participants were the mitigation of supply chain risks and the vulnerabilities that organisations experience within the South African 3PL industry. This correlates with existing literature that claims there is no clear consensus or standard definition of SCRM (Heckmann, Comes & Nickel 2015:121; Sodhi et al. 2012:2).
In considering the second research question pointing to supply chain disruptions within the South African 3PL industry, it was evident that the causes of disruptions primarily originate from external sources, especially either the supplier or customer side of the supply chain. This corresponds to the literature stating that organisations' supply chains tend to be more vulnerable to external disruptions (Costantino et al. 2014:3; Nel, de Goede & Niemann 2017:10; Prakash et al. 2017:80).
The third research question aimed to identify the sources of supply chain vulnerabilities within the South African 3PL industry. The results revealed that the leading sources of vulnerabilities arise from one of three causes, namely strikes, cyberattacks and accidents. The analysis of data indicated that the frequency of these events has increased over the past few years, making supply chains vulnerable. This finding is in line with previous literature, which showed that organisations tend to be more vulnerable to supply chain risks over which they have no control (Costantino et al. 2014:3; Prakash et al. 2017:80).
The fourth research question aimed to determine the mitigation methods used by supply chain practitioners to minimise the potential impact of supply chain risks on the South African 3PL industry. The findings of the study show that practitioners mostly use CPFR and internally generated processes to mitigate supply chain risks. Communication and transparency are the two primary drivers to the implementation of CPFR. When using internal business processes as a mitigation method, it was evident that the implementation of SOPs and BCPs were the key drivers. Throughout the interviews, specific themes such as disruptions, vulnerabilities, mitigation methods, SCRM constraints and SCRM intent emerged that specifically refer to the organisations' intention towards SCRM. An analysis revealed that organisations implement different processes to prevent or mitigate disruptions.
The fifth research question aimed to determine the constraints faced by supply chain practitioners within the South African 3PL industry when implementing SCRM. The results revealed that the high cost that is incurred by implementing a comprehensive SCRM strategy and the unwillingness of supply chain partners to buy into SCRM makes it difficult to implement SCRM strategies. Client firms and parties within the supply chain are not receptive towards implementing SCRM strategies because most of the responsibilities are transferred to the 3PL. Furthermore, the power balance that certain supply chain (SC) parties have over the other influences the organisations' ability to implement SCRM successfully.
Theoretical implications
The findings of this study revealed that each participant's understanding of SCRM varied, which corroborates the literature which states that there is no standard grasp of the concept (Heckmann et al. 2015:120; König & Spinler 2016:127). It was evident throughout the interviews that the participants found it difficult to distinguish between supply chain risks and supply chain disruptions. This problem was also noted by Habermann et al. (2015:494), who asserted that disruptive events could be perceived as a realised supply chain risk. Consequently, the same sources of supply chain risks such as customer-, internal- and supplier risks were identified under the supply chain disruption themes. These sources of disruptions are less apparent from an internal perspective, which correlates with the literature in that supply chain disruptions are less evident from an internal environment perspective (Costantino et al. 2014:3; Prakash et al. 2017:80).
It is apparent in the literature that vulnerabilities can emanate from various sources. However, certain sources of vulnerabilities tend to arise more than others. It was evident in the research that sources of vulnerabilities experienced by the participants, such as cyberattacks and strikes, are more frequent than others. The nature of these vulnerabilities correlates with literature. However, this research emphasised those sources of vulnerabilities that were most prevalent (Ho et al. 2013:98).
The mitigation methods used by the participants were evident as being mostly CPFR and internal business processes. The CPFR and internal business process are implemented in organisations to promote supply chain visibility and flexibility throughout the whole supply chain. These findings relate to the literature, which revealed that improving supply chain visibility and flexibility assists organisations in mitigating supply chain risks (Kurniawan et al. 2017:8; Shao & Dong 2012:202). Considering the constraints experienced by practitioners while implementing SCRM within the South African 3PL industry, it was evident that three constraints were most frequently identified, namely non-compliance, power asymmetry and uncontrollable risks.
