Servicios Personalizados
Articulo
Indicadores
Links relacionados
-
 Citado por Google
Citado por Google -
 Similares en Google
Similares en Google
Compartir
South African Journal of Information Management
versión On-line ISSN 1560-683X
versión impresa ISSN 2078-1865
SAJIM (Online) vol.22 no.1 Cape Town 2020
http://dx.doi.org/10.4102/sajim.v22i1.1130
Introduction
Master data, which capture core information about an organisation's stakeholders, products and relationships amongst them (Haneem, Kama & Kazmi 2016), have been the staple discourse for explaining organisational operations (Infovest 2018). The concentration on master data has been accentuated by the recognition of big data as a strategic asset for organisations (Hagerty 2016) and increased business and data management capabilities in the digital economy (Bärenfänger, Otto & Gizanis 2015). These capabilities manifest in advanced analytics tools' capacity to generate insightful business information and enhance the provision of digital services to customers (Organisation for Economic Co-operation and Development [OECD] 2016). Such capabilities are also evident in digital technologies that avail and pool masses of data from multiple modes to one central place or distributed locations for in-depth analysis. Whilst these capabilities can increase data types that can be analysed by organisations, master data remain the preferred data sources because of the panoramic picture it renders on business operations (Entity Group 2016). The oversight on less strategic data forms, such as metadata and transactional data quality, is concerning (Palavitsinis 2013) because data quality is a strategic resource in prudent decision-making, especially in public institutions where scarce resources must be strategically harnessed to ensure the long-term sustainability of programmes (Alketbi 2014).
The limited application of transactional data in explaining business operations is attributed to its volume, volatility (Bester 2019) and complex connections with daily operations of organisations. The American Council for Technology-Industry Advisory Council (ACT-IAC) (2015) observes that the high volume of transactional data that government agencies deal with daily, complex business processes, complex policy requirements and ancient technology systems complicate the management of transactional data quality. The American Council for Technology-Industry Advisory Council (2015) elaborates that even within the same agency, different divisions apply the same data differently and how these data elements are defined within the same agency varies widely.
Literature on transactional data and its applications in large organisations has gained momentum even though such data should be used cautiously because of their complexities (Hand 2018). The increasing prominence of transactional data quality in explaining organisational operations arises from increasing programme funding accountability and effective monitoring of public programmes (Rothbad 2015), the need to render responsible customer experiences and the growing competitive intensity of knowledge-intensive industries (Biegel et al. 2018). Other considerations include the demand for data analytics to steer contemporary business operations and the need for comprehensive business insights (Hagerty 2016), the surging costs of surveys and transactional data's potential to generate insightful discoveries (Hand 2018).
The need for high transactional data quality has been accentuated by large secondary data sets used in secondary analysis (Hand 2018), and organisations' desire for richer understanding of customers to provide relevant, meaningful and efficient interactions (Biegel et al. 2018). Despite these developments, management executives are concerned about the paucity of sufficient, correct, reliable and timely data upon which to ensure sound organisational decisions and bemoan the depletion of quality information (Bester 2019).
One grey area regarding transactional data quality is whether and the extent to which data sets generated at the organisational sources (e.g. by call agents) are consistent with other data sources (e.g. feedback generated by field technicians who deal with customer queries on data quality). Addressing this issue contributes to improving data quality at multiple organisational levels by integrating various information from diverse sources (Rothbad 2015). Quality assurance (QA) processes should commence at the initial data entry stages and progress through the entire process of integrating data from multiple sources to build an integrated data system (Rothbad 2015). The failure to corroborate transactional data quality from multiple agent sources can lead to incongruence of data quality, imprudent decision-making within large publicly owned companies (Rambe & Bester 2016) and catastrophic social consequences such as massive power failures (Fürber 2015).
Providing in-built complementarities and coherence within and across transactional data from multiple agencies ensures appropriate evaluation of public programmes (Rothbad 2015). To establish the quality of transactional data, we examined the coherence of data generated by an African power generation and distribution company (APGDCO1) from two fronts: data generated from customer calls received at the call centre (customer calls transactional data) and technician feedback on customer transactions they executed. The study addressed the following questions:
-
What is the quality of transactional data captured from customer calls at APGDCO based on source system measurement?
-
How many downstream system transactions have feedback of field technicians that indicates incorrect transactional data?
Problem background
The African power generation and distribution company has many customers such as households, corporations, mines and city councils. Larger customers often have complex monitoring systems for measuring quality of electricity received and can alert APGDCO immediately when an interruption in electricity supply occurs. Small customers cannot afford monitoring systems and report electricity supply problem (ESP) cases to APGDCO's call centre whenever they experience electricity outages. Subsequently, call centre agents probe customer queries using call scripts or case-based reasoning to categorise an issue correctly. If agents conceive APGDCO's network as the source of the problem, an ESP case is logged and a field technician is dispatched to restore electricity supply.
Therefore, correct interpretation and classification of customer problems are paramount to utilising APGDCO's resources appropriately. Sometimes, call centre agents may misinterpret a customer's explanation of an issue or are misled by customers. Consequently, a fault caused by a customer's defective equipment can be logged as an ESP case, something that APGDCO should not respond to as it is the customer's responsibility to resolve. For each transaction ESP case logged, a work order is automatically generated in the receiving system and technicians mark on the work order the cause of the ESP and the action performed to restore supply. If the issue was caused by customer's faulty equipment, the technicians will mark the customer side fault, which signifies that call agents captured incorrect transaction data at the source. As a data consumer, the technician is the primary authority on data quality as transaction data quality measured by the contact centre agents may not present a true reflection of the data consumer's experience.
Theoretical framework
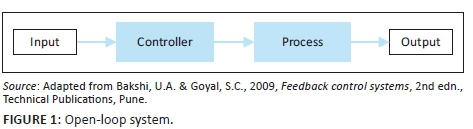
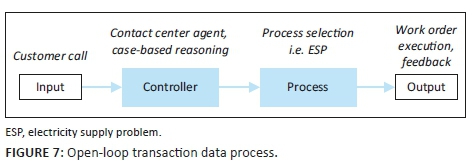
Systems theory considers a system as a set of inter-related and interdependent parts (Mele, Pels & Polese 2010). Cybernetics, generally used as a synonym for systems theory, is concerned with the communication and regulation of systems using a feedback control system (FCS) (Skyttner 2001). An FCS is configured to control itself, another system and feedback loops which are the mechanisms for exercising such control by facilitating desired outcomes. The simplest feedback loop is an open-loop system where input influences output via a control system (see Figure 1). Although such open-loop systems are cheap, simple to design and easy to maintain, their configuration is often inaccurate as no feedback is redirected into the system. Consequently, open-loop system can neither act on the output or external environment nor use it to influence subsequent outputs (ed. Liptak 2018).
A closed-loop system is a better configuration for a system to act on its external environment to regulate itself (see Figure 2). Whilst the system replicates an open-loop system, it has an appendage relaying feedback back to the input. Feedback can be used to adjust subsequent input or facilitate a desired output. A closed-loop system supports higher accuracy as it responds quickly to external and internal changes. However, this system is complex and expensive to create, maintain and often overcorrect itself if not designed carefully (ed. Liptak 2018).

Orr (1998) applied cybernetics to data quality by suggesting that an information system's data quality will be 100% if it represented data exactly as it existed in the real world and 0% if no conformity existed. Data quality changes over time and will not stay at a 100% level ad infinitum. Orr (1998) warns that the absence of an FCS will prevent continuous alignment between data in a system and the real world because feedback is the only valid mechanism that ensures the tracking of changes in the real world to related information systems. Even though Orr's (1998) application of cybernetics focussed on correcting existing master data records, an FCS can also improve the quality of transaction data.
Literature review
Data types
Data are defined as input of unprocessed items such as facts, figures, text, images, numbers, video and audio typically stored in a digital format (Epstein 2012; Nazim & Mukherjee 2016; Vermaat 2014). Consumer and brand-related data tend to be categorised into various types, namely, digital, terrestrial, transactional, emergent/speciality and identity data (Biegel et al. 2018). Other classifications include unstructured data such as e-mails, files and videos, and structured data that comprise master, reference, transactional, metadata, history and queue data (Arun & Jabasheela 2014). Master data refer to vital business information about products, suppliers and customers that has a low change frequency. Reference data describe a business entity such as a customer, product or supplier and do not change frequently. Historical data are data that relate to previous transactions, which include master, reference and transactional data and are retained for compliance purposes (Borek et al. 2014). Transactional data are captured during an interaction and are combined with master and/or reference data to form a transaction at a specific time and have high volume and changes frequently (Borek et al. 2014). Overall, master data are often accorded the highest priority in organisational settings as these capture diverse organisational information such as customers, suppliers, products and their inter-relationships and are shareable across multiple business units of public entities (Nelke et al. 2015).
However, the extraction of quality data is often laborious and dissociated with public service quality, such as patient care in emerging contexts (Marais 2017). The high volume and velocity of various data forms imply that new tools and methodologies are required to capture, manage and process them efficiently (Statistics Divisions of United Nations, Department of Economic and Social Affairs [UN/DESA] and UN Economic Commission for Europe 2015). Therefore, huge investments in human expertise, technology and infrastructure are necessary for organisations to leverage fully the benefits of such data. More so, the silo-based approach to the capturing, curation and management of master data in government organisations also increases the duplication of master data across departments, thereby accentuating government costs and wasting resources (Haneem et al. 2016).
Data quality
Wang and Strong (1996) define data quality as data that are fit for use from the consumer's perspective. Although data quality has traditionally been considered from an accuracy perspective (Lin, Gao, Koronios & Chanana 2007), completeness, timeliness and consistency have become over-riding dimensions of data quality in recent times (ACT-IAC 2015). Completeness describes the extent to which data captured all dimensions that they were created to capture. According to Cai and Zhu (2015), completeness denotes that the values of all components of a single datum are valid. They elaborate that completeness is measured by establishing whether the deficiency of a component will impact the use of the data, especially for data with multi-components and whether the deficiency of a component will impact data accuracy and integrity (Cai & Zhu 2015).
Validity implies that data must be generated from reliable sources. Grillo (2018) concurs that the validity of data deals with the trustworthiness of the data, which increases user engagement, sustains the functioning of a data warehouse and is a critical dimension in the development of a data quality scorecard (DQS) that measures the quality of data in the data warehouse. Consistency means that the same process or source must generate the same data and the same data values describing an object or event should be reflected across the entire organisation (ACT-IAC 2015). For databases, this means that the same data that are located in different storage areas should be considered to be equivalent or possessing equal value (Silberschatz, Korth & Sudarshan 2006). Consistency, therefore, points to whether the logical relationship between correlated data is correct and complete (Cai & Zhu 2015).
Timeliness denotes that data must be adequately current. It is the time delay from data generation and acquisition to its utilisation (McGilvray 2010) to allow for meaningful analysis. It points to the temporal difference between the time at which the data were collected and when they become available for analysis (Brackstone 1999; Keller et al. 2017). Accuracy implies that the appropriate values should be captured at the first time of data entry and should be retained throughout the enterprise (ACT-IAC 2015). Therefore, accuracy measures the degree to which data represent the phenomena they were designed to measure (Brackstone 1999) and whether their numerical value is within a specified threshold (Marev, Compatangelo & Vasconcelos 2018).
However, an improvement of one dimension of data quality may compromise another dimension. For instance, data can be provided timely but at the expense of its completeness. Moreover, whilst the use of data repositories may increase timeliness of access of data to scientists originally not involved in the initial data collection and experiments, access may be restricted if it violates information security and privacy, or accessibility of data may be restricted across organisations because of competitiveness across organisations (Milham 2012). Data completeness may be realised at the expense of their concise representation (Neely & Pardo 2002) and different data consumers may have varying evaluations of the same data quality (Lin et al. 2007). Moreover, the high data expenditures and their exponential growth in relation to media channels they are associated with (Biegel et al. 2018) imply that different organisational departments may undervalue certain data quality dimensions, such as comparability, thereby compromising data quality.
Transactional data quality
Oracle Corporation (2011) observes that transactional data quality captures automated business processes such as sales, service, order management, manufacturing and purchasing. Point-of-sale transactions involve data aspects such as product, place, time, price and name of sale agent and contribute directly to the complexity and volatility of transactional data (Baran & Galka 2016). Research highlights that South African customer data quality is problematic and hampers the quality of decision-making in firms (Burrows 2014). Neil Thorns, Informatica's territory manager for sub-Saharan Africa, contends that most South African companies have low transactional data quality with an average accuracy of 50% or less. This is lower than the 73% global mark advocated by Experian's (2017) latest survey on customer data. The poor data quality is attributed to few business rules and limited automation during data capturing because of limited high-technology adoption and resource constraints (Burrows 2014). The difficulty of upgrading multiple systems and departmental support systems through which data flow also contributes to low transactional data quality. One conundrum is that whilst the support systems through which data are captured are constantly changing, they may be run on antiquated programming languages, thereby making their interfacing with new programmes problematic, culminating in inaccurate transactional data (ACT-IAC 2015).
World Economics' Data Quality Index on the gross domestic product (GDP) of 154 countries employed five indicators - base year, system of national accounts, informal economy, quality of statistics and corruption - and ranked South Africa 49th, with an overall score of 77.1% (World Economics 2017). This ranking is higher than the 73% global mark set by Experian's (2017) survey on data quality. These contradictory statistics on South Africa's data quality raise perplexing questions about the quality of transactional data, thereby amplifying the need to conduct research on data quality.
Methodology
Research design
Because this research corroborated the perspectives of APGDCO's field technicians who resolved customer ESP queries with source data generated by APGDCO's call centre agents, a combination of a quantitative cross-sectional survey and historical transactional data was considered as the appropriate research design. Cross-sectional surveys serve to establish the prevalence of a phenomenon, attitudes and opinions from individuals to portray an overall picture at the time of conducting the study (Kumar 2014). To ascertain the quality of data, the study needed to compare the technicians' view with customer centre's data quality measurements. As such, the study employed historical data (i.e. work orders from the receiving system that were marked with customer-side fault) as the technicians' view and compared it with the contact centre's data quality measurements captured in the source system. The original data captured by call centre agents (i.e. historical transactional data) relating to client ESP data included call numbers, client locations and nature of ESP type. The historical data sets on transactional data employed in the study covered April 2012 to March 2017, a period that is conceived enough to detect trends in ESPs in the region the study covered.
Instrumentation
The structured questionnaire had two sections, namely, the demographic data section covering technicians' years of experience, the experience of using enterprise digital assistant (EDA) and transactional data quality section (customer-side fault). Historical transactional data encapsulated the followings: volume of work order distribution across various service centres, source system transactional data quality versus feedback on transactional data per financial year.
Data collection
The second author (J.B.) conducted a census on the 303 technicians who resolved customer queries in APGDCO over 2 months in 2017. The self-administered questionnaire comprised ordinal and ratio scales. Respondents completed (1) a hard copy questionnaire, scanned and emailed it to the second author, (2) an electronic version that they word processed and emailed or (3) a computer- or smartphone-based web browser version of the questionnaire. Despite numerous follow-ups made with APGDCO technicians, the census generated a 35% response rate (106 out of 303), mostly from the scanned copy sent via email. These data were coded and captured on an Excel spreadsheet and exported to Statistical Packages for the Social Sciences (SPSS) for a detailed data analysis.
Data preparation
The historical transactional data were extracted using Structured Query Language (SQL) from the company's ESP application database containing work order records. The normalisation and enrichment of the data involved checking of record descriptions for the wording 'customer fault' and any variations that indicated a customer fault. An interpretation of transaction dates allowed for the addition of fields and categorisation of data according to APGDCO's financial years. A precompiled report that indicated the mean of the transactional call and quality per month was referenced to indicate transactional data quality at the source system per secondary data record. All records were exported to an Excel spreadsheet for secondary data preparation and initial analysis before its exportation to SPSS for detailed analysis.
Data analysis
The study employed descriptive statistics to organise and summarise data based on sample demographics (Holcomb 2016). Frequency distributions, means and percentage analysis were used for the presentation and analysis of descriptive statistics. This study's frequency distribution covered work order amounts and data quality measured at source system and via feedback. Means were generated for the quality of source system data and feedback from technicians. Inferential statistics were instrumental in drawing conclusions about the population by determining the relationship amongst variables and making predictions about the population (McKenzie 2014). Correlation and regression analysis were used to determine the associative and predictive relations of variables examined.
Validity and reliability
Nieuwenhuis (2014) argues that validity requires the researcher to document procedures for evaluating the trustworthiness of the data collection and analysis. The statistician and researchers examined the conciseness and precision of questions to ensure face validity. The technicians' manager also appraised the questionnaire to ensure that the breadth of questions covered data quality issues (i.e. content validity). The researchers also verified raw data through availing questionnaires and field notes to respondents to correct factual errors (Nieuwenhuis 2014). For transactional data at the source, all compiled data sets were exchanged with data custodians (data analyst and manager of call centre agents) to authenticate data sources and ensure the credibility of results.
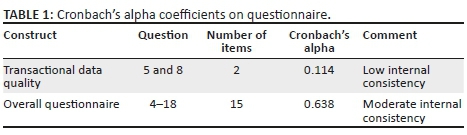
The researchers and the statistician shared all data sets to ensure consistency in the coding process, and where opinions varied, they met to clarify consistencies and generate consensus. This ensured intra- and inter-coder reliability. The instrument had an internal consistency of 0.638 even though two items had low consistency (see Table 1). The small number of items on transactional data quality perhaps explain the low internal consistency of construct on this instrument.
Presentation of findings
The results on years of experience at an APGDCO Customer Service Centre (CSC) in Figure 3 show that 40.566% of the technicians had 6-10 years, 27.358% had 0-5 years, 21.698% had more than 20 years, 8.491% had 11-15 years and only 1.887% had 15-20 years of experience. It is important to understand that all values were rounded to three decimals so that they add up to 100.000%. Although rounding them to one decimal seemed appropriate mathematically, it was not considered as the values would be too close to but not add up to 100%. Most of the technicians had more than 5 years of work experience and, therefore, had enough work exposure to fulfil their responsibilities.
The African power generation and distribution company adopted EDA devices in the 2011-2012 financial year. Thus, the maximum possible experience a technician had on EDA usage was around 5 years. The distribution analysis of EDA usage, depicted in Figure 4, reveals that only 8.491% of the technicians had EDA usage experience of 1 year or less, whilst 53.774% had more than 4 years of experience. It is important to note that even when expanded to three decimals, exact summation to 100.0000 occurs at fourth decimal only. Therefore, the EDA usage experience was enough for technicians' effective utilisation of these devices judging from the distribution analysis.
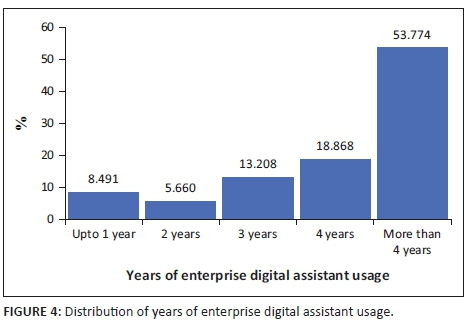
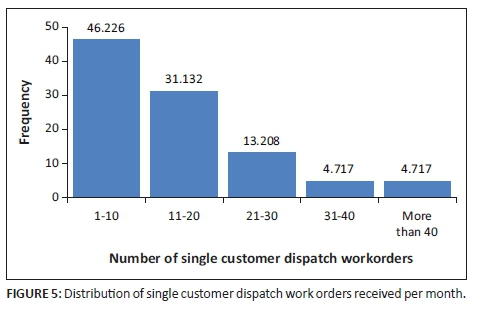
Figure 5 indicates that most technicians received less than 20 single customer dispatch work orders per month, 46.226% had 1-10 and 31.132% had 11-20 work orders. Therefore, 77.358% of technicians received an average of one customer dispatch work order per working day per month. Therefore, technicians were not overburdened with dispatch work orders and could properly evaluate work and provide feedback on the executed work.
Source system and feedback data quality
The descriptive summary in Table 2 shows a hierarchical breakdown of APGDCO's historical data. The three-level hierarchy system has at its lowest level the service centres where technicians are located, who are responsible to restore ESP cases. Service centres are grouped one level up under sectors, which are again grouped under zones as the highest level. It contains columns for the amount of ESP work orders received, the overall percentage of work orders, work order percentage received during work time and overtime, source system data quality as measured by the call centre agents (data creators) at the source system and data quality based on feedback from technicians (data consumers) on work orders.
Source system data quality is measured via a QA process that evaluates 1% of historical call centre system transactional data and expresses it as a quality percentage. Data quality based on technician feedback is determined by dividing the total number of historical work orders at the receiving system by the amount of work orders marked as valid ESP transactions and displaying it as a percentage.
Table 2 reveals that data quality for all hierarchy levels, which data creators measured at the source system, had a very narrow distribution. It consisted of a mean of 80%, a maximum deviation from the mean of 0.2% and a minimum deviation of 0%. Measurement of data quality via technician feedback at the receiving system indicated a mean of 81.3%, with the biggest deviation of 14% at Service Centre 2.B.5 and the closest deviation of 0.1% observed at Service Centre 2.B.6. The measurements were very similar, implying that measurement by data creators confirmed the data quality experience measured from data consumers' feedback. The higher deviation from the mean found within feedback measurements could be attributed to high granularity in the data analysed (i.e. per transaction) compared to the much lower granularity (i.e. monthly) of data creators' measurements.
Comparison of transactional data quality: Source system with feedback
Data quality measured at the source system by the data creators was based on results from a QA process performed on a 1% sample of the total historical ESP transactions for a month. This QA process consumes much time and only 1% of the total transactions could be assessed. The QA process evaluates the extent of call professionalism when data capturers are answering calls, for instance, whether correct steps were followed to identify a customer, interpret his or her fault symptoms, send the fault to the correct department and if the call was concluded professionally. Most scoring relates to transactional data quality and hence this score is used as a proxy for transactional data quality at the source system. Data quality measured at the receiving system via technician feedback was calculated by dividing the total number of historical work orders automatically generated from ESP cases logged by the amount of work orders marked as a valid ESP case.
A comparison of historical transactional data quality measured by data creators at the source system and historical data quality measured by evaluating feedback from technicians on work orders at the receiving system reveals whether feedback is impacted by source system data quality or not. Transactional feedback from field technicians indicates the correctness of work order/transactional data quality if it describes a valid resolution of an ESP.
Descriptive analysis is presented in Table 3 where each financial year's source system transactional data quality and feedback on correct transactions are compared to the average for all years combined. A value higher than the average is denoted with a double dagger, whilst a value lower than the average is marked with a single dagger. The indicated daggers for source system data quality and feedback indicating correct transactions correspond in the financial years 2014-2015, 2015-2016 and 2016-2017.

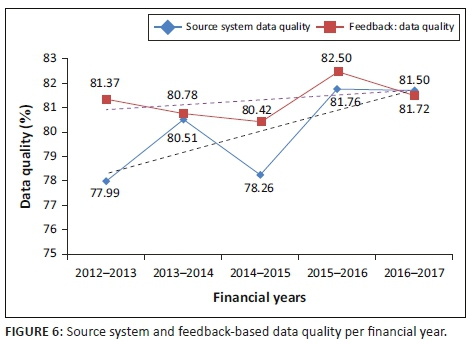
Figure 6 displays data quality from both source system and transactions, with feedback indicating correct data. Transactional data quality from the source system indicates an upward trend, despite the slump during the 2014-2015 financial year. Data quality based on transactional feedback from the data consumer perspective also displays a general upward trend even though it has more declines than source system data quality. Therefore, on a year-by-year basis, the perspectives on data quality by the data creator and data consumer did not always cohere. Therefore, data creators can focus on improving data quality measurements to ensure its closer reflection of the data consumer's perspective, but this must be considered carefully as the small sample size of the transactions measured by data creators might explain this difference in results.
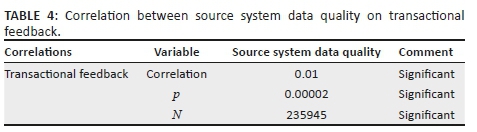
Correlation analysis between source system data quality (independent variable) and data from transactional feedback (response variable) in Table 4 reveals a weak positive statistically significant (0.01; p = 0.00002) relationship between the two variables. The weak correlation could be influenced by the extensive granularity of data quality measured via technician feedback (e.g. measured per individual work order) versus low granularity of data quality measured at the source system that only analyses 1% sample of transactions via the QA process.
The study also sought to establish whether data quality measured at source has an impact on data quality measured via feedback (i.e. whether the nature of data quality at the source predicted the data quality generated by field technicians).
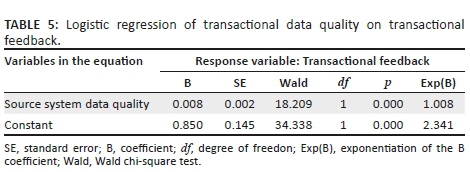
Logistic regression was used to assess inferentially the relationship between transactional data quality from the data creator (i.e. contact centre) and transactional feedback from the data consumer (i.e. field technician). This tool is preferred as the independent variable, source system data quality is a ratio-scale variable measured in percentages and the response variable, transactional feedback, is a binary value where 1 = correct and 0 = incorrect. The results in Table 5 illustrate that transactional feedback is significantly dependent on source system data quality (Wald statistic = 18.209, df = 1, p = 0.000).
Discussion
A comparison of percentages of transactional data quality at the source system and feedback on correct transactions gave interesting results. Most of the percentages on feedback on correct transactions were higher than those of source system transactional data quality, creating an impression that data from execution of work orders provided a more accurate picture of transactional data quality than data captured at the source. Nevertheless, the differences between these percentages were marginal and were closer to the averages for the years considered. These differences demonstrate the absence of a clear feedback loop from technicians' feedback on transactions to source system data quality, which can compromise the quality of data at the source. Therefore, despite the importance of data management in addressing data quality challenges, sub-optimal data entry affects the operational efficiency and accurate reporting of business operations (Oracle Corporation 2011). Notwithstanding the minor differences between data quality averages measured from feedback data and source system transactional data in Table 3, at least 18.69% (= 100% − 81.31%) to 19.95% (= 100% − 80.05%) of the dispatched work orders should not have been executed. These minor variances cost APGDCO substantially from a resource and reputation perspective as the resource expended, namely, labour hours and vehicle kilometres driven could have been spent on, for example, plant maintenance work. Furthermore, customers would wait longer for their supply to be restored because of invalid ESP calls receiving undue attention. The variances between these perspectives on data demonstrate that transactional data constitute large, complex, unstructured data sets that are hard to deal with using conventional tools and techniques and reflect public institutions' incapacity to optimally unlock value from such data (OECD 2016). Despite these discrepancies between source data quality and feedback data quality, the general upward trajectory of data quality between 2012 and 2017 indicates that APGDCO was striving to use its analytical capabilities to optimise data quality, notwithstanding its institutional constraints surrounding productive usage of data. The prudent use of data analytics is considered instrumental in facts-based strategic decision-making, improving operational efficiency and revenue levels (Singh 2018). However, APGDCO has not sufficiently exploited these data-driven capabilities to increase its profit margins and revenue.
The correlation result demonstrates a positive statistically significant but weak relationship between source system data quality and transactional feedback. This somewhat coheres with the upward trajectory reported in the interaction of source system data quality and transactional feedback - a clear indication that as more correct data quality is captured at the source, technicians are more inclined to execute more correct ESP (which are faults of APGDCO), which results in more feedback of correct transactions executed. This finding could give credence to the claim that data integration and transaction analytics are rendering implementable data-driven insight in a visually interactive (to both data agents and technicians) and iterative, agile manner (OECD 2016). However, accepting this claim contradicts the observation that the persistent albeit marginal discrepancies between source system data quality and transactional feedback are clearly indicative of the failure of APGDCO to exploit technicians' feedback to optimally improve successive data capturing processes. These discrepancies between results of data quality measured from data creators and data consumer perspectives demonstrate that processing big data remains a daunting task for public institutions and cannot guarantee optimal decision-making even though it is instrumental in decision support systems (Alketbi 2014).
The results of regression analysis show that transactional feedback is significantly dependent on source system data quality - that is source data significantly predicts feedback quality. This means the frequency of accurate data captured at the source increases the successful resolution of customer ESPs by field technicians. Apart from accurate data capturing, data consolidation and real-time data synchronisation have potential to improve data quality in organisational operations (Oracle Cloud 2015). This finding supports the view that because decision-making in companies can be foreseen and proactive, the initiation of information collection process earlier means that the timeliness of information should improve the quality of data-driven decision-making (Dillon, Buchanan & Corner 2010).
From a theoretical perspective, the current transactional data system under scrutiny demonstrates an open-loop system as depicted in Figure 7, where:
-
Input is the customer call.
-
Controller function is performed by the contact centre following the case-based reasoning logic.
-
Process such as ESP will be determined via the controlling function.
-
Output is a resultant work order executed by the field technician and feedback captured during the completion of the work order.
As evident in the results of the correlation and regression analyses, an increase in correct transactions captured will result in improved transaction feedback, indicating that correct transactions were captured and executed. To improve the quality of transactional data captured, an FCS with a closed-loop configuration shown in Figure 8 would be invaluable. This configuration is the same as Figure 7, but the feedback of the technician is fed back to the controller.
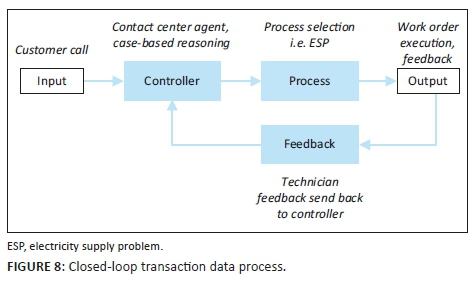
The application of an FCS in this context is different from the one envisioned by Orr (1998) to update an existing master data record. Updating an incorrect transaction after it was executed will not provide any immediate benefit to the organisation as costs (e.g. on mileage, time and overtime payments) would have already been incurred by the organisation to resolve a customer-side fault. This understanding seems incongruent with the claim that large sets of raw data combined with powerful and sophisticated analytics tools provide insights that improve operational performance of large organisations (Henke et al. 2016). This is because recognition of a mistake may not always translate into pre-emptive and corrective future interventions even though organisations would be expected to learn from past mistakes to enhance the accuracy of their future transactions. However, when organisations learn, such a learning experience which unfolds via feedback is also known as a self-normative FCS (ed. François 2011). In this example, feedback indicating a customer side fault will be fed back to the data creator/contact centre agent. This feedback can then be used to identify the root cause of the incorrectly logged customer-side fault, such as data creator interpretation, issues in the logic of the case-based reasoning questions or customer providing false information.
Managerial implications
The fact that accurate source data predicts technician feedback implies that effective data management through reducing fragmentation and inconsistencies amongst data agents dealing with data collection can contribute to improved data quality in dynamic environments (Lin et al. 2007). Therefore, organisations can stand to improve their operational efficiency, reduce financial misappropriations and waste if their data capturing at the source improves. This implies that managers should commit more financial and intellectual resources towards continuous on-the-job training in data capturing to reduce inaccurate data capturing which leads to multiple technician assignments to resolve ESP caused by customer mistakes, such as overloading of their residential electrical circuit and faulty appliances causing a circuit breaker to trip.
Transactional data quality can also be improved by an FCS, if (1) a mechanism is available to capture feedback and (2) the feedback is integrated back to the controller of the transactional data. This will allow identification of the root cause of poor-quality data and facilitate the reduction in or eradication of future occurrences thereof. As the complexity of a closed-loop system comes at an increased cost, performing a cost-benefit analysis is critical before deciding whether to implement an FCS strategy to improve transactional data quality (Batini & Scannapieco 2016).
The fact that at least 18.69% - 19.95% of the dispatched work orders should not have been executed is indicative of the financial and time cost that can be avoided should appropriate data capturing techniques be applied. As such, customer misinformation must be prevented by requiring data capturers to sufficiently probe customer queries before dispatching technicians to ensure that correct, comprehensive and reliable data are captured at the source. Because the mistakes made by data capturers also contributed to ESP faults, continuous training on data capturing can contribute to the generation of quality data at the source. Moreover, managers and executives should continue to focus on the critical importance of correct data entry as it forms the basis of a successful data management system.
When this happens, the root cause of faulty data entry can be identified and corrective actions and/or learning and application can be facilitated to reduce or ultimately prevent future occurrences of invalid transactions.
Implications for future research
In view of the consistencies (upward improvements in data quality) and discrepancies (technician feedback quality being slightly higher than source-generated data) between data quality measurements from technician feedback and source-generated data, future studies may need to track the sequence of the generation of each perspective/source on data quality (technician-generated and source-generated) and their synchronisation and integration. As Hand (2018) observes, transaction data are special types of administrative data concerned with the sequences of events relating to transactions, their retention in databases and analysis to improve the understanding of organisations' operations. As such, what happens at each stage becomes critical to improve the quality of transactional data.
Data quality improvement costs should always be an important consideration before deciding on an appropriate quality improvement strategy (Batini & Scannapieco 2016). Therefore, even though an FCS has the potential to facilitate transaction data quality improvements, the cost to implement should be carefully analysed before implementation to ensure a positive return on investment (ROI). Future studies can examine the return on investment potential of various FCS and compare it to the improvement in transaction data quality achieved. This is because although an FCS could be initially expensive to establish, the ROI would rise over time of its application. Future studies may also explore methodologies to accurately determine the cost of incorrect transactional data across industries and different businesses and determine at which level of data quality does the cost to improve negate the benefits derived.
Because some inconsistencies in data quality may be attributed to organisational difficulties in defining master and transactional data, future studies can examine the different ways in which such data types are defined and characterised in organisations to ensure congruence and consistencies in ways the same data pieces are defined, categorised and assessed by different agents within and outside organisations. Recent literature suggests that the quality of a data set and each of its individual components can be influenced by a number of different factors (e.g. inaccuracy, imprecision in definitions, gaps or inconsistencies in measurements), thus necessitating the development of a context-dependent data quality evaluation framework (Marev et al. 2018). For consistency and believability, consistent representation of data partly depends on the precise characterisation and definition of data dimensions in specific contexts (Batini et al. 2009; Pipino, Lee & Wang 2002).
Conclusion and recommendations
In view of the inconsistencies between data quality measurements from technician feedback and source-generated data, the entire value chain of data generation needs scrutiny. Moreover, Broadridge (2017) recommends increased granularity in consolidated data presentation because granular data often demonstrate that surface-level transactions may be inconsistent with the picture developed from lowest-level detail. Moreover, Alketbi (2014) recommends the development of a complete data quality framework for improved data quality and data-driven decision-making in public organisations. At the level of predictive relations, the positive association between source-generated data and technician feedback data could be indicative of the capacity of tracking different types of data to improve overall data quality. Broadridge (2017) observes that data quality issues are proportionally related to the sequence in which firms tackle data improvement projects (i.e. from valuation or reference, transactional and derived data). Therefore, firms should consider the proper implementation of an FCS to enhance their data quality strategy, as it provides critical information required to drive four of the 12 directives of a continuous improvement programme as suggested by Sebastian-Coleman (2012), namely:
-
Understand data quality as defined by its consumers.
-
Attend to root causes of data issues.
-
Measure data quality.
-
Ensure data producers are kept accountable for the quality of their data.
Acknowledgements
The authors are grateful to the power generation company for availing historical data and to technicians for participating in the interviews
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
All authors contributed equally to this work.
Ethical consideration
This article followed all ethical standards for research without direct contact with human or animal subjects.
Funding information
This research received funding from the Central University of Technology and the power generation company that cannot be named for anonymity purposes.
Data availability statement
Data sharing may not be possible for this article as some of the pieces of data will expose the name of the institution in which the research was conducted, thus compromising participants' anonymity.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Arun, K. & Jabasheela, L., 2014, 'Big data: Review, classification and analysis survey', International Journal of Innovative Research in Information Security 1(3), 17-23. [ Links ]
Alketbi, O., 2014, Data quality assurance for strategic decision making in Abu Dhabi's public organisations, University of Bedfordshire, Luton.
American Council for Technology-Industry Advisory Council (ACT-IAC), 2015, Data quality: Letting data speak for itself within the enterprise data strategy, Collaboration & Transformation (C&T) Shared Interest Group (SIG) and Financial Management Committee, Fairfax, VA.
Bakshi, U.A. & Goyal, S.C., 2009, Feedback control systems, 2nd edn., Technical Publications, Pune.
Baran, R.J. & Galka R.J., 2016, Customer relationship management: The foundation of contemporary marketing strategy, 2nd edn., Taylor & Francis, New York, NY.
Bärenfänger, R., Otto, B. & Gizanis, D., 2015, Business and data management capabilities for the digital economy White Paper. Capabilities in the digital economy, Competence Centre Corporate Data Quality (CC CDQ), May 2015.
Batini, C., Cappiello, C., Francalanci, C. & Maurino, A., 2009, 'Methodologies for data quality assessment and improvement', ACM Computing Surveys 41(3), 1-52. https://doi.org/10.1145/1541880.1541883 [ Links ]
Batini, C. & Scannapieco, M., 2016, Data and information quality: Dimensions, principles and techniques, Springer, Cham.
Bester, J., 2019, 'The influence of transactional data quality improvements on monetary savings of Eskom distribution, Free State', Master's thesis, Central University of Technology Free State, Bloemfontein. [ Links ]
Biegel, B., Margulies, J., Maggi, G. & Davis, C., 2018, The state of data 2018: A Winterberry Group Report, December 2018, Winterberry Group, New York, NY.
Borek, A., Parlikad, A.K., Webb, J. & Wooda, P., 2014, Total information risk management: Maximizing the value of data and information assets, Elsevier, New York, NY.
Brackstone, G., 1999, 'Managing data quality in a statistical agency', Survey Methodology 25(2), 139-150. [ Links ]
Broadridge, 2017, A practical guide on data initiatives for public and private investments: Establishing data governance and better data management, Broadridge Financial Solutions, New Hyde Park, NY.
Burrows, T., 2014, ITWeb: SA looks to address data quality, viewed 03 January 2018, from https://www.itweb.co.za/content/JOlx4z7kGXY756km.
Cai, L. & Zhu, Y., 2015, 'The challenges of data quality and data quality assessment in the big data era', Data Science Journal 14(2), 1-10. https://doi.org/10.5334/dsj-2015-002 [ Links ]
Dillon, S., Buchanan, J. & Corner, J., 2010, 'Comparing public and private sector decision making: Problem structuring and information quality issues', Proceedings of the 45th annual conference of the ORSNZ, November 2010, pp. 229-237.
Entity Group, 2016, Why not to put transactional data in an MDM hub, viewed 07 November 2018, from https://www.entitygroup.com/wp-content/uploads/2016/05/master_data_management_and-Transaction_data_whitepaper.pdf. https://www.entitygroup.com/wp-content/uploads/2016/05/master_data_management_and-Transaction_data_whitepaper.pdf.
Epstein, E., 2012, Implementing successful building information modeling, Artech House, Norwood, OH.
Experian Data Quality, 2017, The 2017 global data management benchmark report, viewed 01 April 2020, from https://www.experian.com.my/wp-content/uploads/2017/12/2017-global-data-management-benchmark-report.pdf
François, C. (ed.), 2011, International encyclopedia of systems and cybernetics, 2nd edn., Walter de Gruyter, München.
Fürber, C., 2015, Data quality management with semantic technologies, Springer, Wiesbaden.
Grillo, A., 2018, 'Developing a data quality scorecard that measures data quality in a data warehouse', PhD thesis, Brunel University, London. [ Links ]
Hand, D., 2018, 'Statistical challenges of administrative and transaction data', Journal of the Royal Statistical Society: Series A 181(3), 555-605. https://doi.org/10.1111/rssa.12315 [ Links ]
Hagerty, J., 2016, 2017 planning guide for data and analytics, Gartner Technical Professional Advice, Stamford, CT, 13 October 2016.
Haneem, F., Kama, N. & Kazmi, A., 2016, 'Master data identification in public sector organisations', Advanced Science Letters 22(10), 2999-3003. [ Links ]
Henke, N., Bughin, J., Chui, M., Manyika, J., Saleh, T., Wiseman, B. et al., 2016, The age of analytics: Competing in a data-driven world, McKinsey Global Institute, McKinsey & Company, San Francisco, CA.
Holcomb, Z.C., 2016, Fundamentals of descriptive statistics, Routledge, New York, NY.
Infovest, 2018, Introduction to data governance, Rondebosch, Cape Town.
Keller, S., Korkmaz, G., Orr, M., Schroeder, A. & Shipp, S., 2017, 'The devolution of data quality: Understanding the transdisciplinary origins of data quality concepts and approaches', Annual Review of Statistics and Its Application 4, 85-108. https://doi.org/10.1146/annurev-statistics-060116-054114 [ Links ]
Kumar, R., 2014, Research methodology: A step-by-step guide for beginners, Sage, Los Angeles, CA.
Lin, S., Gao, J., Koronios, A. & Chanana, V., 2007, 'Developing a data quality framework for asset management in engineering organisations', International Journal of Information Quality 1(1), 100-126. [ Links ]
Liptak, B.G. (ed.), 2018, Instrument engineers' handbook, volume two: Process control and optimization, 4th edn., CRC Press, Boca Raton, FL.
Marais, H., 2017, 'Assessing the data quality of performance information generated by the health sector in the Breede Valley subdistrict for evidence-based decision-making', Master's dissertation, University of Stellenbosch, Cape Town. [ Links ]
Marev, M., Compatangelo, E. & Vasconcelos, W., 2018, Towards a context-dependent numerical data quality evaluation framework, Technical Report, University of Aberdeen, Aberdeen.
McGilvray, D., 2010, Executing data quality projects: Ten steps to quality data and trusted information, Publishing House of Electronics Industry, Beijing.
McKenzie, S., 2014, Vital statistics: E-book: An introduction to health science statistics, Elsevier Australia, Chatswood, NSW.
Mele, C., Pels, J. & Polese, F., 2010, 'A brief review of systems theories and their managerial applications', Service Science 2(1-2), 126-135. https://doi.org/10.1287/serv.2.1_2.126 [ Links ]
Milham, M.P., 2012, 'Open neuroscience solutions for the connectome-wide association era', Neuron 73(2), 214-218. https://doi.org/10.1016/j.neuron.2011.11.004 [ Links ]
Nazim, M. & Mukherjee, B., 2016, Knowledge management in libraries: Concepts, tools and approaches, Chandos Publishing, Cambridge.
Neely, P. & Pardo, T., 2002, Teaching data quality concepts through case studies, Centre for Technology in Government, Albany, NY.
Nelke, S., Oberhofer, M., Saillet, Y. & Seifert, J., 2015, Method and system for accessing a set of data tables in a source database, U.S. Patent 2015/0066987 A1, 05 March 2015.
Nieuwenhuis, J., 2014, 'Analysing qualitative data', in K. Maree (ed.), First steps in research, pp. 99-103, Van Schaik Publishers, Pretoria.
Oracle Cloud, 2015, The role of data integration in public, private, and hybrid clouds, Redwood Shores, CA.
Oracle Corporation, 2011, Oracle master data management, An Oracle White Paper, September 2011, Redwood Shores, CA.
Organisation for Economic Co-operation and Development (OECD), 2016, 'Using big data in tax administrations', in Technologies for better tax administration: A practical guide for revenue bodies, pp. 47-73, OECD Publishing, Paris.
Orr, K., 1998, 'Data quality and systems theory', Communications of the ACM 41(2), 66-71. https://doi.org/10.1145/269012.269023 [ Links ]
Palavitsinis, N., 2013, 'Metadata quality issues', PhD thesis, Alcalá de Henares, Madrid. [ Links ]
Pipino, L.L., Lee, Y.W. & Wang, R.Y., 2002, 'Data quality assessment', Communications of the ACM 45(4), 211-218. https://doi.org/10.1145/505248.506010 [ Links ]
Rambe, P. & Bester, J., 2016, 'Financial cost implications of inaccurate extraction of transactional data in large African power distribution utility', Problems and Perspectives in Management 14(4), 112-123. https://doi.org/10.21511/ppm.14(4).2016.14 [ Links ]
Rothbad, A., 2015, Quality issues in the use of administrative data records, pp. 3-38, University of Pennsylvania, Philadelphia, PA.
Sebastian-Coleman, L., 2012, Measuring data quality for ongoing improvement: A data quality assessment framework, Elsevier, Waltham, MA.
Silberschatz, A., Korth, H. & Sudarshan, S., 2006, Database system concepts, Higher Education Press, Beijing.
Singh, H., 2018, Using analytics for better decision-making, viewed 01 April 2020, from https://towardsdatascience.com/using-analytics-for-better-decision-making-ce4f92c4a025?gi=ea4ae2c019a2
Skyttner, L., 2001, General systems theory: Ideas and applications, World Scientific River Edge, NJ.
Statistics Divisions of UN/DESA and UN Economic Commission for Europe, 2015, Results of the UNSD/UNECE survey on organizational context and individual projects of big data, Statistics Divisions of UN/DESA and UN Economic Commission for Europe, New York, NY, 03-06 March 2015.
Vermaat, M.E., 2014, Discovering computers and Microsoft Office 2013: A fundamental combined approach, Cengage Learning, Boston, MA.
Wang, R.Y. & Strong, D.M., 1996, 'Beyond accuracy: What data quality means to data consumers', Journal of Management Information Systems 12(4), 5-33. https://doi.org/10.1080/07421222.1996.11518099 [ Links ]
World Economics, 2017, The data quality index (DQI), viewed 03 January 2018, from https://www.worldeconomics.com/Pages/Data-Quality-Index.aspx.
 Correspondence:
Correspondence:
Patient Rambe
prambe@cut.ac.za
Received: 16 July 2019
Accepted: 23 Feb. 2020
Published: 19 May 2020
1 . Because of intense scrutiny from civil society, this state-owned enterprise (SOE) is under pressure owing to its financial losses and allegations of malpractices, and therefore its name has been anonymised as APGDCO.
^rND^sArun^nK.^rND^sJabasheela^nL.^rND^sBatini^nC.^rND^sCappiello^nC.^rND^sFrancalanci^nC.^rND^sMaurino^nA.^rND^sBrackstone^nG.^rND^sCai^nL.^rND^sZhu^nY.^rND^sHand^nD.^rND^sHaneem^nF.^rND^sKama^nN.^rND^sKazmi^nA.^rND^sKeller^nS.^rND^sKorkmaz^nG.^rND^sOrr^nM.^rND^sSchroeder^nA.^rND^sShipp^nS.^rND^sLin^nS.^rND^sGao^nJ.^rND^sKoronios^nA.^rND^sChanana^nV.^rND^sMele^nC.^rND^sPels^nJ.^rND^sPolese^nF.^rND^sMilham^nM.P.^rND^sOrr^nK.^rND^sPipino^nL.L.^rND^sLee^nY.W.^rND^sWang^nR.Y.^rND^sRambe^nP.^rND^sBester^nJ.^rND^sWang^nR.Y.^rND^sStrong^nD.M.^rND^1A01^nLucian T.^sde Koker^rND^1A01^nTanya^sdu Plessis^rND^1A01^nLucian T.^sde Koker^rND^1A01^nTanya^sdu Plessis^rND^1A01^nLucian T^sde Koker^rND^1A01^nTanya^sdu PlessisORIGINAL RESEARCH
Research as a service offering of knowledge management firms in the Fourth Industrial Revolution
Lucian T. de Koker; Tanya du Plessis
Department of Information and Knowledge Management, College of Business and Economics, University of Johannesburg, Johannesburg, South Africa
ABSTRACT
BACKGROUND: The fourth industrial revolution (4IR) is primarily based on innovative new technologies, such as artificial intelligence, robotics, and the Internet of Things, which is generally considered as a driving force behind recent global changes. This revolution is reshaping economies, the global landscape and business ecosystems. The 4IR is disrupting the status quo of traditional business operations.