Managerial implications
Managers in the 3PL logistics industry should not underestimate the significance of SCRM and have to realise the positive impact that this strategic process could have on an organisation's supply chain. The ability of managers to better identify and assess possible supply chain disruptions could result in mitigating methods that will minimise the impact of these disruptions on the supply chain and protect the organisation against vulnerabilities. Supply chain vulnerabilities such as cyberattacks and strikes are some of the leading supply chain risks that practitioners should consider in their operations. This research may also provide further insight for organisations to create guidelines to identify, assess and mitigate potential sources of disruptions and vulnerabilities. It is recommended that supply chain practitioners should adopt a proactive intent towards SCRM. The Benjamin Franklin axiom that 'an ounce of prevention is worth a pound of cure' is as true today as it was when Franklin made the quote. By being proactive in identifying possible risks, it could help to predict supply chain risks before they occur. Furthermore, supply chain practitioners should realise the significance of information flow to identify, assess, as well as mitigate supply chain risks.
Limitations and recommendations for future research
The research focussed on the South African 3PL industry alone and therefore the findings might be limited to that specific industry and country. Furthermore, the study only explored the perspectives of the supply chain practitioners working in the 3PL industry. Future studies could include perspectives from client firms and other members of the supply chain. A quantitative study can be conducted to survey a larger sample of participants to assess the generalisability of the findings. This will allow a more holistic and illustrative perspective of SCRM among supply chain practitioners within South Africa.
An additional avenue for future research is to investigate and analyse contemporary or trending supply chain disruptions and vulnerabilities such as cyberattacks and strikes and the impact of these supply chain risks on organisations. Lastly, it would also be significant to conduct this study in other developing countries and compare the results from various geographical areas.
Acknowledgements
Competing interests
The authors declare that they have no financial or personal relationships that may have inappropriately influenced them in writing this article.
Authors' contributions
G.U. and D.B. conducted the research as part of their honours degree. A.M. and W.N. acted as the supervisors of the research and prepared the manuscript.
References
Agigi, A., Niemann, W. & Kotzé, T., 2016, 'Supply chain design approaches for supply chain resilience: A qualitative study of South African fast-moving consumer goods grocery manufacturers: Original research', Journal of Transport and Supply Chain Management 10(1), 1-15. https://doi.org/10.4102/jtscm.v10i1.253 [ Links ]
Ambulkar, S., Blackhurst, J. & Grawe, S., 2015, 'Firm's resilience to supply chain disruptions: Scale development and empirical examination', Journal of Operations Management 33, 111-122. https://doi.org/10.1016/j.jom.2014.11.002 [ Links ]
Asian, S. & Nie, X., 2014, 'Coordination in supply chains with uncertain demand and disruption risks: Existence, analysis, and insights', IEEE Transactions on Systems, Man, and Cybernetics: Systems 44(9), 1139-1154. https://doi.org/10.1109/TSMC.2014.2313121 [ Links ]
Berle, Ø., Norstad, I. & Asbjørnslett, B.E., 2013, 'Optimization, risk assessment and resilience in LNG transportation systems', Supply Chain Management: An International Journal 18(3), 253-264. https://doi.org/10.1108/SCM-03-2012-0109 [ Links ]
Bode, C. & Wagner, S.M., 2015, 'Structural drivers of upstream supply chain complexity and the frequency of supply chain disruptions', Journal of Operations Management 36, 215-228. https://doi.org/10.1016/j.jom.2014.12.004 [ Links ]
Brandon-Jones, E., Squire, B., Autry, C.W. & Petersen, K.J., 2014, 'A contingent resource-based perspective of supply chain resilience and robustness', Journal of Supply Chain Management 50(3), 55-73. https://doi.org/10.1111/jscm.12050 [ Links ]