OBJECTIVE: The research objective was to determine how a newly-developed information and knowledge management framework can be used as an enabler for knowledge management (KM) firms to successfully conduct business in the 4IR, further establishing if new innovative services are required for KM firms in the 4IR.
METHODS: Qualitative research methodology was used to select business cases, and critical case sampling was used for the selection of interviewees. Structured content analysis was conducted on the business cases, and in-depth face-to-face interviews were conducted with the interviewees.
RESULTS: The result was the development of an information and knowledge management framework that can be used as a new 4IR enabler by KM firms. The research elaborates on a new service offering that was developed specifically for the KM firm, namely Research as a Service.
CONCLUSION: Knowledge management firms need to adapt their existing business frameworks, business models and commercialisation lifecycles, to ensure that the business is prepared for successful business operations in the 4IR.
Keywords: fourth industrial revolution; information and knowledge management framework; knowledge management firm; Research as a Service; business models.
Introduction
The fourth industrial revolution (4IR) was announced and recognised in Germany in the year 2011. It would be beneficial for professional business firms, especially entrepreneurs and small businesses, to proactively understand what is required of a business to remain competitive in the 4IR. Over the past couple of years, a rise in the growth and development of technologies of the 4IR has been seen, specifically, artificial intelligence (AI), the Internet of Things, and robotics. Various economies and organisations have realised the need for upskilling for the 4IR and have started to invest in such efforts. Schwab (2016a, 2016b), notes that the 4IR is primarily characterised by a range of new technologies, such as AI, the Internet of Things and robotics, through which the interconnectedness of physical, digital and biological worlds will be seen, with a direct impact on all economies, businesses and industries. With the 4IR bringing the colossal change as depicted by Schwab (2016a), it is imperative that new frameworks are adopted for conducting business.
Professional business consulting firms increasingly include information and knowledge management (IKM) in their business consultation services:
Information and knowledge management is defined as the simultaneous management of numerous processes associated with both information (information management) and knowledge (knowledge management), to generate and contribute to the overall competitiveness of an organisation. (De Koker 2019:xiii)
An IKM framework for knowledge management (KM) firms is required, to improve the likelihood of successful business in the 4IR.
With the advent of the 4IR and all the changes that are associated with the 4IR, businesses will need to upskill, change and prepare for the 4IR in order to be competitive (Forbes 2018; Matskevich 2018). This study developed an IKM framework specifically for KM firms to be utilised by them as a guideline for successful business operations in the 4IR. Furthermore, a new service offering was developed, namely, Research as a Service (RaaS), implemented through the Research Methodology Value Proposition (RMVP). As the definition of IKM provided above states, the IKM framework was developed with the stance that business processes associated with both information (information management) and knowledge (knowledge management), should be included and managed in the IKM framework.
The objective for this research was:
-
to determine how a newly-developed information and knowledge management framework can be used as an enabler for knowledge management firms to successfully conduct business in the 4IR.
-
to determine if new innovative services are required for KM firms in the 4IR.
In order to adhere to the objective of the study, a literature review of information and knowledge management elements was done, as can be found in the next section.
Literature review
The IKM framework used as an enabler for KM firms to conduct business in the 4IR was a newly-developed tool, and was based on five IKM elements. The five IKM elements are pivotal in the IKM framework, under which 25 criteria exist. The five IKM elements that will be discussed here are: (1) components of a commercialisation lifecycle, (2) components of the business model canvas, (3) features of digital business transformation, (4) features of the 4IR, and (5) principles of strategic information management.
Components of a commercialisation lifecycle
Razak, Murray and Roberts (2014:262) explain that 'commercialisation success is about converting ideas and new innovations into new marketable products'. Many researchers view commercialisation as a process, with innovation being introduced into the market. Innovation can be a product and or a service (Bers et al. 2008; Cannatelli et al. 2017; Razak et al. 2014). The components of the commercialisation lifecycle (CLC) made up six of the 25 criteria in the IKM framework, namely: (1) idea generation, (2) research, (3) concept development and testing, (4) analysis, (5) product or service development, market testing and marketing, and (6) commercialisation stage.
Dehghani (2015) explains that for any business to turn a service into a profit, the service needs to undergo commercialisation. In order to create economic value it is necessary to 'build a successful profitable business', which means 'creative ideas should be commercialized' (Dehghani 2015:193). For every business, its CLC would be unique. Different businesses may share elements of CLCs but are ultimately different in stages. There exist no specific CLC suitable for all organisations and contexts (Ismail, Nor & Sidek 2015:288), therefore a unique CLC is adapted for the IKM framework.
Idea generation is crucial for innovation, which is the starting point and first stage in the CLC (Dehghani 2015:196; Foss et al. 2013:28). Innovation is not a specific stage in the CLC; however, innovation is important for idea generation and idea generation is important for innovation (Ojasalo & Ojasalo 2018a, 2018b). Furthermore, Gurtner and Reinhardt (2016:34) believe that 'idea generation is the most important part of the innovation process because it is the starting point'.
Research is done to understand the feasibility, eligibility and appetite for the idea (to become a service) in any given market (Bansi 2016:357; Khumalo & Du Plessis 2017:198; Ojasalo & Ojasalo 2018a). Thorough research can further reveal if the market is ready for such a service and determine if any competitors operate in the market, if any at all (Ojasalo & Ojasalo 2018b). According to Moore (2009:28), 'once a new idea or solution to a problem is recognized, that invention's viability must be researched and protected either with patents or secrecy'.
Depending on the type of business, concept development and testing differs from business to business and economy to economy (Drucker 1992, 1993; Kotter 2012; Moore 2009; Watson 2017). During the third stage of the CLC, concepts are developed and tested to determine which concept has the potential to move forward in the CLC.
In the analysis stage of the CLC, many ideas have been looked at, with only a few ideas remaining, as all the ideas have gone through a filtering process (Bansi 2016). The analysis stage forecasts the market demand, costs (production) involved, and the sales and profits (Ojasalo & Ojasalo 2018a). Analysed results will provide valuable intelligence on what the target markets expect (Illbury 2012; Jordan 2010).
During the product or service development, market testing and marketing stage, the actual product or service is developed as a prototype (Bansi 2016; Moore 2009; Razak et al. 2014). The prototype is offered to a group of clients, who then scrutinise the offering. Product or service development, market testing and marketing allow for improvement of the prototype, basically having the prototype in an iterative cycle in this stage, until the prototype is transformed into the actual product or service (Furr & Dyer 2014; Watson 2017).
Once the development of the product or service is complete, the product or service is sold at a price to the target market, as was established in the analysis stage. Innovation can be commercialised successfully to the market, leading to improved income streams (Latif, Abdullah & Jan 2016:94). At this stage, the product or service is sold, and a profit is generated. The process of commercialisation 'is a cycle whereby a given input passes through a series of stages to reach a specific output and in every stage some value is added to it' (Dehghani 2015:193).
Components of the business model canvas
'A business model describes the rationale of how an organization creates, delivers, and captures value' (Ojasalo & Ojasalo 2018b:72; Osterwalder & Pigneur 2010:14). Nine building blocks are found in the business model canvas (BMC), namely: (1) customer segments, (2) value propositions, (3) channels, (4) customer relationships, (5) revenue streams, (6) key resources, (7) key activities, (8) key partners, and (9) cost structure. These building blocks made up nine of the 25 criteria in the IKM framework.
'The customer segments building block defines the different groups of people or organizations an enterprise aims to reach and serve' (Ojasalo & Ojasalo 2018b:72; Osterwalder & Pigneur 2010:20). The customer segments building blocks for the KM firm include Government Institutions, Private Companies, Small Businesses and Entrepreneurs. The KM firm focuses on the above as its core customers, with a view that a beneficial and mutual relationship can be maintained. Customers are core to the KM firm, which results in profitability. 'In order to better satisfy customers', the KM firm will group the customers into 'distinct segments with common needs, common behaviors, or other attributes' (Osterwalder & Pigneur 2010:20). The KM firm has to ensure that the business model is designed around 'a strong understanding of specific customer needs' (Osterwalder & Pigneur 2010:20).
'The value propositions building block describes the bundle of products and services that create value for a specific Customer Segment' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:22). The value proposition sets the KM firm apart from its competitors. The value proposition offers something unique to the customer; it solves a customer's problem and provides a product or service based on the customer's need.
'The channels building block describes how a company communicates with and reaches its customer segments to deliver a Value Proposition' (Ojasalo & Ojasalo 2018b:72; Osterwalder & Pigneur 2010:26). The channels for the KM firm include the KM firm's Website, Social Media, Direct Selling processes, and Referrals from the KM firm's network. Channels are crucial to the KM firm, as they are the point(s) where the business interacts with the customer or potential customer.
'The customer relationships building block describes the types of relationships a company establishes with specific customer segments' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:28). The KM firm will ensure customer relationships are maintained through Client Relationship Management, dependent on project timelines (e.g. weekly, monthly). This can be face-to-face, telephonic, or through automated engagement.
'The revenue streams building block represents the cash a company generates from each customer segment (costs must be subtracted from revenues to create earnings)' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:30). Every project determines the revenue stream, based on the size and duration of a project. Resources working on a project will also have a determining factor on the revenue streams. Possible Revenue Streams for the KM firm will be determined based on the resources required for a specific project.
'The key resources building block describes the most important assets required to make a business model work' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:34). Any business requires resources to function optimally; specifically, for the KM firm, the Key Resources are Human Resources (Researchers) and Physical Assets (computers, data services, transportation). Researchers are insourced, who will be the primary resource for the KM firm.
'The key activities building block describes the most important things a company must do to make its business model work' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:36). The key activity for the KM firm is the RaaS.
'The key partners building block describes the network of suppliers and partners that make the business model work' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:38). The KM firm's key partners include Universities (Academic Researchers), Research Institutions, Entrepreneurs, and Small Businesses.
'The cost structure describes all costs incurred to operate a business' (Ojasalo & Ojasalo 2018b:73; Osterwalder & Pigneur 2010:40). The KM firm is initially funded by the founder, however additional funding is required to expand the business operations. Second round funding is required, in order to expand on Human Resources, and improving the RaaS and the RMVP (Value Proposition to render services).
Features of digital business transformation
According to Schwertner (2017:388), the use of new technologies for the development of new business models, new business processes, new workflows, new technologies, new software, new systems and new services leading to the improvement of business operations and efficiency, and further resulting in greater profit generation for the business, can be defined as digital business transformation (DBT). The features of DBT made up four of the 25 criteria in the IKM framework, namely: (1) innovation is key to the organisation, (2) big data are embedded in the organisation, (3) business process automation is found in the organisation, and (4) information security is key in the organisation.
According to Perkin and Abraham (2017):
Heightened pace and progression through broad and proficient adoption and application of digital-native processes including design thinking, agile and lean, continuous experimentation and a culture that supports constant testing and learning, coupled with an exhaustive, customer-centric innovation process that enables rapid origination, validation and commercialization of ideas […] (p. 55)
… relates to agility leading to innovation as key in the organisation. The KM firm ensures that innovation is embedded in the RaaS process. The RaaS process should, in turn, generate innovative results for the customer. The RMVP is thus achieved for the customer, ensuring that the customer is competitive in the 4IR.
In the DBT process, enormous amounts of data are produced, constituting big data (Geng 2017:13):
Data-driven decision-making is essential in the agile business. Data is central to the flow of knowledge into and within a business, to governance processes, performance optimization and customer experience delivery. (Perkin & Abraham 2017:158)
Many organisations struggle with big data, in that the organisation is unable to make sense thereof (Marr 2017:8-27). It is therefore important for the KM firm to ensure that it is able to provide RaaS in such a manner that it allows for the customer to make sense of the big data in the organisation (customer). This leads to the customer leveraging the 4IR, as big data is the backbone for technologies to be effective in the 4IR.
According to Perkin and Abraham (2017:161), 'business process automation, to communication and notification systems, customer service interaction, marketing automation and lead management, workflow automation can bring powerful efficiency benefits' to the organisation. Business process automation, however, does not mean that every process will be automated, as human intervention will be required when, for instance, formulating a strategy (Nakamura & Zeira 2018). With regard to the KM firm, RaaS should be offered in a manner which will allow for the customer to automate certain processes but be able to keep the human aspect embedded for certain processes and function, such as strategy development:
In response to privacy and data security laws […] businesses have expanded their protections to cover personal information about individuals. Partitioning off this information, responsible organizations have invested heavily in protecting the privacy and security of these data, and ensuring compliance with applicable legal requirements. Bruening et al. (2008:2)
With this in mind, Bruening et al. (2008:2) explain that 'a company's information assets must be managed in accordance with laws that are far broader than those regulating only privacy and information security'. Information security is crucial for any organisation operating in the 4IR and specifically for the KM firm; when offering RaaS or any other service to customers, the KM firm will have to ensure that information security is addressed according to appropriate laws and legislation geared for the 4IR.
Features of the fourth industrial revolution
The founder and executive chairman of the World Economic Forum, Klaus Schwab, explains in his book that humankind, like never before, is engaged in a revolution that will change the everyday lives of humanity (Schwab 2016a:1), and this revolution is known as the 4IR (Schwab 2016a:1). In some instances, this is also referred to as Industry 4.0 (Magruk 2016:275), with existing Industry 4.0 literature depicting that KM and decision-making strategies are crucial factors for organisations (Abubakar, Elrehailb & Alatailat 2017), and that the 4IR will bring colossal change to the world, in various economies, businesses and private life, which will happen at a much faster rate than ever anticipated or experienced in history (Schwab 2016a:1). The features of the 4IR made up three of the 25 criteria in the IKM framework, namely (1) AI, (2) robotics, and (3) the Internet of Things.
Makridakis (2018:18), explains that AI will have the most profound effect on firms and employment in the immediate future, 'for it is in the world of business, manufacturing, commerce, and government that AI will likely have the most profound effects on our lives, for good and ill' (Makridakis 2018:18). Skilton (2017) explains that AI technologies will provide new opportunities and a competitive advantage in the market for the business. The KM firm needs to take advantage of these new AI technologies, allowing for greater service delivery to customers:
The Internet of Things is a system consisting of networks of sensors, actuators, and smart objects whose purpose is to interconnect 'all' things, including every day and industrial objects, in such a way as to make them intelligent, programmable, and more capable of interacting with humans and each other. (Geng 2017:7)
In the 4IR, the KM firm needs to take advantage of the fact that everything is connected through the Internet of Things. This allows for collection of valuable data that can be used to make predictions about customers and future scenarios - referred to as predictive analytics:
Robotics is the industry related to the engineering, construction and operation of robots - a broad and diverse field related to many commercial industries and consumer uses. The field of robotics generally involves looking at how any physical constructed technology system can perform a task or play a role in any interface or new technology. (Technopedia 2018; https://www.techopedia.com/definition/32836/robotics)
Businesses and economies are being disrupted by new technologies in the 4IR, to an extent where the loss of jobs as a result of robotics, is becoming a concern. Businesses and economies will have to adapt current business models, providing skills development to those who are in the path of jobs being lost due to robotics.
Principles of strategic information management
Strategic information management (SIM) is defined as a situation in which 'information and related resources […] are used or utilized by an organization (profit or non-profit) to support, implement or achieve strategic position in order to gain competitive advantage/strategic advantage' (Hussin, Hashim & Yu 2018:292). Strategic information management focuses on the overall strategic management of all the confidential and non-confidential information (data, information, tacit and explicit knowledge, wisdom and intelligence) in any form (physical and electronic) in a business. In the context of the IKM framework, the IKM element SIM is used, with the view that SIM is crucial for any organisation to be competitive. Based on the assertions of Huggett, Hoos and Rensink (2007), Mutula and Wamukoya (2007), Davenport and Patil (2012), Zulu et al. (2012), and Bwalya and Saul (2014), four timeless principles for SIM have been identified for this study, namely: (1) information is a key asset to the organisation, (2) information is integrated in the overall strategy of the organisation, (3) information is managed strategically in the organisation, and (4) information is crucial to the success of the organisation
These four timeless principles made up the remaining four of the 25 criteria in the IKM framework.
Many researchers agree that the first principle, 'information is a key asset for any organisation', is an important factor adding to competitive advantage (Bruening et al. 2008; Galliers & Leidner 2003; ed. Galliers & Leidner 2014; ed. Galliers & Stein 2018; Hussin et al. 2018). Information is a key asset and should be managed strategically. In terms of the KM firm offering services to its customers, the KM firm needs to ensure that information is managed strategically as an information asset that is key to the customer's competitive advantage in the 4IR.
The second SIM principal states that 'information is integrated in the overall strategy of the organisation', and according to Hussin et al. (2018:293), SIM begins with mastering and understanding how to think strategically. During the SIM process, a strategic plan is developed, implemented and assessed for effectiveness. As a combination of strategic management and information management, SIM is crucial in order for an organisation to achieve its organisational objectives. With regard to the KM firm's service offering, it should offer RaaS strategically to customers, making sure that information is integrated in the overall strategy of the organisation.
The third SIM principle, 'information is managed strategically in the organisation', resonates with the declarations of Galliers and Leidner (2003:21), Dearstyne (2004:33), Bruening et al. (2008:3), and Hussin et al. (2018:293). Information should be managed strategically, taking into account that people and technology are key in the strategic management of information. Bruening et al. (2008), further states that:
[M]anaging information strategically not only mitigates risk, it shapes decisions about data to assure that this critical resource is available to the appropriate personnel when needed. It fosters sound investment in data and data systems that meet the diverse needs of the business. (p. 3)
With the support of technology, SIM adds to the overall competitiveness of an organisation through the alignment of organisational objectives with SIM objectives.
The fourth and last SIM principle, 'information is crucial to the success of the organisation' is supported by Galliers and Leidner (2003:19), Bruening et al. (2008:1), Iuga and Kifor (2014:32), and Hussin et al. (2018:293). They agree that the fourth principle leads to a competitive advantage for an organisation. Information is used strategically, aligned to the objectives of the organisation, giving the organisation a competitive advantage over competitors. The KM firm needs to ensure that when offering services to customers, information managed strategically should be instilled in the business models of customers.
Service offering - Research as a Service
Research in the CLC leads to the design of the service offering (Watson 2017). The service offering is referred to as RaaS. The primary service the KM firm offers is Research, referred to as RaaS, constituting a major component of the service offering of the KM firm. The RaaS offered by the KM firm is the competitive edge of the business. The actual value proposition is known as the Research Methodology Value Proposition (RMVP), not to be confused with the Research Methodology of the study. The RMVP is the method or process in which RaaS is conducted or offered, adding the value proposition perspective to the service offering.
Research methodology
According to Saunders, '[r]esearch is value bound, the researcher is part of what is being researched, cannot be separated and so will be subjective' (2009:119). This research study had the researcher embedded in every step of the research process, so interpretivism was selected for the study. The inductive research approach was chosen for the research. Saunders, Lewis and Thornhill (2012:165) explain that the collection of data to explore a 'specific phenomenon, identify themes and or explain patterns', refers to inductive reasoning, which is best suited for research where limited theory exists for what is being researched, leading to the development of theory through the analysis of data collected. Qualitative research was conducted to determine how the development of a new IKM framework can be used as an enabler for a KM firm to conduct business in the 4IR. The multi-method qualitative research method was used for this study. This was deemed appropriate, as two data collection techniques were used. The data collection techniques used were content analysis of 101 strategic information management business case studies (BCSs), and an interview process including four participants. The selection of participants for the interview process derived from the concept of content analysis. Methodological choices in terms of critical case sampling were selected under purposive sampling techniques, with the selection of BCSs based on the five IKM elements and 25 criteria used under the Nominal Ranking Technique, which was used to rank the BCSs based on their relevance. From the 101 BCSs, the top four were selected and used for the next phase in the research. The next phase was the interview process, during which three out of the four participants from the four BCSs were interviewed, in individual in-depth face-to-face interviews. The fourth participant was used in the triangulation process, to test the findings from the interviews and the content analysis.
Purposive sampling was best suited since it allowed the research to make use of critical case sampling, selecting critical cases on the basis of importance, in order to understand each case critically so that logical generalisations could be made (Saunders, Lewis & Thornhill 2009:240). The Data Analysis Spiral method which, according to Creswell (2013:182), is not a set process, but is rather customised for the specific research, was best suited for the study. The Data Analysis Spiral was specifically used to ensure the reliability and validity of the research, through continuous triangulation.
Ethical consideration
Ethical clearance was obtained from the Faculty of Management Faculty Ethics Committee, University of Johannesburg in 2016. Reference number: FOM2016-IKMNov2016_4.
Results and discussion
The newly-developed IKM framework is offered in the form of a service offering, namely RaaS. Research as a Service was coined as the service offering in the study, together with the methodology through which the RaaS is offered. The methodology is the value proposition, coined as the RMVP. Figure 1 illustrates how the five IKM elements and 25 criteria are housed in the IKM framework, each indicated with a different colour. The first element is the CLC, shown in red. The second element is the BMC (orange), the third element is DBT (green), the fourth element is the 4IR (purple), and the fifth element is SIM (blue).
The IKM framework is illustrated below in Figure 1.
The outer layer of the IKM framework shows the RaaS in the KM firm, which is the service offered by the KM firm. Within the RaaS in the KM firm, the RMVP (the value added to the RaaS) is found, namely, a method or process in which RaaS is conducted or offered to clients. The five IKM elements and 25 criteria are embedded in the RaaS. The KM firm renders RaaS to a client, making use of the IKM framework as a guideline for implementation in the client's business, as relevant for the 4IR. The RMVP is added to the RaaS through the five IKM elements and 25 criteria. A utopian situation will be achieved when all five IKM elements and 25 criteria are present within the business of the client. In the event where there are only certain IKM elements and criteria of the IKM framework in a client's business, the IKM framework should be used to guide the implementation of the missing IKM elements and criteria.
The IKM framework does not follow a specific order in which the five IKM elements and 25 criteria should be implemented in a business. Businesses differ; therefore implementation will depend on the needs of the business at that point in time. Based on the IKM framework, the elements are CLC, BMC, DBT, 4IR and SIM, and will be deliberated on in that order.
Evidence showed that the IKM framework will be beneficial to a KM firm and to clients of a KM firm. The evidence further showed that the IKM framework will add a unique value proposition (RMVP) to the service offering (RaaS) of a KM firm.
The IKM framework can be implemented systematically, differently for each client business, ensuring that the specific business need of the client is met. There is no prescribed order in which the IKM framework is implemented, however, when all five IKM elements and 25 criteria are implemented in the client's business, competitive advantage will be achieved. In order for a KM firm to achieve competitiveness in the 4IR, it is recommended that the IKM framework should be used as indicated. The application of the IKM framework could be beneficial to other types of businesses as well, keeping in mind that the implementation and application of the IKM framework will differ from business to business, based on the needs of the business.
Conclusion
The newly-developed IKM framework as an enabler provides KM firms with a guideline and business tool that can be utilised through systematic implementation and application, and which will lead to business competitiveness and success in the 4IR.
To grow the IKM framework to extensively include and cater for all business types, research can be done to determine if more than five IKM elements and 25 criteria should be included. Further, on the point of inclusion of other IKM elements and criteria, research can be done to determine if the 4IR element and criteria should be broadened.
Future research can also be done to determine if the proposed IKM framework could be linked to other existing business frameworks and business models. As the world changes and businesses change and grow, CLCs, BMCs, business frameworks and business models need to change and adapt to the changing environment. New CLCs, BMCs, business frameworks and business models will continually be required, therefore research should be done to determine how these CLCs, BMCs, business frameworks and business models will change and how these CLCs, BMCs, business frameworks and business models will adapt beyond the 4IR.
The RaaS as service offering and RMVP as method of implementing the RaaS, were developed in conjunction with the IKM framework, together offering a unique guideline to a KM firm for competitive business operations in the 4IR.
Acknowledgements
Competing interests
The authors declare that they have no financial or personal relationships that may have inappropriately influenced them in writing this article.
Authors' contributions
L.T.d.K. conducted the overall Master's study whilst registered as a student at the University of Johannesburg. T.d.P. supervised the study and contributed to the writing of the article.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The data that support the findings of this study are available from the corresponding author, L.T.d.K., upon reasonable request. The IKM framework (Figure 1), developed by the researcher (L.T.d.K.), is the intellectual property of said researcher.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abubakar, M.A., Elrehailb, H. & Alatailat, M.A., 2017, 'Knowledge management, decision-making style and organizational performance', Journal of Innovation & Knowledge 4(2), 104-114. https://doi.org/10.1016/j.jik.2017.07.003 [ Links ]
Bansi, R., 2016, 'Commercialization of university innovation in South Africa', DTech Public Management dissertation, Faculty of Management, Durban University of Technology, Durban. [ Links ]
Bers, J.A., Dismukes, J.P., Miller, L.K. & Dubrovensky, A., 2008, 'Accelerated radical innovation: Theory and application', Technological Forecasting & Social Change 76(2009), 165-177. https://doi.org/10.1016/j.techfore.2008.08.013 [ Links ]
Bruening, P.J, Sotto, L.J, Abrams, M.E. & Cate, F.H., 2008, 'Strategic information management', Privacy and Security Law Report 7(36), 1-3. [ Links ]
Bwalya, K.J. & Saul, Z.F.C., 2014, 'Unleashing the conceptual value of information management for organisational competitiveness: Semantic understandings', in K.J. Bwalya, N.M. Mnjama & P.M.M. Sebina (eds.), Concepts and advances in Information and Knowledge Management: Studies from developing and emerging economies, Chandos Publishing, Amsterdam; pp. 111-127.
Cannatelli, B., Smith, B., Giudici, A., Jones, J. & Conger, M., 2017, 'An expanded model of distributed leadership in organizational knowledge creation', Long Range Planning 50(2017), 582-602. https://doi.org/10.1016/j.lrp.2016.10.002 [ Links ]
Creswell, J.W., 2013, Qualitative inquiry and research design: Choosing among five approaches, 3rd edn., Sage Publications, Thousand Oaks, CA.
Davenport, T.H. & Patil, D.J., 2012, 'Data scientist', Harvard Business Review 90(5), 70-76. [ Links ]
Dearstyne, B., 2004, 'Strategic information management: Continuing need, continuing opportunities', The Information Management Journal 38(2), 28-36. [ Links ]
Dehghani, T., 2015, 'Technology commercialization: From generating ideas to creating economic value', International Journal of Organizational Leadership 4(2015), 192-199. https://doi.org/10.33844/ijol.2015.60449 [ Links ]
De Koker, L.T., 2019, 'The commercialisation lifecycle of a knowledge management consulting firm in the fourth industrial revolution', Master's dissertation, University of Johannesburg, Auckland Park. [ Links ]
De Koker, L.T. & Du Plessis, T., 2019, 'Development of a framework for a knowledge management firm in the fourth industrial revolution', in M. Twum-Darko (ed.), Pragmatic business solutions by Africa for Africa: 5th International Conference on Business and Management Dynamics 2019 proceedings, AMHI, Cape Peninsula University of Technology in collaboration with University of Namibia Business School, Swakopmund, September 02-04, 2019, pp. 109-121.
Drucker, P.F., 1992, 'The new society of organisations', Harvard Business Review 70(5), 95-104. [ Links ]
Drucker, P.F., 1993, Post-capitalist society, Butterworth Heinemann, Oxford.
Forbes, 2018, How is artificial intelligence changing the business landscape?, viewed 22 August 2018, from https://www.forbes.com/sites/quora/2018/07/31/how-is-artificial-intelligence-changing-the-business-landscape/#4553189b75f4.
Foss, N., Pedersen, T., Pyndt, J. & Schiltz, M., 2013, Innovation organization & management: New sources of competitive advantage, Cambridge University Press, Copenhagen.
Furr, N. & Dyer, J., 2014, 'Choose the right innovation method at the right time', Harvard Business Review 12, viewed 22 August 2018, from https://hbr.org/2014/12/choose-the-right-innovation-method-at-the-right-time. [ Links ]
Galliers, R.D. & Leidner, D.E., 2003, Strategic information management: Challenges and strategies in managing information systems, 2nd edn., Butterworth-Heinemann, Oxford.
Galliers, R.D. & Leidner, D.E. (eds.), 2014, Strategic information management: Challenges and strategies in managing information systems, 4th edn,. Routledge, Oxford.
Galliers, R.D. & Stein, D.E. (eds.), 2018, The Routledge companion to management information systems, Routledge, Oxford.
Geng, H., 2017, Internet of things and data analytics handbook, John Wiley & Sons, Inc., New Jersey, NJ.
Gurtner, S. & Reinhardt, R., 2016, 'Ambidextrous idea generation: Antecedents and outcomes', Product Development & Management Association 33(S1), 34-54. https://doi.org/10.1111/jpim.12353 [ Links ]
Huggett, M., Hoos, H. & Rensink, R., 2007, 'Cognitive principles for information management: The principles of mnemonic associative knowledge (P-MAK)', Minds & Machines 17, 451-485. https://doi.org/10.1007/s11023-007-9080-4 [ Links ]
Hussin, N., Hashim, H. & Yu, H., 2018, 'Strategic information management (SIM) in Malaysian organizations: An investigation of its antecedent', International Journal of Academic Research in Progressive Education and Development 7(3), 291-304, viewed 19 November 2018, from http://hrmars.com/hrmars_papers/Strategic_Information_Management_(SIM)_ In_Malaysian_Organizations_An_Investigation_of_its_Antecedent11.pdf. [ Links ]
Illbury, C., 2012, Welcome to the age of the fox thinking the future, Human & Rousseau, Cape Town.
Ismail, N., Nor, M.J.M. & Sidek, S., 2015, 'A framework for a successful research products commercialisation: A case of Malaysian academic researchers', Procedia - Social and Behavioral Sciences 195, 283-292, viewed 21 August 2018, from www.sciencedirect.com. [ Links ]
Iuga, V. & Kifor, C.V., 2014, 'Information and knowledge management and their interrelationship within lean organizations', Bulletin Scientific 1(37), 31-38. [ Links ]
Jordan, J.F., 2010, Innovation, commercialization, and the successful start-up, Heinz College, Carnegie.
Khumalo, S. & Du Plessis, T., 2017, 'Responsiveness of a South African university to the country's agenda for entrepreneurial universities', in Proceedings of the Africa Research Group 5th International Conference: Managing Organisations in Africa, University Of Mauritius in collaboration with University of Nottingham, Belle Mare, Mauritius, August 29-31, 2017.
Kotter, J.P., 2012, 'How the most innovative companies capitalize on today's rapid-fire strategic challenges and still make their numbers: Accelerate!', Harvard Business Review 97, 44-58. [ Links ]
Latif, N.S.A., Abdullah, A. & Jan, N.M., 2016, 'A pilot study of entrepreneurial orientation towards commercialization of university research products', Procedia Economics and Finance 37, 93-99, viewed 25 July 2018, from www.sciencedirect.com. [ Links ]
Magruk, A., 2016, 'Uncertainty in the sphere of the Industry 4.0 - Potential areas to research', Business, Management and Education 14(2), 275-291. https://doi.org/10.3846/bme.2016.332 [ Links ]
Makridakis, S., 2018, 'Forecasting the impact of artificial intelligence: Part 3 of 4: The potential effects of AI on businesses, manufacturing, and commerce', Foresight, viewed from https://foresight.forecasters.org.
Marr, B., 2017, Big data in practice, John Wiley & Sons, Inc., New Jersey, NJ.
Matskevich, D., 2018, Preparing your business for the artificial intelligence revolution, viewed 21 August 2018, from https://www.forbes.com/sites/forbestechcouncil/2018/07/12/preparing-your-business-for-the-artificial-intelligence-revolution/#ed5b6f27ac83.
Moore, V., 2009, 'Nano Entrepreneurship: Before nanotechnology can transform industries such as energy or biotech, its innovations have to be commercialized', Mechanical Engineering 131(4), 27-29. https://doi.org/10.1115/1.2009-APR-2 [ Links ]
Mutula, S.M. & Wamukoya, J., 2007, Web-based information management: A cross disciplinary approach, Chandos Publishing, Oxford.
Nakamura, H. & Zeira, J., 2018, Automation and unemployment: Help is on the way, viewed 21 August 2018, from https://voxeu.org/article/automation-and-unemployment-help-way.
Ojasalo, J. & Ojasalo, K., 2018a, 'Lean service innovation', Service Science 10(1), ii-iii, 1-109, C2. https://doi.org/10.1287/serv.2017.0194 [ Links ]
Ojasalo, J. & Ojasalo, K., 2018b, 'Service logic business model canvas', Journal of Research in Marketing and Entrepreneurship 20(1), 70-98. https://doi.org/10.1108/JRME-06-2016-0015 [ Links ]
Osterwalder, A. & Pigneur, Y., 2010, Business model generation, John Wiley & Sons, Inc., New Jersey, NJ.
Perkin, N. & Abraham, P., 2017, Building the agile business through digital transformation, Kogan Page Ltd, New York, NY.
Razak, A.A., Murray, P.A. & Roberts, D., 2014, 'Open innovation in universities: The relationship between innovation and commercialisation', Knowledge and Process Management 21(4), 260-269. https://doi.org/10.1002/kpm.1444 [ Links ]
Saunders, M., Lewis, P. & Thornhill, A., 2009, Research methods for business graduates, 5th edn., Pearson Education Limited, Essex.
Saunders, M., Lewis, P. & Thornhill, A., 2012, Research methods for business graduates, 6th edn., Pearson Education Limited, Essex.
Schwab, K., 2016a, The fourth industrial revolution, World Economic Forum, Geneva.
Schwab, K., 2016b, The fourth industrial revolution: What it means, how to respond, viewed 5 April 2018, from https://www.weforum.org/agenda/2016/01/the-fourth-industrial-revolution-what-it-means-and-how-to-respond/.
Schwab, K., 2018, The urgency of shaping the fourth industrial revolution, viewed 5 April 2018, from https://www.weforum.org/agenda/2018/01/the-urgency-of-shaping-the-fourth-industrial-revolution.
Schwertner, K., 2017, 'Digital transformation of business', Trakia Journal of Sciences 15(1), 388-393. https://doi.org/10.15547/tjs.2017.s.01.065 [ Links ]
Skilton, M., 2017, The impact of artificial intelligence on business, Warwick Social Sciences Policy Briefing, 4/2017, viewed 27 August 2018, from https://warwick.ac.uk/fac/soc.
Technopedia, 2018, Robotics, viewed 5 April 2018, from https://www.techopedia.com/definition/32836/robotics.
Watson, B., 2017, Design thinking as strategy, viewed from http://www.led.org.uk.
Zulu, S.F.C., Sebina, P.M., Grand, B. & Mutula, S.M., 2012, 'Benchmarking Botswana's e-government initiatives with WSIS Principles: A review of progress and challenges', in K. Bwalya & S. Zulu (eds.), Handbook of research on e-government in emerging economies: Adoption, e-participation, and legal frameworks, pp. 237-262, IGI Publishers, New York, NY.
 Correspondence:
Correspondence:
Lucian de Koker
Lucian.dekoker@gmail.com
Received: 05 Dec. 2019
Accepted: 02 Apr. 2020
Published: 11 June 2020
ORIGINAL RESEARCH
Contributing factors to increased susceptibility to social media phishing attacks
Heather J. Parker; Stephen V. Flowerday
Department of Information Systems, Faculty of Commerce, Rhodes University, Grahamstown, South Africa
ABSTRACT
BACKGROUND: The migration of phishing scams to social media platforms poses a serious information security threat to social media users. Users often remain unaware of the various phishing threats on social media and consequently they thoughtlessly engage on these platforms.
OBJECTIVES: The objective of this article was to identify the factors that contribute to an increased susceptibility to social media phishing attacks and propose a model to reduce this susceptibility.
METHOD: A systematic literature review was conducted in Emerald Insight, ScienceDirect and Google Scholar by using a search string. The identified articles underwent two rounds of screening and the articles thus included moved on to a quality assessment round. Finally, these articles were imported into MAXQDA where a content analysis was conducted, which involved extracting, coding and analysing the relevant data.
RESULTS: The final 25 articles included in the study indicated that women with low technical and security knowledge between the age of 18 and 25, who habitually use social media and process content heuristically, are more susceptible to phishing attacks. The insights gained from conducting this review resulted in developing a model that highlights the individuals who are most susceptible to phishing attacks on social media.
CONCLUSION: This article concludes that certain people are more susceptible to phishing attacks on social media as a result of their online habits, information processing, demographics, Information and Communications Technology (ICT) knowledge and personality traits. As such, these identified people should be more aware that they fall into this susceptibility group and thus should behave more cautiously when engaging on social media platforms.
Keywords: phishing; social media; information processing model; phishing; social media; information processing; awareness; personality traits.
Introduction
Social media websites have gained significant popularity over the years, with 3.484 billion users reported at the start of 2019 (Kemp 2019). The traditional platform for conducting phishing merely via email has evolved. Phishing attacks are now migrating to social media platforms, with a 30% increase in phishing links from the first quarter of 2018 (ProofPoint 2018). Consequently, phishing is still a serious cybersecurity threat, with phishers using social media sites such as Facebook, Instagram and Twitter to target significant numbers of victims. For instance, in the first quarter of 2018, fake Facebook pages were used to launch 60% of phishing attacks on social networks (Kaspersky 2018). Later, in 2019, phishing on Instagram and Facebook among others saw a 74.7% increase (Barker 2019). These statistics highlight that the threat of phishing shows no sign of retreating.
Phishing refers to 'a form of online identity theft that aims to steal sensitive information such as online passwords and credit card information' (Banu & Banu 2013:783). Phishing attacks are effective because they use social engineering techniques to persuade people into performing actions that will advance the phisher's attack (Frauenstein & Flowerday 2016). These social engineering techniques appeal to the victim's emotions and create a sense of trust by using personalised messages. Social media phishing attacks occur in two stages and result in high victimisation and a high success rate. During the first stage, the phisher sends a friend request to the prospective victim (Vishwanath 2015b). At this stage, the phisher can view the victim's friends and personal details. The second stage of the attack takes place when the phisher contacts the victim and requests information via a social media messaging platform such as Facebook messaging (Vishwanath 2015b). Such information requests are personalised using information provided on the user's wall, in posts, photos and news feeds. Messages include links and attachments that could infect the user's device with malware. These attacks lead to more victims, as other users connected to the first victim see the phisher as a mutual friend and believe that they are legitimate (Vishwanath 2015b).
Activities such as posting videos, comments, status updates and photos, as well as sending messages and liking posts, can be rewarding for users and thus encourage further use of social media platforms. This gratification fosters the frequent and repetitive use of social media, which, together with the inability to control these activities, results in people acquiring unconscious habits when engaging on these platforms (Vishwanath 2015b). The habitual use of social media may also make users more susceptible to phishing attacks because they do not process messages and links with enough attention to detail. This, coupled with certain character or personality traits, could lead to some users being more susceptible to phishing attacks than others.
The objective of this article was to identify the factors that contribute to an increased susceptibility to social media phishing attacks and to propose a model to reduce susceptibility. As such, the main research question is as follows:
Why are certain people more susceptible to phishing attacks on social media platforms than others?
Some users spend a considerable amount of time on social media sites and participate in repeated behaviours that form habits. These behaviours include habitually liking pages and posts, as well as not processing messages and comments adequately. To address the inadequate processing of phishing threats on social media, the theoretical foundation for this article is the heuristic-systematic model. This model states that people employ two modes of information processing when making assessments about received messages (Chaiken & Eagly 1989).
This article starts by providing an overview of the method. A review of the literature is then provided, as well as a discussion of the proposed model to reduce phishing susceptibility. The article concludes with a summary that highlights the implications of the findings for both individuals and organisations.
Method
A systematic literature review was conducted by using a post-positivist paradigm to explore why certain people are more susceptible to phishing attacks on social media. This review made use of argumentation theory to develop an argument that was balanced and well reasoned (Metcalfe & Powell 2000). As such, the argument was developed by providing evidence from the literature reviewed to reach conclusions related to the research question and synthesising these findings into a model that identifies people who are most susceptible to phishing attacks on social media.
A 'who', 'what', 'how' and 'where' (WWHW) table was created to ensure all the relevant search terms were present in the search string. Table 1 was developed to ensure that the main research question encapsulated all the aspects that needed to be covered in the review.

To develop the final search string, susceptibility had to be broken down into information processing and habits. Furthermore, demographics and personality traits were used to determine certain people within the search string.
The final search string used in ScienceDirect and Google Scholar was as follows: ('phishing' OR 'phishing attacks') AND ('information processing' OR 'heuristic systematic processing' OR 'cognitive processing') AND ('habits') AND ('personality traits' OR 'Big Five personality traits') AND ('social media' OR 'Facebook').
A shorter version of the search string had to be developed for Emerald Insight, as the database only allows a maximum of seven terms. The search string for Emerald insight was as follows: ('phishing' and 'phishing attacks') AND ('information processing' OR 'heuristic systematic processing') AND ('habits') AND ('personality types' AND 'social media').
Emerald Insight, ScienceDirect and Google Scholar were the bibliographical databases used in this review. ScienceDirect was used owing to the wide variety of academic journals it contains, encompassing current and relevant articles related to the topic. Similarly, Emerald Insight was chosen because it contains various current journals related to the field of information systems that do not delve into aspects that are too technical. Finally, Google Scholar was used for this search because it accesses multiple databases that have relevant peer-reviewed articles.
A total of 285 articles were identified by using the database search, with 177 results being identified in Emerald Insight, 68 results in ScienceDirect and 40 results in Google Scholar. A total of 14 duplicates were removed, leaving 271 articles to undergo a first round of screening. The first round of screening involved using inclusion and exclusion criteria to filter the results based solely on the title and abstract; subsequently, the number of included articles was reduced to 25. These 25 articles then underwent a second round of screening, which resulted in further nine articles being excluded, thus leaving 16 articles for inclusion. During the second round of screening, the articles had to focus on one or more aspects of the inclusion criteria. Thus, the articles had to discuss the personality traits, demographics and social media habits that influence the user's susceptibility to phishing on social media. Articles were excluded if they were irrelevant, too technical, in a foreign language, had a publication date prior to 2010 and/or focussed on the wrong platform such as mobile messages. Backward searching was applied to the 16 articles included by identifying useful works cited in these articles and, accordingly, nine useful articles were identified. These 25 articles moved on to a quality assessment round to ensure that the results presented in each article were trustworthy and met the specifications. This assessment, which is shown in Appendix 1, consisted of 14 questions divided into sections for design, conduct, analysis, conclusion and general. These questions were answered by assigning a ranking and the results were tallied to determine the final score for each article. An illustration of the study selection process is provided in the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) flow diagram in Appendix 2 (University of Carolina 2018). This diagram illustrates the flow of information through the phases of a systematic literature review.
The qualitative data analysis software tool MAXQDA was used to extract, code and analyse the data from the sample of articles found in Appendix 3. MAXQDA was used for performing the content analysis of the sample of articles generated through the systematic literature review. The data extraction process included collecting all the data pertaining to the main research question and sub-questions. This was performed by grouping sections of text from each article together with a corresponding code. By using codes, the researcher was able to concentrate on specific aspects of the data found in an article (Nowell et al. 2017). Table 2 depicts the number of tags for each code. This refers to the number of times a code appeared in the 25 articles imported into MAXQDA.
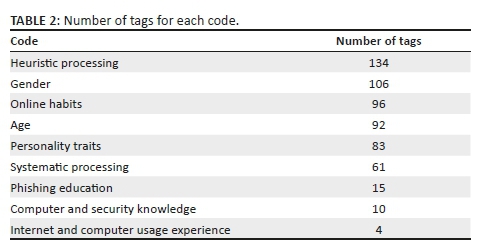
Results gathered from this tagging process were analysed and thematic analysis was conducted to combined codes that focussed on similar aspects into themes, which can be seen in Figure 1. Thus, heuristic processing and systematic processing were combined to create the information processing theme; age and gender were combined to create the demographic theme; and phishing education, computer and security knowledge, and Internet and computer usage experience were combined to form Information and Communications Technology (ICT) knowledge. Following this, a data extraction table was created to report the results of this process and to highlight the similarities and differences among the articles. Figure 2 shows a chart depicting the number of articles that discussed each theme. Where an article discussed more than one theme, it was counted in several themes. As may be seen, some themes were studied extensively in comparison with the others. The findings related to the overarching themes are discussed in the next section as factors that influence phishing susceptibility.

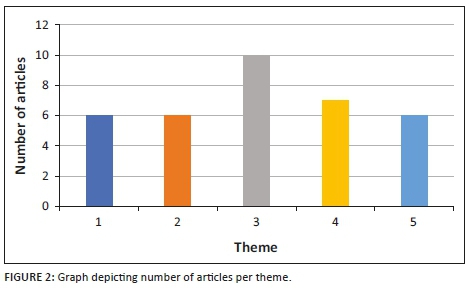
Factors influencing susceptibility to phishing attacks on social media
In this section, a discussion of the themes identified that influence a user's susceptibility to phishing on social media is presented. These themes will inform the creation of the phishing reduction model in the following section.
Information processing
The first factor identified that influences a user's susceptibility to phishing attacks refers to the way in which users process the messages, posts and comments that they encounter on social media. The articles related to information processing on social media discussed the two modes of processing found in the heuristic-systematic model (Chaiken & Eagly 1989). The choice of which processing method to employ is determined by the individual's perception of the sufficiency of the available information (Chaiken & Eagly 1989). In terms of the heuristic-systematic model, individuals utilise both heuristic processing and systematic processing. The former involves using simple heuristic cues that utilise limited cognitive resources to make judgements and decisions (Vishwanath, Harrison & Ng 2016), although the latter involves carefully examining information to reach a decision or make a judgement (Harrison, Vishwanath & Rao 2016). Thus, systematic processing is effortful and requires the use of far more cognitive resources than heuristic processing, which is more efficient and time sparing (Vishwanath et al. 2016). Overall, individuals predominantly use heuristic processing (Harrison et al. 2016; Vishwanath et al. 2016). The risk of information overload on social media and technology affordances encourages individuals to process content heuristically, which leads to quick and effortless judgements (Lin, Spence & Lachlan 2016). Consequently, although processing content heuristically is far more efficient, it significantly increases an individual's susceptibility to phishing attacks (Harrison et al. 2015; Hong 2012; Vishwanath et al. 2011, 2016); the reason for this is that when processing messages heuristically individuals often overlook informational cues that suggest the message is malicious and might pose a threat. Because heuristic processing relies on judging the credibility of information based on superficial cues, users often trust phishing messages (Frauenstein & Flowerday 2016).