Braun, V. & Clarke, V., 2012, 'Thematic analysis', in H. Cooper, P.M. Camic, D.L. Long, A.T. Panter, D. Rindskopf & K.J. Sher (eds.), APA handbook of research methods in psychology: Research designs: Quantitative, qualitative, neuropsychological, and biological, vol. 2, pp. 57-71, American Psychological Association, Washington, DC. [ Links ]
Caelli, K., Ray, L. & Mill, J., 2003, '"Clear as mud": Toward greater clarity in generic qualitative research', International Journal of Qualitative Methods 2(2), 1-13. https://doi.org/10.1177/160940690300200201 [ Links ]
Charmaz, K., 2006, Constructing grounded theory: A practical guide through qualitative analysis, Sage, Thousand Oaks, CA. [ Links ]
Christopher, M. & Holweg, M., 2017, 'Supply chain 2.0 revisited: A framework for managing volatility-induced risk in the supply chain', International Journal of Physical Distribution & Logistics Management 47(1), 2-17. https://doi.org/10.1108/IJPDLM-09-2016-0245 [ Links ]
Cooper, D.R. & Schindler, P.S., 2014, Business research methods, 12th edn., McGraw-Hill, Singapore. [ Links ]
Costantino, F., Di Gravio, G., Shaban, A. & Tronci, M., 2014, 'Replenishment policy based on information sharing to mitigate the severity of supply chain disruption', International Journal of Logistics Systems and Management 18(1), 3-23. https://doi.org/10.1504/IJLSM.2014.062119 [ Links ]
Creswell, J.W., 2007, Qualitative inquiry & research design: Choosing among five approaches, 2nd edn., Sage Publications, Thousand Oaks, CA. [ Links ]
Creswell, J.W., 2012, Educational research: Planning, conducting, and evaluating quantitative and qualitative research, 4th edn., Pearson, Boston, MA. [ Links ]
Foulds, S., 2015, 'Understanding supply chain capabilities: Supply chain logistics', Transport World Africa 13(1), 24-25. [ Links ]
Francis, J.J., Johnston, M., Robertson, C., Glidewell, L., Entwistle, V., Eccles, M.P. et al., 2010, 'What is an adequate sample size? Operationalising data saturation for theory-based interview studies', Psychology and Health 25(10), 1229-1245. https://doi.org/10.1080/08870440903194015 [ Links ]
Grant, D., Juga, J., Juntunen, J. & Juntunen, M., 2014, 'Investigating brand equity of third party service providers', Journal of Services Marketing 28(3), 214-222. https://doi.org/10.1108/JSM-06-2012-0104 [ Links ]
Grötsch, V.M., Blome, C. & Schleper, M.C., 2013, 'Antecedents of proactive supply chain risk management - A contingency theory perspective', International Journal of Production Research 51(10), 2842-2867. https://doi.org/10.1080/00207543.2012.746796 [ Links ]
Habermann, M., Blackhurst, J. & Metcalf, A.Y., 2015, 'Keep your friends close? Supply chain design and disruption risk', Decision Sciences 46(3), 491-526. https://doi.org/10.1111/deci.12138 [ Links ]
Heckmann, I., Comes, T. & Nickel, S., 2015, 'A critical review on supply chain risk - Definition, measure and modeling', Omega 52, 119-132. https://doi.org/10.1016/j.omega.2014.10.004 [ Links ]
Ho, W., Zheng, T., Yildiz, H. & Talluri, S., 2015, 'Supply chain risk management: A literature review', International Journal of Production Research 53(16), 5031-5069. https://doi.org/10.1080/00207543.2015.1030467 [ Links ]
Ho, Y., Li, J. & Holloway, L.E., 2013, 'Resilient control for serial manufacturing networks with advance notice of disruptions', IEEE Transactions on Systems, Man, and Cybernetics: Systems 43(1), 98-114. https://doi.org/10.1109/TSMCA.2012.2189879 [ Links ]
Hsu, C.W., Kuo, T.C., Chen, S.H. & Hu, A.H., 2013, 'Using DEMATEL to develop a carbon management model of supplier selection in green supply chain management', Journal of Cleaner Production 56, 164-172. https://doi.org/10.1016/j.jclepro.2011.09.012 [ Links ]
Jüttner, U., 2005, 'Supply chain risk management: Understanding the business requirements from a practitioner perspective', The International Journal of Logistics Management 16(1), 120-141. https://doi.org/10.1108/09574090510617385 [ Links ]
Kakabadse, N.K. & Khan, N., 2016, 'Editorial: Cosmopolitanism or globalisation', Society and Business Review 11(3), 234-241. https://doi.org/10.1108/SBR-06-2016-0040 [ Links ]