Online habits
Online habits have also been found to influence phishing susceptibility, with habitual Facebook use resulting in an increased susceptibility to social media phishing attacks (Vishwanath 2014, 2015b). Users who are highly active on social media platforms are more susceptible to social engineering attacks than those who participate less often (Vishwanath 2015b). Furthermore, an individual's online habits influence the way they process misleading social engineering methods on social media sites (Frauenstein & Flowerday 2016). Thus, poor online habits increase susceptibility because individuals automatically click on links and respond to messages without engaging sufficient cognitive resources or paying enough attention to their online behaviour (Frauenstein & Flowerday 2016; Vishwanath 2015a; Vishwanath et al. 2011). For example, it was determined that individuals who habitually use Facebook are more likely to fall for phoney profiles created to target users and are more prone to reveal sensitive personal information requested by a phisher (Vishwanath 2015b). Thus, online habits influence an individual's susceptibility to fall for phishing on social media by causing them to follow ritualised patterns of social media use that involve little cognitive engagement when using the platform. This increases the probability that these users will thoughtlessly click on malicious links in a message or accept a friend request from a fake profile without thinking about the potential consequences of these actions (Vishwanath 2015b). Behaviours such as clicking on links, sharing and liking posts, and scrolling through posts regularly result in the user not paying attention to suspicious information on social media (Frauenstein & Flowerday 2016). One explanation regarding why Facebook habits lead to an increased vulnerability to social media phishing attacks is that these habits may negatively influence a user's trust and risk perception (Albladi & Weir 2016).
Demographic factors
The next factor that influences susceptibility to phishing attacks is age and gender. Users classified as youth between the ages of 18 and 25 were identified as being the most susceptible to phishing attacks on both email and social media platforms (Algarni, Xu & Chan 2015; Darwish, El Zarka & Aloul 2012; Sheng et al. 2010). This finding is plausible as younger users may be more susceptible to social media phishing because they are constantly engaging on the Internet, and this extensive use often results in Internet addiction (dependence) (Smahel, Brown & Blinka 2012). Excessive Internet and social media use creates ample opportunities for these young people to be targeted by a phisher who gains access to their account to spread malicious links, hijack the accounts of their friends or family and gather information on a specific person for a more targeted attack (Brecht 2017). It should also be noted that age has been linked to risky behaviour, with adolescents in particular being inclined to engage in such behaviour, which could increase their chances of being phished on social media (Sheng et al. 2010). Furthermore, younger users have less education, less distaste for financial risk and less exposure to phishing training (Sheng et al. 2010). Additionally, women have been identified as the most susceptible to phishing and social engineering (Algarni et al. 2015; Darwish et al. 2012; Goel, Williams & Dincelli 2017; Iuga, Nurse & Erola 2016; Sheng et al. 2010). Sheng et al. (2010) attribute this increased susceptibility to a lack of technical skills in comparison with men. In contrast, it has been postulated that women are easier to entice to open phishing emails, but are equally as capable and proficient as men in detecting a deceptive message (Goel et al. 2017).
Furthermore, various factors related to ICT knowledge influence susceptibility to phishing attacks, including computer and security knowledge, phishing education and Internet experience. Although only Algarni et al. (2015) and Albladi and Weir (2018) found that computer and security knowledge decreases a user's susceptibility to phishing attacks, this finding seems credible as greater knowledge increases the user's awareness of possible online social engineering threats and in turn provides them with an increased probability of being able to detect phishing attacks. According to Albladi and Weir (2018), contradictory results relating to whether computer or Internet knowledge reduces susceptibility to phishing exist; this might be because it is a general concept and its influence on risky or cautious online behaviour might be difficult to measure. Phishing education conducted through anti-phishing training received a weak result in this review, but the notion that exposure to phishing education is related to reduced susceptibility to phishing attacks is supported by other studies that fall outside the scope of this review, including Alnajim and Munro (2009), Dodge et al. (2011) and Jensen et al. (2017). Internet experience was also identified as a factor that influences phishing susceptibility, and although only Alseadoon et al. (2012) and Moody et al. (2011) found this factor to be important, the study conducted by Wright et al. (2010) supports this finding. Individuals who use the Internet frequently will have an increased awareness of the risks associated with the Internet and social media than individuals who do not use the Internet frequently. This is because frequent Internet users regard the probability of an online threat happening to them as greater than people who use the Internet less (Halevi, Lewis & Memon 2013). Thus, increased Internet experience increases a user's awareness of online threats.
Personality traits
Finally, personality traits were identified as influencing an individual's susceptibility to phishing attacks. The literature that discussed the influence of personality traits on phishing susceptibility in this study focussed on the Big Five model. This model uses the NEO Personality Inventory (NEO PI-R) to determine an individual's Big Five personality traits that assess their experiential, emotional, attitudinal, motivational and interpersonal facets (Costa & McCrae 1992). The Big Five personality traits linked with susceptibility to email-based phishing are extraversion, openness and agreeableness. As the same social engineering techniques that are employed in phishing emails are also employed on social media platforms (Frauenstein & Flowerday 2016), the personality traits of people who are most susceptible to email-based phishing can be applied to social media-based phishing. Individuals scoring high in extraversion are sociable, talkative, optimistic and driven (Costa & McCrae 1992). Hence, on social media, these individuals are likely to engage in greater amounts of social activity because of their sociable nature (Liu & Campbell 2017). Individuals with high openness to experience are curious and creative (Liu & Campbell 2017); online these individuals are curious, like to explore sites and are more likely to try all social media activities (Liu & Campbell 2017). Moreover, individuals scoring high on agreeableness are often trusting, amenable and giving (Costa & McCrae 1992). In a social media environment, these individuals are more likely to engage in online interaction; they are specifically more likely to engage in social networking activities with real-life friends (Liu & Campbell 2017). Interestingly, some studies found that users scoring high in agreeableness and contentiousness are prone to more secure behaviour online and are not more susceptible to phishing attacks (McCormac et al. 2017; Shropshire, Warkentin & Sharma 2015). However, these studies did not specifically test phishing susceptibility, whereas the studies by Darwish et al. (2012) and Alseadoon, Othman and Chan (2015) tested phishing susceptibility and found that high scores of agreeableness increase phishing susceptibility. Lastly, individuals scoring high in conscientiousness are less susceptible to phishing attacks (Darwish et al. 2012).
Model to reduce phishing
Based on the findings above, a model detailing how susceptible people should engage on social media to reduce the possibility of falling for phishing was developed. In this case, a model is a representation of the theoretical components identified by answering the research question. The model shown in Figure 3 proposes that individuals can reduce their susceptibility to phishing on social media by being aware of the individual factors that make them susceptible, by increasing their ICT knowledge and by processing information systematically. The model should be read from the inside out, starting with processing social media content and moving around the circle in a clockwise direction. The inner circle illustrates the four high-level factors that individuals need to address to reduce phishing on social media, and the outer circle identifies the specific aspects in these factors that the individual should consider and address. The interaction between the corresponding inner and outer circles is discussed at length in the following paragraph.
The most significant aspect proposed by the model to reduce phishing on social media is processing content systematically. This is proposed because it increases the likelihood that a user will correctly identify deceptive messages because they are consciously analysing the message content. By employing systematic processing, individuals are provided with more evidence of the validity of the information or message (Chaiken & Eagly 1989). Thus, systematic information processing is methodical and involves extensive, in-depth processing of the messages and information received (Chaiken & Eagly 1989). Although this method of processing information requires more cognitive effort, it significantly decreases susceptibility to phishing attacks on social media (Frauenstein & Flowerday 2016). To further reduce their susceptibility to social media phishing, individuals should have basic computer and security knowledge, as well as use the Internet frequently to increase their awareness of online threats and social engineering attacks. Furthermore, users can take an online anti-phishing training course to learn how to detect phishing attacks. Additionally, individuals should be aware of their habits on social media. Users who use social media habitually are more inclined to be absentminded and automatically provide requested personal information (Vishwanath 2015b). This awareness will allow them to be conscious of the way they use the platform and thus they could try to engage on social media in a conscious and attentive manner.
Moreover, individuals should be aware of potential individual factors that could increase their susceptibility to social media phishing such as their age, gender and personality traits. The age group that is most susceptible to phishing includes individuals between 18 and 25 years, and the gender that is more susceptible is female. Increased awareness of these factors could allow the individual to take preventative measures such as learning how to identify phishing scams and investing in phishing detection software. Finally, individuals should determine their personality traits by completing an online Big Five personality test (e.g. https://www.truity.com/test/big-five-personality-test) to see whether they are more inclined to fall for phishing attacks, which will give them the opportunity to try and behave in a more secure manner on social media. As illustrated by the model, individuals with high consciousness scores have a decreased likelihood of falling for phishing attacks. These individuals tend to be dutiful and industrious and follow the rules (Liu & Campbell 2017). Thus, the model postulates that if individuals process content systematically, increase their ICT knowledge, identify their personality traits and online habits and have an overall awareness of the most susceptible age group and gender, they should be less susceptible to phishing on social media.
Additionally, it is important to note that social media platforms provide controls and measures to educate users and prevent phishing attacks. For instance, Facebook launched phish@fb.com, a dedicated email address where users can report phishing attempts (Facebook 2012). This allows Facebook to investigate, blacklist and hold phishers accountable for their actions (Facebook 2012). They also provide users with information and steps to follow if a user has been phished on Facebook (2020a) or if their device is infected with malware (Facebook 2020b). Together both the user and the social media platform are responsible for preventing, reporting, dissolving and remaining aware of phishing attacks. The social media platform is responsible for educating users and providing controls to reduce phishing attacks. On the other hand, users bear the responsibility of staying informed regarding prevention techniques and using the controls put in place to reduce these incidents.
Limitations and future research
The main limitation of this review is that the effectiveness of the model has not yet been evaluated. As such, additional research could empirically test the proposed model and its ability to assist in reducing phishing susceptibility to social media phishing attacks. Moreover, country of residence could be investigated to determine the impact of culture, Internet access and education level on phishing susceptibility. This could also determine which countries are targeted most by social media phishing attacks. In addition, research should be conducted on how to mitigate the influence of incorrect information processing, online habits, demographics, ICT knowledge and personality traits. This research could include the controls social media platforms implement to reduce phishing attempts and preventative measures an individual could follow to reduce their susceptibility to social media phishing attacks. It would also be useful to test the effectiveness of these controls.
Conclusion
The increasing popularity of social media sites has led to the migration of phishing attacks to these platforms. Hence, phishing poses a serious threat to social media users, as phishers are able to target a significant number of victims across various platforms such as Facebook, Instagram, Twitter and Snapchat. In the face of evolving phishing threats, users often lack the awareness and ability to manage these threats, and thus they thoughtlessly engage on these platforms. As a result of this problem, the objective of this article was to identify the factors that contribute to phishing susceptibility on social media and produce a model that will reduce the likelihood that identified individuals would fall for phishing attacks on social media. To facilitate this, a systematic literature review was conducted to determine the specific factors that contribute to an increased susceptibility to phishing attacks on social media platforms. The method employed in this review started by determining a suitable search string, and after various rounds of screening a total of 25 articles were finally included in the content analysis. From these articles, it was established that women with low technical and security knowledge between the age of 18 and 25, who habitually use social media and process content heuristically, are more susceptible to falling for phishing attacks. These findings served as the basis for the proposed phishing reduction model that facilitates an increased awareness of the factors that influence a user's susceptibility to social media phishing. Based on the heuristic-systematic model, which served as the theoretical foundation of this article, the most significant aspect in the proposed model to reduce phishing on social media is processing content systematically. It is hoped that the individuals belonging to the susceptible groups identified, who follow the model, will reduce their susceptibility to falling for phishing attacks. Additionally, organisations can increase their knowledge of the specific factors that contribute to an increased susceptibility to social media-based phishing attacks. This will enable them to identify the specific groups that are susceptible to phishing attacks on social media to conduct targeted security training.
Acknowledgements
Competing interests
The views expressed in this article are that of the authors and not an official position of Rhodes University.
Authors' contributions
H.J.P. was responsible for the research and write-up of the article. S.V.F. acted in a supervisory capacity and was responsible for model refinement, manuscript review and submission.
Ethical consideration
This article followed all ethical standards for carrying out research.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Albladi, S.M. & Weir, G.R.S., 2016, 'Vulnerability to social engineering in social networks: A proposed user-centric framework', in Proceedings of the IEEE International Conference on Cybercrime and Computer Forensic (ICCCF), IEEE, Vancouver, Canada, June 12-14, 2016, pp. 1-6.
Albladi, S.M. & Weir, G.R.S., 2018, 'User characteristics that influence judgment of social engineering attacks in social networks', Human-Centric Computing and Information Sciences 8(5), 1-24. https://doi.org/10.1186/s13673-018-0128-7 [ Links ]
Algarni, A., Xu, Y. & Chan, T., 2015, 'Susceptibility to social engineering in social networking sites: The case of Facebook', in Proceedings of the 36th International Conference on Information Systems, AIS, Fort Worth, TX, December 13-16, 2015, pp. 1-23.
Alnajim, A. & Munro, M., 2009, 'An anti-phishing approach that uses training intervention for phishing websites detection', in Proceedings of the 6th International Conference on Information Technology: New Generations, IEEE, Las Vegas, NV, April 27-29, 2009, pp. 405-410.
Alseadoon, I., Chan, T., Foo, E. & Gonzales Nieto, J., 2012, 'Who is more susceptible to phishing emails?: A Saudi Arabian study', in Proceedings of the 23rd Australasian Conference on Information Systems, ACIS, Geelong, December 03-05, 2012, pp. 1-11.
Alseadoon, I., Othman, M. & Chan, T., 2015, 'What is the influence of users' characteristics on their ability to detect phishing emails?', in H.A. Sulaiman, M.A. Othman, M.F.I. Othman, Y.A. Rahim & N.C. Pee (eds.), Advanced computer and communication engineering technology, pp. 949-962, Springer, Cham.
Banu, M.N. & Banu, S.M., 2013, 'A comprehensive study of phishing attacks', International Journal of Computer Science and Information Technologies 4(6), 783-786. [ Links ]
Barker, I., 2019, Social media phishing attacks up more than 70 percent, viewed 15 September 2019, from https://betanews.com/2019/05/02/social-media-phishing/
Brecht, D, 2017, Phishing attacks targeting young adults, in Infosec, viewed 10 March 2020, from https://resources.infosecinstitute.com/phishing-attacks-targeting-young-adults/#gref
Chaiken, S. & Eagly, A.H., 1989, 'Heuristic and systematic information processing within and beyond the persuasion context', in J.S. Uleman & J.A. Bargh (eds.), Unintended thought, pp. 212-252, Guilford Press, New York, NY.
Costa, P.T. & McCrae, R.R., 1992, NEO Personality Inventory-Revised (NEO PI-R), Psychological Assessment Resources, Odessa, FL.
Darwish, A., El Zarka, A. & Aloul, F., 2012, 'Towards understanding phishing victims' profile', in Proceedings of the International Conference on Computer Systems and Industrial Informatics, pp. 1-5, IEEE, Sharjah, December 18-20, 2012.
Dodge, R., Rovira, E., Zachary, R. & Joseph, S., 2011, 'Phishing awareness exercises', in Proceedings of the 15th colloquium for Information Systems Security Education, pp. 120-125, CISSE, Fairborn, OH, June 13-15, 2011.
Facebook, 2012, New protections for phishing, viewed 11 March 2020, from https://www.facebook.com/notes/facebook-security/new-protections-for-phishing/10150960472905766/
Facebook, 2020a, What can I do if I've been phished on Facebook? viewed 11 March 2020, from https://www.facebook.com/help/166863010078512?faq=168134929914064#What-is-phishing?
Facebook, 2020b, What can I do about malicious software on Facebook? viewed 11 March 2020, from https://www.facebook.com/help/389666567759871
Frauenstein, E.D. & Flowerday, S.V., 2016, 'Social network phishing: Becoming habituated to clicks and ignorant to threats?', in Proceedings of the 15th International Conference on Information Security South Africa, IEEE, Johannesburg, August 17-18, 2016, pp. 98-105.
Goel, S., Williams, K. & Dincelli, E., 2017, 'Got phished? Internet security and human vulnerability', Journal of the Association for Information Systems 18(1), 22-44. https://doi.org/10.17705/1jais.00447 [ Links ]
Halevi, T., Lewis, J. & Memon, N., 2013, 'A pilot study of cyber security and privacy related behavior and personality traits', in Proceedings of the 22nd International Conference on World Wide Web, AMC, Rio de Janeiro, May 13-17, 2013, pp. 737-744.
Harrison, B., Vishwanath, A., Ng, Y. & Rao, R., 2015, 'Examining the impact of presence on individual phishing victimization', in Proceedings of the 48th Hawaii International Conference on System Sciences, IEEE, Kauai, HI, January 05-08, 2015, pp. 3483-3489.
Harrison, B., Vishwanath, A. & Rao, R., 2016, 'A user-centered approach to phishing susceptibility: The role of a suspicious personality in protecting against phishing', in Proceedings of the 49th Hawaii International Conference on System Sciences, IEEE, Koloa, HI, January 05-08, 2016, pp. 5628-5634.
Hong, J., 2012, 'The state of phishing attacks', Communications of the ACM 55(1), 74-81. https://doi.org/10.1145/2063176.2063197 [ Links ]
Iuga, C., Nurse, J.R.C. & Erola, A., 2016, 'Baiting the hook: Factors impacting susceptibility to phishing attacks', Human-centric Computing and Information Sciences 6(1), 1-20. https://doi.org/10.1186/s13673-016-0065-2 [ Links ]
Jensen, M., Dinger, M., Wright, R. & Thatcher, J., 2017, 'Training to mitigate phishing attacks using mindfulness techniques', Journal of Management Information Systems 34(2), 597-626. https://doi.org/10.1080/07421222.2017.1334499 [ Links ]
Kaspersky, 2018, Fake Facebook sites account for 60% of social network phishing in early 2018, viewed 16 September 2019, from https://www.kaspersky.com/about/press-releases/2018_social-network-phishing-early-2018
Kemp, S., 2019, Digital trends 2019: Every single stat you need to know about the Internet, viewed 16 September 2019, from https://thenextweb.com/contributors/2019/01/30/digital-trends-2019-every-single-stat-you-need-to-know-about-the-internet/
Lin, X., Spence, P. & Lachlan, K., 2016, 'Social media and credibility indicators: The effect of influence cues', Computers in Human Behaviour 63, 246-271. https://doi.org/10.1016/j.chb.2016.05.002 [ Links ]
Liu, D. & Campbell, W., 2017, 'The big five personality traits, big two metatraits and social media: A meta-analysis', Journal of Research in Personality 70, 229-240. https://doi.org/10.1016/j.jrp.2017.08.004 [ Links ]
McCormac, A., Zwaans, T., Parsons, K., Calic, D., Butavicius, M. & Pattinson, M., 2017, 'Individual differences and information security awareness', Computers in Human Behavior 69, 151-156. https://doi.org/10.1016/j.chb.2016.11.065 [ Links ]
Metcalfe, M. & Powell, L., 2000, 'Revisiting the argumentative research methodology', Communications of ACIS Proceedings, Brisbane, Australia, December 6-8, 2000, pp. 1-13.
Moody, G., Galletta, D., Walker, J. & Dunn, B., 2011, 'Which phish get caught? An exploratory study of individual susceptibility to phishing', European Journal of Information Systems 26(6), 564-584. https://doi.org/10.1057/s41303-017-0058-x [ Links ]
Nowell, L.S., Norris, J.M., White, D.E. & Moules, N.J., 2017, 'Thematic analysis: Striving to meet the trustworthiness criteria', International Journal of Qualitative Methods 16(1), 1-13. https://doi.org/10.1177/1609406917733847 [ Links ]
ProofPoint, 2018, The latest in phishing trends: October 2018, viewed 16 September 2019, from https://www.proofpoint.com/us/security-awareness/post/latest-phishing-october-2018.
Sheng, S., Holbrook, M., Kumaraguru, P., Cranor, L.F. & Downs, J., 2010, 'Who falls for phish?: A demographic analysis of phishing susceptibility and effectiveness of interventions', in Proceedings of the SIGCHI Conference on Human Factors in Computing Sytems, AMC, Atlanta, GA, April 10-15, 2010, pp. 373-382.
Shropshire, J., Warkentin, M. & Sharma, S., 2015, 'Personality, attitudes, and intentions: Predicting initial adoption of information security behavior', Computers & Security 49, 177-191. https://doi.org/10.1016/j.cose.2015.01.002 [ Links ]
Smahel, D., Brown, B. & Blinka, L., 2012, 'Associations between online friendship and Internet addiction among adolescents and emerging adults', Developmental Psychology 48(2), 381-388. https://doi.org/10.1037/a0027025 [ Links ]
University of Carolina, 2018, Creating a PRISMA flow diagram, viewed 20 November 2018, from https://guides.lib.unc.edu/prisma
Vishwanath, A., 2014, 'Diffusion of deception in social media: Social contagion effects and its antecedents', Information Systems Frontiers 17(6), 1353-1367. https://doi.org/10.1007/s10796-014-9509-2 [ Links ]
Vishwanath, A., 2015a, 'Examining the distinct antecedents of e-mail habits and its influence on the outcomes of a phishing attack', Journal of Computer-Mediated Communication 20(5), 570-584. https://doi.org/10.1111/jcc4.12126 [ Links ]
Vishwanath, A., 2015b, 'Habitual Facebook use and its impact on getting deceived on social media', Journal of Computer-Mediated Communication 20(1), 83-98. https://doi.org/10.1111/jcc4.12100 [ Links ]
Vishwanath, A., Harrison, B. & Ng, Y., 2016, 'Suspicion, cognition, and automaticity model of phishing susceptibility', Communication Research 45(8), 1146-1166. https://doi.org/10.1177/0093650215627483 [ Links ]
Vishwanath, A., Herath, T., Chen, R., Wang, J. & Rao, H.R., 2011, 'Why do people get phished? Testing individual differences in phishing vulnerability within an integrated, information processing model', Decision Support Systems 51(3), 576-586. https://doi.org/10.1016/j.dss.2011.03.002 [ Links ]
Wright, R., Chakraborty, S., Basoglu, A. & Marett, K., 2010, 'Where did they go right? Understanding the deception in phishing communications', Group Decision and Negotiation 19(4), 391-416. https://doi.org/10.1007/s10726-009-9167-9 [ Links ]
 Correspondence:
Correspondence:
Stephen Flowerday
s.flowerday@ru.ac.za
Received: 27 Nov. 2019
Accepted: 31 Mar. 2020
Published: 15 June 2020
^rND^sAlbladi^nS.M.^rND^sWeir^nG.R.S.^rND^sBanu^nM.N.^rND^sBanu^nS.M.^rND^sGoel^nS.^rND^sWilliams^nK.^rND^sDincelli^nE.^rND^sHong^nJ.^rND^sIuga^nC.^rND^sNurse^nJ.R.C.^rND^sErola^nA.^rND^sJensen^nM.^rND^sDinger^nM.^rND^sWright^nR.^rND^sThatcher^nJ.^rND^sLin^nX.^rND^sSpence^nP.^rND^sLachlan^nK.^rND^sLiu^nD.^rND^sCampbell^nW.^rND^sMcCormac^nA.^rND^sZwaans^nT.^rND^sParsons^nK.^rND^sCalic^nD.^rND^sButavicius^nM.^rND^sPattinson^nM.^rND^sMoody^nG.^rND^sGalletta^nD.^rND^sWalker^nJ.^rND^sDunn^nB.^rND^sNowell^nL.S.^rND^sNorris^nJ.M.^rND^sWhite^nD.E.^rND^sMoules^nN.J.^rND^sShropshire^nJ.^rND^sWarkentin^nM.^rND^sSharma^nS.^rND^sSmahel^nD.^rND^sBrown^nB.^rND^sBlinka^nL.^rND^sVishwanath^nA.^rND^sVishwanath^nA.^rND^sVishwanath^nA.^rND^sVishwanath^nA.^rND^sHarrison^nB.^rND^sNg^nY.^rND^sVishwanath^nA.^rND^sHerath^nT.^rND^sChen^nR.^rND^sWang^nJ.^rND^sRao^nH.R.^rND^sWright^nR.^rND^sChakraborty^nS.^rND^sBasoglu^nA.^rND^sMarett^nK.^rND^1A01^nSimeon A.^sNwone^rND^1A02^nStephen M.^sMutula^rND^1A01^nSimeon A.^sNwone^rND^1A02^nStephen M.^sMutula^rND^1A01^nSimeon A^sNwone^rND^1A02^nStephen M^sMutula
ORIGINAL RESEARCH
Active and passive information behaviour of the professoriate: A descriptive comparative pattern analysis
Simeon A. NwoneI; Stephen M. MutulaII
IInformation Studies Programme, School of Social Sciences, College of Humanities, University of KwaZulu-Natal, Pietermaritzburg, South Africa
IISchool of Management, IT and Governance, College of Law and Management Studies, University of KwaZulu-Natal, Pietermaritzburg, South Africa
ABSTRACT
BACKGROUND: The study explored and analysed patterns in active and passive information behaviour of the professoriate in different information sources in teaching and research context. Exploring patterns in human information behaviour fills the knowledge gaps in this under-researched area, besides having practical significance.
OBJECTIVES: The study explored the patterns in active and passive information behaviour in different information sources used by the professoriate in the social sciences and humanities in three federal universities in Nigeria.
METHODS: The study used a descriptive survey to explore the active and passive information behaviour of the professoriate. The sample consisted of 246 professors from the social sciences and humanities departments at three federal universities in Nigeria. Data were collected using an adapted questionnaire and analysed descriptively using the Statistical Package for Social Sciences.
RESULTS: The patterns that emerged across electronic resources, media, print sources, interpersonal and academic gathering, in three usage categories, showed both consistent and divergent results. A broad pattern in frequently-used sources revealed that the more active information seeking takes place in an information source, the more chances of passive encounters, and vice versa. This pattern is, however, consistent in electronic resources, print sources, and academic gathering, but differs in media and interpersonal sources. Media has more instances of passive encounters than active usage whilst in interpersonal sources, information encountered in active engagements with professional colleagues did not yield significant result.
CONCLUSION: Exploring patterns in human information behaviour is still evolving, with the benefit of advancing a better understanding of active and passive information behaviour at a micro level.
Keywords: information behaviour; professoriate; information sources; seeking; encountering.
Introduction
Active and passive information behaviour constitute part of the holistic human behaviour concerning uses of information resources and the channels through which information reaches users. Active information behaviour is the purposeful or intentional search for information to satisfy a goal, and usually requires the information seeker to make a demand on an information system in the form of request, search or query (Wilson 2000). Passive information behaviour, on the other hand, refers to the opportunistic discovery of information (Erdelez 1997; Toms & McCay-Peet 2009) and describes the unexpected encountering of useful information whilst engaged in other activities (Erdelez 1997). Academic faculties at the professorial level use both formal and informal methods to seek information to meet their teaching and research goals (Xuemei 2010) and, in the process, encounter valuable information for future use. Over the years, print sources have dominated the academic information environment, and encountering valuable information in them is not a new phenomenon, as serendipitous encounters have been the focus of researchers for many decades (McNally, Prier & MacMillan 2011; Van Andel 1994).
Furthermore, with the advent of information technology, electronic information resources have changed the way information is accessed, stored and used conveniently, and have become a dominant tool in the academia influencing scholarly communication in an unprecedented manner (Tahir, Mahmood & Shafique 2008). Besides the use of print sources for teaching and research, professoriates also seek information using electronic information resources such as online databases and electronic journals (Engel, Robbins & Kulp 2011; Rupp-Serrano & Robbins 2013). These platforms have equally become potent grounds for discovering useful information that can be stored electronically for future reference (Jiang, Liu & Chi 2015).
Active usage of information resources by the professoriate are found to differ across academic discipline, age, geographical boundaries, context (e.g. teaching, research) and individual orientation and disposition towards information resources (Hemminger et al. 2007; Marouf & Anwar 2010; Nwone & Mutula 2018; Rupp-Serrano & Robbins 2013; Singh & Satija 2007; Xuemei 2010). Generally, social science professors use electronic resources more than their counterparts in humanities, preferring electronic resources for research and print resources for teaching (Xuemei 2010). Social science professoriate studying stateless nations, besides using traditional methods, used the World Wide Web and email for locating relevant information (Meho & Haas 2001), whilst the professoriate of social science at the University of the West Indies preferred textbooks for teaching, followed by journals and monographs, and relied on e-journals and online database for current information (Hannah 2005). The professoriate in the Xuemei (2010) study used more electronic resources than print sources to meet their research needs, whilst their preference for electronic information resources varied across professorial ranks and disciplines. Professoriates in social sciences in Kuwait show heavy reliance on books and print journals for teaching and research due to lack of scholarly databases in Arabic. Conferences, subject experts and colleagues were their main informal sources of information (Marouf & Anwar 2010). For research endeavours, faculty of education professoriates in the United States used scholarly journals, internet resources and books, whilst face-to-face communication with colleagues was their informal means of obtaining information (Rupp-Serrano & Robbins 2013). Law faculty professors relied more on textbooks and law reports for information seeking. Their use of online databases was significantly low, implying heavy dependence on print over electronic sources (Aforo & Lamptey 2012; Thanuskodi 2009). In all these instances, there are bound to be some measures of information encountering. Information can be encountered more frequently in some sources and occasionally in other sources, whereas in other sources, information encountering rarely occurs.
The value of information encountered in an active process is of practical significance. It presents the need for platform developers to recognise the value of 'serendipitous information' and create a clipboard for users to place information encountered for future reference. This may require users to highlight the information of interest with an option to send the highlighted information to a 'serendipity clipboard'. It can help the library to re-align library services and channel marketing campaigns on frequently-used sources with high chances of serendipity.
Although studies (Erdelez 1997; Williamson 1998) have shown that useful information can be encountered in the process of deliberate information seeking and even when leisurely exposed to different forms of media, researchers have given little attention to this passive information behaviour. The role of passive information behaviour or information that is accidentally acquired, especially in an academic context, has not received adequate attention in information science literature. Haley, Wiessner and Robinson (2009) focused on encountering new information and perspectives in constructing knowledge in conference contexts. Foster and Ford (2003) examined the nature of serendipity in the information-seeking context of interdisciplinary scholars, whilst Marshall & Bly (2004) explored how people share information they encountered in their everyday reading. Stewart and Basic (2014) explored information-encountering experiences of undergraduate students and the potential role of personal information collection, management, and retrieval in information literacy instruction. The paucity of studies on passive information behaviour of academic faculties exacerbates the scantiness of studies on the relationship between active and passive information behaviour. The closest study comparing active and passive information behaviour was carried out by Pálsdóttir (2007) on health and lifestyle information seeking of Icelanders. The study found that those active in information seeking were also active in information encountering, and those who were passive in either of the two styles of information seeking were passive in the other. This study is highly significant as it advances knowledge on the connection between active and passive information behaviour in information science literature.
Actively seeking information for teaching and research using search engines and/or online databases is associated with salient but passive information gathering. The significance of information passively encountered during active information seeking has become an interesting topic for researchers (Erdelez 1997; Foster & Ford 2003; McBirnie 2008; Pálsdóttir 2007; Williamson 1998). Since active information seeking occurs in print and on digital platforms, and at an interpersonal level, passive information gathering is unsurprisingly expected and, in the view of Erdelez (2005:25), it is an integral part of the information-seeking process, not to be seen as a separate behaviour, describing it as a '… common element of users' behaviour'. The close association between these two activities warrants further empirical investigations. A cross analysis of patterns emanating from the associated information behaviours will make a significant theoretical contribution of advancing the understanding of human information behaviour at a micro level, besides laying a foundation for further empirical research.
This study focused on examining the active and passive information behaviour of the professoriate in selected universities in Nigeria and compared patterns inherent in the highly-correlated behaviour. Specifically, the patterns in the associated information behaviour will be examined across different information sources in three usage categories (frequently, occasionally and rarely) by the professoriate for teaching and research. The information sources are electronic and print sources, media, interpersonal and academic gathering.
Literature review
The literature review focused on empirical literature on active information behaviour (information-seeking behaviour) of the professoriate. Since literature that focused specifically on the professoriate are few, emphasis was placed on literature which included the professoriate population. A search on passive information behaviour in an academic faculties did not produce significant results, while are comparative literature on active and passive information behaviour is sparse. The reviewed literature unveiled the knowledge gaps filled by this study.
Active information behaviour
In a study of active information behaviour of the social science and humanities faculty in the United States, Xuemei (2010) showed that whilst social scientists tend to rely heavily on periodicals, humanities researchers rely more on books and primary sources. Overall, the respondents of the study used electronic resources to satisfy 58% of their research needs and print sources to satisfy 42% of their research needs. Despite the general preference for electronic information resources, individual differences exist amongst the professorial ranks and disciplines. A full professor in the history department was concerned about the availability of older materials in the discipline, justifying the relevance of print sources to his discipline. A professor in the African Studies department was not familiar with the library's electronic information resources and found it hard to evaluate electronic resources on the web, since the nature of his research relied more heavily on field studies and preferred print to the digitised. In Kuwait, the information-seeking behaviour of 10 professors, 25 associate professors and 19 assistant professors of social science (Marouf & Anwar 2010) suggests that the majority of the professoriate were heavily dependent on books and journals for teaching and research purposes. The professoriate were constrained to using print sources written in Arabic because of the scarcity of online databases that offer scholarly information in Arabic. They relied on conferences, subject experts and colleagues as informal sources of information. Active information behaviour of the social science faculty at the University of Bahawalpur, Pakistan, revealed that the faculty used books, periodicals, indexes, abstracts for teaching and research (Tahir et al. 2008). The majority of the participants were not satisfied with the current stock of books related to their fields as they found them inadequate in meeting their research needs. There was no mention of electronic journals or online databases as part of information sources, suggesting that the university has not fully embraced information technology to access electronic resources. Discussion with seniors and colleagues, seminars, workshops and conferences constitute their informal sources of gathering information. The study participants include 40 lecturers, 40 assistant professors, 10 associate professors, and 10 professors (Bhatti 2010). A study of information seeking behaviour of social science faculty at the University of West Indies, Jamaica (Hannah 2005), observed that textbooks were the preferred source of information for teaching, followed by journals and monographs. For current awareness, respondents named current issues of journals, followed by online database searches. Information sources used for teaching and research included citations at the end of journal articles and citations at the end of the chapters of a book. Meho and Haas's (2001) study on information seeking of the social science faculty studying stateless nations across countries of the United States, United Kingdom, Germany, Canada, Australia, France, Italy, Netherlands, Switzerland and Turkey, showed that besides using traditional methods, social science professors used the World Wide Web and email for locating relevant information. It shows that these faculty members are aware of and utilise information technology to support their research. Studying active information behaviour of the education faculty in the United States, Rupp-Serrano and Robbins (2013) uncovered the heavy dependence on scholarly journals for research by the faculty, followed by internet resources and books. Browsing current issues of journals, attending conferences, following references or leads from articles and personal communication were the most frequent means of staying current. Face-to-face interaction with colleagues is the informal means of obtaining information. Purposeful information seeking in the Law faculty at the Central Law faculty in Salem, India, had five professors, seven senior lecturers, 19 lecturers and 25 guest lecturers as study participants (Thanuskodi 2009). The author observed that the Law faculty relied more on text books and law reports for information seeking, whilst the use of online databases was significantly low, indicating that the professoriate in Law relied more on print resources than electronic sources. A similar study of the Law faculty in Ghana reported the use of law reports, law journals and textbooks to seek information, and further buttressed the heavy reliance on print resources by the Law faculty (Aforo & Lamptey 2012). The next section presents literature on passive information behaviour.
Passive information behaviour
Active information seeking has since dominated information science literature. The role of information acquired accidentally has not received sufficient empirical attention (Williamson 1998). Studies (Erdelez 1997; Foster & Ford 2003; Pálsdóttir 2007; Williamson 1998) have shown that useful information can be encountered in the process of a deliberate search for information. The term 'incidental information acquisition' is seen as synonymous with 'accidental information discovery', suggesting that people find information unexpectedly as they engage in other activities. Some of the information, they did not know they needed until they heard or read it. McKenzie (2003) used the term 'active scanning', referring to people being aware of the possibility of finding useful information in certain places although they are not seeking specific information. Erdelez (1997:412) used the term 'information encountering' for 'memorable experiences of accidental discovery of useful or interesting information'. Wilson (1999) used the term 'passive attention' for the unintentional discovery of useful information. In addition, Wilson (1999) coined 'passive searching', where a person discovers relevant information in the process of seeking for information. The term active scanning was used by McKenzie (2003), referring to an awareness of the likelihood of discovering valuable information in media when the person is not seeking for any specific information.
Haley et al. (2009) conducted a collaborative qualitative enquiry into encountering new information and perspectives in constructing knowledge in conference contexts. Collaborators in the inquiry included conference coordinators, university faculty researchers, doctoral student research assistants, and conference attendees. The findings of their research focused on patterns that emerged through data analysis. Initial open coding of the data revealed a pattern of interaction and engagement with conference content at two different levels. Participants may engage in the material, they may state their intention to act based on the material, and participants are more likely to report engagement than action.
Foster and Ford (2003) applied a naturalistic inquiry into the nature of serendipity in the information-seeking context of interdisciplinary scholars, both as a problem-solving strategy and a sheer mode of knowledge acquisition. The outcome suggests that serendipity was widely experienced amongst the interdisciplinary researchers. Serendipitously discovered information impacts on the discovery process by reinforcing or strengthening the researcher's existing problem, conception or solution, and taking the researcher in a new direction, in which the problem conception or solution is re-configured in some way (Foster & Ford 2003). Besides the impact of serendipity, the nature of serendipitous information is revealed in two ways: (1) the unexpected finding of information, the existence, and/or location of which was unexpected rather than the value, and (2) the unexpected finding of information that also proved to be of unexpected value (Foster & Ford 2003).
There is a dearth of research on passive information behaviour or information encountering of university faculties, especially at the professorial level. Besides, most previous studies (Foster & Ford 2003; Haley et al. 2009; Pálsdóttir 2007) used qualitative approaches with small samples. Furthermore, besides Pálsdóttir (2007, 2010), who examined the connection between purposive information seeking and information encountering in a study of Icelanders' health and lifestyle information seeking, comparing patterns between active and passive information behaviour in an academic context have not gained much attention in library and information science literature. This paper presents analysis from a larger quantitative study on the information behaviour of the professoriate in selected federal universities in Nigeria. The aim of this paper is to explore patterns that emerged from the comparison of active (purposive) and passive (encountering) information behaviour of the university professoriate.
Methodology
The study used a descriptive survey design to examine the information-seeking behaviour of the professoriate. The population of the study comprised 246 members of the professoriate from the social sciences and humanities department at the University of Ibadan, University of Lagos and Obafemi Awolowo University. A census survey using questionnaires that consists of self-structured and adapted questions from previous studies was used to collect quantitative data from the professoriate. Reliability of the constructs in the data collection instrument measured 0.88 on the Cronbach's alpha scale. The researcher made use of professional research assistants to collect data from the professoriate through personal visits to their offices. The research assistants were very familiar with the three universities and have good experience in research data collection. Collecting data from the professors was a daunting task, because of their regular unavailability in their offices and often-busy schedules, thereby prolonging the period of data collection, which took approximately 7 months, from January to July 2016. At the University of Lagos, 86 questionnaires were distributed, 48 collected and 40 found fit for data analysis. At the University of Ibadan, 91 questionnaires were distributed, 76 collected and 70 were suitable for analysis. At Obafemi Awolowo University, 69 questionnaires were distributed, 60 questionnaires were retrieved and 55 were appropriate for analysis. In all, 246 questionnaires were distributed, 184 were collected and 165 questionnaires were fit and coded for data analysis. The data were analysed using descriptive statistics with the Statistical Package for the Social Sciences (IBM Corp., Armonk, New York, United States).
Ethical consideration
The study followed all ethical procedures stipulated by the University of KwaZulu-Natal ethical committee. Protocol reference number: HSS/1444/015D.
Results
The results of the professoriate's active and passive information behaviour patterns are presented below.
Professoriate active information behaviour
The results presented in Table 1 on the active information seeking of the professoriate, describe the various information source categories (electronic resources, media, print resources, interpersonal sources, academic gathering) used by the professoriate to seek information for teaching and research.
Professoriate passive information behaviour
The respondents were asked whether they have encountered information in any of the information sources listed whilst deliberately seeking information to be used for teaching and research. Table 2 shows the results.
Comparing active and passive information behaviour - Descriptive analysis
Customarily, information seeking has been described as seeking information on purpose, nevertheless, a small but increasing number of studies have recognised information encountering as being a part of information-seeking behaviour (Abrahamson & Fisher 2007; Foster 2004; Hider 2006; McKenzie 2003; Wilson 1999). Since encountering information happens during a purposeful search, the data on (passive) information encountering were juxtaposed with (active) purposeful information seeking. The results revealed that the ratio of frequent encounters against the frequent information seeking in online databases (49.1%; 77%), electronic journals (50.3%; 71.5%) and web portals (22.4%; 52.7%) is comparatively higher in relation to websites (4.2%; 50.9%), where the professoriate encountered less (4.2%) 'frequent' information in relation to those (50.9%) that admittedly used websites for information seeking. Expectedly, since the 'frequent' use of email (9.7%), online catalogue (5.5%), listservs (0%), and File Transfer Protocol (0%) for teaching and research were low, information encountered on these media was also low. The findings here imply that the more information is 'frequently' sought in online databases, electronic journals and web portals, the more chances of encountering new information. In websites where the professoriates do more 'browsing', there are less chances of encountering information for teaching and research. For email and online catalogues, the low rate of information encountered in these sources simply corresponds to its low frequency of use in seeking information for teaching and research. In contrast, there are more reported cases of occasional information encounters in online databases (49.1%), electronic journals (50.3%), web portals (56.4%) and websites (82.4%) by the professoriate in comparison to their counterparts' occasional active usage at 22.4% (online databases), 25.5% (electronic journals), 29.1% (web portals) and 32.1% (websites). For online databases and electronic journals, the rate of frequent information encounter is same as for occasional encounters and further buttresses the high rate of both frequent and occasional information encountered in these sources. For web portals (56.4%), and particularly websites (82.4%), there are more reported cases of occasional information encounters (22.4%) than frequent (4.2%). For websites, the high occasional information encounters could be as a result of its browsing nature where, expectedly, the professoriate are more likely to occasionally rather than frequently encounter information. For email, the relatively few cases of its active but occasional (20%) usage correspond to the few intances of occasional information encounters (12.1%). This implies that not so much information is encountered, either frequently or occasionally, in the use of email for seeking information for teaching and research purposes. For the online catalogue, the number of professoriate that admitted encountering information occasionally (14.5%) was more than those that encountered information frequently (0.6%). This figure is low compared to those that use the online catalogue actively but occasionally. The reason could be that the online catalogue does not offer so much information, but is rather just a guide to library resources. It is therefore, expected that encountering information in this medium could only occur in a few occasional instances, bearing in mind the apparent challenges of accessing library information resources in the Nigerian academic environment. In the case of listserv and File Transfer Protocol, the few cases of occasional information encounters might well have been slightly exaggerated because they are hardly used and have few reported cases of occasional usage. The patterns in rare information encountering in electronic resources are anticipated since there are more cases of frequent and occasional information encounters in online journals and electronic databases; it is not surprising, therefore, to see that only a few of the professoriate rarely encounter information in these sources.
Comparing patterns in active and passive information behaviour
Electronic resources - Frequent
The patterns (Figure 1) that emerged when data on purposeful information seeking (active) was compared with information encountering (passive) on the 'frequent' dimension shows more active usage of online databases, electronic journals and web portals, and less of email, online catalogues and listservs. Information encountering follows a similar pattern, with the exception of websites, where the gap seems wider. The pattern revealed two groups of datasets. One group comprised online database, e-journals, web portals and websites, and the second group comprised email, online catalogue and listservs. There are more active and passive information behaviours in the first group, and less in the second group. The pattern shows that the more active information seeking takes place in an information source, the more the chances of encountering new information, and vice versa.
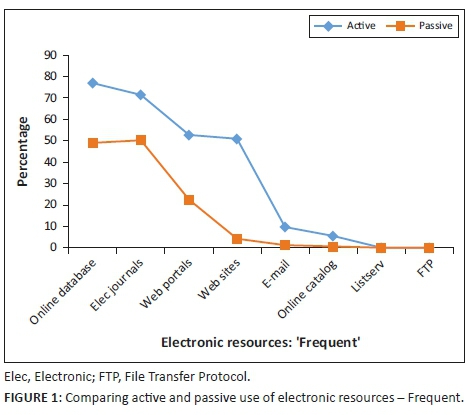
Electronic resources - Occasionally
In the occasional instance, two groups of datasets emerged. In the first group, and on the active and passive paths, online databases, e-journals, web portals and websites appear to have a consistent pattern but veered significantly along the passive path in websites. Passive information encountering was more along the paths of online databases, e-journals, web portals and websites on 'occasional' instances, implying a higher 'occasional' rate of information encountering in those sources in relation to their active usage. In the second group, emails, online catalogues, listservs and File Transfer Protocol behaved consistently along the passive path, and in comparison, online catalogues veered significantly along the active path. Overall, the pattern shows more instances of occasional (passive) information encountering in the first group than in the second group compared with active instances (Figure 2).

Electronic resources - Rarely
In the 'rarely' electronic resource category (Figure 3), two groups of datasets surfaced. The first set, namely, online databases, e-journals, web portals and websites, appeared on the downward slope on both active and passive paths and implies that a low usage of these sources amounts to 'rare' information encounters in the same sources. The second group, namely, emails, online catalogues and listservs, has a higher rate of 'rare' usage on the active and passive paths, with passive instances more on email and listserv. This implies that information is 'rarely' encountered in these sources and corresponds to their low usage for purposeful information seeking. The broad pattern in the rarely category somewhat reflects the inverse of the frequent category, suggesting that instances of rare information encountered correspond to rare usage of those sources.

Comparing active and passive use of information in media resources
Media sources - Frequent
In the media category (Figure 4), the pattern shows that newspaper, television and radio are seldom used 'frequently' by the professoriate for teaching and research, and explains the downwards nature of the active curve compared with the passive curve, where the points for newspaper and television are far above its active counterparts. This implies that the professoriate encounter more 'frequent' information in newspaper and television, as opposed to deliberately using them to access information (for teaching and research). In the case of radio, there is significantly no difference between the active and passive points, implying its low usage and rare information encountering. Overall, in media, instances of passive information encountering occur more frequently in newspaper and television than in radio, in comparison to the active usage of those sources.
Media sources - Occasionally
In the occasional instance (Figure 5), the active curve for the three media (newspaper, television and radio) appeared above the passive curve, depicting more instances of 'occasional' but purposeful usage compared to instances of information encounters. In both cases, newspaper took the lead, followed by television and radio. The broad pattern shows that more instances of occasional (active) usage of newspaper, television and radio in that order correspond to (passive) information encountering in those sources in the same order.

Media sources - Rarely
The rare instance (Figure 6) is similar but opposite in direction to the occasional instance. There are more instances of rare information encounter in the three media than are purposively but rarely used. Newspaper recorded the least instances of rare information encounters in comparison with other media sources.
Print resources - Frequent
Two sets of patterns emerged on active use and information encountered in print sources. One pattern grouped the sources into two echelons: journals and textbooks at the upper echelon and encyclopaedia, maps and magazines at the lower part. The second pattern shows a close correlation between the purposeful (active) use of the sources and information encountered in those sources (Figure 7).
Print resources - Occasionally
Superimposing active and passive data in the occasional category (Figure 8) shows that the highest occasional information encounters were with encyclopaedias, corresponding to high instances of active seeking in the medium in relation to other sources. At the lower ebb of the curve are few occasional cases of journal and textbook usage with more instances of information encounters. Maps and magazines, on the other hand, had more instances of actively seeking than passive encountering.
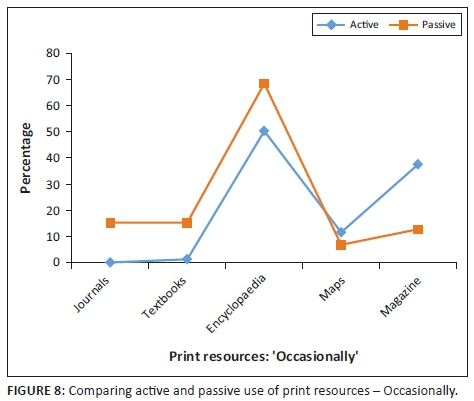
Print sources - Rarely
Comparing active and passive data on rare instances in print sources usage show no cases of rare information encounter in journals and textbooks. For encyclopaedias, rare instances of information encountered are slightly more but equivalent to its rare active usage. In the case of maps, there are very large cases of rare information encountering experiences, somewhat equivalent to the large number that rarely used the source. Whereas, for magazines, reported cases of rare active usage are higher in relation to the information encountered in the medium (Figure 9).
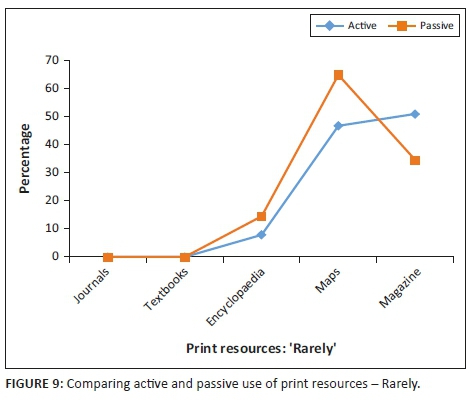
Interpersonal and academic gathering sources - Frequent
The pattern that emerged in the frequent category (Figure 10) when purposeful information seeking (active) was superimposed with information encountering (passive) data on interpersonal and academic gathering sources, shows that purposeful information seeking occurs more frequently with colleagues than with friends, and more in conferences than in seminars and workshops. Comparing both patterns shows huge difference between actively seeking information from colleagues and the insignificant information encountered from colleagues. On the paths of academic gathering, active information seeking occurs more in conferences than in seminars and workshops in that order. Information encountering follows a similar pattern, with conferences having more instances than seminars and workshops.

In the occasional category (Figure 11), there are more instances of occasional information encountering amongst colleagues than with friends, and more occasional information-encountering instances in conferences, seminars and workshops, with workshops having slightly more instances than seminars and conferences. Comparing both patterns depicts more instances of information encountering with colleagues than active instances, and on interaction with friends, both active and passive instances are insignificant. In academic gatherings, instances of information encountering surpasses active information seeking but in a corresponding manner, with relatively more instances of passive behaviour in workshops than in other groups (conferences and seminars), and relatively more active instances in seminars in relation to other groups (conferences and workshops).

In the rarely category (Figure 12), an overall view shows a corresponding similarity between active instances of rare information seeking and passive instances of rare information encountering in interaction with colleagues and friends, and in conferences, seminars and workshops. There are slightly more passive instance of rare information encounter than its active counterpart in interaction with friends. This implies that friends are hardly ever used to obtain academic information, and consequently, information encountering hardly ever occurs. Interaction with colleagues has a low passive instance of rare information encountering with a corresponding lower instance of active information seeking. Conferences, seminars and workshops behaved similarly, with insignificant, but slightly higher, cases of active information seeking than information encountering in workshops.
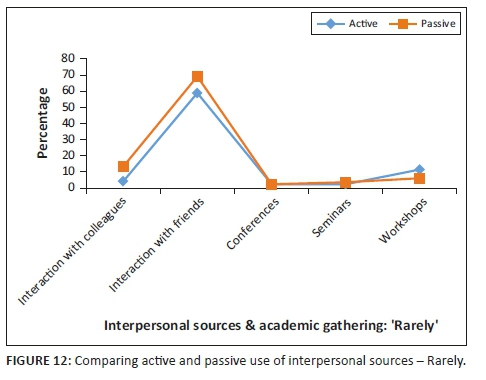
Discussion
A purposeful search to meet an information need is often associated with discovery of new information. The serendipitous nature of the discovered information does not reduce its relevance, as it can be set aside for future use. In this regard, researchers (Abrahamson & Fisher 2007; Erdelez 2000; McKenzie 2003) have narrowed the line separating both types of behaviour, describing passive information seeking as a part of an active process. Invariably, information seekers will likely encounter more information in the medium they are often exposed to. With retrospect to disciplinary fields, professoriates in this study encounter and discover more useful information in print sources than in electronic resources. This supports the evidence that print sources are more convenient, especially for teaching. Even when electronic materials are downloaded from online databases, it is more often printed to ensure accessibility in an environment frequently plagued with erratic power supply. Whilst comparing patterns may look rudimental, it brought to the fore the proportion of purposeful information seeking and serendipity across the matrix of information sources and their usage frequencies. Exploring patterns in information behaviour is still at its infancy, and the outcome of previous research (Pálsdóttir 2007, 2010) that investigated this phenomenon is noteworthy, revealing a strong connection between active and passive information behaviour. Part of the phenomenon observed in this study is consistent with the trend in Pálsdóttir (2007, 2010); professoriates active in a source are equally active discoverers, especially in sources 'frequently' used. However, this trend is apparent in electronic resources, print sources and academic gatherings, but not in media and interpersonal sources. In a sense, the first group (electronic resources, print sources and academic gatherings) fits into traditional academic sources, often used more frequently in academic circles than the second group (media and interpersonal sources), and justifies the high cases of serendipity. The rather higher instances of frequent information encountering in the electronic media (newspaper and television) than its active usage to gather information for teaching and research is anticipated, since television is a platform for less active engagement where serendipitous information can be garnered in a more leisurely style. However, its occasional uses for academic purposes is emphasised in this study, as media reports can be used for academic reference purposes or case studies. Although professional colleagues are innate information custodians in academic settings, reported instances of frequent deliberate information seeking amongst them did not yield a corresponding magnitude of serendipitous instances, but at the occasional level, these instances were significant. This simply implies that sourcing academic information from colleagues is preferred, but does not necessarily produce a corresponding proportion of serendipity, which only occurs occasionally. Academic gatherings are usually occasional events where academics gain insights from paper presentations from other academic colleagues, thereby justifying the occasional instances of serendipitous events. The almost non-existent rare active and passive cases in academic gatherings portrays academic gatherings as an opulent platform for useful information gathering that occurs either frequently or occasionally, subject to individual contexts and perspectives.
Conclusion
The study examined and compared data on active and passive information behaviour of the professoriate in selected Nigerian universities. The results of pattern analysis on active and passive data in electronic resources, media, print sources, interpersonal and academic gathering categories across usage frequencies (frequently, occasionally and rarely) showed both similar and divergent results.
The pattern in sources frequently used revealed that the more active the engagement with an information source, the greater the chances of passive encounters, and vice versa. This pattern is, however, consistent in electronic resources, print sources, and academic gatherings, but varies in media and interpersonal sources. In media, instances of passive encounters are more than active usage. In interpersonal sources, the amount of information encountered during active engagements with professional colleagues is very low. Active interaction with friends and passive instances did not yield significant result.
In sources used occasionally, the pattern showed higher instances of information encountering in online databases, e-journals, web portals and websites in comparison with active usage. The pattern is consistent in print resources, academic gatherings and interaction with colleagues, but differed in media sources. In print sources, information encountering has lower instances, yet more than active uses, in journals and textbooks. In encyclopaedias, instances of occasional information encountering surpasses active cases, but varied in maps and magazines. Occasional but active engagement in media sources results in corresponding occasional passive encountering of information.
The pattern in rarely-used sources suggests that infrequent cases of rare usage of electronic resources correspond to rare cases of passive encounters in sources with high reported instances of frequent usage (online databases, e-journals, web portals and web sites), in comparison with sources (emails, online catalogues and listservs) with less reported instances of frequent usage. This pattern is consistent in print, interpersonal and academic gatherings. In print, sources (journals and textbooks) with high usage frequency have no instances of rare information encountering in relation to encyclopaedias, maps and magazines, with higher instances of rare but active usage and passive encounter. In interpersonal sources, the pattern is consistent in interaction with colleagues but not with friends. In academic gatherings, it is consistent across all dimensions of academic gathering. With reference to media, the pattern shows higher cases of rare passive encountering in relation to rare active exposure to all the media sources.
Exploring patterns in active and passive information behaviour is still developing, with the need for researchers to focus more on the dynamics of human information behaviour at a micro level, and in other information platforms, such as the social media.
Recommendation
The study recommends that library should re-aligning library services to accommodate both active and passive information behaviour of academic staff.
Future research
Future research should explore patterns in information behaviour of other academic groups and in various social media platforms.
Acknowledgements
The financial assistance of the National Institute for the Humanities and Social Sciences Council for the Development of Social Science Research in Africa (NIHSS-CODESRIA) towards this research is hereby acknowledged. Opinions expressed and conclusions arrived at are those of the authors and are not necessarily to be attributed to the NIHSS-CODESRIA.
Competing interests
The authors have declared that no competing interest exist.
Author's contributions
S.A.N. originated the research idea, the work was an excerpt from his doctoral research at the University of KwaZulu-Natal. He conceptualised and drafted the work, collected and analysed data, and wrote the report. S.M. supervised the entire research project. He refined the idea and the entire report.
Funding information
The financial assistance of the National Institute for the Humanities and Social Sciences Council for the Development of Social Science Research in Africa (NIHSS-CODESRIA) towards this research is hereby acknowledged. Opinions expressed and conclusions arrived at are those of the authors and are not necessarily to be attributed to the NIHSS-CODESRIA.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abrahamson, J. & Fisher, K.E., 2007, 'What's past is prologue: Towards a general model of lay information mediary behaviour', Information Research 12(4), 65-72. [ Links ]
Aforo, A.A. & Lamptey, R.B., 2012, 'Information needs and seeking behaviour of law lecturers in Kwame Nkrumah University of Science and Technology, Kumasi, Ghana', International Research Journal of Arts and Social Sciences 1(4), 75-80. [ Links ]
Bhatti, R., 2010, 'Information needs and information-seeking behaviour of faculty members at the Islamia University of Bahawalpur', Library Philosophy and Practice (e-journal), Paper 314.
Engel, D., Robbins, S. & Kulp, C., 2011, 'The information-seeking habits of engineering faculty', College and Research Libraries 72(6), 548-567. https://doi.org/10.5860/crl-155 [ Links ]
Erdelez, S., 1997, 'Information encountering: A conceptual framework for accidental information discovery', in P. Vakkari, R. Savolainen & B. Dervin (eds.), Information seeking in context. Proceedings of an international conference on research in information needs, seeking, and use in different contexts (14-16 August, 1996, Tampere, Finland). pp. 412-421. Taylor Graham, Los Angeles, CA.
Erdelez, S., 2000, 'Towards understanding information encountering on the web', in Proceedings of the ASIS Annual Meeting (November 12-16, 2000, Chicago, IL). pp. 363-371.
Erdelez, S., 2005, 'Information encountering', in K.E. Fisher, S. Erdelez & L.E.F. McKechnie (eds.), Theories of information behaviour, pp. 179-184, Information Today, Medford, NJ.
Foster, A., 2004, 'A non-linear model of information seeking behaviour', Journal of the American Society for Information Science and Technology 55(3), 228-237. https://doi.org/10.1002/asi.10359 [ Links ]
Foster, A. & Ford, N., 2003, 'Serendipity and information seeking: An empirical study', Journal of Documentation 59(3), 321-340. https://doi.org/10.1108/00220410310472518 [ Links ]
Haley, K.J, Wiessner, C.A. & Robinson, E., 2009, 'Encountering new information and perspectives: Constructing knowledge in conference contexts', The Journal of Continuing Higher Education 57(2), 72-82. https://doi.org/10.1080/07377360902964384 [ Links ]
Hannah, F., 2005, 'The information-seeking behaviour of social faculty at the University of West Indies, St Augustine Campus', Journal of Academic Librarianship 31(1), 67-72. https://doi.org/10.1016/j.acalib.2004.11.003 [ Links ]
Hemminger, B.M., Lu, D., Vaughan, K.T.L. & Adams, S.J., 2007, 'Information seeking behaviour of academic scientists', Journal of the American Society for Information Science and Technology 58(14), 2205-2225. https://doi.org/10.1002/asi.20686 [ Links ]
Hider, P., 2006, 'Search goal revision in models of information retrieval', Journal of Information Science 32(4), 352-361. https://doi.org/10.1177/0165551506065811 [ Links ]
Jiang, T., Liu, F. & Chi, Y., 2015, 'Online information encountering: Modelling the process and influencing factors', Journal of Documentation 71(6), 1135-1157. https://doi.org/10.1108/JD-07-2014-0100 [ Links ]
Marouf, L. & Anwar, M.A., 2010, 'Information-seeking behaviour of the social sciences faculty at Kuwait University', Library Review 59(7), 532-547. https://doi.org/10.1108/00242531011065127 [ Links ]
Marshall, C.C. & Bly, S., 2004, 'Sharing encountered information: Digital libraries get a social life', in Proceedings of the 4th ACM/IEEE-CS Joint Conference on Digital Libraries, (June 7-11, 2004, Tucson, AZ). pp. 218-227.
McBirnie, A., 2008, 'Seeking serendipity: The paradox of control', Aslib Proceedings: New Information Perspectives 60(6), 600-618. https://doi.org/10.1108/00012530810924294 [ Links ]
McKenzie, P., 2003, 'A model of information practices in accounts of everyday life information seeking', Journal of Documentation 59(1), 19-40. https://doi.org/10.1108/00220410310457993 [ Links ]
McNally, A., Prier, C.K. & MacMillan, D.W., 2011, 'Discovery of an α-amino C-H arylation reaction using the strategy of accelerated serendipity', Science 334(6059), 1114-1117. https://doi.org/10.1126/science.1213920 [ Links ]
Meho, L.I. & Haas, S.W., 2001, 'Information seeking behaviour and use of social science faculty studying stateless nations: A case study', Library and Information Science Research 23, 5-25. https://doi.org/10.1016/S0740-8188(00)00065-7 [ Links ]
Nwone, S.A. & Mutula, S., 2018, 'Information behaviour of the professoriate in selected universities in Nigeria', South African Journal of Library and Information Science 84(1), 20-34. https://doi.org/10.7553/84-1-1733 [ Links ]
Pálsdóttir, Á., 2007, 'Patterns of information seeking behaviour: The relationship between purposive information seeking and information encountering', in P.A. Bath et al. (eds.), ISHIMR 2007: The Twelfth International Symposium on Health Information Management Research: Sheffield, 18-20 July: Proceedings, University of Sheffield Centre for Health Information Management Research, University of Sheffield, Sheffield, pp. 3-15.
Pálsdóttir Á., 2010, 'The connection between purposive information seeking and information encountering: A study of Icelanders' health and lifestyle information seeking', Journal of Documentation 66(2), 224-244. https://doi.org/10.1108/00220411011023634 [ Links ]
Rupp-Serrano, K. & Robbins, S., 2013, 'Information seeking habits of education faculty', College & Research Libraries 74(2), 131-141. https://doi.org/10.5860/crl-322 [ Links ]
Singh, K.P. & Satija, M.P., 2007, 'Information seeking behaviour of agricultural scientists with particular reference to their information seeking strategies', Annals of Library and Information Studies 54, 13-220. [ Links ]
Stewart, K.N. & Basic, J., 2014, 'Information encountering and management in information literacy instruction of undergraduate students', International Journal of Information Management 34(2), 74-79. https://doi.org/10.1016/j.ijinfomgt.2013.10.007 [ Links ]
Tahir, M., Mahmood, K. & Shafique, F., 2008, 'Information needs and information-seeking behaviour of arts and humanities teachers: A survey of the University of the Punjab, Lahore, Pakistan', Library Philosophy and Practice (e-journal), Paper 227. [ Links ]
Thanuskodi, S., 2009, 'Information-seeking behaviour of law faculty at Central Law College, Salem', Library Philosophy and Practice (e-journal), Paper 282. [ Links ]
Toms, E.G. & McCay-Peet, L., 2009, 'Chance encounters in the digital library', in M. Agosti, J. Borbinha, S. Kapidakish, C. Papatheodorou & G. Tsakonas (eds.), ECDL'09. Proceedings of the 13th European Conference on Research and Advanced Technology for Digital Libraries, Corfu, Greece, pp. 192-202, Springer Verlag, Berlin.
Van Andel, P., 1994, 'Anatomy of the unsought finding. Serendipity: Origin, history, domains, traditions, appearances, patterns and programmability', The British Journal for the Philosophy of Science 45, 631-648. https://doi.org/10.1093/bjps/45.2.631 [ Links ]
Williamson, K., 1998, 'Discovered by chance: The role of incidental information acquisition in an ecological model of information use', Library & Information Science Research 20(1), 23-40. https://doi.org/10.1016/S0740-8188(98)90004-4 [ Links ]
Wilson, T.D., 1999, 'Models in information behaviour research', Journal of Documentation 55(3), 249-270. https://doi.org/10.1108/EUM0000000007145 [ Links ]
Wilson, T.D., 2000, 'Human information behaviour', Special Issues on Information Science Research 3(2), 49-55. [ Links ]
Xuemei, G., 2010, 'Information-seeking behaviour in the digital age: A multidisciplinary study of academic researchers', College and Research Libraries 34(2), 435-452. https://doi.org/10.5860/crl-34r2 [ Links ]
 Correspondence:
Correspondence:
Simeon Nwone
simeonnwone@gmail.com
Received: 16 Oct. 2019
Accepted: 19 Apr. 2020
Published: 30 June 2020
ORIGINAL RESEARCH
Knowledge forms in the project lifecycle: A blueprint for knowledge management in small creative agencies in Johannesburg
Cobi W. Labuscagne
Gordon Institute of Business Science, University of Pretoria, Johannesburg, South Africa
ABSTRACT
BACKGROUND: Knowledge-intensive Organisations (KIO) are heavily reliant on the creation, communication and archiving of different forms of knowledge for their survival. Many KIOs that are creative agencies organise their workflows according to projects. Each phase of a project produces distinct forms of knowledge. Understanding the variations in the demands on knowledge management (KM) in step with changes in knowledge forms in different project lifecycle phases allows for the development of appropriate KM.
OBJECTIVES: The research set out to use the project lifecycle in Small and Medium-sized Enterprises (SME) KIO creative agencies as an organising device for outlining different knowledge forms at each phase. The objective was to map KM forms onto the knowledge forms in each project phase.
METHOD: A qualitative research approach with phenomenological research design was used. The empirical site was at eight organisations in Johannesburg, South Africa in the creative industries. The data was analysed using content analysis.
RESULTS: There are dramatic changes in knowledge forms at different points in a typical project lifecycle in SME KIO. However, the stages of a project are replicable and consistent between most of the projects that were analysed.
CONCLUSION: A strategy for mitigating against knowledge loss in SME KIO creative agencies is to use a range of different KM that are appropriate to the forms of knowledge. Using the project phases as a blueprint can lead to more accurate forms of KM at each distinct stage in the project lifecycle.
Keywords: knowledge management; knowledge-intensive organisations; creative agencies Johannesburg; project lifecycle; knowledge forms; knowledge management forms.
Introduction
Knowledge-intensive Organisations (KIO) have recognised the need to safeguard against knowledge loss. This is especially true in creative agencies where there is a high level of reliance on the knowledge brought by key individuals in a team. This knowledge often resides in the key team members themselves and is of a particularly tacit nature. The danger of knowledge loss when employees leave is real to all organisations (Khoza 2019) but might be said to be more severe in Small and Medium-sized Enterprises (SME) KIO creative agencies. Additionally, there is a disregard for formal knowledge management (KM) systems in many SME KIO and an over-reliance on 'remembering' (Cerchione & Esposito 2017). Working conditions are often fast-paced coupled with a pressure to move straight onto the next project once the present one is completed. It is necessary to develop KM tactics for storing and retrieving knowledge to the best of the firm's abilities. Many KIOs organise their workflows according to projects. Each phase of a project produces distinct forms of knowledge. When considering the variation in knowledge forms at different phases in a typical project lifecycle, it becomes possible to attune the KM options to the knowledge forms. The study proposes to use the project lifecycle as a blueprint for a combination of KM forms comprising of narrativisation, visualisation and information systems (IS).
Knowledge-intensive Organisations is a broad term to reference businesses that offer non-utilitarian services (Marin, Cordier & Hameed 2016), and creative agencies can be seen as a sub-section that focusses on, for example, art, design, entertainment, and advertising (Lampel, Lant & Shamsie 2000). This research is situated in this sub-section of KIOs. The KIOs that this study looked at were also SMEs.
This research uncovered four tendencies in the KM relationship in SME KIO creative agencies: (1) On deadline behaviour typically pushes reflection to the back. (2) A disregard for new systems of working if the benefit is not immediate. (3) Some forms of spontaneous KM taking place in an ad hoc manner. (4) A desire to better manage knowledge to safeguard against knowledge loss which might lead to the loss of clients.
Aims and research applicability
This research aims to name the different knowledge forms that are present at different points in a project lifecycle, and to map KM forms onto those phases. As Nissen (2002) points out, it is not enough or effective to simply introduce IS for KM to automate an existing practice. Rather, '… the organisation, people, procedures, culture and other factors need to be considered in addition to technology' (Nissen 2002:256). Potgieter, Dube and Rensleigh (2013) mention the importance of positive adoption by the employees of any suggested KM system. When the KM is considered in relation to the knowledge forms it is likely to feel more natural to the team.
The research aims, furthermore, to produce empirical insights into how creative organisations create and manage knowledge while focussing on a project lifecycle. The specific focus on the project lifecycle grounds the research in the practicalities of the work-life in KIO SME creative agencies, which can be adapted and used for other types of organisations.
Lastly, a point of departure in this research is that a better understanding of the different aspects of KM can add to management practices (Roblek et al. 2013), as well as competitive advantage (Krylova, Vera & Crossan 2016; Soto-Acosta & Cegarra-Navarro 2016; Steinmueller 2000). In this way the research aims to have application beyond the specific geography and industry discussed here.
Problem statement
How can SME KIO better safeguard themselves against knowledge loss? Can the project lifecycle be used to better attune KM for SME KIO to knowledge forms? Some scholars have looked at this question in the fields of construction and engineering and have also used the project lifecycle as an entry point (Sagsan 2006). Those kinds of projects are often large scale, and many actors are involved. Knowledge loss in the small creative agency brings on a different set of challenges that not only weighs on the success of the project itself, but can jeopardies the very survival of the business. Baptista Nunes et al. (2006) opine that SMEs do not see the value of KM and are overtly focussed on the immediate gain that knowledge can give, rather than being future focussed.
Coexisting with this attitude of disregard for KM, this research has found certain structures to be in place to gather knowledge as and when it is needed. This observation concurs with what Cerchione and Esposito (2017) found when creating a taxonomy of KM used in SMEs. They observed that certain KM practices were in place that could be turned into a more coherent KM system. This paper argues that the project lifecycle can be used to tailor the KM with the knowledge forms, thereby, some of the practices that are already in place can be mapped onto the knowledge forms that different stages in the project lifecycle present.
Many KIO creative agencies operate on projects (Farzaneh & Shamizanjani 2014; Lapunka & Pisz 2014). A project has been defined by the Project Management Institute as 'temporary', 'unique', and in need of 'expert management' to 'deliver the on-time, on-budget results' (2018). In the respondents for this study, examples of projects were: the launch and roll out of an advertising campaign; an art auction; a trade fair; a new line of clothing. The focus of the project lifecycle adds to this study a grounding in the everyday reality of KIO creative agencies.
Literature review
Knowledge-intensive Organisations, as noted earlier, is a broad term to reference those that offer non-utilitarian services (Lampel et al. 2000; Marin et al. 2016), which include financial institutions, law, technology companies, and many creative industry businesses. Lampel et al. (2000), as well as Lawrence and Phillips (2002), argue that the sub-sector within this grouping of creative agencies, which include art, advertising, fashion, and design is under-investigated.
For Garrick and Chan (2017) the importance of creative agencies is immense, in that they have the power to shape, influence and affect audiences. These authors opine that the high levels of creativity present in these organisations, and their unique ways of dealing with managerial issues might be of use to other businesses faced with the challenge of creative innovation. It is also possible that, given their flexibility, SME KIO might be dealing with complex organisational problems faster than larger ones can (Lampel et al. 2000). Baptista Nunes et al. (2006) describe these types of organisations as having high levels of creativity, problem solving and highly educated employees. Millar, Lockett and Mahon (2016) make the bold claim that when knowledge-intensive organisations fail to capture knowledge it becomes useless and lost.
Knowledge management has been a thriving research field for some decades now (Alavi & Leidner 2001; Teece 1998). Baptista Nunes et al. (2006) define knowledge management as how knowledge is 'generated, represented, stored, transferred, transformed and applied to future organisational problems' (p. 102). Knowledge management theory have evolved as organisational natures have changed. Recent work has turned to Web 2.0, and found it has opened up new knowledge management challenges (Roblek et al. 2013; Soto-Acosta & Cegarra-Navarro 2016). There is also a growing body of work that looks at more abstract concepts in relation to KM, such as experimentation (Krylova et al. 2016); the importance of team construction (Savino, Petruzzelli & Albino 2017); performativity (Marin et al. 2016), and the importance of improvisation (Pina e Cunha & Da Cunha 2006).
Despite this diversity of writing on KM, there is very little attention given to KM needs as they change in fundamental ways, during the course of a project lifecycle. Furthermore, while a considerable proportion of attention has been given to different KM options, it is still hard to determine which knowledge forms benefit from IS and which need other ways of management. Accordingly, some existing literature on KM suffers from linearity that does not take into account the dynamic nature of knowledge as changing in form and function. Diedrich and Guzman (2015) point out that, traditionally, academics in KM studies have not considered 'procedural' and 'contextual' factors (p. 1274). Additionally, while the concepts of explicit and tacit knowledge (Nonaka & Takeuchi 1995), elaborated on below, have been given much attention, there is little that dissect these terms to be more accurately descriptive.
Many studies on KM begin by creating an appropriate definition of knowledge (Nevo & Chan 2007). Taylor and Zorn (2004) distinguish between data, information, knowledge and wisdom as building on top of one another, with 'human interpretation and judgment' creating links between the concepts (p. 11). Taking a similar stance, Alavi and Leidner (2001) explain that information provides a new version of knowledge once it has been understood by a person. This study applies the definitions by both Taylor and Zorn (2004), and that by Alavi and Leidner (2001).
A key work attempting to position knowledge in business practice is that by Nonaka and Takeuchi (1995). These authors mobilise the findings that knowledge exists on two levels: the first is explicit, or codified knowledge; and the second is tacit, or uncodified knowledge. Academic literature offers other terms for these knowledge distinctions. Madhavan and Grover (1996) speak of embedded versus embodied knowledge and Roberts (2000) mentions the difference between know-how and show-how. While many scholars have built on Nonaka and Takeuchi's (1995) seminal, qualitative work (Alavi & Leidner 2001), some writers have fundamentally disagreed (Heaton & Taylor 2002). Tsoukas (2002), and others (Fahey & Prusak 1998) argue that the concept of tacit knowledge as the opposite of explicit knowledge misconceives the way knowledge functions, as the concepts are two sides of the same coin (Tsoukas 2002). In this study, there is a preference for more descriptive approaches to knowledge forms that go beyond the duality created by the terms 'tacit' and 'explicit'.
Forms of knowledge management
The consideration of different forms of KM found in the literature is key to the research question and is used to better understand the KM in the organisations under investigation in this study.
Information systems
There is a long-established relationship between KM and IS that often takes precedence in general discussion around knowledge in organisations (Garrick & Chan 2017). Writing about recent phenomena, Soto-Acosta and Cegarra-Navarro (2016) consider ways in which new technology such as Web 2.0/3.0 can facilitate KM. They list specifically: 'collaboration technologies, social networking tools, wikis, internal blogging' (Soto-Acosta & Cegarra-Navarro 2016:417). However, some scholars have questioned how well IS and KM is working and how the value can be measured (McDermott 1999; Roberts 2000). In most writing on IS and KM there is a single focus on one type of IS or one type of KM, and so the theory is falling short on offering more comprehensive solutions. Furthermore, none of the above examples from literature focusses on creative agencies, and so there is a further opportunity to enlarge the theoretical span of writing on KM and IS options.
Narrativisation
Farzaneh and Shamizanjani (2014) suggest one can use storytelling to convey and manage knowledge. They argue that a story is imbedded in contextual and experiential information, which makes it potentially, more memorable. According to these authors, stories could be ways of combining emotion and values within a task-based situation such as a project. Krylova et al. (2016) also propose storytelling as the relaying of experience. Narratives are thus informal archives of what might happen, given what has happened before. Authors have not combined the suggestion to narrativise knowledge with other forms of KM to see if there might be an ecosystem of KM at play. It is within this gap that the present research positions itself.
Visualising
A stream of writing exists that considers ways of visualising knowledge. This form of KM fits particularly well with the work done in KIO creative agencies. Examples include the research by Ambrosini and Bowman (2001) who argue that the way of extracting knowledge is through specific tactics to do with 'cognitive mapping' (Ambrosini & Bowman 2001:817). Eppler and Burkhard (2007) refer to this process as 'knowledge visualisation', the main aim of which is to 'transfer insights, experiences, attitudes, values, expectations, perspectives, opinions and predictions … enable(ing) someone else to reconstruct, remember, find or apply these insights correctly' (pp. 122-123). Visualisation is a process that might well naturally take place within a project. However, it might not be a fit-all answer to understanding all the forms of knowledge that come into play in a project lifecycle.
Research methods and design
This study employed a phenomenological, qualitative methodology. Creswell and Poth (2018) characterise phenomenology as strongly connected to the researcher who is intent on representing a particularity of the lived world. Accordingly, ingredients include 'assumptions', 'a situation', 'meaning', 'voices of participants', and 'reflexivity' (Creswell & Poth 2018:37).
Research context and setting
This research is positioned within the context of the South African creative industries, which can also be referred to as creative agencies (Lampel et al. 2000). South African, Van Graan (2005), in a White Paper for the Department of Economic Development and Tourism elaborates on this sector in the following way:
Creative Industries are those areas of social and economic activity that are premised on - or closely aligned with - a) individual or collective intellectual or artistic creativity, innovation and originality and/or b) the preservation, teaching and celebration of cultural heritage including language and which have the capacity to provide work and generate income for the original creators as well as for others involved in education and training production, distribution, documentation and support for creative products or cultural experiences, whether in a not-for-profit capacity or for commercial gain. (p. 6)
Unit of analysis
The research aimed to understand KM and knowledge forms in the KIO creative agencies that are SMEs, and so it was felt that more than one organisation should be brought into the data-gathering process. Interviews took place with eight respondents. Specific requirements for businesses to be chosen as respondents included:
-
An organisation focussed on cultural products
-
An SME
-
An organisation that structure workflow via projects.
Requirements for interview candidates included:
-
An owner, manager or director
-
In employment with the organisation for more than 8 years
-
Multiple years of experience in the field
-
An ability to articulate complex concepts relating to the topic
-
Available for more than one interview.
Sampling
In-depth semi-structured interviews
The research questions ask for interpretative answers that are based on experience. For that reason, in-depth semi-structured interviews were appropriate (Easterby-Smith, Thorpe & Jackson 2012). Questions were targeted to answer the research question, but were left open-ended. Questions included:
-
Please describe your project lifecycle
-
How do you view knowledge management in organisations in general?
-
Do you think you are retaining knowledge well at the moment?
Peer recruitment was used to identify respondents and to ensure a group that was independent of the researcher. After a process of cultivating interest in the project via email, consent forms were sent and interview dates were set. Interviews lasted between 45 and 90 min. Semi-structured interview questionnaires guided the discussion. However, the respondents were encouraged to speak freely and not be concerned if their responses felt like 'rambling'. In this way, broad themes might start to emerge that could not have been anticipated when the interview guidelines were created (Kissling Hansen 2009).
Focus groups
Focus groups were conducted in one of the organisations as a way of questioning some of what was emerging from the data. Two sessions were conducted with seven team members present. It was important in these sessions to get the full team who administered the entire lifecycle of a project present. This could only be achieved in one of the respondent organisations. It was useful to have more than one session as the data and findings could be double-checked with the same team at two different points in the analyses to ascertain to what extent the findings were reflecting their experience. In these sessions a fictional scenario was created to get the organisation's project team to actively engage in thinking about the knowledge at different points in a project. The project team was asked what forms of knowledge would be required if the organisation was to open an office in another country. This fictional paradigm was a device to allow the process of 'cognitive mapping' to take place (Ambrosini & Bowman 2001:817).
Data analysis
Given the phenomenological nature of the inquiry and the ontology of relativism, it was appropriate to approach the data inductively and there was a consideration of complexity, contingencies and interactions of different data points. The research questions demanded content analyses of the data (Easterby-Smith et al. 2012). There was also sensitivity for what was happening around the interview data, for example, the setting, the industry and the dynamic in the interview process.
Validity and reliability
The research followed steps towards validity and reliability of the data. These processes can be summarised as:
-
Key informers were returned to for presentation and discussion of findings.
-
All informers have experience and are of good standing in the industry.
-
The researcher addressed her proximity and possible biases through focus groups where results were presented and discussed.
Ethical consideration
Before the interview process, consent letters and information on the subject of study was circulated, ensuring upfront ethical clearance. This article followed all ethical standards for a research without direct contact with human or animal subjects.
Results
Presentation of the data
The presentation of the data here follows the suggestion for phenomenological studies outlined by Creswell (2007).
Personal experience bracketing
The researcher worked as an owner/manager for over a decade in an organisation operating as a KIO SME creative agency in Johannesburg. Upon entering the field the intention was to bring past experience to the fore. However, as the data gathering progressed, the relative weight shifted to the experience of the respondents and what came through in the interviews.
Descriptions of the setting
Creative agencies are emotive places of work that thrive on creativity (Lampel et al. 2000). Imagine a workplace that is filled with energy, passion and opinions. Within this setting it is tangible that this passionate energy and these opinions are the fuel that makes the engine run. The working environment is colourful and inventive and there is a fast pace of work. There are communal working spaces and discussions are taking place. The workforce is diverse, including multiple generations, races and genders.
The above is a portrait of a typical SME KIO creative agency in South Africa. For this study a broad range of these small creative agencies were approached, and these are summarised in Table 1.
Following the guidelines set by the Project Management Institute (2018), four distinct project lifecycle phases were identified. These were:
-
Development phase
-
Planning phase
-
Execution phase
-
Evaluation phase
Description of project lifecycle phases
The development phase could take the form of a response to a tender, a new range of clothing, or a proposal to win a new client. Some projects were annually recurring in which case the development phase marked the period where innovation and 'new-ness' for the coming iteration was discussed and developed. This phase was heavily collaborative. Team members had brainstorming workshops and some elements of research on trends or the behaviour of competitors informed the process.
In contrast to the 'development phase', planning was more passive in that it happened individually, followed by recurring status meetings where planning and progress was assessed. Planning involved timeline, budget and resource allocation. It was not a phase that demanded direct experience, since many of the aspects were merely adapted from previous projects. This phase is thus well documented and archived as the below quote from a respondent illustrates:
We put everything on Google, and then it sits there. So, for instance, every single budget, every single recon of that budget, so what we actually spent, where, the suppliers on that project - Every single proposal, strategy - is all in Google Docs. And we tap into those budgets and those things all the time. (Anonymous 1, pers. comm., 17 January 2018)
By its nature the execution phase was 'out of the office' for the members of the KIO SME that was interviewed for this study. In execution a project takes place or is 'rolled out'. Execution also encompassed the marketing and sales aspects of the project and so the focus was external to the organisation. Projects took many different forms, as is outlined in Table 1 above.
The review phase was the only one of the four identified stages that was actively associated with KM. There was often an attempt to 'remember' and capture everything that had happened throughout the different project phases. The review typically took the form of a debrief where all the project team members were present and tended to revolve around points of unhappiness in the process. Accordingly, it was more focussed on what went wrong and could be an emotional session. There was pressure to rapidly move on to the next project and not get around to doing any formal archiving. What this practice translated into, was KM that were purely document related and lacked narrative and visual information that other forms of KM offer. Many of the organisations interviewed had to do an external review for clients. This took the form of surveys, videos and narratives of what happened. These documents were created with the client in mind, however, often the best form of post project review that they engaged with.
Discussion
Key findings
-
It was found that project lifecycle phases can be used as a guideline for more effective KM. The project lifecycle was a successful research focus to delineate and isolate forms of knowledge and corresponding forms of KM. It was found that the project lifecycle was useful as a focal structure for respondents, as it forced them to think very specifically about 'what they did', 'what they needed in order to do what they did' and what the knowledge form was at each phase in the lifecycle.
-
It was clear from the data that there is a high risk of knowledge loss in small creative agencies due to a number of factors:
■ small teams rely heavily on spontaneous decision-making
■ reluctance to spend time recording due to high demands of the project client
■ over-reliance on team member trust
■ over-reliance on key person permanency.
All of these 'obstacles' can be managed by systematically reviewing the knowledge forms being produced and relied on at each stage in a project lifecycle and suggesting appropriate forms of KM for each stage. The suggestion is to imbed the KM in the project phase itself in as natural a way as possible.
-
Different forms of knowledge demand different forms of KM that attune more naturally to the project lifecycle phase. The KM system should comprise of narrativisation, visualisation and IS options. This is illustrated in Table 2 below.
Discussion of key findings
Knowledge management in the project lifecycle
Development Phase knowledge management: The knowledge form characteristic of this phase was an idea or a concept. Team members relied on creativity, innovation and experience. The quotation below from one respondent emphasises the degree to which the knowledge is tacit and personal:
It's been a dream of mine. … To have vocations in fields that I love and that I am passionate about. Because of this I can bring all my knowledge of pictures, beauty, clients and design together in my business. (Anonymous 2, pers. comm., 17 December 2017)
The most appropriate form of KM would be narrativisation. This would entail a commitment to recording, in narrative form, how the ideas were come by for the new project and how they were seen to be new, innovative and fitting the brief. This KM could take place as brainstorm meetings happen, or after the ideas have been crystallised in the form of interviews and active mentorships. These can then be turned into 'development phase case studies'. The quotation below illustrated the need for this kind of documenting:
Every time we do end up having a piece of potential new business, we scramble around and think, when last did we use a credential document? We better update it. And so it would be much better to have live, fresh case studies. But to be honest, it falls by the wayside, because our clients are the priority, not us. (Anonymous 3, pers. comm., 02 December 2017)
Visualisation maps can be used to illustrate the process whereby an idea is formed. This form of KM should take place in the moment when ideas are discussed, rather than after the fact.
Planning phase knowledge management
Most befitting to the knowledge form existing in this phase are IS options of document sharing, team collaboration tools and social enterprise development, given that much information is recycled. In this phase it was observed that budgets were re-used and changed, timelines were adapted from pervious projects and applied to the current needs, and resource allocation documents were adjusted from previous projects. Collaboration tools should streamline this process while simultaneously archiving the information systematically for future use.
Execution phase knowledge management
In the organisations under investigation the execution took two forms: first a process of sales and marketing took place, and thereafter the project itself 'happened'. In the marketing phase IS forms of social media played an overriding role because of its accessibility to small businesses, as well as the high adoption rate of creative individuals. The marketing often took the form of stories that were told to databases and so were already versions of KM that lived and were archived within the social media tools that were used. These included, bulk mailers, Instagram and Facebook. All of these tools can be seen as KM systems in themselves and offer analytics that offer insight into past behaviour.
When the project was rolled out, 'new knowledge' was created. For this reason a varied spectrum of KM tools should be employed to best capture the knowledge for future learning. Recording devices such as photos, video and sound recording can capture the in-the-moment nature of the knowledge that is created in this phase.
Review phase knowledge management
For most organisations the review phase was where all the KM practices were located, however, there was a rush to move on. This phase lends itself to narrativisation, as well as visualisation of what happened in the project. It is important that individual members of the team take time to tell the stories of what happened the way they experienced it and so take the focus off the negative aspects of the project. It is also recommended that at this point in the project all the KM from the previous three stages are collated and stored using an IS system. This could take the form of a cloud-based storage or a project collaboration tool.
The implication of choosing a particular knowledge form within a particular phase has direct bearing on the knowledge management that has to be applied. In turn, the knowledge management has to mirror the type of knowledge that the project phase produces and relies on. The KM forms, as listed in the Table 2, have been paired with the types of knowledge that have been created, given the particularities of each project lifecycle phase. It is critical that there is a relationship between the knowledge form and the KM form for it to be easily adopted by the team.
Situating the findings in academic writing
The research findings presented here depart from the conversations around tacit and explicit knowledge mobilised by Nonaka and Takeuchi (1995). The present study argues that the contemporary landscape within which organisations operate demands more descriptive and varied approaches to the life of knowledge. As such, the findings are more in line with studies that look at KM through the lenses of experimentation (Krylova et al. 2016); the importance of team construction (Savino et al. 2017); performativity (Marin et al. 2016), improvisation (Pina e Cunha & Da Cunha 2006); and creative work environments (Ensor, Cottam & Band 2001). However, these discussions are taken further and different forms of KM are attuned to knowledge forms in the project lifecycle. The research suggests that there is merit in accurately naming the knowledge forms in order to create a KM fit.
Strengths and limitations
The first strength of these findings is regional and pertains to the emerging economy of South Africa (Al-Shammari 2011). The work that the writers on knowledge, knowledge economies and KM have done have an urgent relevance to the South African context (Baltezarević, Baltezaravic & Jovanovic 2015; Blankley & Booyens 2010). South Africa is facing a need for a shift away from a resource and industrial economy to a knowledge economy (Du Toit 2003; Snowball 2016) to spur economic growth and offer skills to a larger workforce (Snowball 2016). For these reasons, more scholarly work and practical research are needed to inform this shift that could lead to job creation and skills upliftment (Blankley & Booyens 2010). This study provides some groundwork for understanding SME KIO agencies in South Africa. More importantly, the research makes suggestions that could contribute to the longevity of SME KIO in South Africa.
The second strength of this study relates to business more broadly and addresses the importance of understanding knowledge and KM in KIO creative agencies in general (Scott 2005). Creative agencies and their relation to knowledge can have powerful learnings for other industries for innovation and creativity (Lampel et al. 2000; eds. Pratt & Jeffcutt 2009). For this reason, a deeper understanding of how knowledge and KM function can be useful to organisations globally and cross-sectorally.
An acute focus on one industry in one country can produce research that is deep rather than broad. This choice of subject matter, together with the qualitative methodology employed, presents the possible limitation that one might read the data as only pertaining to the subject at hand. However, the findings serve to lay the groundwork for further investigation and theory creation.
Implications and recommendations
It is recommended for SME KIO creative agencies to use the project lifecycle, which is a blueprint for all the activities within a project, to create appropriate KM systems for different forms of knowledge. It is also recommended for these businesses to have different forms of KM in the system rather than trying to retro-fit their existing activities into one type of KM.
As some of the literature on small KIO (Millar at al. 2016) suggests, the situational factors that this research uncovered might well apply to organisations operating on a larger scale. As such, the knowledge forms as the project lifecycle unfolds and the relevant KM, here perceived on a micro scale, might be found to be the practical reality in many other organisations. The research would have to be taken further to test this supposition.
Conclusion
Many small creative agencies do not give active attention to KM. This study found that they do, however, see the value of archiving knowledge and sometimes admitted that KM might be critical to their survival. There are obstacles preventing KIO creative agencies from fully adopting an already existing KM IS. This study suggests that if one can delineate the different tasks in a project lifecycle and couple those with the knowledge forms produced in each, appropriate KM solutions could be offered that could more easily be incorporated into the already existing workflow.
Acknowledgements
Thanks to my supervisor, Elaine Garcia, for her assistance during this project. Thanks also to Prof. Roy Johnson for assisting in editing another version of this research.
Competing interests
The author has declared that no competing interest exist.
Author's contributions
The author is the sole contributor to the work.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy or position of any affiliated agency of the author.
References
Alavi, M. & Leidner, D.E., 2001, 'Review: Knowledge management and knowledge management systems: Conceptual foundations and research issues', MIS Quarterly 25(1), 107-136. https://doi.org/10.2307/3250961 [ Links ]
Al-Shammari, M., 2011, Knowledge management in emerging economies: Social, organisational and cultural implementation, Hershey, New York, NY.
Ambrosini, V. & Bowman, C., 2001, 'Tacit knowledge: Some suggestions for operationalisation', Journal of Management Studies 38(6), 811-829. https://doi.org/10.1111/1467-6486.00260 [ Links ]
Baltezarević, V., Baltezaravic, R. & Jovanovic, J., 2015, 'Knowledge management as imperative for economic growth', Knowledge Management, EA 48(3-4), 62-68. [ Links ]
Baptista Nunes, M.B., Annansingh, F., Eaglestone, B. & Wakefield, R., 2006, 'Knowledge management issues in knowledge-intensive SMEs', Journal of Documentation 62(1), 101-119. https://doi.org/10.1108/00220410610642075 [ Links ]
Blankley, W.O. & Booyens, I., 2010, 'Building a knowledge economy in South Africa', South African Journal of Science, viewed 26 February 2018, from http://www.scielo.org.za/scielo.php?pid=S0038-23532010000600009&script=sci_arttext&tlng=en
Cerchione, E. & Esposito, A., 2017, 'Using knowledge management systems: A taxonomy of SME strategies', International Journal of Information Management 37(1), 1551-1562. https://doi.org/10.1016/j.ijinfomgt.2016.10.007 [ Links ]
Creswell, J.W., 2007, Qualitative inquiry & research design: Choosing among five approaches, 2nd edn., Sage, New York, NY.