Kilubi, I., 2016a, 'Investigating current paradigms in supply chain risk management - A bibliometric study', Business Process Management Journal 22(4), 662-692. https://doi.org/10.1108/BPMJ-05-2015-0060 [ Links ]
Kilubi, I., 2016b, 'The strategies of supply chain risk management - A synthesis and classification', International Journal of Logistics Research and Applications 19(6), 604-629. https://doi.org/10.1080/13675567.2016.1150440 [ Links ]
Kim, Y., Chen, Y.S. & Linderman, K., 2015, 'Supply network disruption and resilience: A network structural perspective', Journal of Operations Management 33, 43-59. https://doi.org/10.1016/j.jom.2014.10.006 [ Links ]
Kırılmaz, O. & Erol, S., 2017, 'A proactive approach to supply chain risk management: Shifting orders among suppliers to mitigate the supply side risks', Journal of Purchasing and Supply Management 23(1), 54-65. https://doi.org/10.1016/j.pursup.2016.04.002 [ Links ]
Klibi, W., Martel, A. & Guitouni, A., 2010, 'The design of robust value creating supply chain networks: A critical review', European Journal of Operational Research 203(2), 283-293. https://doi.org/10.1016/j.ejor.2009.06.011 [ Links ]
König, A. & Spinler, S., 2016, 'The effect of logistics outsourcing on the supply chain vulnerability of shippers', The International Journal of Logistics Management 27(1), 122-141. https://doi.org/10.1108/IJLM-03-2014-0043 [ Links ]
Kurniawan, R., Zailani, S.H., Iranmanesh, M. & Rajagopal, P., 2017, 'The effects of vulnerability mitigation strategies on supply chain effectiveness: Risk culture as moderator', Supply Chain Management: An International Journal 22(1), 1-15. https://doi.org/10.1108/SCM-12-2015-0482 [ Links ]
Langley, C., 2012, Third-party logistics study: The state of logistics outsourcing, viewed 14 August 2018, from https://www.capgemini.com/resource-fileaccess/resource/pdf/2013_Third-Party_Logistics_Study.pdf [ Links ]
Lavastre, O., Gunasekaran, A. & Spalanzani, A., 2014, 'Effect of firm characteristics, supplier relationships and techniques used on supply chain risk management (SCRM): An empirical investigation on French industrial firms', International Journal of Production Research 52(11), 3381-3403. https://doi.org/10.1080/00207543.2013.878057 [ Links ]
Marley, K., Ward, P. & Hill, J., 2014, 'Mitigating supply chain disruptions: A normal accident perspective', Supply Chain Management: An International Journal 19(2), 142-152. https://doi.org/10.1080/00207543.2013.878057 [ Links ]
Meyer, A., Niemann, W. & Kotzé, T., 2017, 'Exploring the dark side of interpersonal relationships between buyers and suppliers of logistics services', Acta Commercii 17(1), 1-12. https://doi.org/10.4102/ac.v17i1.437 [ Links ]
Nel, J., De Goede, E. & Niemann, W., 2018, 'Supply chain disruptions: Insights from South African third-party logistics service providers and clients', Journal of Transport and Supply Chain Management 12(1), 1-12. https://doi.org/10.4102/jtscm.v12i0.377 [ Links ]
Obayi, R., Koh, S.C., Oglethorpe, D. & Ebrahimi, S.M., 2017, 'Improving retail supply flexibility using buyer-supplier relational capabilities', International Journal of Operations & Production Management 37(3), 343-362. https://doi.org/10.1108/IJOPM-12-2015-0775 [ Links ]
Oke, A. & Gopalakrishnan, M., 2009, 'Managing disruptions in supply chains: A case study of a retail supply chain', International Journal of Production Economics 118(1), 168-174. https://doi.org/10.1016/j.ijpe.2008.08.045 [ Links ]
Olsson, C. & De Verdier, C., 2017, 'The connections between proactive and reactive supply chain risk management', Master's dissertation, Lund University, viewed 11 June 2017, from http://lup.lub.lu.se/luur/download?func=downloadFile&recordOId=8906665&fileOId=8906666. [ Links ]
Percy, W.H., Kostere, K. & Kostere, S., 2015, 'Generic qualitative research in psychology', Qualitative Report 20(2), 76-85. [ Links ]
Pettersen, S.S. & Asbjørnslett, B.E., 2016, 'A design methodology for resilience in fleets for service operations', paper presented at PRADS2016, Copenhagen, 4-8th September, viewed n.d., from https://brage.bibsys.no/xmlui/bitstream/handle/11250/2483682/Pettersen_ Asbj%C3%B8rnslett+-+PRADS+2016.pdf?sequence=1 [ Links ]