Creswell, J.W. & Poth, C.N., 2018, Qualitative inquiry & Research design: Choosing among five approaches, 4th edn., Sage, New York, NY.
Diedrich, A. & Guzman, G., 2015, 'From implementation to appropriation: Understanding knowledge management system development and introduction as a process of translation', Journal of Knowledge Management 19(6), 1273-1294. https://doi.org/10.1108/JKM-02-2015-0055 [ Links ]
Du Toit, A.S.A., 2003, 'Competitive intelligence in the knowledge economy: What is in it for South African manufacturing enterprises?', International Journal of Information Management 23(2), 111-120. https://doi.org/10.1016/S0268-4012(02)00103-2 [ Links ]
Easterby-Smith, M., Thorpe, R. & Jackson, P., 2012, Management research, 4th edn., Sage, London.
Ensor, J., Cottam, A. & Band, C., 2001, 'Fostering knowledge management through the creative work environment: A portable model from the advertising industry', Journal of Information Science 27(3), 147-155. https://doi.org/10.1177/016555150102700304 [ Links ]
Eppler, M.J. & Burkhard, R.A., 2007, 'Visual representations in knowledge management: Framework and cases', Journal of Knowledge Management 11(4), 112-122. https://doi.org/10.1108/13673270710762756 [ Links ]
Fahey, L. & Prusak, L., 1998, 'The eleven deadliest sins of knowledge management', California Management Review 40(3), 265-275. https://doi.org/10.2307/41165954 [ Links ]
Farzaneh, N. & Shamizanjani, M., 2014, 'Storytelling for project knowledge management across the project lifecycle', Knowledge Management and E-Learning 6(1), 83-97. https://doi.org/10.34105/j.kmel.2014.06.006 [ Links ]
Garrick, J. & Chan, A., 2017, 'Knowledge management and professional experience: The uneasy dynamics between tacit knowledge and performativity in organizations', Journal of Knowledge Management 21(4), 872-884. https://doi.org/10.1108/JKM-02-2017-0058 [ Links ]
Heaton, L. & Taylor, J.R., 2002, 'Knowledge management and professional work: A communication perspective on the knowledge-based organization', Management Communication Quarterly 16(2), 210-236. https://doi.org/10.1177/089331802237235 [ Links ]
Khoza, L.T., 2019, 'Managing knowledge leakage during knowledge sharing in software development organisations', South African Journal of Information Management 21(1), 1-7. https://doi.org/10.4102/sajim.v21i1.1075 [ Links ]
Kissling Hansen, J., 2009, 'How knowledge is transferred within the Danish Fashion Industry', Masters Thesis, Copenhagen Business School, viewed 25 October 2017, from http://studenttheses.cbs.dk/bitstream/handle/10417/618/jonas_kissling_hansen.pdf. [ Links ]
Krylova, K.O., Vera, D. & Crossan, M., 2016, 'Knowledge transfer in knowledge-intensive organizations: The crucial role of improvisation in transferring and protecting knowledge', Journal of Knowledge Management 20(5), 1045-1064. https://doi.org/10.1108/JKM-10-2015-0385 [ Links ]
Lampel, J., Lant, T. & Shamsie, J., 2000, 'Balancing act: Learning from organizing practices in cultural industries', Organisational Science 11(3), 263-269. https://doi.org/10.1287/orsc.11.3.263.12503 [ Links ]
Lapunka, I. & Pisz, I., 2014, 'Knowledge management in the project life cycle: Initial research on Polish SMEs', Foundations of Management 6(2), 67-82. https://doi.org/10.1515/fman-2015-0012 [ Links ]
Lawrence, T.W. & Phillips, N., 2002, 'Understanding cultural industries', Journal of Management Inquiry 11(4), 430-441. https://doi.org/10.1177/1056492602238852 [ Links ]
Madhavan, R. & Grover, R., 1996, From embedded knowledge to embodied knowledge: New product development as knowledge management, Institute for the Study of Business Markets Report, Pennsylvania State University, viewed 23 October 2017, from https://pdfs.semanticscholar.org/f5b4/3a13449fb96b86bec28720a834979f467d64.pdf.
Marin, A., Cordier, J. & Hameed, T., 2016, 'Reconciling ambiguity with interaction: Implementing formal knowledge strategies in a knowledge-intensive organization', Journal of Knowledge Management 20(5), 959-979. https://doi.org/10.1108/JKM-11-2015-0438 [ Links ]
McDermott, R., 1999, 'Why information technology inspired but cannot deliver knowledge management', California Management Review 41(4), 103-116. https://doi.org/10.2307/41166012 [ Links ]
Millar, C.C.J.M., Lockett, M. & Mahon, F., 2016, 'Guest editorial: Knowledge intensive organisations: On the Frontiers of Knowledge Management', Journal of Knowledge Management 20(5), 845-857. https://doi.org/10.1108/JKM-07-2016-0296 [ Links ]
Nevo, D. & Chan, Y.E., 2007, 'A Delphi study of knowledge management systems: Scope and requirements', Information & Management 44(6), 583-597. https://doi.org/10.1016/j.im.2007.06.001 [ Links ]
Nissen, M.E., 2002, 'An extended model of knowledge-flow dynamics', Communications of the Association of Information Systems 8(2002), 251-266. https://doi.org/10.17705/1CAIS.00818 [ Links ]
Nonaka, I. & Takeuchi, H., 1995, The knowledge creating company: How Japanese companies create the dynamics of innovation, Oxford University Press, New York, NY.
Pina e Cunha, M. & Da Cunha, J.V., 2006, 'Towards the improvising organisation', Business Leadership Review III(IV), 1-6. [ Links ]
Potgieter, A., Dube, T. & Rensleigh, C., 2013, 'Knowledge management awareness in a research and development facility: Investigating employee perceptions', SA Journal of Information Management 15(2), Art. #592, 6 pages, viewed 01 July 2019, from https://doi.org/10.4102/sajim.v15i2.592 [ Links ]
Pratt, A.C. & Jeffcutt, P. (eds.), 2009, Creativity, innovation and the cultural economy, Routledge, London.
Project Management Institute, 2018, What is project management, viewed 14 February 2018, from https://www.pmi.org/about/learn-about-pmi/what-is-project-management.
Roberts, J., 2000, 'From know-how to show-how? Questioning the role of information and communication technology in knowledge transfer', Technology Analysis & Strategic Management 12(4), 429-443. https://doi.org/10.1080/713698499 [ Links ]
Roblek, V., Bach, M.P., Mesko, M. & Bertoncelj, A., 2013, 'The impact of social media to value added in knowledge-based industries', Kybernetes 42(4), 554-568. https://doi.org/10.1108/K-01-2013-0014 [ Links ]
Sagsan, M., 2006, 'A new life cycle model for processing of knowledge management', in 2nd International Conference on Business, Management and Economics, Izmar.
Savino, T., Petruzzelli, A.M. & Albino, V., 2017, 'Teams and lead creators in cultural and creative industries: Evidence from the Italian Haute Cuisine', Journal of Knowledge Management 21(3), 607-622. https://doi.org/10.1108/JKM-09-2016-0381 [ Links ]
Scott, A.J., 2005, 'Cultural-products industries and urban economic development', Urban Affairs Review 39(4), 461-490. https://doi.org/10.1177/1078087403261256 [ Links ]
Snowball, J., 2016, 'Why art and culture contribute more to an economy than growth and jobs', The Conversation, viewed 2 March 2018, from https://theconversation.com/why-art-and-culture-contribute-more-to-an-economy-than-growth-and-jobs-52224.
Soto-Acosta, P. & Cegarra-Navarro, J., 2016, 'New ICTs for knowledge management in organizations', Journal of Knowledge Management 20(3), 417-422. https://doi.org/10.1108/JKM-02-2016-0057 [ Links ]
Steinmueller, W.E., 2000, 'Will new information and communication technologies improve the "Codification" of knowledge?', Industrial and Corporate Change 9(2), 361-376. https://doi.org/10.1093/icc/9.2.361 [ Links ]
Taylor, J.R. & Zorn, T., 2004, 'Knowledge management and/as organisational communication', International Communication Association, New Orleans, viewed 10 December 2017, from http://citation.allacademic.com/meta/p_mla_apa_research_citation/1/1/2/4/2/p112428_index.html.
Teece, D.J., 1998, 'Research directions for knowledge management', California Management Review 40(3), 289-292. https://doi.org/10.2307/41165957 [ Links ]
Tsoukas, H., 2002, 'Do we really understand tacit knowledge?', Knowledge Economy and Society Seminar, London, viewed 17 September 2017, from http://mba.eci.ufmg.br/downloads/dowereally.pdf.
Van Graan, M., 2005, Cultural industries, arts, culture and creative arts first paper: Towards an understanding of the current nature and scope of the creative industries in the Western Cape, viewed 21 February 2018, from https://www.westerncape.gov.za/other/2005/11/final_first_paper_cultural_industries_printing.pdf.
 Correspondence:
Correspondence:
Cobi Labuscagne
cobilabuscagne@gmail.com
Received: 01 Aug. 2019
Accepted: 19 Apr. 2020
Published: 01 July 2020
ORIGINAL RESEARCH
The gap between user perceptions and expectations of students at the main library of the University of KwaZulu-Natal: Pietermaritzburg Campus
Matsobane D. KekanaI; Siyanda E. KheswaII
IDepartment of Information Studies, Faculty of Arts, University of Zululand, KwaDlangezwa, South Africa
IIDepartment of Information Studies, College of Humanities, University of KwaZulu-Natal, Pietermaritzburg, South Africa
ABSTRACT
BACKGROUND: An academic library is defined as the heart of a university, providing a venue for students, lecturers and researchers to advance their knowledge and conduct their research. These institutions should provide learning opportunities for all who choose to use them. The materials in the library are for anyone to use, which is why university libraries are important. This study investigated the gap between postgraduate students' perception and expectations of the main academic library (Cecil Renaud) at the University of KwaZulu-Natal: Pietermaritzburg campus.
OBJECTIVES: This study's objective was to determine the gap between the existence of users' expectations and perceptions of the quality service.
METHOD: This study employed the quantitative research method, with a survey research design. The study population included postgraduate students in the School of Social Sciences, College of Humanities, at the University of KwaZulu-Natal: Pietermaritzburg campus
RESULTS: The services that have a relatively big gap in agreement between expectations and perceptions are: computers that work well, adequate number of computer workstations and an efficient short loan service, and the library helping the user to stay abreast of developments in their field of interest. On the other hand, services that have a small gap are: a library environment that has sufficient lighting; and staff willing to help, who understand the library service need and who are sufficiently knowledgeable.
CONCLUSION: The study found that there was a gap in almost all the services provided by the Cecil Renaud Main library. For example, with the comprehensive collection, there were not adequate print journals and books. In relation to access to information, the major gaps were re-shelving of journals, missing books and journals, and an inefficient short loan and interlibrary loan service.
Keywords: service quality; user perceptions; user expectations; postgraduate students; University of KwaZulu-Natal.
Introduction
Husain and Nazim (2015:135) state that 'academic libraries are established to support teaching, learning, research activities and development of a culture of sharing and imparting knowledge to fulfil the mission and objectives of their main institution'. A university library can be defined as the heart of the academic community, providing a venue for students, lecturers and researchers to conduct their research and advance their knowledge (Kiran 2010:261). The strategic objective of an academic library as a service organisation is to sustain the standard of service quality (Einasto 2009). The standard of services rendered should be able to satisfy the library users, and to ensure the finance of activities which are satisfactory for the existence and development of the university. These institutions are supposed to provide learning opportunities for all who choose to take advantage of them.
Ramezani et al. (2018) assert that measuring the quality of service is necessary when it comes to the planning and the improvement of the quality of the organisational services. Arshad and Ameen (2010:313) state that the role of libraries in the developed world has progressed merely from a storehouse of books and other physical artifacts to local and remotely-held databases. It has been emphasised by Quintal and Phau (2014:90) that it is clear that students are primary stakeholders in global education and their perceptions and behaviour towards the globalised learning environment in either a university's home or offshore campus are important. To start, their perceptions and attitude could assist teaching staff of the university to identify and put emphasis on specific attributes. Habre and Kammourie (2018) state that the library being the heart of a university campus, students' expectations and needs have had a high impact on libraries, when it came to the functionalities, services, library staff skills, learning resources and library space.
Simba (2006:1) states that 'the importance of academic libraries cannot be underestimated'. By saying this, it was further stressed that the reputation of a library has no measure. Academic libraries are not independent bodies of learning; they belong to the universities' community and they play an important role in the learning process of that institution. One of the most competitive obstacles for academic libraries in the 21st century is reinstating themselves as the first destination where the users go to for assistance. For users to be assisted, Brenza, Kowalsky and Brush (2015) mention that libraries should hire student assistants who can help users with duties such as providing direction, helping with computer challenges and printers and facilitating connections between the user and the librarians. Libraries should satisfy their users, with a proactive assessment of their needs and give feedback by providing a quality service that can intersect those needs. For academic libraries to add value to the learning process, they need to be both effective and efficient (Simba 2006:1). Echezona and Chigbu (2018) assert:
[M]any libraries in sub-Saharan Africa have problems keeping up-to-date with information resources procurement, especially print books and journals and the concern is on the budget inadequacies they received from the institution. (p. 93)
In traditional days, before technology was developed to its current standard the library worked differently. Sahu (2007:234) states that the service 'quality of an academic library has been described in terms of its collection and measured by the size of the library holdings and statistics on its use'. According to Nitecki and Hernon (2000:259) and Deng and Zhang (2015) researchers in Library and Information Science have examined information needs, user needs, and user perceptions about the estimation of library administrations. Fasola (2015) is of the opinion that new technologies being implemented in the library can be affected by the perceptions and attitudes of librarians towards them. Fasola (2015) had taken a glimpse at an elusive idea like 'quality' as far as collections (electronic or print), and 'effectiveness' of library administrations.
Research problem
The University of KwaZulu-Natal (UKZN) libraries aim to provide high quality information services to their users, and there should be statistics proving how the users perceive the library services. Not only that, but also getting the users' expectations of the services that should be rendered. This could be accomplished through assessment because, according to McNicol (2002:251), providing support for learners is increasingly shifting major attention for libraries; it is important that approaches are developed to assist the staff in assessing the learning needs of their users and in considering ways in which those concerns could be met. Libraries are now turning to discovery products which are, according to Trapido (2016:9), 'tools and interfaces that a library implements to provide patrons the ability to search its collection and access to materials'.
According to Gannon-Leary, Bent and Webb (2008:3), 20 years ago, working spaces in a university library comprised individual study carrels, possibly bookable and enclosed, discrete spaces to use technology, often in the form of catalogue terminals and a few computers, and open reading room spaces. A research conducted through interviews by Gannon-Leary et al. (2008) on the spaces in the library claim that the virtual presence of a library rendered its physical appearance less important.
The UKZN libraries code of conduct states that users have the right to a library environment suitable for reading, study and other activities in support of research and instructional programmes (University of KwaZulu-Natal 2014). The UKZN has five campuses. Altogether, the 14 libraries contain 1.4 million volumes of collection in the form of journals, books, theses, reports and print media. Furthermore, there is an audiovisual collection and access to a number of electronic resources (e-resources). These electronic collections can be accessed through the subscriptions made by the library in the form of journals and databases.
Normally, several students see the library as an environment where they might go for reference or to be assisted in conducting research, and they do not view it as a place where they see themselves returning in the future. In this regard, the problem that this study seeks to understand is the perception of the end user regarding the service quality of the library, and to link users' perceptions and expectations with the services provided by the library.
This research has focused on the Pietermaritzburg Campus libraries; the assessment of the users' perceptions and expectations was based on the quality of services offered by Cecil Renaud Main (CRM) library. There are several studies that have been conducted about the users' perceptions and expectations of academic libraries from an internal perspective. In South Africa, there are arguably six academic libraries which have studies that evaluated their users' perceptions and expectations.
Research question
What is the gap between the existence of users' expectations and perception of quality service?
Literature review
The literature gathered indicates that there are many studies which are concerned with users' perception and expectations of quality service, and which determine how satisfied the users are in academic and public libraries. These studies have identified the gap between users' perceptions and users' expectations of the quality service.
Simba's (2006) study was based on the premise that the culture of library assessment from the users' perspective is of vital importance in determining users' needs and whether these needs are being met. The study examined the quality of service at Iringa University College (IUCo) library from the users' perceptions. The population of the study used was undergraduate and postgraduate students, as well as the academic staff. The insights gained from this study indicate a gap between users' expectations and perceptions.
The magnitude of the gaps found varied depending on individual services. The findings show that the most problematic services for users were electronic journals, photocopying facilities, interlibrary loans, electronic databases, and a quiet library environment. The academic staff have higher expectations and lower perceptions compared to postgraduate and undergraduate students.
A study conducted by Moon (2007) looked at the implementation of LibQUAL+ in the first South African university library, which is the Rhodes University library. Rhodes University was founded in 1904 and it had an enrolment of 6245 students. The reason for this university to embark on LibQUAL+ was influenced by the library's need to benchmark the quality of their service provision against that of other university libraries in South Africa, to fulfil requirements of the institutional audit which was conducted by the Higher Education Quality Committee.
The LibQUAL+ survey was employed to collect data. The population of the study was undergraduate and postgraduate students and academic staff. The findings on the library usage patterns were that the undergraduates were the most frequent on-site users of the library resources. In contrast, they were the least frequent users of the library's remote access facilities. The academic staff's library usage patterns show that they were less responsive to on-site usage, but exhibited high remote usage through the library website. Even though Rhodes ranked below the national average where service quality to undergraduate students was concerned, it ranked above average in some cases where all other user groups were concerned.
Other findings are on the three dimensions of LibQUAL+ which are: Affect of service, information control, and library as a place. In the dimension of 'Library as Place', Rhodes performed very poorly. A negative gap was noted between the minimum and perceived levels of service in the overall results; this attribute fell outside the zone of tolerance. On 'Information control', the findings show that the library performed very well. On the 'Affect of service', the findings show that the academic staff rated it higher than undergraduate and postgraduate students.
A study conducted by Naidu (2009) examined the quality of service provided by the Mangosuthu University of Technology (MUT) library from the perspectives of the users of the library. It determined the gaps between users' expectations and perceptions of service quality. A LibQUAL+ survey was used in this study, modified and simplified to identify these gaps. The population of the study consisted of undergraduate and postgraduate students, as well as academic and administration staff. The extent of the gap between user expectations and the actual service provided varied depending on the individual services, such as library spaces, library facilities, the library collection, and access to information.
Bhim's (2010) study examined the quality of services provided by the Bessie Head library from the perspective of the adult users of the library. The study assessed the adult users' perception of the quality of service and determined the level of user satisfaction at the Bessie Head library. The population consisted of 200 registered adult library users, and a LibQUAL+ survey instrument, which was modified and adapted for use in a public library, was used in this study.
The findings were that there was a gap between users' perceptions and expectations of service quality at the Bessie Head library. Some expectations were not in keeping with the actual experience at the library, for example, access to information, users experiencing problems with Internet access and the reference collections. Other findings revealed that the majority of adult users rated the overall quality of services as good and that the library was, to a large extent, excelling in service provision.
A study by Kachoka (2010) assessed undergraduate students' perceptions of the quality of service at Chancellor College library at the University of Malawi. The LibQUAL+ instrument, which was derived from the gap theory of service quality, and the SERVQUAL instrument were adapted and used in this study.
The findings of the study show that the undergraduate students had higher expectations of service quality than the perceived quality service. Furthermore, the results of the study indicated that the Chancellor College library was not meeting the minimum expectations of service quality of its users in the three dimensions of service quality: Affect of services, library as a place and information control.
A study by Pretorius (2011) looks at the shifting focus on the role of academic libraries, which may entail developing a better understanding, awareness and responsiveness to the needs of the library users. In an ever-changing environment and an age of accountability, academic libraries have to determine and demonstrate the impact of their resources and services. It is noted that service quality is not based exclusively on the perceptions of the librarians, but is also dependent on the perceptions of the users.
This study assessed the quality to determine the perceptions of the users of the Vaal Triangle Campus library as they relate to quality service and developed a model to improve service quality. This study also determined library users' minimum expectations for services, their desired level of services and then sought to identify the extent of service they currently perceive on three dimensions, which are: Affect of service, library as place and access to information. Data collected used focus groups as well as individual interviews, and the LibQUAL+ instrument was adapted, modified and simplified to relate to the study. The findings indicated there was a gap between the perception and expectations of service quality. Ncwane's (2016) and Matiwane's (2017) studies assessed users' perceptions of the quality of service and determined the level of user satisfaction at two universities. Ncwane's (2016) study focused on the Mangosuthu University of Technology's Natural Sciences library and Matiwane's (2017) study was to determine student library users' expectations and perceptions of service quality provided by Walter Sisulu University Libraries at the Butterworth campus; both of these studies successfully adopted the LibQUAL+ instrument.
Nel and Fourie's (2016) study examined the information behaviour and expectations of veterinary researchers and their requirements for academic library services. This study believed that there was limited research conducted on veterinary researchers and the role of the library in supporting them. It used qualitative and quantitative methods to collect data from researchers and information specialists by means of questionnaires focus group interviews and citation analyses. The study uncovered that the information needs of researchers were influenced by the area of research and expectations for research output. Findings of this study reveal that there are gaps between researchers' expectations and their own perceptions of roles to fulfil. Researchers need, amongst other things, more information on sources and access, and a more personalised awareness service.
Methodology
This study is a quantitative research, an investigation used primarily for the positivism paradigm. The survey research design was chosen for this study. The population of this study included all registered postgraduate students in the School of Social Sciences of the College of Humanities at the UKZN: Pietermaritzburg campus. The total population of this study was 313 students. To get a proper sample for this study, a stratified random sampling was implemented. The sample chosen for this study was 169 students. In this study, a specific questionnaire was adopted as a data collection instrument. A specific survey was used in this pursuit, and that survey is known as a LibQUAL+ survey instrument. Statistical Package for the Social Sciences v 24.0 (IBM Corp., Armonk, New York, United States) was used to analyse the responses.
Ethical consideration
The researchers were guided by, and adhered to, the ethical code of the University of KwaZulu-Natal. The code is concerned with questions of anonymity, privacy and confidentiality of the students. The researchers obtained a gatekeepers letter and all the participants were clearly informed of the research objectives, and their consent in writing was obtained prior to participation. Ethical Clearance Number: HSS/1357/016M.
Results and discussion
This study's aim was to establish the gap between users' perception and expectations of service quality which was provided to them by the CRM library, and then to identify the strengths and weaknesses of the existing library services. Furthermore, in this section, the user perceptions and expectations of service quality are numerically reported and compared. The positive and negative responses, which are strongly agree and agree, disagree and strongly disagree, are combined together respectively to form one positive (agree) and one negative (disagree); the neutral responses from both the expectations and perceptions were also added together.
In Tables 1-6 below, the users' expectations and perceptions and the gap between them are indicated. In the agree column in the difference columns, the larger the number, the bigger the gap. Also in the neutral and disagree column in the difference columns, the smaller the number, the smaller the gap.
The gap difference between expectations and perceptions of service quality in this category was significantly low (2.9%) for adequate electronic journals. The major gap in this category is 13 (12.4%) in the print collection (books) and 18 (17.1%) in print journals. The major gap in this category implies that the library has not met its users' expectations with regard to adequate print books and journals.
'Comprehensive collection' (Table 1) refers to adequate books, print journals and electronic journals that address the needs of the postgraduate library users and fulfil the objectives of the parent institution. Oyewole and Adetimiring (2015) assert that African universities, such as those in Nigeria, still find it difficult to provide efficient and effective resources. This is because of funding being a challenge facing university libraries, resulting in a decrease in acquisition of information resources like journals (print or electronic).
In relation to South Africa, a report by the International Federation of Library Associations and Institutions (2015) states that academic and research libraries are increasingly playing a crucial role in support of teaching, learning and research. It should also be noted that CRM is one of 12 libraries in UKZN and it can therefore be assumed that the funding received is divided centrally amongst their 12 libraries.
The study indicates that there is a gap between users' expectations and perceptions of service quality relating to access to information. The extent of gaps in this category vary from one service to another. The gap between the expectations and perceptions indicates a significant gap (n = 25, 23.8%) for an efficient short loan service; 19 (18.1%) for re-shelving of journals; 18 (17.1%) for prompt corrective action regarding missing books and journals; 16 (15.2%) for a prompt interlibrary loan service and re-shelving of books; 14 (13.3%) for a catalogue that is clear and has useful information; 12 (11.4%) for easily available access to electronic journals; and 3 (2.9%) for a webpage that is clear and has useful information. The service that has a big gap in this section is the efficient short loan service.
Access to information (Table 2) for this study refers to easily available access to electronic databases, prompt interlibrary loan, an efficient short loan, prompt re-shelving of books and journals, and a catalogue that is clear and has useful information, to mention a few.
The information and resources should be properly stored, preserved and organised in a way that it is easily accessible. Hoppenfeld and Arant-Kaspar (2010) mentions that there have been cases in Texas A&M University and their academic libraries where access to information, more specifically the course reserves collection, is strictly controlled. The situation there was that the students could only check out the materials (books and journals) for 4 h, but they were not allowed to leave the building. The issue was not only for the print material, but also for the audiovisual collection (records or films).
In the African context, Tanzania specifically, Simba (2006) demonstrates that the users of the IUCo library had higher expectations of what the library should offer to them, which were services that allowed them easy access to information. The services that were perceived to be provided poorly were interlibrary loan services, short loan services, and adequate electronic databases. In South Africa, Durban to be specific, Naidu (2009) demonstrates that the users of the MUT library also had higher expectations and lower perceptions of services of easy access to electronic databases and adequate print library collection.
The facilities in the library equipment category (Table 3) showed a large gap in all four statements. The first major gap of 27 (25.7%) was for the computers that work well, followed by 25 (23.8%), which was for the adequate number of computer workstations. There was a gap of 19 (18.1%) for adequate printing facilities and 17 (16.2%) for the adequate number of photocopying facilities. It could be assumed that services in this category were unsatisfactory for respondents because of large gaps that were identified for each service. However, the service with the biggest gap in this category was on the computers that work well.
This category was about an adequate number of computer workstations, computers that work well, adequate photocopying and printing facilities. The library equipment in this study plays a vital role in satisfying users' needs. Relevant resources are not all the library users expect to receive and do their work with; they also require good equipment and facilities.
When this study outlines library equipment, it refers to the Information and Communication Technologies. This equipment includes photocopy and printing machines, as well as computers and their services. They assist in the access of information for the library users, for instance, a computer which is linked to the World Wide Web gives the user access to a wide range of information, most of which can be retrieved with no charge to the users and the library offering the services.
This study revealed that in the staff services category (Table 4), there was no huge gap relating to staff services as compared to other categories. The biggest gaps in ascending orders were: 17 (16.2%) for comments on the staff who are readily available; 14 (13.3%) for those on the staff who instill confidence in users and staff who provide users with information skills for their work or study; 10 (9.5%) for staff who are friendly and staff who have the knowledge to answer users' questions; 8 (7.6%) for staff who understand the users' library service's needs; and, lastly, 3 (2.9%) for staff who are willing to help. In this category, the three services by staff that have the biggest gap were on the staff being readily available, staff who instill confidence in users, and staff who provide users with information skills for their work or study.
In the library staff category, the study focused on staff who are friendly, instill confidence in users, are readily available to respond to queries, are willing to help, and who understand users' library service needs, to mention a few. Academic libraries, or any other library, need qualified, honest, committed and passionate staff members in order to fulfil the library's vision, which is the provision of resources to meet users' information needs. Dimarco and Van Dam (1998) assert that an academic library staff know that the library serves purposes other than purely that of preserver of the human record or gateway to information.
The study revealed that there was a gap between expectations and perceptions regarding the service of 'library as a place' (Table 5). The extent of the gap varied with the individual services. For example, the services that have a significant gap were a need for a quiet library environment which was a concern from 21 (20%) students, whilst 16 (15.2%) students said there was a need for more space for group study and learning, and 13 (12.4%) students felt a need for space that inspires studying and learning. The study further revealed that 10 (9.5%) students expressed a need for a safe and secure place for studying and a service that had a small gap was a library space with sufficient lighting, which was identified by 2 (1.9%) students. The service with the biggest gap is the library being a quiet environment. This gap is significantly accurate because the CRM library is said to always be noisy, thus it can be assumed based on the findings that the students making a noise are those discussing their academic work, which can be aligned with the gap of the students' need for discussion rooms or extending the hours of the current operating timetable. This can be achieved through a careful administering of the service. Also, the quietness in the library environment can be maintained through the enhancing of security personnel and a provision of sound-proofed discussion rooms to control the noise level from disturbing those not in the discussion rooms.
In this study, the library as a place investigated the critical areas and their contribution to the service quality of the library. These areas included: a quiet library environment; library space that inspires students' own study and learning; a library space for group learning and study; and a library environment that has sufficient lighting, to mention a few.
This category is critical to this study in the sense that it is the primary focus of the whole study. It is asserted by Nitecki (2011:27) that the changing paradigms of the academic library as an accumulator and preserver of knowledge resources, service provider for accessing information, facilitate intentional learning and knowledge creation among its users or researchers. The CRM library is a big building and most of the Pietermaritzburg Campus collection is housed in this library; however, there are concerns with regard to not having enough discussion rooms and other concerns which will be brought to light in the following sections. Nitecki (2011) states that library spaces do change slowly, however these changes amongst campus libraries are evident and follow planning and design processes that can happen when informed by conceptualisations that articulate not only what to place within the space but also the result of interactions between the people and their environment.
Simba (2006) discussed the results of the IUCo library as a place, and found that their library users not only expected to receive relevant resources for their work, but they also expected a suitable place to read, to search for information, to discuss with their colleagues or fellow students matters relating to their academic work, and a place to anticipate their academic activities, to outline a few. In this study, the services that had higher expectations were on their library environment having sufficient lighting and the library being a safe and secure environment. The services that had a high negative response were on the library not being a quiet environment and the library space not being conducive enough for group learning and studying. Simba (2006:104) further asserts that the IUCo library is relatively small as compared to the increasing number of its users. Naidu (2009) discusses the high expectations of the MUT library users. The results showed that a library space that inspires learning and a quiet library environment were the services that had high expectations.
The library users do not only expect to receive relevant resources for their studies, they also expect a suitable environment, for which there's comfort and inspiration when they search for information, discuss with classmates the issues related to their academic work, and an environment where they examine academic affairs.
The study revealed that there were gaps identified by students for general services (Table 6). These ranged from 23 (21.9%) for the gap related to the library helping users stay abreast of developments in their field of interest, to 20 (19%) concerning the library helping users to advance in their academic field. The study also showed that in this category the statement on the library helping users with their research needs had a small gap (n = 12, 11.4%). The service that showed the biggest gap was that of the library helping users stay abreast of developments in their field of interest.
Academic libraries in general play a critical role in fulfilling the research and academic needs of the students within a university. This is asserted by Majid, Anwar and Eisenschitz (2001), who argued that a library is reflected as an important and essential component of any high quality research institute. Also, in Naidu (2009), the MUT library users also stated that their research needs were not met by the library and contradicted with Simba's (2006) study on the IUCo library, where users agreed that their library did provide for research needs. What the CRM library can attempt to implement in collaboration with the research office or academic staff is to conduct research-related workshops for postgraduate students, most especially honours and masters students, because at those levels it is imperative that the students know how to draft a comprehensive research proposal and have a clear understanding of each section therein. The CRM library can also try to emphasise the literature and advanced searching workshops for the postgraduate students, and teach them how to use certain databases.
Subject librarians should be available to the postgraduate students to assist and inform them of recent developments occurring in their field of study; this can be done through creating class alerts on the UKZN student emails for students in their different fields of study. This alert can aid the students on what is new, either in their field or in research and these subject librarians can form special workshops for the students in their specific fields on how to do advance searches and properly evaluate the journals and articles accessed by them. Contrary to this, Naidu (2009:148) states that the postgraduate students in MUT library had communication barriers with the subject librarians because of unavailability.
Findings
The study found that there was a gap in almost all the services provided by the CRM library. For example, with regard to the comprehensive collection, the biggest gap was that there were not adequate print journals and print books. In relation to access to information, the major gaps were that the library was not providing an efficient short loan service and re-shelving of journals. It was also found that the library did not take corrective action regarding missing books and journals, or re-shelving of books, and there was no prompt interlibrary loan service.
The study revealed that the library equipment category had more major gaps compared to all other library services. The study found that big gaps were on computers that work well and not having an adequate number of computer workstations. In regard to the library staff, the study found that there is a major gap in staff who are not readily available to respond to the users' queries, staff who instill confidence in the users and, lastly, staff who do not provide users with the information skills needed for work or study. With the library as a place, the study found that the three major gaps were the library not being a quiet environment, the library not having sufficient space for group learning and group study, and a library space that does not inspire users' studies and learning. With regard to the library services concerning research and academic fields, the study found that there were only two big gaps, namely, on the library helping the students to stay abreast of any developments in their field of interest, and the library helping the students advance in their academic field.
This study makes the contribution that there be tools for library evaluation that assess the users' perceptions of service quality and degree of satisfaction with the mission, policies, procedures, library staff, budget and processes of the libraries. In addition, this study suggests that there are barriers to the provision of quality library services and the end-user satisfaction in academic libraries in developing countries. This study also found that the duties of library staff were to increase the level of library users' satisfaction and to assist the new students who were from previous institutions. Finally, this study also suggests that research be done using focus groups and interviews to assess any new services that are introduced in the library.
Conclusion
In summation, the students' expectations were higher than their perceptions of what the library provided. A gap does exist between the users' expectations and perceptions. The perceptions they had of the library services were not in line with their expectations, which resulted in a gap in quality service and service delivery.
The results indicated that the CRM library is deficient in quality service, and the library staff should be encouraged to help users to define and satisfy the quality information needs and provide a standard library service quality. For the library to operate smoothly the CRM library should provide easy access to information, update its library equipment, improve in terms of the staff services, and also improve the 'library as a place'.
The library users had high expectations for most of the services in each category, for instance, comprehensive collection, access to information, library staff, the library as a place and general services. However, their perceptions varied from their expectations in many instances. The students' perceptions were lower in comparison with their expectations of the service quality at the CRM library.
Acknowledgements
The authors would like to acknowledge the postgraduate students of the University of KwaZulu-Natal for their time and effort in making this study possible.
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
M.D.K. devised the topic for the Master's research thesis and S.E.K. helped in refining it in his capacity as the supervisor. M.D.K. was responsible for drafting the article out of the master's study and sent it to S.E.K. for review and positioning. Both M.D.K. and S.E.K. contributed to the design and implementation of the research, to the analysis of the results and to the writing of the manuscript.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Any data that support the findings of this study are included within the article.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Arshad, A. & Ameen, K., 2010, 'Service quality of the University of the Punjab's libraries: An exploration of users' perception', Performance Measurement and Metrics 11(3), 313-325. https://doi.org/10.1108/14678041011098578 [ Links ]
Bhim, S., 2010, 'Adult user perceptions of library services provided by the Bessie Head library in Pietermaritzburg, Msunduzi, KwaZulu-Natal', MIS thesis, University of KwaZulu-Natal, Pietermaritzburg. [ Links ]
Brenza, A., Kowalsky, M. & Brush, D., 2015, 'Perceptions of students working as library reference assistance at a University library', Reference Services Review 43(4), 722-736. https://doi.org/10.1108/RSR-05-2015-0026 [ Links ]
Deng, S. & Zhang, Y., 2015, 'User perception of social questions and answer websites for library reference services', The Electronic Library 33(3), 386-399. https://doi.org/10.1108/EL-12-2013-0213 [ Links ]
Dimarco, S. & Van Dam, S., 1998, 'Late night in an academic library', Library and Archival Security 14(2), 7-23. https://doi.org/10.1300/J114v14n02_03 [ Links ]
Echezona, R.I. & Chigbu, E.D., 2018, 'User expectations and innovative strategies for improved patronage in University libraries in Nigeria', African Journal of Library, Archives and Information Science 28(1), 93-105. [ Links ]
Einasto, O., 2009, 'Using service quality monitoring to support library management decisions: A case study from Estania', The International Information and Library Review 41, 12-20. https://doi.org/10.1080/10572317.2009.10762793 [ Links ]
Fasola, O.S., 2015, 'Perceptions and acceptance of librarians towards using facebook and twitter to promote library services in Oyo State, Nigeria', The Electronic Library 33(5), 870-882. https://doi.org/10.1108/EL-04-2014-0066 [ Links ]
Gannon-Leary, P., Bent, M. & Webb, J., 2008, 'A destination or a place of last resort? The research library of the future, its users and its librarians', Library and Information Research 32(101), 3-14. https://doi.org/10.29173/lirg65 [ Links ]
Habre, C. & Kammourie, H., 2018, 'Redesigning spaces for effective learning: Challenges facing Riyad Nassar Library in meeting users' perceptions and expectations', Journal of Library Administration 58(5), 519-544. https://doi.org/10.1080/01930826.2018.1468674 [ Links ]
Hoppenfeld, J. & Arant-Kaspar, W., 2010, 'Do-it-yourself for course reserves: A student driven service in an academic library', Journal of Interlibrary Loan, Document Delivery and Electronic Reserve 20(5), 353-361. https://doi.org/10.1080/1072303X.2010.520264 [ Links ]
Husain, S. & Nazim, M., 2015, 'Use of different information and communication technologies in Indian academic libraries', Library Review 64(1-2), 135-153. https://doi.org/10.1108/LR-06-2014-0070 [ Links ]
International Federation of Library Associations and Institutions, 2015, The state of libraries in South Africa, Department of Arts and Culture, Pretoria.
Kachoka, N.D., 2010, 'Undergraduate students' perception of the quality of service at Chancellor College Library, University of Malawi', MIS thesis, University of Kwazulu Natala, Pietermaritzburg. [ Links ]
Kekana, M.D., 2016, 'Postgraduate students' perception of the library as an environment for reading, studying and researching at the University of KwaZulu-Natal: Pietermaritzburg Campus. Master's thesis, University of KwaZulu-Natal, Pietermaritzburg. [ Links ]
Kiran, K., 2010, 'Service quality and customer satisfaction in academic libraries: Perspective from a Malaysian university', Library Review 59(4), 261-273. https://doi.org/10.1108/00242531011038578 [ Links ]
Majid, S., Anwar, M.A. & Eisenchitz, T.S., 2001, 'User perception of library effectiveness in Malaysian agricultural libraries', Library Review 50(4), 176-186. https://doi.org/10.1108/00242530110390451 [ Links ]
Matiwane, N., 2017, 'User perception of education students with special reference to the quality of service at Walter Sisulu University library, Butterworth, South Africa', MIS thesis, University of KwaZulu-Natal, Pietermaritzburg. [ Links ]
McNicol, S., 2002, 'Learning in libraries: Lessons for staff', New Library World 103(7-8), 251-258. https://doi.org/10.1108/03074800210438073 [ Links ]
Moon, A., 2007, 'LibQUAL+ at Rhodes University library: An overview of the South African implementation', Performance Measurement and Metrics 8(2), 72-87. https://doi.org/10.1108/14678040710760586 [ Links ]
Naidu, Y., 2009, 'User perceptions of service quality and the level of user satisfaction at the Mangosuthu University of Technology Library, Umlazi, Durban', MIS thesis, University of KwaZulu Natal, Pietermaritzburg. [ Links ]
Ncwane, S., 2016, 'User perception of service quality and level of user satisfaction at the Mangosutho University of Technology's Natural science library, Umlazi, Durban', MIS thesis, University of KwaZulu-Natal, Pietermaritzburg. [ Links ]
Nel, M.A. & Fourie, I., 2016, 'Information behavior and expectations of veterinary researchers and their requirements for academic library services', The Journal of Academic Librarianship 44, 44-54. https://doi.org/10.1016/j.acalib.2015.10.007 [ Links ]
Nitecki, D.A., 2011, 'Space assessment as a venue for defining the academic library', The Library Quarterly: Information, Community, Policy, 81(1), 27-59. https://doi.org/10.1086/657446 [ Links ]
Nitecki, D.A. & Hernon, P., 2000, 'Measuring service quality at Yale University libraries', The Journal of Academic Librarianship 26(4), 259-273. https://doi.org/10.1016/S0099-1333(00)00117-8 [ Links ]
Oyewole, O. & Adetimiring, A., 2015, 'Lecturers and postgraduates perception of libraries as promoters of teaching, learning and research at the University of Ibadan, Nigeria', New Review of Academic Librarianship 21(1), 83-93. https://doi.org/10.1080/13614533.2014.934965 [ Links ]
Pretorius, H.F., 2011, 'Developing a service quality model for an academic library: A case study of the North West University-Vaal triangle campus library', MIS thesis, University of South Africa, Pretoria. [ Links ]
Quintal, V. & Phau, I., 2014, 'Student's perception of an internationalised learning environment', Marketing Intelligence and Planning 32(1), 89-106. https://doi.org/10.1108/MIP-04-2013-0066 [ Links ]
Ramezani, A., Ghazimirsaeed, S.J., Azadeh, F., Esmaeilpour-Bandoni, M. & YektaKooshali, M.H., 2018, 'A meta-analysis of service quality of Iranian university libraries based on the LibQUAL model', Performance Measurement and Metrics 19(3), 186-202. https://doi.org/10.1108/PMM-05-2017-0014 [ Links ]
Sahu, A.K., 2007, 'Measuring service quality in an academic library: An Indian case study', Library Review 56(3), 234-243. https://doi.org/10.1108/00242530710736019 [ Links ]
Simba, C.A., 2006, 'User perception of quality of service at Iringa University College Library, Tumaini University, Tanzania', MIS thesis, University of KwaZulu Natal, Pietermaritzburg. [ Links ]
Trapido, I., 2016, 'Library discovery products: Discovering user expectations through failure analysis', Information Technology and Libraries 35(3), 9-26. https://doi.org/10.6017/ital.v35i3.9190 [ Links ]
University of KwaZulu-Natal, 2014, UKZN libraries, viewed 15 March 2016, from http://library.ukzn.ac.za/TopNav/GeneralInformation/Aboutus919.aspx.
 Correspondence:
Correspondence:
Matsobane Kekana
kekanam@unizulu.ac.za
Received: 03 Feb. 2020
Accepted: 19 Apr. 2020
Published: 09 July 2020
ORIGINAL RESEARCH
Gender and cognitive factors influencing information seeking of graduate students at Kenyatta University Library
Johnson M. MasindeI; Daniel M. WambiriII; Jing ChenI
IDepartment of Information Science, School of Information Management, Central China Normal University, Wuhan, China
IIDepartment of Information Science, School of Education, Kenyatta University, Nairobi, Kenya
ABSTRACT
BACKGROUND: Gender has been identified as a possible influencing factor in users' information-seeking process. Previous studies have alluded to the fact that gender as a variable may be useful for a better understanding of the cognitive and social background of human information processing and may have important implications in the information-seeking process. Although a number of studies have investigated gender, amongst other variables, as having an effect on the information-seeking process of users, no attempt has been made to investigate the relationship between gender and cognitive factors on the information-seeking patterns of graduate students of Kenyatta University Library.
OBJECTIVE: The study investigates gender and cognitive factors influencing the information-seeking process of graduate students at Kenyatta University Library.
METHODOLOGY: To achieve this objective, the study developed a theoretical framework which can be used by academic libraries as a basis for implementing both digital and reference desk services in order to meet the dynamic user needs. The study then investigated whether there were any gender differences through the correlation coefficient in the context of expectancy theory. The motivational process amongst the male and female users was then examined to establish whether there was any difference.
RESULTS: This study found no gender difference in all the variables considered, including interaction service quality, outcome (need satisfaction,) service satisfaction, users' performance of service, past experience, expectancy and effort.
CONCLUSION: This study found no gender difference in all the variables investigated. The implication of the findings was that there is no need for mainstreaming gender in service programming in the library service.
Keywords: gender; cognitive factors; graduate students; information seeking; academic libraries.
Introduction
Information-seeking behaviour is broad and involves a set of actions that an individual takes to express their information needs, seek information, evaluate and select information and, finally, use this information to satisfy their information needs (Brindesi, Monopoli & Kapidakis 2013). It occurs when an individual senses a problem situation which internal knowledge does not satisfy, normally referred to as the mental state 'Anomalous State of Knowledge' (Kassim 2017). Hsieh and Wu (2015) asserted that information seeking is a natural and necessary mechanism of human existence. It is a basic activity of all people and is manifested through particular behaviours.
At the root of information seeking are personal cognitions which are known as cognitive needs. Savolainen (2013) argued that there are three categories of cognitive needs: need for new information, need to elucidate the information held, and need to confirm the information held. The motives that give rise to cognitive needs, and result in information seeking, are physiological, affective and cognitive (Masinde 2016). Cognitive approaches examine the individual user attributes as the main driving forces behind information-seeking behaviour (Masinde 2016). Such approaches would help libraries to answer basic questions such as, why do students approach, stop or avoid using university libraries.
Studies have employed the expectancy theory in the investigation of cognitive factors that influence information seeking (Masinde 2016; Savolainen 2013; Wu, Tang & Tsai 2014). The expectancy theory suggests that people are motivated if valence, instrumentality and expectancy are present. The variable investigated in the context of the above theory is gender. Gender has previously been identified as a variable shaping information-seeking behaviour (Hsieh & Wu 2015). Gender refers to the state of being male or female. Studies have revealed multiple physical, mental and social differences in information-seeking behaviour between men and women (Hsieh & Wu 2015; Savolainen 2013). For instance, Hsieh and Wu (2015) stated that information seeking may vary according to the gender of the user, making it a variable in the information-seeking process.
The study of gender as a factor influencing human behaviour may therefore be helpful when striving to obtain a better understanding of the cognitive and social bases of human information processing, which may also have significant implications for the designing of information services and systems (Kassim 2017). Gender differences, if any, will therefore be investigated through the correlation coefficient in the context of Vroom's expectancy theory which was improved by Porter and Lawler (1968). This is a cognitive motivational theory and it will be expected to help explain the relation between gender and cognitive factors that influence the information-seeking behaviour of graduate students in using the library services (Porter & Lawler 1968). The motivational process between men and women will then be examined to establish whether gender influences the information-seeking behaviour of graduate students at the Kenyatta University Post Modern Library. Accordingly, the study will be user-centred, shifting from previous studies which have been system-centred.
Conceptual framework
The conceptual model in this study is based on the Expectancy Value Theory as propounded by Vroom (1964) and imported by Campbell et al. (1970). The common factors are valence, expectancy, instrumentality, value of outcome, and effort. These perceptions are tempered by the service personnel's (interaction service quality) and users' past experience. These last factors influence service users whilst they are performing the service.
The study assumes an awareness of cultural and biological identities amongst the respondents. It is significant that this research expected to develop a theoretical framework or model which can be used by academic libraries as a basis for developing both digital and reference desk services that would meet dynamic user needs. Accordingly, gender differences, if any, were investigated through the correlation coefficient in the context of the expectancy theory. The motivational process amongst men and women was examined to establish whether there was a difference.
Literature review
Gender has been identified as one of the variables influencing information seeking (Hsieh & Wu 2015; Khaola & Mabilikoane 2015; Savolainen 2013). For instance, Khaola and Mabilikoane (2015), in a study of cancer information service, found that use of the service was mainly by women (80%). In another study by Sacks (1994), as quoted by Conrad (2014), it was found that high school student attitudes towards computers and their use varied by gender. Gender was considered as a major predictor of internet use and attitudes. Men seemed to use browsing for enjoyment whilst women tended to use it for work-related purposes. Equally, Rehman (2016) observed that girls and boys differed in their search patterns when using library services to find answers to specific questions. According to the study, boys tend to use horizontal search methods when searching the web in which they iteratively submit searches and then scan the document snippets returned as search results. In contrast, girls tend to employ vertical search methods in which they open and browse the web pages returned by the search engine without reviewing the list or filtering out irrelevant results. In the end, the strategy adopted by most boys tends to provide superior search performance.
Wu et al. (2014) also established that women tended to experience more difficulties finding information online. They felt less competent and comfortable using the internet. The study, however, found no link between women and low self-efficacy, meaning it is not the gender variable that determines self-efficacy. Whilst this study alluded to the fact that gender studies in general had been done, it tried to ground gender as a variable within the motivational process theory in the context of academic libraries.
Brindesi et al. (2013), whilst investigating the factors that affect international students' information-seeking behaviour, found that female immigrants had higher social-cultural and psychological adaptation scores than male immigrants, but had lower competencies with regard to the use of computerised library resources and technologies. According to Brindesi et al. (2013), most database searching requires extensive computer use and familiarity, which affected their ability. On the other hand, male immigrants seemed more comfortable around information technologies. Therefore, in this area, men were more satisfied and confident and had fewer difficulties than women. Another study by Halder, Ray and Chakrabarty (2010) also argued that gender is an essential variable in information-seeking behaviour. The study stated that satisfaction with a service varied in accordance with the gender of the library user. The men were more comfortable around computers, freely and easily interacting with them, as compared to their female counterparts who seemed to seek the assistance of a reference librarian from time to time.
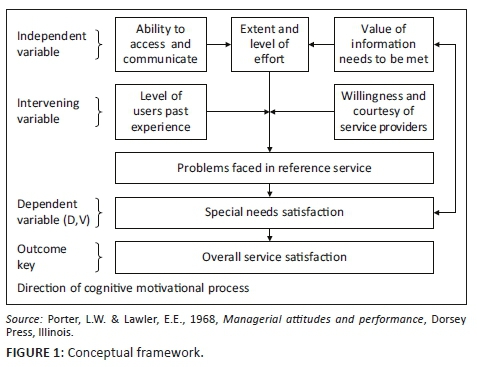
In summary, the review of literature revealed that the information needs, as well as the information-seeking behaviour amongst men and women, do not show any uniform and consistent pattern. The findings have also revealed that there are variations of needs and behaviour for seeking information between an individual man and woman. In this context, the study seeks to investigate gender and the cognitive factors influencing the information-seeking behaviour of graduate students at Kenyatta University.
Methodology
The purpose of this study was to investigate gender and the cognitive factors that influence the information-seeking process of graduate students at Kenyatta University. The determinants were based on Vroom's (1964) expectancy theory of motivation. The theory suggests that individuals will be motivated if three factors are present:
-
Valence - they must value the outcome;
-
Expectancy - they should expect that they are capable of performing the behaviour that is instrumental to the outcome;
-
Instrumentality - they must believe that the desired behaviour is instrumental in achieving the valent outcome.
Research design
According to Nardi (2015), survey research design offers higher representativeness, convenience in collection of data, statistical significance and accuracy in outcomes or findings As a matter of fact, survey research design enables the investigator to gather large amounts of data and employ validated models to arrive at statistically meaningful results (Wisdom & Creswell 2013). Consequently, this study utilised survey research design as a framework for collection of data. The survey research was cross-sectional and the data were collected using a questionnaire. The data collected were quantitative in nature and were collected from graduate students at Kenyatta University Library. The research then examined the relationship between gender and the cognitive factors that affect the information-seeking process of users.
Variables
A variable is an attribute on which cases vary. Cases in this study were the students who use the library. The independent variables in this study were the information needs and the expectancy levels. The dependent variable in this study was gender.
Value of outcomes: According to Vroom (1964), value of outcome is the valence. The valence is an individual's subjective judgment about possible outcome or, simply put, the value an individual attaches to rewards. There can be a discrepancy between the anticipated satisfaction from an outcome (valence) and the actual satisfaction. Outcomes are need satisfactions. This variable referred to the anticipated value library attach to their information needs being satisfied through the use of the library service. An outcome is positively valent when a person prefers attaining it to not attaining it, and an outcome has a valence of zero when a person is indifferent to attaining it. This concept assessed differences amongst the male and female users with regard to their subjective judgment about possible outcome. A five-point Likert scale was used on each of those aspects.
Effort-to-performance expectancy: This is the second variable in this study. It is the library user's estimated probability that he or she can accomplish a task, given effort or the belief that an individual's effort will lead to realisation of the desired outcomes (Vroom 1964). It is the likelihood that he or she can perform a task at a given level and that his or her effort will lead to successful performance. This was scored on a Likert scale. Two main areas were scored: the conviction that different genders will be able to use the service without problems and that different genders will be able to communicate with the librarians offering the service.
Effort by the user: This is the amount of energy library users exert in the information-seeking process. According to Porter and Lawler (1968), effort is influenced by the value of rewards. The intensity of effort an individual puts in depends on the perception that the effort will result in a desired outcome (Vroom 1964). If the rewards can satisfy an individual's needs for security, self-esteem, autonomy and self-actualisation, the rewards are considered valuable to the individual. Judging the value of rewards, individuals can then determine the effort they put in a search. There is also a perceived probability that there is a close relationship between effort and reward.
Service performance/accomplishment: Library services are produced interactively with the different genders. The study examined how well different genders performed the basic requirement of the reference service without difficulty. This variable focused on how the different genders executed or performed the basic requirements of a reference service in service delivery. Access issues and challenges faced by the different genders whilst executing the tasks were assessed and scored.
User perception interaction service quality: Interpersonal interactions that take place during the service delivery between the reference librarian and the different genders were assessed. The study considered the service provider's response, willingness, courtesy and ability. The different genders' perception of the service quality was assessed.
User's past experience: This refers to the previous and memorable experiences a user has had with the service - the overall experience by the service user. This was important because it influenced the different genders' own convictions in their own effectiveness (Bandura 1977) or self-efficacy.
Library user service satisfaction: This is the overall assessment of the service experience by the different genders - the subjective judgment of the service by the different genders. It included service features, attribution of service success or failure and perceptions of equity and fairness. Extent of the different genders' satisfaction, the likelihood of repeat use and the possibility of the users recommending the service to somebody else.
Location of the study
This study was carried out in Kenyatta University Library. The role of a library is to support teaching, learning and research. Kenyatta University was selected because:
-
The Post-Modern Library has some of the latest library facilities; inaugurated in 2010 with a sitting capacity of 6000 students. The investment took over 10 million USD (Kenyatta University 2013).
-
Kenyatta University has one of the largest number of graduate students (13 193). Accordingly, the library service requires to know how to meet the information needs of such users.
Target population
The number of registered graduate students stood at 13 193 in 2017 (Kenyatta University 2018). This was the target population in this study.
Sampling techniques
To select the participants, a quota sampling method was utilised. Quota sampling permits investigators to sample a subunit that is of great importance to the investigation. The design demanded that the data be collected at one point in time from a specified population, especially where the data collected was to be subject to correlation analysis (Ary, Jacobs & Sorensen 2010). The study targeted the collection of data from a sample of 373 out of a total of 13 193 postgraduate students. Postgraduate library users were intercepted in the postgraduate floor of the postmodern library. The researcher explained the purpose of the study and then requested them to spare a few minutes to complete the questionnaire. The instruments were collected as soon as they were completed.
Sample size
Sample size was calculated by determining the sample size of an infinite population and then adjusting it to the sample size of the required population, which was 13 193 (Cochrun 1977). For the purpose of this study, a 95% confidence level was expected. This corresponded to a Z score of 1.96 and a 5% margin of error (Saunders, Lewis & Thornhill 2009). Given that the 13 193 students had an equal chance of being selected, the sample size was 373.
Calculation of sample size
-
Sample size was calculated by determining the sample size of the infinite population and then adjusting it to the sample size of the required population (Cochrun 1977)
-
Formulae of sample size for infinite population:
■ S = Z2 * P* (1−P) /M2
■ where: S = Sample size for the infinite population
■ Z = Z score
■ P = Population proportion (Assumed to be 50% = 0.5)
■ M = Margin of error
-
Z score determined based on confidence level
-
Confidence level = 95%
-
Z = 1.96
-
M = 0.05
-
Substitution of formulae [S = (Z2) * P* (1−P)/(M2)]:
■ S = (1.96)2 * 0.5 *(1-0.5)/ (0.052)
■ S = 3.8416 * 0.25/ 0.0025
■ S = 384.16
-
Adjustment of the sample to the required population:
■ Population of Kenyatta University post-graduate students is = 13 193
■ Formula for adjusted sample size = (S)/ 1+ [(S - 1)/ Population]
■ Adjusted sample size = 384.16/1+ [(384.16 - 1)/ 13 193
■ Adjusted sample size for Kenyatta University post-graduate students = 373
Research instruments
The study used a questionnaire which was developed on the basis of the objectives of the study and the variables. The variables were: Interaction service quality, Effort-to-performance (EP) Expectancy, User needs satisfaction, Service Performance (Service satisfaction), Effort by the user, Outcome, Value of outcomes, User's past experience, and gender relationship with cognitive variables.
Pretesting and/or piloting study
A pilot study was carried out at a private university, namely, Methodist University, Nairobi campus. It was selected because it has a library that offers digital information services. It is also well funded. The pilot involved seeking permission from the university librarian. Once permission was granted, an appropriate date for distributing the questionnaire was fixed. About 20 participants were selected. The questionnaire was given out to them and collected later. The intention of the pilot study was to validate that the study population would comprehend the questionnaire. The pilot findings revealed that the students comprehended the questions with no difficulty.
Validity
To collect data, the researcher ensured that the questionnaire was appropriate. This was done by testing internal consistency of the questionnaire. Reliability refers to the consistency of a measure of a concept. It entailed asking whether the measure was stable so that the study could be confident that the results relating to that instrument were reliable and did not fluctuate. Cronbach's alpha coefficient was used to test reliability. The figure 0.70 alpha levels was employed as a rule of thumb to denote an acceptable level of reliability.
The instrument already developed for this study was a multiple-item measure for each concept, for example, outcome, EP Expectancy and past experience. This was done to avoid the potential problems associated with overreliance on a single indicative measure. The study used Cronbach's alpha coefficient to test the consistency of the questions. Each variable achieved a coefficient greater than 0.7.
Data collection techniques
Questionnaires are known to be easy to construct and administer as they can reach larger populations at relatively cheaper costs. Most people are also familiar with them. The study therefore adopted the questionnaire as a data collection technique. In the questionnaire questions are asked about people's gender, beliefs, opinions, characteristics and behaviour, and was then used as a source of data. The data collected described the variable of gender as a factor that influences information seeking amongst the students. The questions were categorised as follows:
-
Preference questions which focused on the gender of the participants and what they thought about a library service.
-
Reported behaviour and likely behaviour focusing on what the different genders say they do in terms of making choices to use or avoid using the library.
Data analysis techniques
The data collected was analysed quantitatively through Statistical Software for Social Sciences (SPSS) v 21.0 (IBM Corp., 2012, Armonk, New York). The following steps were taken:
-
Organise and learn the data.
-
Summarise the findings using averages, and present in the form of tables.
-
A correlation analysis was done to examine how closely the variables were connected. These variables were the ones identified to have some bearing on information seeking. Correlation research helped in understanding the relationships between gender and the factors which were being considered in this study as the ones which were likely to drive information seeking amongst graduate students. The correlation coefficient ranges from +1 showing a perfect positive correlation and a −1 showing a negative correlation.
-
The connections between variables were explored through discovering associations of two variables to a significant level using chi-square as a statistical test. It was tested as P < 0.05 (1 in every 20). The significance level measures how frequently the conclusion will be wrong in the long run. A 0.05 or 5% significance level means that, in the long run, this type of conclusion will be wrong 5% of the time (Mahuli & Mahuli 2015).
The study also used multiple regression analysis to interpret the results. This allowed for exploration of interrelationship amongst the variables.
Logistical and ethical considerations
The purpose of ethical considerations in research is to ensure that no individual suffers from harmful effects as a consequence of research activities (Cooper 2003). Consequently, in this study great care was taken with the issues that could arise in relation to research and participants. This included harm, confidentiality, informed consent, and invasion of privacy.
Findings, interpretation and discussion
The purpose of this study was to investigate gender and cognitive factors the information-seeking seeking of graduate students at Kenyatta University Library. The study was based on the expectancy theory of motivation developed by Vroom (1964) and improved by Porter and Lawler (1968). The theory deals with the mental models/processes an individual undergoes to make choices - in this case, to use or avoid using the library reference service. The findings are discussed and interpreted below.
General and demographic information
This section presents data on personal characteristics in the study. These were based on gender. The respondents for this study were postgraduate students at Kenyatta University main campus library. The data were collected in November and December 2017. This enabled the study to access both regular, Institutional Based Programmes and Kenyatta University Digital School of Virtual and Open Learning students. Students participated out of an expected sample size of 373. However, four responses were struck from the study during data cleaning, thus a total of 369 were analysed. Of these, 222 (60.1%) were men and 147 were women (39.9%). Table 1 shows the demographics of the study.
Relationship between cognitive factors and gender
Outcomes and gender
Outcome in this study may be explained as 'information needs satisfaction'. It had four main elements, as follows:
-
Helpfulness of the service given by librarians.
-
Satisfaction with information acquired through face-to-face reference service.
-
Usefulness of information from reference librarians.
-
Satisfaction acquired through digital reference service.
Nearly three-quarters of the male students (72.6%) reported that librarians gave helpful information, and an almost equal proportion (71.2%) of female students felt that the information given to them by the face-to-face reference service was helpful. There seemed to be no difference between male and female students on the helpfulness of information given to them. A correlation coefficient of −0.003 was found for the relationship between gender and helpfulness of information given to them. The two variables related negatively. The score on the issue of satisfaction did not show significant differences amongst men and women, as shown in Table 2. A very small number was dissatisfied with the information acquired through the face-to-face reference service, as is shown by those who disagreed with the statement. About one-quarter (24.0%) of the female students were not decided on whether they were satisfied or not, whereas 20% of their male counterparts were also undecided.
Satisfaction and gender
A total of 64.5% of the men and 56.4% of the women agreed that the information given to them by reference librarians was useful. Further analysis showed that less than one-fifth of both the women (19.3%) and men (15.7%) strongly disagreed that the information given by face-to-face reference librarians was useful (Table 2).
Satisfaction with information acquired through digital reference
There was a difference of opinion between genders on the satisfaction with information acquired though digital reference. The men (62.0%) seemed to be more satisfied than the women (50.3%) with the information acquired through digital means. There seemed to be no significant difference of opinion amongst the male and female students on an indicator of satisfaction with regard to information acquired through the digital reference service. A correlation of −0.84 was established between gender and outcomes.
Gender and value of outcome
On assessing whether there were gender differences on the cognitive variable of 'value of outcomes', three issues were considered:
-
Desirability of information needed to be met through a face-to-face reference service,
-
Importance for information needs to be met through a face-to-face reference service, and
-
Value of information needs to be met through a face-to-face reference service.
Table 3 shows the importance of information needs to be met through face-to-face reference services.
The majority of both male (63.3%) and female (68.4%) students agreed that it was very valuable for their information needs to be met through a face-to-face reference service. Those who felt that it was not valuable for their information needs to be met in this way were 16.5% of the women and 18.4% of the men. There did not seem to be significant differences between the gender perception of the value of the outcome variable (Table 3).
A similar finding was obtained on the importance for their information needs to be met through a face-to-face reference service. The majority of the participants (62.6% male and 68.0% female) felt that the service was important, 17.9% of men and 19% women disagreed, and 19.6 men and 16% women were neutral. On whether it was desirable for their information needs to be met through a face-to-face reference service, 67.6% of the male and 70.3 of the female students agreed with the statement that it was important for them to have their information needs met through such a service, whilst 14.5% of both male and female participants disagreed with the statement (Table 4).
When considering gender and value of outcome, there seemed to be no gender difference on the issues of desirability (68.7%), importance (64.7%) and value (65.85%) of needs to be met through a face-to-face reference service. The gender variable showed a −0.52 correlation to value of outcome. This was a medium negative correlation between the two variables, and was considered significant at a 0.05 level of significance.
There were comparatively few participants who did not think it was valuable, important and desirable for the information needs to be met through face-to-face interaction.
Gender and interaction service quality
Interaction service quality was assessed in two ways:
-
Willingness of face-to-face personnel to help.
-
Courteousness of face-to-face reference service personnel.
Male respondents thought that the service personnel had either a high (44.3%) or very high (8.8%) willingness to help - this represented over half (53.1%) of the male students. The female respondents who rated the service personnel's willingness to help as either high (28.9%) or very high (7.2%) represented 36.1%. There was a 17.0% difference of rating between male and female students in this regard. Of the male respondents, 15.4% thought that the service personnel had a low willingness to help, whilst 8.3% rated this as very low. Female respondents, however, rated these as low (23%) or very low (15.1%). The situation was as shown in Table 5.
The male respondents rated the service personnel's courtesy to be either high (39.7%) or very high (10.5%). This meant that about half (50.2%) of the male respondents rated the service personnel's courtesy positively. By comparison, only 9.5% of the female students rated the service personnel's courtesy as high (29.5%) or very high (9.4%) (Table 6).
Courtesy and gender
Almost half of the female students (38.9%) rated courteousness as being high or very high. Overall, one-third (30.9%) of the female respondents considered the service personnel's courteousness to be low or very low, whereas only one-fifth (21.0%) of the male respondents had the same rating. Despite the differences between male and female ratings, gender did not seem to be a significant enough discriminator for this metric. Overall interaction service quality and gender showed a negative relationship (−0.156), meaning that gender and interaction service quality were negatively correlated. Figure 2 shows this relationship.
Gender and overall satisfaction with a face-to-face reference service
The satisfaction ratings show that the female students were less satisfied than male students. A correlation of −0.100 was found between overall satisfaction and gender. This meant that gender and overall satisfaction were negatively correlated. Equally, on the likelihood of using a face-to-face reference service in the future, more male students (68.6%) were likely to do so than female students (61.6%).
Only 20.3% of male and 29.2% of female students were not likely or very unlikely to recommend the face-to-face reference service to friends and colleagues. Overall library user satisfaction with the service was negatively correlated with gender, indicating that the decisions of recommending or not recommending face-to-face reference service to friends and colleagues were not likely to be influenced by gender. The ratings for the likelihood to use the service in the future and the likelihood of recommending the service to friends and colleagues were comparatively close amongst male and female students. They were both likely to use the service and to recommend the service to friends. Table 7 shows the likelihood of using a face-to-face reference service in the future.
Gender and effort by users of face-to-face reference service
Effort by the user of the reference service was considered in the following ways:
-
Extent of use of reference service.
-
Level of effort spent using face-to-face reference service.
The scores between male and female respondents on the extent of use of face-to-face reference service were close. The majority (69.6%) of the male respondents considered the extent of use to be either low (21.3%) or medium (48.3%). The female repondents (73.0%) assessed the extent of their effort to be either low (27.6%) or medium (45.4%) as well. Both male and female participants scored the extent of use of face-to-face reference to be either low or medium. One-fifth of the men assessed their extent of effort to be high (20.0%), and 16.4% of women felt the same. A small proportion (4.3% of the male respondents and 5.9% of the females) rated their effort to be very high. There seemed to be an insignificant difference between men and women (Table 8).
There was a negative correlation (−0.054) between gender and the extent of use of face-to-face reference service.
The level of effort spent using face-to-face reference service was reported to be mainly low (24.0%) and medium (48.8%) for male respondents, whilst the female respondents had a combined level of 70.4% clustered around low and medium effort. Both men (72.8%) and women (70.4%) had very similar ratings for their level of effort.
On whether there was a difference between genders, the extent of use of face-to-face reference service was close. The majority of men (69.6%) considered the extent of use to be either low (21.3%) or medium (48.3%). The women (73.0%) assessed the extent of their effort to be either low (27.6%) or medium (45.4%). Both genders assessed the extent of use of a face-to-face reference service to be either low or medium. One-fifth of the men assessed their extent of effort to be high (20.0%), versus 16.4% of the women. A small proportion rated their effort to be very high (4.3% of the male students and 5.9% of the females). There seemed to be an insignificant difference between male and female respondents. On the correlation between gender and effort, there was a negative correlation (r = 0.54). A medium negative correlation was established.
Performance and/or accomplishment of the service and gender
Performance of the service was assessed in two ways:
-
Problems faced with digital reference service.
-
Problems faced communicating with reference librarian.
About 58.6% of male and 54.9% of female students reported that they had problems with the digital reference service. About 12.3% of the male respondents and 12.6% of the female were neutral. This should mean that over 60% of students of both genders had problems with the digital reference service. Only about one-third (28.9%) of the men and a similar proportion of the women (32.5%) reported that they did not have problems with the digital reference service. Performance/accomplishment of service by users was found to be negatively correlated to gender (−0.47).
On the problems faced with communicating with the reference librarian, 49.4% of the men and 40.8% of the women reported that they did not have problems. At the same time one-third, 31.6% of men and 34.2% of women, acknowledged that they had problems with communication with the reference librarians. Hence, about half of the respondents (both male and female) could communicate with the reference librarians without problems. Both female and male respondents had very close findings on the variable of communicating with reference librarians, and a negative correlation coefficient of −0.02 was found between gender and ability to communicate with the reference librarian.
Users' past experience and gender
Users' past experience was assessed in two main areas:
-
Experience with reference service.
-
Experience with digital reference service.
Users' experience with the face-to-face reference service was rated to be mainly low (27.6%) and medium (44.2%). This meant that 71.8% of the respondents rated their experience to be mainly medium and low. Only about 8.9% were neutral. About one fifth (19.2%) reported that they had a high or very high rating of their experience with the face-to-face reference service. These rating scores were comparatively close for both male (70.7%) and female (73.5%) respondents. A similar pattern was found in those respondents who considered their experience to be high (19.7% for male students and 18.6% for females). Both male and female respondents scored their experience similarly on the face-to-face reference service.
A negative correlation coefficient of −0.010 was found. Gender and level of experience were negatively correlated. The level of experience with digital reference service was mainly low (20.7%) and medium (33.1%). This meant that about half of the men (54.2%) and women (53.3%) had a low or medium experience. Apparently, 37.6% of men and 37.5% of the women considered their experience with the digital service to be high. An analysis of the level of experience in both male and female respondents showed that it was close and there was little difference. A negative correlation of −0.026 was found between level of experience with digital and gender.
Cognitive factors and gender
Previous studies had found two main positions on gender and user services. Some found that there was a difference between men and women on the use of services (Brindesi et al. 2013; Ford, Miller & Moss 2001; Halder et al. 2010). Some studies (Brown 2001; Hsieh & Wu 2015) found no gender difference amongst students' use of a digital library (Rehman 2016). This study found no gender differences in all the variables considered, including interaction service quality, outcome (need satisfaction), service satisfaction, users' performance of service, past experience, expectancy and effort. The implication of this was that there is no need for mainstreaming gender in service programming in the library service.
Conclusion
This study examined gender as one of the drivers and triggers of cognitive factors that influence information-seeking behaviour, prior to contacting the librarian. Cognitive information-seeking behaviour was considered as an approach to how an individual applies his or her mental models of the world to process information seeking. The focus was user-covered and the study utilised the expectancy theory of motivation to explain information seeking. The expectancy theory can explain information seeking as being driven by cognitive factors. These cognitive factors that, combined together, influence information-seeking process prior to making contact with reference librarians, include interaction service quality, outcomes (needs satisfaction), overall satisfaction of service, users' competencies in performing a service, expectancies and past experience. Consequently, this study investigated whether there was a relationship between gender and these cognitive factors that influences information seeking. The study found that there was no relationship between gender and all the cognitive variables. Information seeking was not affected by gender as there was no gender-based difference. There were more similarities between male and female respondents on cognitive information seeking, however, gender made no difference in predicting cognitive information seeking.
Implication
The implication of this finding was that the library need not develop any interviewing strategies to develop mental images or experiences based on gender.
Recommendations
An appropriate information literacy programme needs to be developed which would integrate information-seeking skills in both learning and teaching, aimed at developing positive mental experiences. The library system developer would want to make systems as convenient and friendly as possible. Such a user-centred system should recognise that students of either gender search for information as individuals, and should help them to build high self-esteem.
Equally, future studies could investigate the relationship between gender and cognitive factors that influence information seeking in different settings, for the purpose of drawing clearer and wider generalisations.
Acknowledgements
This study would not have been possible without the exceptional support of Professor Jing Chen, and the whole community of Central China Normal University for agreeing to sponsor the study. We forever remain grateful.
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
All authors contributed equally to this work.
Ethical consideration
This article followed all ethical standards as set out by the scientific community of researchers.
Funding information
The publication cost is funded by the Central China Normal University.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Ary, D., Jacobs, L.C. & Sorensen, C., 2010, 'Introduction to research in education', Wadworth 35, 63-68. [ Links ]
Bandura, A., 1977, 'Self-efficacy: Towards unifying theory of behavioural change', Psychological Review 84(2), 191-215. https://doi.org/10.1037/0033-295X.84.2.191 [ Links ]
Brindesi, H., Monopoli, M. & Kapidakis, S., 2013, 'Information seeking and searching habits of Greek physicists and astronomers: A case study of undergraduate students', Proceedings in Social and Behavioural Sciences 73, 785-793. https://doi.org/10.1016/j.sbspro.2013.02.119 [ Links ]
Brown, S.P., 2001, 'Self-efficacy as a moderator of information-seeking effectiveness', Journal of Applied Psychology 86(5), 1043-1051. https://doi.org/10.1037/0021-9010.86.5.1043 [ Links ]
Campbell, J.J., Dunnette, M.D., Lawler, E.E. & Weick, K.E., 1970, Managerial behavior; Performance and effectiveness, McGraw-Hill Book Company, New York, NY.
Cochrun, W.G., 1977, Sampling techniques, Wiley & Sons, New York, NY.
Conrad, S., 2014, 'Toward improved discoverability of scholarly content: Cross-sector collaboration essentials', Collaborative Librarianship 6(1), 42-46. [ Links ]
Cooper, D.R.A.S., 2003, Business research methods, McGraw-Hill, Irwin, Boston.
Ford, N., Miller, D. & Moss, N., 2001, 'The role of individual differences in internet searching: An empirical study', Journal of the American Society for Information Science and Technology 52(12), 1049-1066. https://doi.org/10.1002/asi.1165 [ Links ]
Halder, S., Ray, A. & Chakrabarty, P.K., 2010, 'Gender differences in information seeking behaviour in three universities in West Bengal, India', The International Information & Library Review 42, 242-251. https://doi.org/10.1080/10572317.2010.10762869 [ Links ]
Hsieh, Y.-Y. & Wu, K.-C., 2015, 'The influence of gender difference on the information-seeking behaviors for the graphical interface of children's digital library', Universal Journal of Educational Research 3(3), 200-206. https://doi.org/10.13189/ujer.2015.030305 [ Links ]
Kassim, N.A., 2017, 'Evaluating users' satisfaction on academic library performance', Malaysian Journal of Library & Information Science 14, 101-115. [ Links ]
Kenyatta University, 2013, Historical development of Kenyatta University Library, Kenyatta University Press, Nairobi, Kenya.
Kenyatta University, 2018, Postgraduate Prospectus, Kenyatta University Press, Nairobi, Kenya.
Khaola, P.M. & Mabilikoane, M., 2015, 'Perception of library service quality, satisfaction and frequency of use of library resources', Journal of Humanities and social sciences 7, 44-52. [ Links ]
Mahuli, A.V. & Mahuli, S.A., 2015, Significance of statistical significance. Journal of Dental Research and Review 2(3), 106. [ Links ]
Masinde, J.M., 2016, 'Investigation of mobile library user needs of international students based on the expectancy theory of motivation', Research Journal of Library Sciences 4, 14-30. [ Links ]
Nardi, P.M., 2015, Doing survey research: A guide to quantitative research, Routledge, London, United Kingdom.
Porter, L.W. & Lawler, E.E., 1968, Managerial attitudes and performance, Dorsey Press, Illinois.
Rehman, S.U., 2016, 'Measuring service quality in public and private sector university libraries of Pakistan', Pakistan Journal of Information Management & Libraries 13(1), 1-11. [ Links ]
Sacks, M., 1994, Cognitive closure and the limits of understanding, Wiley Online Library, London, United Kingdom
Saunders, M., Lewis, P. & Thornhill, A., 2009, Research methods for business students, Pearson, New York, NY.
Savolainen, R., 2013, 'Approaching the motivators for information seeking: Viewpoint of attribution theories', Library and Information Science research and International Journal 35(1), 63-68. https://doi.org/10.1016/j.lisr.2012.07.004 [ Links ]
Vroom, V.H., 1964, Work and motivation, Wiley.
Wisdom, J. & Creswell, J.W., 2013, Mixed methods: Integrating quantitative and qualitative data collection and analysis while studying patient-centered medical home models, Agency for Healthcare Research and Quality, Rockville, MD.
Wu, K.C., Tang, Y.M. & Tsai, C.Y., 2014, 'Graphical interface design for children seeking information in a digital library', Visualization in Engineering 2(5). https://doi.org/10.1186/2213-7459-2-5 [ Links ]
 Correspondence:
Correspondence:
Johnson Masinde
masindejohnson@mails.ccnu.edu.cn
Received: 25 Sept. 2019
Accepted: 10 Apr. 2020
Published: 14 July 2020
ORIGINAL RESEARCH
Exploring the impact of cloud computing on existing South African regulatory frameworks
Mpho MohlameaneI; Nkqubela RuxwanaII, III
IResearch Department, Da Vinci Institute for Technology Management, Modderfontein, South Africa
IICybersecurity Research Centre, Defence and Security, Council for Scientific and Industrial Research, Brummeria, Pretoria, South Africa
IIIInformatics Department, Faculty of Information and Communication Technology, Tshwane University of Technology, Pretoria, South Africa
ABSTRACT
BACKGROUND: The use of cloud computing services raises policy and regulatory challenges globally, more specifically on data security and privacy, amongst other issues. There is a concern on whether South African information and communications technology (ICT) policies and regulatory frameworks are sufficient to address emerging cloud computing regulatory challenges. Therefore, this necessitates a review to determine the extent to which existing regulatory frameworks are applicable to cloud computing and the challenges thereof.
OBJECTIVES: The study determines the impact of cloud computing on existing South African ICT policies and regulatory frameworks and ascertains whether they are sufficient to address challenges regarding the use of cloud computing services.
METHOD: The study followed an interpretivism philosophical stance. A multi-method qualitative research approach was employed and a thematic analysis was applied in which the data was collected through interviews, questionnaires and document analysis.
RESULTS: The existing policies and regulatory frameworks as applicable to computing are playing 'catch-up' where technology has a footprint. Moreover, some existing policies use a blanket approach and are not specific to the subject matter. As a result, there is a need for policies that are future-proof and specific to the subject matter.
CONCLUSION: The emergence of cloud computing has exposed the existing ICT policies and regulatory laws as being inadequate to address cloud computing developments, complexities and challenges, especially challenges related to public confidence regarding the use of cloud computing services and cloud competitiveness.
Keywords: cloud computing; policy; law; regulation; cloud computing regulatory; South African cloud regulatory framework.
Background of the study
Cloud computing is considered to be a cost-effective information and communication technology (ICT) solution that, when implemented appropriately, can help mitigate challenges experienced with the use of traditional ICT, such as high costs of procurement and maintenance of ICT infrastructure within organisations (Alharbi 2017; Mohammed & Ibrahim 2015).
Even though cloud computing services provide essential benefits for individuals and organisations, there are challenges that negatively impact on the public confidence regarding the adoption and use of cloud computing, as well as cloud computing competitiveness. The public confidence challenges in relation to cloud computing services foster doubt and uncertainty regarding the safety and privacy of data and the loss of control on data in the cloud computing environment. While the competitiveness challenges impede the growth of the cloud computing market as this could lead to digital monopoly, hampering the growth of new cloud services providers into the market.
The challenges that impact on public confidence regarding the adoption and use of cloud computing includes security and reliability issues (Abolfazli et al. 2015; Mahler 2014; Vasiljeva, Shaikhullina & Kreslins 2017); access to underlying ICT infrastructure that enables cloud computing to thrive (i.e. broadband costs and quality issues); and regulatory, governance, and legal uncertainties (Abolfazli et al. 2015; Gillwald & Moyo 2016; Kumar & Vajpayee 2016; Vasiljeva et al. 2017).
Cloud computing challenges that impact on the cloud computing market growth and competitiveness includes, but is not limited to, data portability and interoperability, vendor lock-in, vertical integration and discrimination issues, data cross-border and jurisdictional challenges, and lack of cloud computing standards (Scholtz, Govender & Gomez 2016; Sluijs, Larouche & Sauter 2012; Van Gorp & Batura 2015). These challenges can negatively impact new entrants into the market by means of digital monopolisation, and thus impact on cloud computing competitiveness.
In addition to these challenges, what is important to note is that the lack of a national cloud computing policy framework has been identified as a barrier and explains the slow cloud computing adoption, more specifically in the public sector (Gillwald & Moyo 2016; Scholtz et al. 2016). The absence of a cloud computing policy framework to help build public confidence regarding the adoption and use of cloud computing services and to improve competitiveness is not only affecting South Africa but Africa as well. There seems to be slow progress in Africa in developing cloud computing policies (Abubakar 2016; Muhammed et al. 2015). These challenges emphasise the need for a cloud computing policy framework, not only for the public sector, but also for the other sectors of the economy since some of these challenges cut across all sectors of the economy.
In this paper we review some of the ICT and legislative frameworks and ascertain to what extent these regulatory frameworks relate to the emergence of cloud computing. This will ascertain if there are any gaps that need to be addressed.
Cloud computing services are accessible over the internet. It is necessary to look at policies and regulatory laws that govern electronic communication and transactions. It is also necessary to include policies that govern consumer protection and ascertain what impact these policies could have on cloud computing. As cloud computing services are geographically dispersed, it is necessary to look into policies that protect personal information in relation to the emergence of cloud computing. For these reasons four legislative policies were reviewed, namely the Electronic Communication and Transaction Act (ECTA), the South African Competition Act, the Protection of Personal Information Act (POPI), and the National Integrated ICT Policy White Paper.
South African information and communication technology regulatory frameworks related to cloud computing
This section discusses some existing South African ICT policies and regulatory frameworks in relation to the emergence of cloud computing, starting with the Protection of Personal Information Act (POPI).
Protection of Personal Information Act (No. 4 of 2013)
The POPI Act is a positive initiative by government as it strives to ensure privacy, safety and confidentiality of data subject personal information, that data is processed in a lawful manner and that there is accountability. It ensures that the data subject participates in the processing of personal information. Moreover, it holds the responsible party and the operator accountable with regard to the unlawful processing of personal information. The POPI Act empowers data subjects and affords them the opportunity to take legal action when they believe that their personal information is being processed in an unlawful manner, such as the processing of personal information without data subject consent. However, it is worth mentioning that the POPI Act has its own challenges.
One of the key challenges of the POPI Act is the organisation's readiness to comply with the Act. This is exacerbated by the lack of necessary skills, knowledge and awareness of the Act (Baloyi & Kotze 2017; Jangara & Bezuidenhout 2015). A survey conducted by Baloyi and Kotze (2017) reveals that there is limited familiarity with the POPI Act and its non-compliance implications. Moreover, the study found that most organisations do not have systems available to help with the classification of personal data and that most organisations in South Africa are not ready to implement compliance with the POPI Act (Baloyi & Kotze 2017). There are also concerns regarding loss of direct marketing as a strategy, and as a result this might lead to job losses (Botha, Eloff & Swart 2015).
There are challenges related to cross-border data flow. Jangara and Bezuidenhout (2015) note five emerging challenges: data location, security, privacy, legal compliance and cloud service providers. They argue that transferring data outside countries gives data owners less control over their data. These five emerging challenges require special attention to ensure that trans-border data transfer is conducted in a secure manner and privacy of data is managed through legal compliance controls.
Chapter 9 of the POPI Act makes provisions for cross-border data transfer, when data is to be transferred to other countries provided the data subject gives consent and the laws of the foreign country regarding privacy policies are similar to those prescribed in the POPI Act. Cloud computing raises security and privacy concerns, especially when it involves multiple cloud platforms across various countries with various legal systems that are not in harmony. This raises legal concerns for policymakers and the legal fraternity and necessitates a review of the POPI Act to address areas within the Act where there might be sections that are considered vague, and assess whether the Act should provide further clarity for those conditions relating to cloud computing. This could address some of the legal concerns regarding the storage of personal information on various cloud platforms.
In most instances the cloud computing services providers have data centres in geographically dispersed locations to meet the high demand for computing resources from various tenants. This also assists where there are outages such as hardware failure or a natural disaster. The cloud service provider can seamlessly provide resources in another country. However, due to the fact that the service provider might require client permission to affect such a move, this can affect the speed at which the resources can be provided.
Electronic Communication and Transaction Act (No. 25 of 2002)
According to Schofield and Abrahams (2015), the ECTA of 2002 is a South African legislation with the potential to be applicable to cloud computing; the ECTA of 2002 consists of 14 chapters on the government's regulatory position regarding the use of electronic communication and online transactions. Furthermore, the Act addresses factors such as facilitating electronic transactions, registration of cryptography providers, accreditation of authentication services providers, consumer and personal information protection in relation to electronic communication and transactions, the liability of service providers and cybercrime. Some of these factors are discussed below, starting with the facilitation of electronic transaction.
The provision for cybercrime in the ECTA of 2002 positively aims to address issues of cybercrime. A further positive factor is that there are initiatives in place to address issues of cybercrime awareness, spearheaded by institutions such as the Centre for Scientific and Industrial Research (CSIR), the University of Venda, the University of Pretoria (UP) (ICSA-PumaScope), and the University of Fort Hare (UFH). The South African government in 2012 approved a National Cybersecurity Framework for South Africa, aimed at addressing the challenges and consequences of cybercrime.
It is worth noting that while ECTA legislation may somehow be applicable to cloud computing, there are some noticeable challenges around trans-border jurisdiction and enforcement of judgment (De Villers 2004; Erasmus 2011), and the use of cryptography as a form of data security in the cloud environment (Issi & Efe 2018; Van Dijk & Juels 2010). Schofield and Abrahams (2015) argue that some of the provisions in ECTA are not specific to cloud computing instances, therefore making it difficult to be applicable in law more particularly, especially computing activities in the cloud environment.
Although ECTA have some provisions that are applicable to cloud computing, this regulatory law needs to be aligned with international best practice. The 2018 BSA cloud computing scorecard lowered South Africa's ranking due to factors such as continued internet filtering and censorship and this can become a barrier to the development of a digital economy (Business Software Alliance 2018). Although cloud service providers are partially free from mandatory filtering or censoring, there are still gaps in this regard which require alignment with international best practice.
South African Competition Act (No. 89 of 1998)
The purpose of the South African Competition Act is to promote and sustain competition in South Africa by ensuring that there is inclusive participation and a spread of ownership specifically to previously disadvantaged individuals (Western Cape Government 2013). Additionally, the Act is premised on ensuring the development of the economy and creation of employment opportunities. Moreover, the Act is premised on ensuring that there are competitive services for consumers in the market.
The South African government preferential procurement policies and regulatory laws (such as the Preferential Procurement Policy Framework Act 2000) have been viewed as a potential barrier to competitiveness. The 2018 BSA cloud computing scorecard perceived these regulatory laws to be complex and this could negatively affect the promotion of free trade. This is a challenge because computing services are not able to operate free from laws that discriminate based on the nationality of the vendor, developer or service provider. Although this might be seen as a potential barrier, South Africa's past economic laws were discriminatory and the majority of black South Africans were excluded from participating in the economy. The purpose of these regulatory laws is thus in part to ensure the participation of those who were previously disadvantaged. While this is necessary, it has to be applied in a manner that does not discourage foreign companies from participating in the local economy.
Another challenge that might arise is around cloud computing pricing and determining whether the pricing is fair and competitive. In most cases, cloud service provider (CSP) might sell cloud computing services at a discounted price in order to discourage competitiveness and push competition out of the market. This type of exclusionary practice requires intervention from a policy or regulatory perspective. Competition issues in the cloud computing environment can be complex, and the complexity can evolve quickly as the technology grows. This necessitates intervention to ensure that competitive challenges such as interoperability and data portability, price discrimination, and vertical integration are addressed.
National Integrated information and communication technology Policy White Paper by the Department of Telecommunications and Postal Services
The National Integrated ICT Policy White Paper is an inclusive paper, taking into account some of the emerging technologies such as cloud computing and internet of things (IoT). Even though the White Paper is not detailed in relation to emerging technologies, it indicates that government is aware of such emerging technologies.
Access to the necessary ICT infrastructure is critical for cloud computing services as they are heavily dependent on the availability of the internet, therefore making broadband accessible will help. However, since broadband tends to be expensive in South Africa, the White Paper acknowledges this and proposes measures to ensure that broadband is accessible and is of high quality. It is worth noting that the White Paper in its current form has its own limitation when it comes to issues of cloud computing.
Cloud computing by its very nature can be sophisticated and if left unattended can be a problem for government and policymakers. While policies such as the National Integrated ICT Policy White Paper promise benefits, from a policy and regulatory point of view there is more to be done in relation to cloud computing. Cloud computing services, reliability and liability, vendor lock-in, and other cloud contractual challenges require further attention. From a consumer protection point of view, consumer protection challenges must be mitigated and consumer concerns addressed in regard to the use of data on the cloud, concerns about the possibility of law enforcement access to data on the cloud as well as secondary use of data, and concerns regarding fairness in terms of service, transparency, interoperability and portability.
Implications of lack of cloud computing policy
The lack of policy to address cloud computing challenges can negatively impact on areas such as security and privacy, competition, intellectual property and liability, consumer protection, and cross-border and juridical challenges. Additionally, the study conducted by Scholtz et al. (2016) revealed factors that affect the adoption of cloud computing, specifically in the public sector. Amongst those factors is a lack of approved cloud standards. Also data availability and privacy concerns, cloud multi-tenancy issues and trans-border information flow. Lack of a national cloud computing policy framework, as well as cloud computing adoption guidelines was identified as a challenge for cloud computing adoption (Gillwald & Moyo 2016; Scholtz et al. 2016).
The implication of the lack of a cloud computing policy framework is that such challenges will continue and raise policy and legal uncertainty. Cross-border data transfer in the cloud computing environment contributes to complex juridical legal challenges. From a cloud computing legal perspective, some of the existing regulatory laws require updates and alignment with international standards and best practice, while others require a thorough revision to take into consideration new technological developments (Gillwald & Moyo 2016).
Cybercrime has become a serious issue in South Africa as it is considered to be the country most affected (Davids 2017; IOL 2017; Van Heerden, Von Soms & Mooi 2016). The government has made strides in addressing cybercrime through the introduction of the National Cybersecurity Bill. One of the impediments to fighting cybercrime in South Africa is lack of skills (Griffiths 2016; Sutherland 2017). Cybercrime has an impact on cloud computing as most cloud computing is conducted online. The lack of skills in fighting cybercrime can thus negatively impact on cloud computing adoption and use.
Methodology
In this study it was essential to understand human beliefs, views and experiences regarding the phenomena under study (Al-Saadi 2014). Thus, it was important to understand participants' views regarding the impact of cloud computing on existing South African ICT policies and regulatory frameworks. From an epistemology stance, interpretivism philosophy was employed in the study to acquire more knowledge (Chowdhury 2014; Kaplan & Maxwell 1994) and to understand meaning about the nature of reality (Goldkuhl 2012). The interpretivism stance was found to be most suitable for this study purpose as it helps to focus on fresh, complex and rich descriptions of the phenomenon as it is concretely lived (Goldkuhl 2012); and further facilitates the understanding of people's perceptions towards events that are external to them (Chowdhury 2014; Saunders, Lewis & Thornhill 2012). The study employed a multi-method qualitative research approach to provide an in-depth understanding of the phenomena under study (Creswell 2012; Saunders et al. 2012). Data was collected using multi-method collection which included interviews, questionnaires and document analyses with the qualitative study paradigm in a South African organisation based in the Gauteng province. Triangulation was used in this study as the main technique for improving trustworthiness. This assures the reliability and validity of the study through the use of a variety of methods to collect data on the same topic, which involves different types of samples, as well as methods of data collection. The participants in this study were selected by making use of the purposive sampling technique, where a selection criteria included participants involved in cloud computing, expert knowledge of the POPI Act and other South African ICT legislative frameworks, expert knowledge in ICT formulation process, ICT law, as well as expert knowledge in ICT security. Thus, this study comprised a total of 50 participants from different institutions and various sectors of the economy (such as telecoms, government, advisory, legal and financial). Of those participants, 14 participated in semi-structured interviews and 36 participated in the questionnaire. The data analysis followed the qualitative data analysis, in which a thematic analysis technique (Creswell 2012) was followed to effectively analyse data collected.
Findings and discussions
This section presents the findings of this study by making use of interviews which were the primary source of data collection, supported by secondary sources of data such as questionnaires and literature. The findings presented in this section answers the following question:
To what extent do current information and communication technology policies and legislative frameworks in South Africa relate to the emergence of cloud computing?
This question is intended to ascertain how current ICT policies and regulatory laws in South Africa are perceived to relate to the emergence of cloud computing, and to further establish whether they are regarded or viewed as being comprehensive and adequate to address the emergence and complexities of cloud computing. To address this sub-question, data was collected using questionnaires, interviews, literature review and expert reviews. The next section presents the findings from the interviews.
Interview findings
To understand the perspectives on how current information policies in South Africa relate to the emergence of cloud computing, several questions were asked of participants. They were asked if existing policies are sufficient to address cloud computing challenges. They were also asked about their views regarding the POPI Act in relation to cloud computing, and whether there is sufficient awareness of the Act and its impact on cloud computing.