Plano Clark, V.L. & Creswell, J.W., 2015, Understanding research: A consumer's guide, 2nd edn., Pearson Education, Boston, MA. [ Links ]
Polit, D.F. & Beck, C.T., 2012, Nursing research: Generating and assessing evidence for nursing practice, 9th edn., Wolters Kluwer Health | Lippincott Williams & Wilkins, Philadelphia, PA. [ Links ]
Prakash, S., Soni, G. & Rathore, A.P.S., 2017, 'A critical analysis of supply chain risk management content: A structured literature review', Journal of Advances in Management Research 14(1), 69-90. https://doi.org/10.1108/JAMR-10-2015-0073 [ Links ]
Purvis, L., Gosling, J. & Naim, M.M., 2014, 'The development of a lean, agile and leagile supply network taxonomy based on differing types of flexibility', International Journal of Production Economics 151, 100-111. https://doi.org/10.1016/j.ijpe.2014.02.002 [ Links ]
Rowley, J., 2012, 'Conducting research interviews', Management Research Review 35(3), 260-271. https://doi.org/10.1108/01409171211210154 [ Links ]
Sandelowski, M., 2000, 'Focus on research methods-whatever happened to qualitative description?', Research in Nursing and Health 23(4), 334-340. https://doi.org/10.1002/1098-240X(200008)23:4%3C334::AID-NUR9%3E3.0.CO;2-G [ Links ]
Scholten, K. & Schilder, S., 2015, 'The role of collaboration in supply chain resilience', Supply Chain Management: An International Journal 20(4), 471-484. https://doi.org/10.1108/SCM-11-2014-0386 [ Links ]
Selviaridis, K. & Spring, M., 2007, 'Third party logistics: A literature review and research agenda', The International Journal of Logistics Management 18(1), 125-150. https://doi.org/10.1108/09574090710748207 [ Links ]
Shao, X.F. & Dong, M., 2012, 'Supply disruption and reactive strategies in an assemble-to-order supply chain with time-sensitive demand', IEEE Transactions on Engineering Management 59(2), 201-212. https://doi.org/10.1109/TEM.2010.2066280 [ Links ]
Shenton, A.K., 2004, 'Strategies for ensuring trustworthiness in qualitative research projects', Education for Information 22(2), 63-75. https://doi.org/10.3233/EFI-2004-22201 [ Links ]
Sodhi, M., Son, B. & Tang, C.S., 2012, 'Researchers' perspective on supply chain risk management', Production and Operations Management 21(1), 1-13. https://doi.org/10.1111/j.1937-5956.2011.01251.x [ Links ]
Stellenbosch University, 2016, Logistics Barometer South Africa 2016, viewed 09 November 2017, from https://www.sun.ac.za/english/faculty/economy/logistics/Documents/Logistics %20Barometer/Logistics%20Barometer%202016%20Report.pdf [ Links ]
Trkman, P., Oliveira, M.P.V.D. & McCormack, K., 2016, 'Value-oriented supply chain risk management: You get what you expect', Industrial Management & Data Systems 116(5), 1061-1083. https://doi.org/10.1108/IMDS-09-2015-0368 [ Links ]
Vilko, J., Ritala, P. & Edelmann, J., 2014, 'On uncertainty in supply chain risk management', The International Journal of Logistics Management 25(1), 3-19. https://doi.org/10.1108/IJLM-10-2012-0126 [ Links ]
Wagner, S.M. & Silveira-Camargos, V., 2012, 'Managing risks in just-in-sequence supply networks: Exploratory evidence from automakers', IEEE Transactions on Engineering Management 59(1), 52-64. https://doi.org/10.1109/TEM.2010.2087762 [ Links ]
Williams, B.D., Roh, J., Tokar, T. & Swink, M., 2013, 'Leveraging supply chain visibility for responsiveness: The moderating role of internal integration', Journal of Operations Management 31(7), 543-554. https://doi.org/10.1016/j.jom.2013.09.003 [ Links ]
Wu, Y.C., Goh, M., Yuan, C.H. & Huang, S.H., 2017, 'Logistics management research collaboration in Asia', The International Journal of Logistics Management 28(1), 206-223. https://doi.org/10.1108/IJLM-09-2013-0104 [ Links ]
Yu, M.C. & Goh, M., 2014, 'A multi-objective approach to supply chain visibility and risk', European Journal of Operational Research 233(1), 125-130. https://doi.org/10.1016/j.ejor.2013.08.037 [ Links ]
Zhang, H. & Okoroafo, S., 2015, 'Third Party Logistics (3PL) and supply chain performance in the Chinese market: A conceptual framework', Engineering Management Research 4(1), 38-48. https://doi.org/10.5539/emr.v4n1p38 [ Links ]
 Correspondence:
Correspondence:
Wesley Niemann
wesley.niemann@up.ac.za
Received: 27 Feb. 2018
Accepted: 17 Sept. 2018
Published: 28 Jan. 2019