Firstly, the participants were asked to identify the current policies, regulations and legislative frameworks that relate to cloud computing. The findings suggest that while all participants indicated that there is no existing legislative framework for cloud computing in South Africa, there are some that incorporate cloud computing, such as the ECTA, Cybercrimes and Cybersecurity Bill, South African Competition Act and the POPI Act.
When asked whether they think existing policies and regulatory laws are comprehensive and adequate to address cloud computing developments, complexities and challenges, the following points were made:
'… I really do not think so that policies are sufficient enough… I think lawmakers are playing catch-up instead of actively monitoring trends and trying to develop policies based on those trends… I don't think the laws we have currently are able to secure the client's data if they have to be hosted in the cloud environment …' (Participant 1, Mr, Managing Director)
'… I think no-one has really thought about what happens to this data that is stored in the cloud and who owns it and who controls it, what the cloud would do with it…. I think to that extent no, because there is no-one who has really thought about those issues … so, no, the regulation doesn't really adequately deal with them… on the security side there is legislation in place that deals with cybercrime, which is a real problem in South Africa, but in terms of enforcing those regulations I think we have a really big problem. I do not think either the will or the skills are there to actually enforce the legislation that is currently on the books …' (Participant 10, Ms, Legal and Regulatory Expert)
Of the recent developments, the Department of Telecommunication and Postal Services (2016) developed a policy White Paper the titled National Integrated ICT White Paper. However, the aspect that is not included in the White Paper is the discussion on cloud computing and how these competition factors raised in the White Paper can help mitigate issues of cloud computing competitiveness (such as fair competition, quality, trust and reliability of cloud computing services). An interviewee who was part of the panel that drafted the paper explained that the White Paper is silent on cloud computing and will therefore need to update provisions to include innovations such as cloud computing and the IoT. The following observation was made:
'… from a legislative point of view, definitely there is a requirement to update the provisions … so there is still a gap you can go through the White Paper [National Integrated ICT White Paper] and you will see that there is only one paragraph that talks to issues of cloud because they are so complex and it is a fast-paced environment what you put in law and regulations might not be relevant in 18 months …' (Participant 13, Ms, Chief Director: ICT Policy)
This reveals some of the weaknesses in the process in which ICT policies and regulatory frameworks are formulated in South Africa, as they are perceived to be designed as a wholesale blanket approach. Most participants hold a view that the ICT policy development approach in South Africa is considered to be holistic rather than being specific to a particular subject matter or domain (i.e. cloud computing, IoT).
The argument being put forward is that cloud computing is very broad and having a wholesale policy approach that is not specific to the subject matter might be a limitation in trying to address technology challenges, especially those that negatively impact on public confidence regarding the adoption and use of cloud computing services, as well as competitiveness. This is because, by focusing on a wholesale policy approach or blanket policy approach, policymakers might overlook the need for rigour and extensive analysis on critical issues. This argument is supported by the findings of the study where interviewees noted that the way policymakers formulate ICT policy and regulatory laws is not adequate, as per below observation from one of the experts:
'… the way we handle policies we do not create specific ICT policies, we create IT blanket policies… I do not think our policies are adequate … we need to create future-proof policies as we have seen how dynamic and ever-changing this environment is, especially the cloud space, so we need to have a forward-thinking type of view …' (Participant 4, Mr, Business Development Manager: Cloud and Data Centre Hosting)
Since the ICT policy development approach is considered to be holistic, some of the existing policies and regulatory laws in relation to cloud computing suggest gaps and concerns regarding their applicability to the pressing challenges of cloud computing (such as data security and privacy, interoperability and portability, cross-border data transfer and jurisdictional challenges). Regulatory laws that were found to be too holistic included the ECTA and the South African Competition Act, as well as the National Integrated ICT White Paper. The Competition Act partially aligns with cloud computing challenges that impact on competitiveness such as data interoperability and portability, as well as vertical integration. These factors are critical in ensuring fair competition and avoiding vendor lock-in, thus ensuring that cloud consumers can move from one cloud provider to the other with minimal costs. The National Integrated ICT White Paper is holistic in a manner that includes other factors such as the postal services policy, radio frequency spectrum policy, broadband policy, National Information Society and Development Plan, and the National Cybersecurity Policy Framework.
It was found that there is a perception that most existing policies in South Africa are playing 'catch-up' because technology has made progress and the process of revising these policies is said to be lacking in agility and scalability to cater for the rapid and continuous technology evolution. This was raised as a concern by most participants, in that the technology evolution is progressing at a rapid rate and this prompts lawmakers to act, thus creating policies that only 'catch-up' with technology, instead of proactively monitoring technology trends and responding quickly to policy issues emanating from technology advancement.
'… I think we have been playing catch-up in terms of policies … A lot of policies that cover up have been to cater what is already here on our doorstep… policies such as POPI and ISO standards have all been put through as a blanket approach to a problem … if there is an issue around leaked information, a policy will come through …' (Participant 4, Mr, Business Development Manager: Cloud and Data Centre Hosting)
'… technology has moved faster than legislation that we have … the legislative framework has not moved as fast as it used to be … so it is trying to catch-up where the technology has moved. Cloud is becoming a key enabler for the digital economy … that's why we need that type of vigorous and transparent regulation and policy around cloud… so we need to have a tight policy framework to regulate the industry and also to protect the consumers …' (Participant 5, Mr, Director, Telecoms & IoT)
The recently developed data privacy regulatory Act known as the POPI Act was identified as one of the best-known regulatory laws on cloud computing. Participants were asked about their views regarding the POPI Act and its impact on cloud computing. The findings reveal that there is unanimity amongst participants that the POPI Act has had a profound impact on cloud computing in the sense that it protects consumers' personal information. Furthermore, it enables the protection and privacy of consumer information by ensuring that it is handled and processed in a responsible manner and within the ambit of the law. Below are some of the participants' views regarding the POPI Act in relation to cloud computing:
'… it is a good piece of legislation and it does not impede cloud computing in any way, it protects the privacy and the rights of the consumer … but it does require a little bit of work for any cloud service provider to subscribe to the requirements of POPI … so for me it is not a barrier but an enabler of cloud …' (Participant 5, Mr, Director, Telecoms & IoT)
'… the POPI Act has a profound impact on cloud computing wherever the cloud is … even if it is in South Africa. If you are using a cloud service, you are using a third party … and they have to ensure that all eight conditions of POPI are applied …' (Participant 2, Ms, POPI Act Expert)
Findings reveal that the complexity inherent in complying with the Act is concerning, more specifically for small, medium and micro enterprises (SMMEs), as most of them are not aware of the POPI Act and its compliance requirements. Moreover, the Act becomes even more concerning in terms of compliance when compared to large organisations since SMMEs, unlike large organisations, have limited financial resources to contract consultants to assist with compliance. This suggests the need for compliance to be simplified in order to improve adherence. Another emerging theme is lack of clarity regarding the POPI Act and its impact on cross-border data transfer. There is a view amongst participants that POPI Act compliance might take long as a result of due diligence with cross-border data transfer laws and regulations. Furthermore, the legislation itself is vague as regards cloud computing. Below are some of the participants' views regarding the POPI Act and its challenges:
'… POPI is very complicated to implement … here is section 57 of POPI that I think is going to create a problem in terms of cloud computing if it is going to take place trans-border …' (Participant 2, Ms, POPI Act Expert)
'… I think people that are in this industry (SMEs) know less about POPI … I got to know or find out about the Act because I read about it and not because of the awareness or any marketing that would have been done by the organisation that is in charge of the Act … but I don't think the awareness is adequate … I'm sure that there are people who are transgressing the Act who don't even know that they are transgressing the Act …' (Participant 3, Mr, SME Director)
Although most participants view the POPI Act as an enabler for cloud computing adoption and use, there are several factors that can negatively impact on how organisations comply with the Act. Principal amongst those are the lack of awareness and complexity in complying with the Act. Awareness is necessary, especially from a policy and regulatory perspective, since it informs the general public about the new policies and regulatory laws, how they affect them and what measures and processes need to be followed to comply. Since most policies and regulatory laws are developed to protect the rights of users, it is important that there is an extensive awareness campaign to educate and inform the users about new policies and regulations.
In summary, the interview findings reveal that most existing South African ICT policies are not comprehensive and adequate to address cloud computing developments, complexities and challenges. Moreover, some of the emerging policies are put in place to try and 'catch-up' where technology has already left a footprint. There is a notion that most existing policies are not 'future-proof' and policymakers are not actively involved in analysing digital technology trends to address the policy gaps that might arise. The interview findings reveal that most South African policies and regulatory laws that are put in place are not specific to a particular domain (i.e. cloud computing), but rather are designed in a blanket manner. The findings further reveal that there is a need to formulate ICT policies that are specific to a subject domain, as discussed in the above analysis.
Questionnaire findings
A questionnaire was used to help understand the perspectives on how current information policies in South Africa relate to the emergence of cloud computing. Since most of ICT and legislative Acts were found in the literature review to have an impact on cloud computing, the questionnaire was also used to validate literature review findings. The following questions were asked: Which of the following regulatory Acts have a general impact on cloud computing?
The participants were provided with policy and legislative options to choose from and indicate whether they either agree or disagree that these regulatory Acts have a general impact on cloud computing. The reason why the participants were provided with predefined options is that some of the regulatory Acts were found in the literature review to have an impact on cloud computing and were drawn on to validate literature review findings.
As depicted in Figure 1 below, of all the regulatory laws that were provided to participants to choose from, over 90% agreed that the POPI Act has the greatest impact on cloud computing, followed by the Electronic Communication Act of 2005. There was agreement amongst the participants regarding regulatory policies such as the Standards Act and Copyright Act where over 36% of participants indicated that these regulatory laws have an impact on cloud computing.
Of the participants interviewed, 11% indicated that there are other policies that have an impact on cloud computing such as ISO27001 and the Promotion of Access to Information Act. This confirms that there are participants who are exposed to different policies and the impact of such policies on cloud computing. Even though some policies scored a lower percentage as depicted in Figure 1 above, this confirms that such policies might have little impact on cloud computing.
Figure 1 further indicates that over 90% of participants viewed the POPI Act as a policy that has an impact on cloud computing, meaning that there are conditions in the regulatory Act that might partially apply to cloud computing, specifically regarding the protection of personal information.
Participants were then asked the following questions regarding existing ICT policies and regulatory frameworks in South Africa: Do you think existing ICT policies and regulations in South Africa address issues of cloud computing?
The above question refers to issues such as security, interoperability, cybercrime, and vendor lock-in. Over 50% of the participants indicated that current ICT policies and regulatory laws are not sufficient to address challenges of cloud computing, while 9% agreed that policies are sufficient, as depicted in Figure 2.
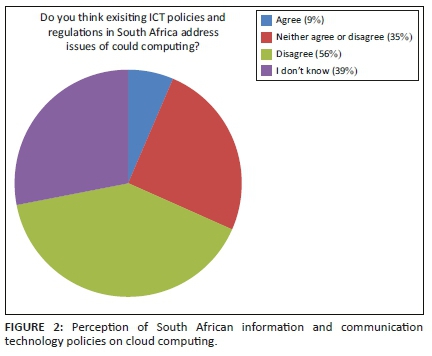
In response, 39% of participants indicated that they do not know whether existing ICT policies are sufficient to address issues of cloud computing. Since cloud computing is still regarded as a new and emerging technology by most people, there might be limited knowledge regarding cloud computing challenges in relation to existing ICT policies.
In summary, the questionnaire findings revealed that there are some regulatory Acts that might have relevance for cloud computing, with the most prominent being the POPI Act, the Electronic Communication Act and the Electronic Communication and Transaction Act. However, the question is whether these policies are sufficient to address challenges related to the cloud. Based on the questionnaire findings, it can be inferred that the policies are not adequate to address emerging challenges of cloud computing. Most ICT policies are old and were enacted some decades past and are not sufficiently aligned with emerging digital technologies. A further argument is that new emerging legislative policies are lagging behind in addressing the gaps where technology has made an impact.
Conclusion
The study findings revealed that there are some existing ICT policies and regulatory laws that have an impact on cloud computing. The Cybercrime and Cybersecurity Bill is more applicable to cloud computing in relation to challenges that negatively impact on the adoption and use of cloud computing services such as security and privacy. However, the findings revealed challenges with the Cybercrime and Cybersecurity Bill, in particular related to lack of skills and political will to enforce the legislation issues of cybercrime, which can negatively impact on public confidence regarding the adoption and use of cloud computing services. The National Integrated Policy White Paper provides a digital transformation agenda to promote an inclusive knowledge society, taking into consideration technological development. The problem with the White Paper is that it is not comprehensive and adequate enough to address cloud computing developments, complexities and challenges. The findings revealed that the paper has a limited focus on cloud computing and will require additional provisions to comprehensively align the policy with emerging challenges of cloud computing. The POPI Act is generally considered to be a good piece of legislation that is perceived to enable cloud computing when implemented correctly, as it helps to secure privacy of personal information. However, there are challenges that might impact on compliance with the Act. One of these challenges is the lack of understanding of how the regulatory Act should be applied. In addition, there is limited awareness and understanding of the regulatory Act. Based on the findings discussed above, it can be concluded that the emergence of cloud computing has exposed the existing ICT policies and regulatory laws as being inadequate to address cloud computing developments, complexities and challenges, especially challenges related to public confidence regarding the use of cloud computing services and cloud competitiveness. This is aggravated by the notion that the approach that is used to develop ICT policies is a holistic approach, rather than having ICT policies that are specific to a particular issue or problem.
Acknowledgements
I wish to thank all the participants, but, due to confidentiality, I cannot mention their names. Thank you for the opportunity you offered to collect data and your willingness to participate.
Competing interests
The authors have declared that no competing interests exist.
Authors' contributions
All authors contributed equally to this work.
Ethical consideration
This article followed all ethical standards for a research article.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abubakar, D.A., 2016, 'Cloud computing adoption by SMEs in Sub-Saharan Africa', PhD thesis, Robert Gordon University, Aberdeen. [ Links ]
Abolfazli, S., Sanaei, Z., Tabassi, A., Rosen, S., Gani, A. & Khan, S.U., 2015, 'Cloud adoption in Malaysia: Trends, opportunities, and challenges', IEEE Cloud Computing 2(1), 60-68. https://doi.org/10.1109/MCC.2015.1 [ Links ]
Alharbi, F., 2017, 'Holistic approach framework for cloud computing strategic decision-making in the Healthcare Sector (HAF-CCS)', Doctoral thesis, Staffordshire University, Stoke-on-Trent. [ Links ]
Al-Saadi, H., 2014, Demystifying Ontology and Epistemology in research methods, viewed 06 March 2015, from https://www.researchgate.net/publication/260244813_Demystifying_Ontology_and_ Epistemology_in_Research_Methods.
Baloyi, N. & Kotźe, P., 2017, 'Are organisations in South Africa ready to comply with personal data protection or privacy legislation and regulations?', in IST-Africa 2017 conference, IEEE, Windhoek, Namibia, 31 May - 02 June 2017.
Botha, J.G., Eloff, M.M. & Swart, I., 2015, 'The effects of the PoPI Act on small and medium enterprises in South Africa', in Proceedings: Information Security for South Africa (ISSA), IEEE, Johannesburg, August 12-13, 2015, pp. 1-8.
Business Software Alliance, 2018, The 2018 BSA global cloud computing scorecard, viewed 23 June 2018, from https://cloudscorecard.bsa.org/2018/pdf/BSA_2018_Global_Cloud_Scorecard.pdf
Chowdhury, M.F., 2014, 'Interpretivism in aiding our understanding of the contemporary social world', Open Journal of Philosophy 4, 432-438. https://doi.org/10.4236/ojpp.2014.43047 [ Links ]
Creswell, J.W., 2012, Educational research: Planning, conducting, and evaluating quantitative and qualitative research, 4th edn., Pearson Education, Boston, MA.
Davids, N., 2017, SA is the leading target in Africa for cyber-crime, warns legal firm, viewed 15 February 2017, from https://www.businesslive.co.za/bd/world/africa/2017-02-13-sa-is-the-leading-target-in-africa-for-cyber-crime-warns-legal-firm/.
Department of Telecommunication and Postal Services, 2016, National integrated ICT policy whitepaper, viewed 14 June 2017, from https://www.dtps.gov.za/images/phocagallery/Popular_Topic_Pictures/National_ Integrated_ICT_Policy_White.pdf.
De Villers, M., 2004, 'Consumer protection under the Electronic Communications and Transactions Act 25 of 2002', Master's dissertation, University of Johannesburg, Johannesburg. [ Links ]
Erasmus, C., 2011, 'Consumer protection in international electronic contracts', Master's dissertation, Northwest University, Potchefstroom. [ Links ]
Gillwald, A. & Moyo, M., 2016, Modernising the public sector through the cloud, viewed 12 August 2017, from https://researchictafrica.net/wp/wp-content/uploads/2017/10/Cloud-Computing-in-the-public-sector-final-25052017_V03.pdf.
Goldkuhl, G., 2012, 'Pragmatism vs interpretivism in qualitative information systems research', European Journal of Information Systems 21(2), 135-146. https://doi.org/10.1057/ejis.2011.54 [ Links ]
Griffiths, J.L., 2016, 'Cybersecurity as an emerging challenge to South African National Security', Master's mini-dissertation, University of Pretoria, Pretoria. [ Links ]
IOL, 2017, SA has third highest number of cybercrime victims in world, viewed 20 October 2017, from https://www.iol.co.za/capetimes/news/sa-has-third-highest-number-of-cybercrime-victims-in-world-11594553.
Issı, H. & Efe, A., 2018, 'Cryptography challenges of cloud computing for e-government services', International Journal of Innovative Engineering Applications 2(1), 4-14. [ Links ]
Jangara, T.B. & Bezuidenhout, H., 2015, 'Addressing emerging risks in transborder cloud computing and the protection of personal information: The role of internal auditors', Southern African Journal of Accountability and Auditing Research 17(1), 11-24. [ Links ]
Kaplan, B. & Maxwell, J.A., 1994, 'Qualitative research methods for evaluating computer information systems', in J.G. Anderson, C.E. Aydin & S.J. Jay (eds.), Evaluation health care information systems: Methods and application, pp. 30-55, Sage, Thousand Oaks, CA.
Kumar, S. & Vajpayee, A., 2016, 'A survey on secure cloud: Security and privacy in cloud computing', American Journal of Systems and Software 4(1), 14-26. [ Links ]
Mahler, T., 2014, First study of legal and regulatory aspects of cloud computing, viewed 15 October 2015, from http://www.coco-cloud.eu/sites/default/files/cococloud/files/content-files/deliverables/Coco_Deliverable%20D2.2_UO_20141031(1of2).pdf.
Mohammed, F. & Ibrahim, O., 2015, 'Drivers of cloud computing adoption for e-government services implementation', International Journal of Distributed Systems and Technologies 6(1), 1-14. https://doi.org/10.4018/ijdst.2015010101 [ Links ]
Muhammed, K., Zaharaddeen, I., Rumana, K. & Turaki, A., 2015, 'Cloud computing adoption in Nigeria: Challenges and benefits', International Journal of Scientific and Research Publications 5(7), 1-7. [ Links ]
Saunders, M.N.K., Lewis, P. & Thornhill, A., 2012, Research methods for business students, 6th edn., Pearson Education, Harlow.
Schofield, A. & Abrahams, L., 2015, Research study on the use of cloud services in the South African government, University of the Witwatersrand, Johannesburg.
Scholtz, B., Govender, J. & Gomez, J., 2016, 'Technical and environmental factors affecting cloud computing adoption in the South African public sector', in International Conference on Information Resources Management (Conf-IRM) proceedings, The International Conference on Information Resources Management (Conf-IRM), Cape Town, May 18-20, 2016.
Sluijs, J., Larouche, P. & Sauter, W., 2012, 'Cloud computing in the EU policy sphere: Interoperability, vertical integration and the internal market', Journal of Intellectual Property, Information Technology and E-Commerce Law 3(2012), 12-32. [ Links ]
Sutherland, E., 2017, 'Governance of cybersecurity - The case of South Africa', The African Journal of Information and Communication (AJIC) 20, 83-112. https://doi.org/10.23962/10539/23574 [ Links ]
Van Dijk, M. & Juels, A., 2010, 'On the impossibility of cryptography alone for privacy preserving cloud computing', in Proceedings of the 5th USENIX conference on hot topics in security, ACM, Berkeley, August 10, 2010.
Van Gorp, N. & Batura, O., 2015, Challenges for competition policy in a digitalised economy, viewed 16 June 2016, from http://www.europarl.europa.eu/RegData/etudes/STUD/2015/542235/IPOL_STU(2015)542235_EN.pdf.
Van Heerden, R., Von Soms, S. & Mooi, R., 2016, 'Classification of cyber attacks in South Africa', in IST-Africa 2016 conference proceedings, IEEE Xplore, Durban, May 11-13, 2016.
Vasiljeva, T., Shaikhullina, S. & Kreslins, K., 2017, 'Cloud computing: Business perspectives, benefits and challenges for small and medium enterprises (case of Latvia)', 16th conference on reliability and statistics in transportation and communication, RelStat'2016, Riga, October 19-22, 2016.
Western Cape Government, 2013, The Competition Act 89 of 1998, viewed 24 December 2014, from https://www.westerncape.gov.za/legislation/competition-act-89-1998.
 Correspondence:
Correspondence:
Mpho Mohlameane
mpho.mohlameane@gmail.com
Received: 22 July 2019
Accepted: 18 Apr. 2020
Published: 11 Aug. 2020
ORIGINAL RESEARCH
The age factor in the use of peer-reviewed electronic journals by Zimbabwean academics
Takawira Machimbidza; Stephen Mutula
Department of Information Studies, School of Social Sciences, College of Humanities, University of KwaZulu-Natal, Pietermaritzburg, South Africa
ABSTRACT
BACKGROUND: The emergence of peer-reviewed electronic journals on the academic scene at the turn of the century was well received by university libraries in Zimbabwe. They established a consortium to facilitate conveyance of the resources to their patrons. Use of electronic journals by academics, however, has remained minimal almost two decades after their introduction. Efforts by librarians to address this challenge are hampered by lack of context-specific information on how age, among other demographic factors, affects adoption and use of electronic journals by academics. Such information is critical in promoting its use.
OBJECTIVES: This study examined age differences in the awareness of peer-reviewed electronic journals by academics in Zimbabwean universities, use of electronic journals and possession of technological skills needed to negotiate the electronic journals environment
METHOD: This study employed a quantitative approach using a survey research design. Data were collected through structured questionnaires administered to a sample of 363 academics from three universities in Zimbabwe. Data were analysed through the Statistical Package for Social Sciences to produce tables.
RESULTS: Younger academics were more aware of electronic journals, however, the older academics accessed more articles. Younger academics possessed higher technological skills than older academics.
CONCLUSION: There are age differences among academics with respect to awareness, use and possession of technological skills that librarians must take into account as they promote adoption and use of electronic journals.
Keywords: academics; peer-reviewed electronic journals; age; awareness; adoption and use; technological skills; Zimbabwean universities.
Introduction
Peer-reviewed electronic journals are vital and indispensable instruments of scholarly information for teaching, learning and research in the contemporary, globalised academic world. The resources have been adopted by university libraries and libraries of other higher and tertiary institutions across the world to support the activities of academics and students (Abinew & Vuda 2013; Machimbidza & Mutula 2017, 2019). The resources are renowned for their depth; timeliness; currency; speed and ease with which they can be accessed; powerful searching capabilities; round-the-clock remote accessibility; facilities for downloading, printing and copying information; a wide range of abstracts and full-text documents from globally renowned academic databases; ability to share downloads with members of research groups; ability to provide multiple access to many researchers at the same time; possibility of inclusion of audio and video content; ability to be adapted to technologies for the visually impaired; advanced functional capabilities such as hyperlinks to other relevant articles; and manipulability like the ability to link, annotate, visualise and integrate tables (Bar-llan, Peritz & Wolman 2003; Dilek-Kayaoglu 2008; Min & Yang 2010; Monopoli et al. 2002; Voorbij & Ongering 2006; Zainab, Huzaimah & Ang 2006). Electronic journals have matured to be considered prerequisites for an efficient and productive academic system (Ani 2013).
Peer-reviewed electronic journals were introduced in Zimbabwean universities in 2003, courtesy of partnerships developed between the Zimbabwe University Libraries Consortium (ZULC) and providers such as the International Network for the Availability of Scientific Publications (INASP), World Health Organization (WHO), Food and Agricultural Organization (FAO), United Nations Environment Programme (UNEP) and Electronic Information for Libraries (EIFL) (Machimbidza & Mutula 2017). Zimbabwe University Libraries Consortium is an association of university libraries in Zimbabwe, which acts as a conduit for the collective subscription of electronic journals and provides a platform for resource sharing for member institutions (Machimbidza & Mutula 2019; ZULC 2018). University librarians in Zimbabwe expected electronic journals to easily gain traction with the academic community owing to their well-established benefits. This expectation has been dampened by the prolonged underutilisation reported in studies by Tsvere, Nyaruwata and Swamy (2013), Madondo, Sithole and Chisita (2017) and Machimbidza and Mutula (2017). Academics in Zimbabwe have been singled out for their failure to provide leadership in the use of electronic journals (Machimbidza & Mutula 2017). In this study, the term 'academics' refers to teaching and research staff in universities who have at least a master's degree.
The consequences of non-use or low usage of electronic journals by academics in Zimbabwe are many. Academics who do not use electronic journals are unlikely to encourage their students to use them. Course outlines and reference materials prepared by such academics would not include electronic journals, thereby perpetuating a culture of indifference towards the electronic resources by the academic community (Tenopir 2003). Academics who do not make much use of electronic journals do not give their students tasks that require them to use these resources. This results in a culture of shallow learning in universities (Khan & Ahmad 2009). Underutilisation of electronic journals by academics could imply that they are teaching with outdated material. The material provided by electronic journals is current and up-to-date (Thanuskodi 2011). Low use of electronic journals by academics negatively affects their own research activities. This ultimately affects the ranking and integrity of universities (Harle 2010). The correlation between academics' productivity and the use of electronic journals is well-founded in literature through studies conducted in multiple geographical contexts globally (Akpojotor 2016; Ellis & Oldman 2005; Jankowska 2004; Kirlidog & Bayir 2007; Nwezeh 2010; Sivathaasan & Velnampy 2013; Tenopir et al. 2008).
Studies that have attempted to understand the problem of underutilisation of peer-reviewed electronic journals by academics in Zimbabwean universities have paid little attention to demographic factors that need to be appreciated to properly promote these resources. Studies have focussed on Internet usage patterns (Tsvere et al. 2013), adoption and use (Madondo et al. 2017), and the conditions that facilitate adoption and use (Machimbidza & Mutula 2017). None of the studies have sought an in-depth understanding of the role of age as a key demographic factor in the adoption and use of peer-reviewed electronic journals by academics in Zimbabwe. This gap in literature starves university libraries in Zimbabwe of the information they need to practice target promotion of electronic journals. It also undermines efforts to craft policies aimed at improving the use of the resources in the country. This situation is undesirable, especially because it comes against the backdrop of increasing subscription costs (Harle 2010; Machimbidza & Mutula 2019; Shahmohammadi 2012). Justifying costs to university administrators is a difficult task in the face of minimal usage. The libraries run the risk of having their electronic journals subscription budgets cut. Understanding all the angles of this problem, including age dynamics, is crucial in improving usage and averting impending budget cuts that will undermine the availability and accessibility of information in Zimbabwean universities.
The need to study demographic factors in general and age in particular as a measure to understand the adoption and use of electronic journals in universities is well established in literature. Zhang, Ye and Liu (2011) argued that research on electronic journals and their use by different demographic groups in academic institutions 'establishes an important foundation for selecting and providing effective library holdings and services'. Such a foundation allows for the understanding of the 'variety of users' demands in order to improve the efficiency and value of the utilisation of electronic journals (Zhang et al. 2011). The operating environment of electronic journals must be tailored according to users' demographics (Voorbij & Ongering 2006). This enables libraries to enhance service quality and customer satisfaction. Research on electronic journals, especially understanding the extent of awareness by age, extent of use by age as reflected in the level of adoption of the resources and the number of articles consulted per week, and skills of different age groups to utilise the resources, is of significant theoretical and practical value (Okiki & Asiru 2011; Tyagi 2011; Waldman 2003). Such a study is made all the more necessary by the contrasting narratives emerging from literature on the effect of age on the adoption and use of peer-reviewed electronic journals (Ani 2013; Tenopir et al. 2008).
Purpose of this study
This study investigated the effect of age in the adoption and use of peer-reviewed electronic journals by academics in selected Zimbabwean universities.
Research questions
The research questions (RQ) of this study were as follows:
-
RQ1: What age differences exist in the awareness of peer-reviewed electronic journals by academics in Zimbabwean universities?
-
RQ2: To what extent is the use of peer-reviewed electronic journals by academics in Zimbabwean universities affected by age?
-
RQ3: Are there any age differences in the possession of technological skills needed to negotiate the electronic journals environment?
Literature review
Several researchers have located the debate about age differences in the adoption and use of peer-reviewed electronic journals within the broader context of age differences in the use of Information Communication Technologies (ICTs), in general, and computers, in particular. Early in the life of electronic journals, Rolinson, Meadows and Smith (1995:135) pointed out that 'it has been part of computer mythology that younger people are happier using computers than older people'. Younger people were more likely to use electronic journals, as the resources are accessed through computers and, more recently, smartphones and tablets. Waldman (2003) studied freshmen students at Baruch College, City University of New York, and found that age was a variable that correlates with comfort with computers and the use of electronic resources. Younger generations have been brought up with computers, whereas older generations may not have had as much exposure, resulting in increased computer anxiety. Tenopir (2003) found in a study at the University of Tennessee, Knoxville, the United States, that younger users were more enthusiastic adopters of digital resources than the older users. Kinengyere (2007) conducted a study in academic and research institutions in Uganda and concluded that the older generation of researchers uses ICTs and e-resources less because most of them have a low level of information technology (IT) literacy. Gamage and Halpin (2007) surveyed the use of ICTs in Sri Lanka and found that most of the users were youths and adults younger than 35 years. Park (2010) opined that younger people learn about technology more easily than older ones. Tyagi (2011) found in a study in India that the ability to use e-resources efficiently depends on basic computer skills, knowledge of what is available and how to use it, and the ability to define a research problem. However, they found that age has an influence on these issues, with younger users displaying more competencies.
Turning specifically to the use of electronic journals, the trend mostly follows that of the use of ICTs and computers. Bar-llan and Fink (2005) concluded after extensive research in Israel that 'increased age is inversely related to the use of electronic journals'. Tenopir (2003) after an analysis of several user studies noted that younger users use electronic journals more frequently than the older users. Older scholars believed that electronic journals decreased the quality and rigour of research. They also tended to complain more of unfriendly interfaces than the younger users. In a study that spanned institutions in east and southern Africa, Harle (2010) postulated that age does affect the adoption and use of electronic journals. The younger academics showed more enthusiasm when using the resources. Older academics felt more comfortable with print. Gargiulo et al. (2003) surveyed academics in 25 Italian institutions and discovered that a large percentage of the users of electronic journals fell in the 31-40 age range with 30.5% of usage. Around 26.1% of academics younger than 30 years and 25.4% of those in the 41-50 age group used electronic journals. Those aged over 50 years were the lowest at 18.1%. Bar-llan et al. (2003) conducted studies at several Israeli universities and found that academics in their 30s and 40s used electronic journals more frequently than those older than 50 years. For example, 75.4% of academics in their 30s used electronic journals, as did 68% of those in their 40s, while only 4.8% of those older than 50 years used these resources.
The survey by Sivathaasan, Achchuthan and Kajananthan (2013) on demographic variables and the usage of electronic journals among academics in Sri Lanka revealed that there were significant mean differences among age groups. University lecturers younger than 35 years had the highest mean usage, followed by those between 35 and 45 years, while lecturers between the age of 45 and 55 years accounted for the lowest usage. Findings from the one-way ANOVA (t test) revealed that usage differed significantly by age group. This finding agrees with that of Monopoli et al. (2002) who found in an online survey of e-journal usage by academics of University of Patras, Greece, that the resources were more frequently used by end-users who were 35 years and younger. Borrego et al. (2007) conducted a study at the universities belonging to the consortium of Catalonian university libraries in Spain and confirmed that age is an explanatory factor in the use of electronic journals. Use was more pronounced in the younger ages. In their study of the use of electronic journals in three countries, Finland, Australia and the United States, Tenopir et al. (2008) found that there was more use of electronic resources by the younger academics than the older ones in the overall results in Australia and the United States. King et al. (2009) studied information-seeking behaviour in US universities and reported that older academic staff were more likely to access and use print than electronic resources in their research; electronic journals were less used among the older academic staff in the universities. Deng (2010) investigated the extent of use of electronic resources in an Australian university among academic staff and students. Results showed that respondents younger than 29 years were the major users of electronic resources (52.4%), followed by those within the range of 30-39 years (21.8%), 40-49 years (12.8%), 50-59 years (11.1%) and those older than 60 years (2%).
Nigeria has more than a fair share of studies addressing the effect of age on the use of electronic journals. Amkpa (2007) conducted a study at the University of Maiduguri and found a significant age difference in the use of computer and electronic journals among undergraduate students. Younger students were more comfortable with technology. Alao and Folorunsho (2008) conducted a study on the use of Internet cybercafé and associated resources in Ilorin and found that the major users were people aged 21-30 years. Okiki and Asiru (2011) conducted a study to determine the factors influencing the use of electronic information sources by postgraduate students in Nigeria. They found significant age differences in the computer task, as measured by older adults, making few correct decisions and taking longer time to make their decisions than younger adults. Quadri (2013) studied the influence of demographic factors on the use of online library resources by undergraduate students in two private universities in Ogun State, Nigeria: Babcock University and Redeemer's University. Results showed that younger users relied on electronic resources more heavily and rated themselves more adept at using them than the older ones. There was a significant relationship between age and the use of electronic resources. Ani (2013) studied two Nigerian universities, University of Ibadan and University of Calabar, and found no significant influence of age on accessibility and utilisation of electronic resources at the University of Ibadan although descriptive statistics still showed that younger respondents used electronic journals more than the older ones. This study found a significant difference by age at the University of Calabar. Further analysis revealed that respondents younger than 40 years significantly accessed and used e-resources more than those aged 60 years and above. Similar results were obtained between respondents aged 40-59 years and those aged 60 years and above.
While majority studies show age differences in the use of peer-reviewed electronic journals, there are few studies that are of the contrary view. Rogers (2001) conducted a study at the Ohio State University and revealed that there was little or no correlation between age and frequency of use. Bar-llan and Fink (2005) studied users at Hebrew University in Jerusalem, Israel, and concluded that more than 80% of the respondents frequently used and preferred an electronic format, irrespective of age. Kurata et al. (2009) conducted a study among Japanese medical researchers and found no significant differences relating to article usage patterns by age groups. Nikkar and Mooghali (2010) conducted a study at Payam-e-Noor University, Iran, and concluded that aged faculty, with more experience, had a higher tendency of electronic journal usage. Zhang et al. (2011) argued that while many studies have shown an inverse relationship between e-journal usage and age, all ages have switched to the use of electronic journals such that impact of age as a usage determinant has dwindled.
Theoretical framework
The impact of age on the adoption and use of peer-reviewed electronic journals evidenced in most of the literature reviewed above is not without theoretical backing. One of the greatest theories to ever emerge on the prediction of user behaviour in the sphere of adoption and use of technology is the Unified Theory of Acceptance and Use of Technology (UTAUT) (Venkatesh et al. 2003). The potency of the theory is recognised internationally not least because it is an amalgamation and synthesis of eight established technology adoption models: Theory of Reasoned Action (TRA), Theory of Planned Behaviour (TPB), Technology Acceptance Model (TAM), Diffusion of Innovation (DOI), Social Cognitive Theory (SCT), Motivational Model (MM), Model of Personal Computer Utilisation (MPCU) and Combined Theory of Planned Behaviour/Technology Acceptance Model (TPB/TAM).
The theory hypothesises that age is one of the moderators that have an effect on the four constructs of the theory: performance expectancy, effort expectancy, social influence and facilitating conditions. Age affects how an individual believes that using the system will enhance job performance (performance expectancy). Age has an effect on the degree of ease associated with the use of the system (effort expectancy). The theory further holds that age affects the degree to which an individual perceives that important others believe he or she should use the new system (social influence). The theory also holds that age affects the degree to which an individual believes that organisational and technical structure exists to support his or her use of the system (facilitating conditions). A summation of these four effects determines how people of different ages adopt and use a given technology, in this case peer-reviewed electronic journals. The UTAUT is diagrammatically represented in Figure 1.
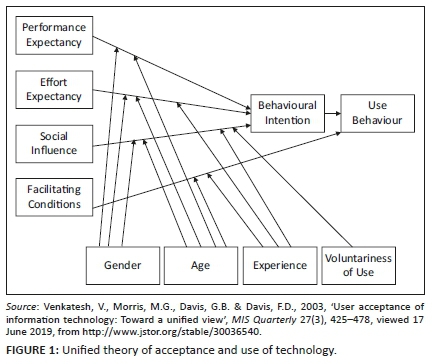
Research methods and design
This study employed a quantitative approach using a survey research design. Data were collected through structured questionnaires administered to a sample of 363 academics from three universities in Zimbabwe: Bindura University of Science Education (BUSE), National University of Science and Technology (NUST) and Midlands State University (MSU). Apart from the University of Zimbabwe (UZ), which declined to participate in this study, the three are the biggest in terms of the number of academics and students. They are all state universities. This is an important quality in this study, given that state universities are the founding members of ZULC. They have been offering peer-reviewed electronic journals for some time. The three universities were also suitable because they offer a variety of disciplines, a feature which was critical in preventing discipline bias in the results of this study.
The sample size for academics was determined through a sampling framework developed by Bartllett, Kotrlik and Higgins (2001). This framework, which assumes a margin of error of 0.05 or 5%, dictates that for a population of 800, the sample size should be 363. The total population of academics in the three universities is 794. This figure was rounded up to 800 so that it fits within the sampling framework. As the respondents came from different universities, the number targeted at each university was decided upon on a proportional basis as follows: the number of academics at each university divided by the total number of academics in the three universities multiplied by the sample size. This produced sample sizes for the three universities as shown in Table 1.
To ensure reliability and validity of the instrument used to collect data in this study, the researchers adapted questionnaires that were successfully used to investigate the adoption and use of electronic resources in several universities in Africa. The first set of questionnaires was developed by Megersa and Mammo (2008) and used to evaluate the use of electronic journals in nine institutions of higher learning in Ethiopia. The second set was developed by Manda (2008) and used to evaluate the use of electronic journals in 23 research and academic institutions in Tanzania. These questionnaires were consistent and valid. Data were analysed through the Statistical Package for Social Sciences (SPSS) to produce tables. Statistical Package for Social Sciences is recognised as a suitable package for statistical representation of information (Franklin 2013).
Ethical consideration
Ethical clearance was sought from the University of KwaZulu-Natal's Humanities and Social Sciences Research Ethics Committee. Full approval was granted (protocol reference number HSS/0201/012D). Clearance to conduct studies in the participating universities was sought from their registrars, and permission was granted. Study participants were shown the permission letters, including a letter explaining the purpose of this study. They also signed the informed consent form before participation.
Results and discussion
Response rate
A total of 212 questionnaires were completed and returned from the 363 that were distributed. This gives a response rate of 58.4%, which was considered adequate for the purposes of this study. The age distribution of the respondents is shown in Table 2.
Academics in the 31-40 years age range made up the largest number of respondents at 44.3%, whereas those of 61 years and above constituted the least at 1%.
Age differences in the awareness of peer-reviewed electronic journals
Results reveal that the majority of academics were aware of the existence of peer-reviewed electronic journals in their institutions. Of the 212 academics who participated in this study, 204 (96.2%) indicated that they were aware of the existence of electronic journals, whereas 8 (3.8%) indicated that they were not aware. Although descriptive statistics show slight variations in awareness by age as shown in Table 3, all ages generally have a high awareness of peer-reviewed electronic journals.
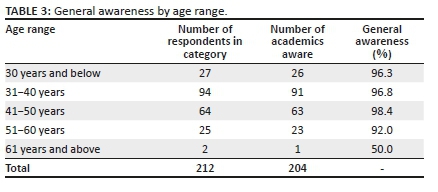
In all the age ranges, except the 61 years and above age group, more than 90% of their academics were aware of the existence of electronic journals. The percentage awareness of the 61 years and above group could have been negatively affected by the fact that only two of them responded to this study.
The high levels of awareness of peer-reviewed electronic journals across all ages established by this study are contrary to the findings of Tenopir (2003), Nwagwu, Adekannibi and Bello (2009) and Harle (2010), who found poor awareness in the institutions they studied. The results are, however, consistent with the views of Tenopir (2003), who asserted that awareness grows with time such that its effect on use decreases the longer the resources are offered. This is confirmed by studies by Tyagi (2011) and Ani (2013), who found high levels of awareness in the institutions they studied.
This study also went further to determine the depth or extent of awareness. This question only applied to the 204 academics who had indicated awareness of electronic journals. The measures of depth or extent of awareness were determined by the number of electronic databases (electronic databases house electronic journals) and the number of electronic journals academics were aware of.
Only 84 (41.2%) knew between five and 10 databases. The rest (120 or 58.8%) knew between one and four. None indicated knowing more than 10 databases. This is against the backdrop of more than 200 databases that Zimbabwean universities have access to. Of the 84 who knew between five and 10 databases, the 30 years and below age group had the highest ratio (18 of 26 or 69.2%), followed by the 31-40 years group with 41 of 91 (45.1%), followed by the 41-50 age group with 22 of 63 (34.9%), followed by the 51-60 age group with three of 23 (13%). The one academic in the 61 and above age group knew less than five databases.
Only 45 of the 204 (22.1%) academics knew between five and 10 specific electronic journals. The rest (159 or 77.9%) knew between one and four. None indicated knowing more than 10 specific electronic journals. There are thousands of electronic journals housed in the more than 200 databases that Zimbabwean universities have access to. This shows that virtually all age groups had poor knowledge of specific journals. However, age trends generally followed that of databases cited above, where awareness decreased as age increased. Studies by Amkpa (2007), King et al. (2009) and Deng (2010) confirmed that academics have unsatisfactory in-depth knowledge of electronic journals at their disposal. The same studies also found that younger users displayed more in-depth knowledge than the older academics.
Extent to which the use of peer-reviewed electronic journals by academics is affected by age
Of the 212 academics who responded to this study, 193 (91%) indicated that they had adopted the use of electronic journals. Nineteen academics (9%) did not use electronic journals at all. The figure of non-users includes the eight (3.8%) who reported not being aware of the resources. Twenty-six of 27 respondents (96.3%) in the 30 years and below age category used the resources, as did 88 of 94 respondents (93.6%) in the 31-40 years age group, 58 of 64 respondents (90.6%) in the 41-50 age group, 20 of 25 respondents (80%) in the 51-60 years age group and one of two (50%) in the 61 years and above age category. The pattern that emerges from these statistics is that the percentage number of users per category decreases as the age ranges increase.
The results on adoption of electronic journals are in tandem with the expectations of the UTAUT theory that underpins this study. The theory hypothesises that age is a factor in the adoption and use of technology (Venkatesh et al. 2003). While this study did not go as far as measuring statistical significance, the descriptive results show a pattern where the level of adoption decreases with an increase in age. These results were also confirmed by researchers such as Waldman (2003), Tenopir (2003), Kinengyere (2007), Gamage and Halpin (2007) and Park (2010).
This study also considered the number of articles consulted per week by each of the age categories from the 193 academics who reported using electronic journals. Use was classified into three categories: low (one to 10 articles per week), average (11-20 articles per week) and high (21 articles and above per week). Table 4 shows the age differences in usage of electronic journals by academics.
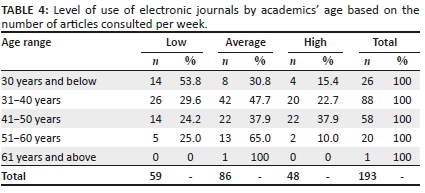
While results cited earlier on the number of academics who have adopted the use of electronic journals revealed a pattern where the number of users decreased as the ages increased, Table 4 suggests that younger academics were actually low users of the resources. The statistics suggest that a number of young academics use electronic journals; however, they use them sparingly. Fewer academics in the older ages use electronic journals, but those who use do so in a significant way. An analysis of Table 4 reveals that 53.8% of academics in the 30 years and below age category are low users, as are 29.6% of those aged 31-40 years, 24.2% of academics in the 41-50 years age category and 25% of those aged 51-60 years, respectively. The age group with the highest number of high users is the 41-50 years category at 37.9%, followed by 31-40 age group (22.7%), 30 years and below age group (15.4%) and 51-60 years age group (10%). The lone user in the 60 years and above category is an average user. Most academics in the 31-40 and 51-60 age groups fall in the average users' category.
Contrary to the findings of this study, past research has found that younger academics use electronic journals more heavily, accessing more articles than older academics (Borrego et al. 2007; King et al. 2009; Quadri 2013; Tenopir et al. 2008). Another school of thought points to neutrality in usage by age. Kurata et al. (2009) and Zhang et al. (2011) argued that given the time that has passed since the introduction of electronic journals, the impact of age as a usage determinant has dwindled. The findings of this study are in line with a third view that holds that the older academics use electronic journals more heavily, accessing more articles than the younger academics. Nikkar and Mooghali (2010) conducted a study in Iran and found that the more experienced and publishing-oriented older academics were heavier users of electronic journals.
Age differences in the possession of technological skills needed to negotiate the electronic journals environment
The third RQ sought to establish if there were age differences among academics in Zimbabwean universities in the possession of technological skills needed to negotiate the electronic journals environment. Academics' responses are shown in Table 5.
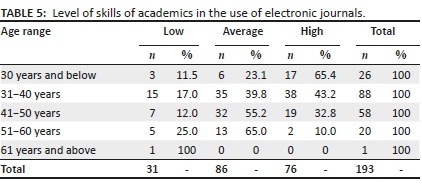
The results provided in Table 5 show that most academics perceived that they had low to average skills. Of the 193 users, 31 indicated low skills and 86 indicated average skills. This means that 60.6% of academics possess low to average skills, with only 39.4% (76) reporting high skills. Results also show that the younger the age the higher the skills. About 65.4% of academics in the 30 years and below category reported high skills, as did 43.2% of academics in the 31-40 years age group, 32.8% of academics in the 41-50 years age group and 10% of those in the 51-60 years age group, respectively. Many of the academics older than 30 years reported average skills. There are also a sizeable number of academics aged over 30 years who demonstrated low skills. Results of this study are consistent with the running theme in literature that younger users possess higher skills in technology use than the older academics. The UTAUT theory asserts that age influences the 'effort expectancy' of the user (Venkatesh et al. 2003). Researchers such as Waldman (2003), Tenopir (2003), Kinengyere (2007), Park (2010), Harle (2010) and Tyagi (2011) have all pointed to younger users having more technological skills than the older users.
Conclusion
The majority of academics across all age groups were aware of the existence of peer-reviewed electronic journals in their institutions. The academics, however, knew very few databases and specific electronic journals. Academics aged 30 years and below knew more databases and journals than their older counterparts. This suggests that while university libraries in Zimbabwe still need to inculcate in-depth awareness of the resources to increase usage, they have to be sensitive to age differences in their efforts. Many of the academics in Zimbabwe have adopted the use of electronic journals; however, there remain differences in the adoption rate by age. The rate of adoption decreases as age increases. This gives a signal to librarians to work more to assist the older academics in their quest to improve usage. This study also reveals that having a higher adoption rate does not necessarily mean more active usage of the resources. The older generation accessed more articles per week than the younger generation of academics in spite the latter having higher adoption rates. Librarians have to work hard to get the younger academics to use the resources to their full potential. This study shows that the majority of academics have low to average technological skills. However, the younger generation of academics possesses higher skills than the older academics. This information is useful for librarians, as they organise training and retraining sessions for academics to increase their confidence in negotiating the electronic journals environment. Overall, this study concludes that there are specific age-related differences in terms on in-depth awareness of electronic journals, usage and possession of technological skills that librarians have to take into account in their provision of these resources.
Acknowledgements
The authors express their gratitude to the National University of Science and Technology, Zimbabwe, for awarding a research grant for data collection.
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
T.M. carried out the research as part of a broader PhD study. S.M. supervised the research.
Funding information
The National University of Science and Technology, Zimbabwe, awarded a research grant for data collection.
Data availability statement
Statistical Package for Social Sciences data are available on request.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abinew, A.A. & Vuda, S., 2013, 'A case study of acceptance and use of electronic library services in universities based on SO-UTAUT model', International Journal of Innovative Research in Computer and Communication Engineering 1(4), 903-910, viewed 25 May 2019, from http://ijircce.com/upload/2013/june/17_A%20Case%20Study.pdf. [ Links ]
Akpojotor, L.O., 2016, 'Awareness and usage of electronic information resources among postgraduate students of Library and Information Science in southern Nigeria', Library Philosophy and Practice 1-23, viewed 21 May 2019, from https://digitalcommons.unl.edu/libphilprac/1408/. [ Links ]
Alao, I.A. & Folorunsho, A.L., 2008, 'The use of cybercafes in Ilorin, Nigeria', The Electronic Library 26(2), 238-248, viewed 11 May 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640470810864127. [ Links ]
Amkpa, S.A., 2007, 'Gender and age differences in computer use and attitudes among students of University of Maiduguri, Nigeria', The Information Technologist 4(1), 60-67, viewed 11 May 2019, from https://www.ajol.info/index.php/ict/article/view/31975. [ Links ]
Ani, O.E., 2013, 'Accessibility and utilisation of electronic information resources for research and its effect on productivity of academic staff in selected Nigerian universities between 2005 and 2012', PhD thesis, Department of Information Science, University of South Africa, Pretoria. [ Links ]
Bar-llan, J. & Fink, N., 2005, 'Preference for electronic format of scientific journals: A case study of the science library users at the Hebrew University', Library & Information Science Research 27, 363-376, viewed 14 April 2019, from https://reader.elsevier.com/reader/sd/pii/S0740818805000368?token=424B35D5F9C9628116571 126FBE76DB6579B11CE6AF5A04B522229FACD13D3F013D89255EE3D3F6E52B5C2C4BF302F64. [ Links ]
Bar-llan, J., Peritz, B.C. & Wolman, Y., 2003, 'A survey on the use of electronic databases and electronic journals accessed through the web by the academic staff of Israeli Universities', Journal of Academic Librarianship 29(6), 346-361, viewed 10 April 2019, from https://www.sciencedirect.com/science/article/pii/S0099133303000909. [ Links ]
Bartllett, J.E., Kotrik, J.W. & Higgins, C.C., 2001, 'Organisational research: Determining appropriate sample size in survey research', Information Technology, Learning, and Performance Journal 19(1), 43-50, viewed 14 May 2019, from https://www.opalco.com/wp-content/uploads/2014/10/Reading-Sample-Size1.pdf. [ Links ]
Borrego, A., Anglada, L., Barrios, M. & Comellas, N., 2007, 'Use and users of electronic journals at Catalan universities: The results of a survey', The Journal of Academic Librarianship 33(1), 67-75, viewed 09 April 2019, from https://reader.elsevier.com/reader/sd/pii/S0099133306001613?token=E7B415B48E5F3ECA9B 62DC7ADC6B3172E764089179C13F45CBA60618060E2B07E775802A4724B2568AF6D4D06F211830. [ Links ]
Deng, H., 2010, 'Emerging patterns and trends in utilising electronic resources in a higher education environment: An empirical analysis', New Library World 111(3/4), 87-103, viewed 15 May 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/03074801011027600. [ Links ]
Dilek-Kayaoglu, H., 2008, 'Use of electronic journals by faculty at Istanbul University, Turkey: The results of a survey', Journal of Academic Librarianship 34(3), 239-247, viewed 19 May 2019, from https://www.sciencedirect.com/science/article/pii/S0099133308000396. [ Links ]
Ellis, D. & Oldman, H., 2005, 'The English Literature researcher in the age of the Internet', Journal of Information Science 31(1), 29-36, viewed 14 May 2019, from https://journals.sagepub.com/doi/pdf/10.1177/0165551505049256. [ Links ]
Franklin, M.I., 2013, Understanding research: Coping with quantitative-qualitative divide, Routledge Publishers, London.
Gamage, P. & Halpin, E.F., 2007, 'E-Sri Lanka: Bridging the digital divide', The Electronic Library 25(6), 693-710, viewed 17 May 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640470710837128. [ Links ]
Gargiulo, P., Conti, C., Contino, U., Farinelli, P. & Marquardt, L., 2003, 'Digital libraries and users: An Italian experience. Changes in academic users' attitudes, perceptions and usage of study and research tools in a hybrid context', viewed 07 April 2019, from https://www.academia.edu/721630/Digital_libraries_and_users_an_Italian_experience._Changes _in_academic_users_attitudes_perceptions_and_usage_of_study_and_research-Tools_in_a_hybrid_context.
Harle, J., 2010, Growing knowledge: Access to research in east and southern African universities, The Association of Commonwealth Universities, viewed 17 March 2019, from https://www.acu.ac.uk/focus-areas/arcadia-growing-knowledge.
Jankowska, M.A., 2004, 'Identifying university professors' information needs in the challenging environment of information and communication technologies', The Journal of Academic Librarianship 30(1), 51-66, viewed 12 April 2019, from https://www.sciencedirect.com/science/article/pii/S009913330300140X. [ Links ]
Khan, A.M. & Ahmad, N., 2009, 'Use of e-journals by research scholars at Aligarh Muslim University and Banaras Hindu University', The Electronic Library 27(4), 708-717, viewed 14 April 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640470910979642. [ Links ]
Kinengyere, A.A., 2007, 'The effect of information literacy on the utilisation of electronic information resources in selected academic and research institutions in Uganda', The Electronic Library 25(3), 328-341, viewed 25 May 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640470710754832. [ Links ]
King, D.W., Tenopir, C., Choemprayong, S. & Wu, L., 2009, 'Scholarly journal information-seeking and reading patterns of faculty at five US universities', Learned Publishing 22(2), 126-144, viewed 06 March 2019, from https://onlinelibrary.wiley.com/doi/epdf/10.1087/2009208. [ Links ]
Kirlidog, M. & Bayir, D., 2007, 'The effects of electronic access to scientific literature in the Consortium of Turksih University libraries', The Electronic Library 25(1), 102-113, viewed 05 May 2019, from https://www.emerald.com/insight/content/doi/10.1108/02640470710729155/full/html?fullSc=1&mbSc=1. [ Links ]
Kurata, K., Mine, S., Morioka, T., Sakai, Y., Kato, S. & Ueda, S., 2009, 'Reading and information seeking behavior of Japanese medical researchers in the era of the electronic journal and open access', Library and Information Science 61, 59-90, viewed 17 May 2019, from https://keio.pure.elsevier.com/ja/publications/reading-and-information-seeking-behavior-of-japanese-medical-rese. [ Links ]
Machimbidza, T. & Mutula, S., 2017, 'Factors influencing the behaviour of academics towards peer-reviewed electronic journals in Zimbabwean state universities', South African Journal of Libraries and Information Science 83(2), 42-51, viewed 27 May 2019, from http://sajlis.journals.ac.za/pub/article/view/1688/1481. [ Links ]
Machimbidza, T. & Mutula, S., 2019, 'Exploring experiences of librarians in Zimbabwean state universities with the consortium model of subscribing to electronic journals', Information Development 1-15, viewed 29 May 2019, from https://journals.sagepub.com/doi/abs/10.1177/0266666919834055. [ Links ]
Madondo, T., Sithole, N. & Chisita, C.T., 2017, 'Use of electronic information resources by undergraduate students in the Faculty of Management and Administration at Africa University, Mutare, Zimbabwe', Asian Research Journal of Arts and Social Sciences 2(2), 1-12, viewed 23 March 2019, from http://www.journalrepository.org/media/journals/ARJASS_45/2017/Feb/Sithole222016ARJASS29633.pdf. [ Links ]
Manda, P.A., 2008, 'Access to electronic library resources and services in academic and research institutions in Tanzania', in D. Rosenberg (ed.), Evaluating electronic resource programmes and provision: INASP research and education case studies no. 3, pp. 33-51, INASP, Oxford.
Megersa, A. & Mammo, W., 2008, 'Evaluation of the use of PERI resources in academic institutions in Ethiopia', in D. Rosenberg (ed.), Evaluating electronic resource programmes and provision: INASP research and education case studies no. 3, pp. 63-78, International Network for the Availability of Scientific Publications (INASP), Oxford.
Min, S. & Yang, Y., 2010, 'E-resources services and user surveys in Tsinghua University Library', Program: Electronic Library and Information Systems 44(4), 314-327, viewed 26 May 2019, from https://www.emerald.com/insight/content/doi/10.1108/00330331011083211/full/html. [ Links ]
Monopoli, M., Nicholas, D., Georgiou, P. & Korfitai, M., 2002, 'A user-oriented evaluation of digital libraries: Case study of electronic journals service of the library and information service of the University of Patras, Greece', ASLIB Proceedings 54(2), 103-117, viewed 09 April 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/00012530210435239. [ Links ]
Nikkar, M. & Mooghali, A.R., 2010, 'Investigating the electronic journals' status in comparison with printed journals among the faculty members of Payam-e-Noor University: A study', International Journal of Information Science and Management 8(1), 83-105, viewed 15 June 2019, from http://ijism.ricest.ac.ir/index.php/ijism/article/viewFile/33/41. [ Links ]
Nwagwu, E.W., Adekannbi, J. & Bello, O., 2009, 'Factors influencing use of the Internet: A questionnaire survey of the students of University of Ibadan, Nigeria', The Electronic Library 27(4), 718-734, viewed 13 May 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640470910979651. [ Links ]
Nwezeh, C.M., 2010, 'The impact of Internet use on teaching, learning and research activities in Nigerian universities: A case study of Obafemi Awolowo University', The Electronic Library 28(5), 688-701, viewed 11 May 2019, from https://www.emerald.com/insight/content/doi/10.1108/02640471011081960/full/pdf?title=the-impact-of-internet-use-on-teaching-learning-and-research-activities-in-nigerian-universities-a-case-study-of-obafemi-awolowo-university. [ Links ]
Okiki, O.C. & Asiru, S.M., 2011, 'Use of electronic information sources by postgraduate students in Nigeria: Influencing factors', Library Philosophy and Practice 4-6, viewed 20 February 2019, from https://digitalcommons.unl.edu/libphilprac/500/. [ Links ]
Park, J., 2010, 'Differences among university students and faculties in social networking site perception and use: Implications for academic library services', The Electronic Library 28(3), 417-431, viewed 12 June 2019, from https://www.emeraldinsight.com/doi/pdfplus/10.1108/02640471011051990. [ Links ]
Quadri, G.O., 2013, 'Influence of demographic factors on use of online library resources by undergraduate students in two private Nigerian university libraries', Library Philosophy and Practice 1-14, viewed 28 May 2019, from https://digitalcommons.unl.edu/libphilprac/976/. [ Links ]
Rogers, S.A., 2001, 'Electronic journal usage at Ohio State University', College and Research Libraries 62(1), 25-34, viewed 18 May 2019, from https://crl.acrl.org/index.php/crl/article/view/15418/16864. [ Links ]
Rolinson, T., Meadows, A.J. & Smith, H., 1995, 'Use of information technology by biological researchers', Journal of Information Science 21(2), 133-139. https://doi.org/10.1177%2F016555159502100207 [ Links ]
Shahmohammadi, N., 2012, 'Online electronic journals use among university academic faculty members of Islamic Azad University, Karaj Branch', Asian Journal of Natural and Applied Sciences 1(1), 26-32, viewed 28 March 2019, from http://www.ajsc.leena-luna.co.jp/AJSCPDFs/Vol.1(1)/AJSC2012(1.1-03).pdf. [ Links ]
Sivathaasan, N., Achchuthan, S. & Kajananthan, R., 2013, 'Demographic variables of university teachers and usage of electronic information resources: A case in Sri Lanka', International Journal of Business and Management 8(19), 90-98, viewed 10 May 2019, from http://www.ccsenet.org/journal/index.php/ijbm/article/view/28807/18021. [ Links ]
Sivathaasan, N. & Velnampy, T., 2013, 'Use of electronic information resources and academic performance of university teachers: A case study', European Journal of Business and Management 5(14), 46-52, viewed 10 May 2019, from https://www.researchgate.net/profile/Thirunavukkarasu_Velnampy/publication/253233550_ Use_of_Electronic_Information_Resources_and_Academic_Performance_of_University-Teachers_A_case_study/links/0deec51f6355cbf55b000000/Use-of-Electronic -Information-Resources-and-Academic-Performance-of-University-Teachers-A-case-study.pdf. [ Links ]
Tenopir, C., 2003, 'Use and users of electronic library resources: An overview and analysis of recent research studies', Council on Library and Information Resources, viewed 10 February 2019, from http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.120.3442&rep=rep1&type=pdf.
Tenopir, C., Wilson, C.S., Vekkari, P., Talja, S. & King, D.W., 2008, 'Scholarly e-reading patterns in Australia, Finland, and the United States: A cross country comparison', in World Library and Information Congress: 74th IFLA General Conference and Council, Quebec, Canada, August 10-14, pp. 1-16, viewed 13 April 2019, from http://origin-archive.ifla.org/IV/ifla74/papers/160-Tenopir_Wilson_Vakkari-Talja_King-en.pdf.
Thanuskodi, S., 2011, 'User awareness and use of e-journals among education faculty members in Chennai: A survey', International Research: Journal of Library and Information Science 1(1), 1-13, viewed 18 March 2019, from http://irjlis.com/wp-content/uploads/2011/11/IR006.pdf. [ Links ]
Tsvere, M., Nyaruwata, T.L. & Swamy, M., 2013, 'Internet usage by university academics: Implications for the 21st century teaching and learning', International Journal of Science and Research 2(9), 19-25, viewed 22 March 2019, from https://www.ijsr.net/archive/v2i9/MjgwODEzMDE=.pdf. [ Links ]
Tyagi, S., 2011, 'Use and awareness of electronic information sources at IIT Roorkee, India: A case study', Italian Journal of Library, Archives and Information Science 2(1), 1-22, viewed 11 April 2019, from https://www.jlis.it/article/view/4586/4482. [ Links ]
Venkatesh, V., Morris, M.G., Davis, G.B. & Davis, F.D., 2003, 'User acceptance of information technology: Toward a unified view', MIS Quarterly 27(3), 425-478, viewed 17 June 2019, from http://www.jstor.org/stable/30036540. [ Links ]
Voorbij, H. & Ongering, H., 2006, 'The use of electronic journals by Dutch researchers: A descriptive and exploratory study', Journal of Academic Librarianship 32(3), 223-237, viewed 21 February 2019, from https://www.sciencedirect.com/science/article/pii/S0099133306000358. [ Links ]
Waldman, M., 2003, 'Freshmen's use of library electronic resources and self-efficacy', Information Research 8(2), 1-26, viewed 24 May 2019, from https://academicworks.cuny.edu/cgi/viewcontent.cgi?article=1051&context=bb_pubs. [ Links ]
Zainab, A.N., Huzaimah, A.R. & Ang, T.F., 2006, 'Using journal use study feedback to improve accessibility', The Electronic Library 25(5), 558-574, viewed 16 April 2019, from https://www.emerald.com/insight/content/doi/10.1108/02640470710829541/full/pdf?title=using-journal-use-study-feedback-to-improve-accessibility. [ Links ]
Zhang, L., Ye, P. & Liu, Q., 2011, 'A survey of the use of electronic resources at seven universities in Wuhan, China', Program 45(1), 67-77, viewed 16 June 2019, from https://www.emeraldinsight.com/doi/full/10.1108/00330331111107402. [ Links ]
Zimbabwe University Libraries Consortium (ZULC), 2018, 'Zimbabwe University Libraries Consortium: Brief history and current status', viewed 27 March 2019, from http://zulc.ac.zw/?page_id=12.
 Correspondence:
Correspondence:
Takawira Machimbidza
tmachimbidza@gmail.com
Received: 23 July 2019
Accepted: 31 Mar. 2020
Published: 17 Aug. 2020
ORIGINAL RESEARCH
A technology, organisation and environment framework analysis of information and communication technology adoption by small and medium enterprises in Pietermaritzburg
Joseph N. Jere; Nsikelelo Ngidi
Discipline of Information Systems and Technology, College of Law and Management Studies, University of KwaZulu-Natal, Pietermaritzburg, South Africa
ABSTRACT
BACKGROUND: Information and communication technology (ICT) has been a major contributor to world economic growth. Information and communication technology has played a vital role when it comes to the growth of small and medium enterprises (SMEs). In developed countries, SMEs are making use of ICT to support their business functions, although this has not been the case in most developing countries. The Global Entrepreneurship Monitor argues that the survival rate of newly established businesses is generally poor, with SMEs in developing countries performing even worse than the standard survival rates
OBJECTIVES: This study aims to investigate the determinants that influence the intention to adopt ICT by SMEs in developing countries using Pietermaritzburg in South Africa as an example to understand this phenomenon
METHOD: The study made use of quantitative methods as its fundamental research approach. A total of 227 SMEs in Pietermaritzburg were surveyed using a close-ended questionnaire. The technology, organisation and environment framework was used as a lens to understand the study, and a structural equation modelling (SEM) approach was applied to analyse the data from respondents
RESULTS: The study revealed that the technology context is the most influential determinant with a regression weight of 0.975 and that both technology and organisation contexts (-0.221) are significant determinants that influence the intention to adopt ICT amongst SMEs in developing countries
CONCLUSION: Based on the findings of the study, it is evident that SMEs need to pay particular attention to ICTs that are relevant to them, including the characteristics and resources of the organisation to successfully adopt these technologies
Keywords: ICT adoption; technology; organisation and environment framework; structural equation modelling; small and medium enterprises.
Introduction
Information and communication technology (ICT) is regarded as a core driver of economic growth (Kossaï & Piget 2014). The majority of world's population has access to some sort of ICT. According to Ying and Lee (2016:3), 'ICT is defined as all those technologies that enable the handling of information and facilitate different forms of communication between human beings and electronic systems'. Different organisations rely on ICT to perform their daily duties to maximise the production of their products and services. Information and communication technology is considered as an important solution that improves the generation and processing of information, and it can further transmit and manage information efficiently (Samuelson & Björk 2014:2). According to Miraz and Habib (2016), in this century, most businesses are influenced by ICT and using ICT as their operation tool. Information and communication technology gives rise to different strategies that organisations can use to gain more revenue whilst spending fewer resources.
Diffusion of ICT has increased rapidly in developing countries, reaching even the low-income populations (Makore 2014). Information and communication technology has provided small and medium enterprises (SMEs) with an opportunity to widen their marketplace, and it enables them to communicate and provide products and services worldwide. Small and medium enterprises are important drivers of the economy and they are the core providers of employment, flexibility and are innovators (Mutula & Van Brakel 2006). It has been suggested that most businesses are classified as SMEs throughout the world, and it is important to understand intentions of these enterprises to adopt ICT (Ramdani, Kawalek & Lorenzo 2009).
Retail business is considered to be one of the most prominent global industries and contributes immensely to the world economy. A large number of retail businesses are considered to be SMEs. The retail industry deals with providing goods to the consumer for personal or household use along with repairing service of the goods (Chinomona & Dubihlela 2014). According to Pantano et al. (2017), the global retail industry in 2014 was responsible for the sales that amounted to $22 trillion and it is estimated that the global retail sales would have reached $28.4 trillion (trn) in 2018. The retail industry is one of the successful businesses throughout the world, and its success has increased the number of shopping centres. Shopping centres are important for development of areas, as they uplift local economy and create employment opportunities that help to eradicate poverty, especially in developing countries.
The adoption of ICT by retail SMEs is considered a significant step towards growth of SMEs, and this research aims to understand the determinants that influence the adoption of ICT by SMEs. According to the researchers, available studies have focused on ICT, but a notable gap is found in these research studies in South Africa. Studies have mainly focused on the adoption of ICT by individuals, governments and big corporate houses, but few studies have investigated the determinants of ICT adoption by retail SMEs.
Small and medium enterprises
Most of the countries in the world consider SMEs as a vehicle of economic growth and employment (Bank 2016), which is also the case with developing countries such as South Africa. The definition of SMEs in South Africa is based on the National Small Business Act 102 of 1996: 'It uses a combination of the number of employees, annual sales turnover, and gross assets excluding fixed property' (Maduku, Mpinganjira & Duh, 2016:2). According to the Banking Association South Africa (TBASA; 2018a), in South Africa approximately 91% of businesses that contribute to the economy are SMEs. They comprise a variety of companies, some of which are registered SMEs, whilst others are not registered and don't contribute towards value-added tax (VAT) (Department of Trade and Industry, Republic of South Africa (DTI) 2005). The informal and non-VAT companies are unlikely to contribute towards the economy, and such companies are mostly for the survival of owner and are unlikely to grow or hire employees.
Contribution of information and communication technology to growth of small and medium enterprises
Information and communication technology is an important infrastructure that connects the world as a whole and is vital for global economic growth. Businesses that use ICT as an operation strategy maximise production and cut costs significantly. According to Ashrafi et al. (2014), there are four ways in which adoption of ICT could contribute in the growth of organisation: (1) recognition of organisation, (2) providing more information to small businesses, (3) towards the organisation exploration of new trade territories, and (4) enabling the enterprise to do business online. According to Niebel (2018), quite a number of studies have examined relationships between ICT effects and economic development in advanced countries, and the majority of studies have shown a positive relationship between the two.
Developing countries trail behind when it comes to adopting ICT, especially for business purposes. Developing countries have less diversified industrial infrastructure which holds back the adoption of ICT (Sadok, Chatta & Bednar 2016). The adoption of ICT in developing countries is hindered by a lot of obstacles such as lack of facilities, technology capabilities and lack of legal determinants (Kossaï & Piget 2014). The majority of developing countries struggle with finances, which impact infrastructure development, and a poorly skilled population to support development. Yousefi (2015) argues that even though developing countries are lagging behind when it comes to ICT penetration, there are evidences that developing countries in the past decade have adopted ICT more than the developed countries.
The arrival of technology such as mobile devices and cloud computing has made it affordable and accessible for businesses to adopt it. ICT allows SMEs to compete with large corporations because of the Internet. According to former studies, there is evidence that shows the positive effect of adopting ICT such as increased revenues, market share and increase in production (Tarutė & Gatautis 2014). The evidence shows that plenty could be gained by SMEs if they adopt ICT. Ashrafi et al. (2014) argue that lack of IT skills is one of the biggest reasons why most SMEs are not adopting ICT even in European countries such as Poland, Portugal and the UK.
Conceptual framework
Technology, organisation and environment framework
The study made use of a conceptual framework whose core constructs were adopted from the technology, organisation and environment (TOE) theoretical framework proposed by Tornatzky, Fleischer and Chakrabarti (1990) consisting of variables which were found to be suitable for the study (Figure 1). Technology, organisation and environment theoretical framework is a classical framework used to predict the firm's intention to adopt an information system (IS). According to Oliveira and Martins (2011), the TOE framework could be used to understand the determinants that influence the adoption of new technology innovation by a firm. The TOE framework consists of the following three constructs: the technological context, the organisational context and the environmental context of the firm. Different studies have used the TOE theoretical framework as a lens to study adoption of technology (Awa, Ojiabo & Emecheta 2015; Baker 2012; Oliveira & Martins 2011).
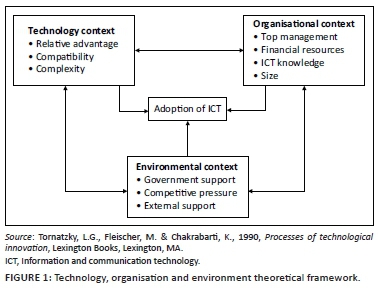
Technology context (Construct 1)
Different theoretical frameworks consider technology as a determinant that influences the adoption of new technology innovations. Baker (2012) argues that for the new technology adoption to succeed, the organisation must have a firm IT infrastructure, employee's technical skills and user time. Organisations that are familiar with technology are more probable to adopt innovations. Existing technology within an organisation set a tone for how much technology adoption can an organisation undertake (Baker 2012). It is not enough for an organisation to have technology resources only. Technology competency is more than just having the equipment; it is important to have innovative and skilful people and people who could keep the organisation ahead of its competitors (Metaxiotis 2009).
Technology context sub-constructs
Relative advantage
The relative advantages of adopting ICT by SMEs are the benefits that the business gains by using ICT. Different types of measures determine that the innovation provides a relative advantage; measures such as financial benefits are important, but convenience, satisfaction and high standard are also crucial measures. Chiu, Chen and Chen (2017) argue that relative advantage is one of the most important determinants that influence the adoption of ICT in Malaysia. The owner/manager of an SME is more likely to adopt an ICT if it is beneficial for the business (Maduku et al. 2016).
Compatibility
If management believes in new technology and its compatibility with the existing systems and business processes, then it is easier to adopt new technology (Borgman et al. 2013). According to Ghobakhloo and Hong Tang (2013), some studies have determined that the adoption and use of ICT, such as e-commerce, are influenced by compatibility. A study in Malaysia on ICT adoption by SMEs has found that compatibility is an influential factor (Chiu et al. 2017).
Complexity
Innovations that are complex to use are more likely to be adopted slowly, whilst innovations that are easy to master are adopted faster. The complexity of technology innovation could be a defining factor between adopting and not adopting of technology because owners believe that complex ICTs could be risky to adopt, and they are more likely to be abandoned (Abualrob & Kang 2016). Owners/managers, especially that of SMEs, may feel that it would be costly to take employees for expensive and long training. Abualrob and Kang (2016) found that complexity is an important determinant that influences the adoption of new technology.
Organisation context (Construct 2)
Organisation context is about defining the determinants of an organisation, for instance organisational size; the centralisation, formalisation and complexity of management structure; and communication channels and decision-making (Angeles 2014). Top executives champion for changes in an organisation, and they hinder progress or encourage the adoption of technology (Angeles 2014). The scope and size of an organisation are important determinants that influence the adoption of technology (Rogers 1995; Tornatzky et al. 1990).
Organisation context sub-constructs
Top management support
Djatikusumo (2014) argues that in SMEs it is important to have managerial support because strategies and organisational objectives are strongly influenced by the owners/managers of a firm. If top management in SMEs find out the potential benefits of using new ICTs and the risks are minimum, then there is a high possibility of adopting new ICT (Ghobakhloo & Hong Tang 2013). Top management support is a key determinant when it comes to understanding the firm's behaviour towards the adoption of a new ICT innovation (Maduku et al. 2016).
Financial resources
Lack of financial resources is a common problem amongst SMEs because of deficiency of effective organisational governance; hence their ICTs are also ineffective (Djatikusumo 2014). In the study conducted by Mpofu, Milne and Watkins-Mathys (2013), most SMEs in South African tourism argue that lack of finances is a major reason that they don't adopt new ICT. Literature on the adoption of ICTs suggests that the adoption of new ICTs is more likely to be influenced by the availability of financial resources (Nguyen & Petersen 2017).
Knowledge of information and communication technology
Alshamaila (2013) argue that a small portion of SMEs have adequate ICT platforms and employees with necessary ICT knowledge (ITK) that can help them to adopt new ICT innovations. Ability of a firm to adopt innovation lies in its employees' ability to use their existing ICT knowledge (Hung et al. 2016). Tarutė and Gatautis (2014) argue that studies that aim to understand the relationship amongst ICT adoption and ICT knowledge have found that there is a positive impact to have ICT knowledge when it comes to the adoption of an innovation.
Firm size
Internet has provided SMEs with a platform to compete with bigger organisations with the aid of an ICT such as e-commerce. According to Nguyen and Petersen (2017), there is a significant relationship between firm size and ICT adoption. Small and medium enterprises are better suited for adopting new ICTs because they are flexible and can adjust quickly, unlike big organisations that are not agile (Kilangi 2012).
Environment context (Construct 3)
The environment aspect looks at the elements of the structure of industry, service providers of the technology, and environment regulations (Baker 2012). Tornatzky et al. (1990) argue that mature and declining industry is less likely to adopt new technology, whilst organisations that are part of fast-growing industries are more likely to adopt technology rapidly. Fast-growing industries adopt technology to maximise production and minimise expenses. Regulators determine whether an organisation could implement certain technology to meet the criteria or not (Angeles 2014).
Environment context sub-constructs
Government support
Government support (GS) is the most important determinant that influences ICT adoption by SMEs (Dahnil et al. 2014). Most governments understand the importance of helping SMEs to grow as most of the SMEs lack resources, so it is important for governments to provide support. There is a delay in the implementation of ICT regulations in most developing countries (Findik 2013). According to Kilangi (2012), government plays an important part as a support system for SMEs by providing rules, regulations and support that help to guide SMEs to success through different organisations such as Small Industries Development Organisation (SIDO).
Competitive pressure
According to Awa et al. (2015), competitive pressure plays a role when it comes to the adoption of ICTs, but it is not very important factor that influences adoption. In industries with high competition, it is important to be ahead when it comes to the adoption of ICT to rip the reward of using ICT (Yoon 2012). A study conducted by Malak (2016) has revealed that there is a relationship between the adoption of cloud computing and competitive pressure. Competitive pressure is mostly observed in developed countries using advance ICTs (Chiu et al. 2017).
External support
Small and medium enterprises rely on external support for implementation and maintenance of ICT because it is expensive to have in-house IT experts. External support is a substantial determinant that influences the adoption of e-procurement and enterprise system, but external support has proved to be more complicated for vendors (Chiu et al. 2017). According to Awa et al. (2015), external support is an important determinant that defines the actual adoption of ICT. External support is very important for SMEs especially when the firms are not familiar with new ICT innovation (Ismail & King 2014).
Research methods and design
This study is a descriptive study and can be explained by three points: describing, explaining and validating the study findings. This study used quantitative approach as its fundamental approach. Quantitative studies have an advantage that they force the thoroughness and intelligence that are fundamental for tending to the measurements and internal consistency that support the adoption of SMEs (Dlodlo & Dhurup 2013). This study used a sample of retail businesses to save time and resources. The study used a non-probability technique, which is also known as a judgement and convenience sampling technique, and the participants were visited at their convenient time. The sample size was determined by using a population size of 533 retail SMEs who operate in Pietermaritzburg with a 5% error margin, 95% confidence level and 50% response distribution, and this provided a minimum sample size of 227 SMEs. The population size was provided by the Msunduzi municipality which had the list of registered SMEs within Pietermaritzburg. The data collection instrument was a self-administered questionnaire. The questionnaire comprised four sections that use a five-point Likert scale with the ratings of 1 as 'strongly disagree' to 5 as 'strongly agree'.
Research Problem
Small and medium enterprises play a major role when it comes to the improvement of national economies in developing countries. According to TBASA (2018b), SMEs are important drivers of an economy as they are significant when it comes to reducing unemployment in South Africa. Small and medium enterprises have the potential to uplift local economies, and therefore governments invest in the development of SMEs. Small and medium enterprises continue to struggle to survive in the South African economy despite participation of government. According to DTI (Strategies 2006), the majority of SMEs fail at an average of 3.5 years of their establishment. The Global Entrepreneurship Monitor (GEM) argues that most start-up businesses hardly survive and the survival rate of SMEs in developing countries is even less (Small Enterprise Development Agency [SEDA] 2016). According to TBASA (2018b), the failure of SMEs in South Africa is mainly caused by the lack of appropriate technology, production capacity and access to markets.
The adoption of ICT is known to improve the status quo of SMEs by providing them competitive advantage (Pillay 2016). The benefits of ICT could assist the sustainability of retail SMEs in South Africa. South Africa is amongst the developing nations of Africa that have a high penetration of ICT adoption (International Telecommunication Union [ITU] 2016). According to Nuamah-Gyambrah, Agyeiwaa and Offei (2016), ICT has helped many businesses in lowering communication and transaction costs, increasing production and widening the market base. According to the United Nations (UN), technological progress is the solution to world economic problems (Sustainable Development Goals [SDGs] 2017). Small and medium enterprises must be educated about the benefits of using ICT as part of their business strategy.
Study objective
The study objective is to investigate determinants that influence the intention to adopt ICTs by SMEs in developing countries and determine the suitability of the theorised model for ICT adoption by SMEs.
This objective is investigated through the lens of a conceptual framework which adopts the TOE theoretical framework constructs by Tornatzky et al. (1990) and applying the framework in the context of a developing nation, that is, South Africa. This framework is well known as a preferred choice when it comes to investigating the adoption of innovation at firm's level.
Analysis
Sampling adequacy
The Kaiser-Meyer-Olkin (KMO) sampling adequacy test was employed to determine the measure of the proportion of variance amongst variables that might be common variance. The recommended value of the KMO test is suggested to be from 0.7 and higher, and the Bartlett's test value is considered significant if p < 0.05 (Kilangi 2012). The KMO test for this study is 0.924, which is acceptable, thus the data are correlated.
The data collected was composed in a form of five-point Likert scale, and it was crucial to test the reliability of data (Table 1). Cronbach's alpha (α) test was employed to measure data reliability. According to Abualrob and Kang (2016), the value of 0.70 is considered to be an acceptable value of Cronbach's alpha. The observed values of Cronbach's alpha were between 0.75 and 0.963, which are considered to be good to excellent values. The internal consistency of the variables is good, which suggests that there is a correlation amongst variables.
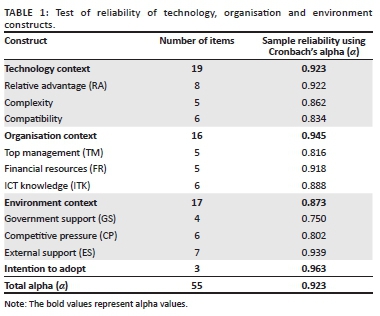
Table 2 shows the correlations between the variables of TOE theoretical framework because the data were not distributed normally and the Spearman's rho (ρ) test was conducted. The correction results show that there was a positive correction between the TOE variables, and all the correlations were significant at p < 0.01.
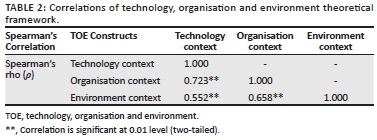
Table 3 shows the regression weight estimates between independent variables, technological context, organisational context and environmental context and the dependent variable Adopt_ICT. The regression estimate between technology context and Adopt_ICT was 0.975 and it was significant at p < 0.05. The regression estimates between organisation context and Adopt_ICT was −0.221 and it was significant at p < 0.05. The regression table further shows that the regression estimate between the variable environment context and Adopt_ICT was −0.014 with a p-value of 0.938, which was greater than 0.05, which means the regression was not significant between the two variables.
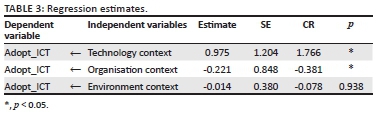
Correlations and regressions of environment context variables
Table 3 revealed that regression estimates of environment context towards Adopt_ICT were insignificant, and this finding was further explored so that the results of environment context variable could be understood in a better way. The environment context variables were positively correlated: government support and competitive pressure had a correlation of 0.155, which was significant at p < 0.05; government support and external support had a correlation of 0.380, which was significant at p < 0.01; and competitive pressure and external support had a correlation of 0.283, which was significant at p < 0.01.
Table 4 shows regression estimates of environment context variables. The findings of regression estimate on environment context found that government support was insignificant when it comes to influencing the adoption of ICT with a p-value of 0.906. Competitive pressure and external support were significant when it comes to influencing the adoption of ICT with a regression estimate of 0.00, which was significant at p < 0.05.
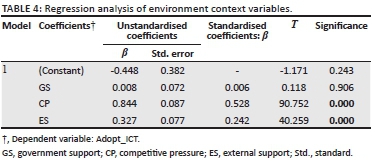
Model-fit index
Table 5 shows the result of a model fit. According to Hu and Bentler (1999), it is recommended to use a combination of comparative fit index (CFI) and Standardised Root Mean Square Residual (SRMR), with a measure of CFI close to 0.95 and that of SRMR close to 0.08 when the sample size is less or equal to 250. Table 5 shows that CFI = 0.929, which was close to 0.95 and was recommended by Hu and Bentler (1999), and SRMR = 0.07, which was close to 0.08. The Root Mean Square Error of Approximation (RMSEA) = 0.074, which means that the model fit was acceptable according to Hu and Bentler (1999). The model fits the data.
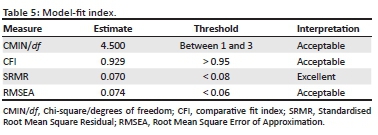
Figure 2 shows that the factor loadings for the observed variables were above 0.6, and there was only one variable below 0.6 with a value of 0.31. Government support has the lowest loading, which suggests that this variable was less correlated with other variables. Further, Figure 2 also shows the regression estimates with the technology context having the highest regression of 0.97 towards the adoption of ICT (Adopt_ICT), and this regression estimate was significant. The regression estimate for organisation context was −0.22 towards intention to adopt ICT and was significant at p < 0.05. The environment context had a regression estimate of −0.01 towards intention to adopt ICT, which meant that the path was insignificant at p < 0.05. The regression weight analyses from structural equation modelling (SEM) revealed that only technology context could be considered the best predictor for intention to adopt ICT by SMEs with a weightage of 0.97, which was above the suggested threshold of 0.80 (Jeyaraj, Rottman & Lacity 2006).
It is also shown in Figure 2 that the covariance correlation with a relationship between technology context and organisation context has a correlation of 0.96. The correlation between technology context and environment context was 1.09. The relationship between organisation context and environment context had the highest correlation of 1.10.
Discussion
The technology context consists of three variables: relative advantage, complexity and compatibility. The analysis shows that these variables are correlated, and compatibility has the highest loading factor. The technology context is correlated with environment context and it was correlated with organisation context. The technology context has a positive correlation and a significant regression estimate towards intention to adopt ICT, which means that technology context is a significant determinant of intention to adopt ICT. According to Jeyaraj et al. (2006), a predictor that has a regression of 0.08 and above is considered to be the best predictor. The technology context is the most influential determinant for intention to adopt ICT by SMEs. Gareeb and Naicker (2015) argue that the technology context determinant is influential when it comes to the adoption of broadband technology by SMEs, with relative advantage and compatibility as the most significant contributors. Gono, Harindranath and Özcan (2016) echo the same sentiments about technology context being a significant determinant, and relative advantage and compatibility being the important players that influence the intention to adopt ICT.
The second determinant of the TOE framework is organisation context. The organisation context consists of four variables: top management support, financial resources, IT knowledge and size of the firm. The analysis shows that the variables of organisation context are highly correlated, and they have a high loading factor compared with the majority of TOE framework's variables except for firm size. The firm size had a low loading factor of below 0.3, and keeping the firm size causes the model to become unfit for data. Loading factor for a sample size of less than 300 should have a value of greater or equal to 0.3 (Yong & Pearce 2013). The firm size was deleted from the model because it had a loading factor of less than 0.3. The organisation context is highly correlated with environment context and it is correlated with technology context. The regression towards ICT adoption intention from organisation is negative but significant. This finding suggests that organisation context is influential towards the adoption of ICT, and the negative regression suggests that as the negative value decreases, the ICT adoption increases. The organisation context is a determinant of ICT adoption. The organisation context is an influential determinant of broadband technology adoption by retail SMEs and top management support has the maximum effect (Gareeb & Naicker 2015). The organisation context is the most influential determinant of mobile marketing technology with top management support having the highest loading factor (Maduku et al. 2016).
The environment context consists of three variables: government support, competitive pressure and external support. The analysis shows that all the variables of environment context are correlated. The loading factor of government support is 0.3, which shows a weak correlation with other variables, whilst the other two variables have loading factors that are just above 0.6, which is significant. The regression estimate towards ICT adoption intention from environment context is negative and insignificant. The environment context is not a significant determinant of ICT adoption in SMEs. This finding suggests that the environment context is not influential towards the adoption of ICT. According to Gareeb and Naicker (2015), the environment context has minimum impact on the adoption of broadband technology because of the government's lack of providing support to businesses. Malak (2016) argue opposite to the findings of Gareeb and Naicker (2015) and observes that the environment context is significant in the study of Cloud adoption.
Further exploration of environment context shows influential variable. The results show that external support is significant, thus it is influential when it comes to the adoption of ICT. Competitive pressure is also shown to be significant and influential when it comes to adopting ICT. Government support is insignificant, and this means that it is not influential when it comes to the adoption of ICT by SMEs. The government's lack of assistance has been the most notable problem when it comes to assisting SMEs in South Africa. Gareeb and Naicker (2015) echo similar sentiments about the lack of government assistance. The government of South Africa has a lot of policies that aims to assist SMEs, but it lacks follow through on its promises to the public. Mpofu et al. (2013) found that the government of South Africa plays a significant role when it comes to assisting the tourism industry, but there is still more that the government can do to uplift the industry. According to Gono et al. (2016), the government should play a better role in providing ICT support to SMEs and developing business personnel's ICT skills.
Understanding the determinants that influence adoption assists SMEs and the government to understand what needs to be exercised to influence the adoption of ICT by SMEs. This study used the TOE theoretical framework as a tool to study influential determinants. The theoretical framework consists of technological context, organisational context and environmental context. The analysis shows that the determinants that influence the intention to adopt ICT are technology context and organisation context. The technology context positively influences the intention to adopt ICT, whilst the organisation context influences the intention to adopt ICT negatively. The study revealed that the environment context was not an influential determinant for the adoption of ICT in SMEs. Further analysis of the environment context revealed that its sub-construct government support was an insignificant variable, whilst two other sub-constructs, competitive pressure and external support, were found to have a significant influence on the adoption of ICT by SMEs in developing countries. Government support is the variable that causes problems, and Gareeb and Naicker (2015) have found lack of government agents, including policy challenges, to be some of the reasons that SMEs have challenges in adopting mobile marketing technology. Lutfi, Idris and Mohamad (2016) argue the opposite of what this study has revealed about government support; in Malaysia, government support is influential when it comes to ICT adoption. The Malaysian context could be explained by its government's liberalisation of telecommunications sector and opening it up to private service providers. This coupled with high investment in the ICT sector lead it to be ranked 56 in the global ICT development index, with the world average at a ranking of 159. Malaysia outranked countries such as China, 76, India, 117, the Philippines, 90 and Indonesia 107 (Hill, Yean & Zin 2013).
Technology context is the only determinant with a regression above 0.08; thus, according to Jeyaraj et al. (2006), it is the only determinant which is considered to be a predictor. Technology context is the most influential determinant. The technology context variables are highly correlated, which are relative advantage, compatibility and complexity. These variables are considered by many studies as important determinants of ICT adoption (Gareeb & Naicker 2015; Gono et al. 2016). Understanding the benefits and compatibility of ICT is important as it makes participants decisive about their intention to adopt ICT.
The TOE theoretical framework is an established framework being used in many studies by researchers. Throughout its existence, various changes have been made to this framework to accommodate for the evolving scenarios and contexts and thereby allowing for the analysis of these different contexts. Use of TOE in this study was based on a previous research that has applied the same framework on firm-level studies (Malak 2016). The model fits the data when tested, thus the TOE framework is a suitable model and can be considered for studying the intention to adopt ICT by SMEs in Pietermaritzburg. This developed theoretical framework assists to understand the relationship between the determinants of intention to adopt ICT.
Conclusion
This study provided empirical evidence concerning the investigation of determinants that influence the adoption of ICT in SMEs in developing countries. The study used a conceptual framework whose core constructs were adopted from the TOE theoretical framework comprising the following constructs: technological context, organisational context and environment context, each of these has sub-constructs extracted from various studies and found to be suitable for this study: complexity, relative advantage, compatibility, top management support, financial resources, ICT knowledge, firm size, government support, competitive pressure and external support. The use of TOE framework allowed for understanding of ICT adoption by SMEs at firm level in developing countries. Although there still is a need to conduct a more comprehensive research to understand ICT adoption by SMEs for growth in developing countries, this study revealed that both technology context and organisational context have a significant influence on ICT adoption by SMEs. The study further revealed that technology context was the most important determinant that influences SMEs' intention to adopt ICT in developing countries such as South Africa. An analysis of environment context revealed that sub-constructs competitive pressure and external support had a significant influence on ICT adoption by SMEs, although the sub-construct government support showed that it did not have a significant influence. One of the main findings of this study was that the model for ICT adoption by SMEs used here fit the data well and could be used to inform the future research.
Acknowledgements
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
N.N. and J.N.J. contributed equally to this work.
Ethical consideration
Ethical approval to conduct the study was obtained from the University of KwaZulu-Natal's School of Management, IT and Governance, Humanities and Social Sciences Research Ethics Committee (reference number HSS/1939/018M).
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The data sets generated during and/or analysed during the current study are not publicly available because of this being a subset of a broader study, which is currently being completed, but are available from the corresponding author on a reasonable request.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abualrob, A.A. & Kang, J., 2016, 'The barriers that hinder the adoption of e-commerce by small businesses: Unique hindrance in Palestine', Information Development 32(5), 1528-1544. https://doi.org/10.1177/0266666915609774 [ Links ]
Alshamaila, Y.Y., 2013, An empirical investigation of factors affecting cloud computing adoption among SMEs in the North East of England, PhD thesis, New Castle University, London.
Angeles, R., 2014, 'Using the technology-organization-environment framework for analyzing Nike's "Considered Index" green initiative, a decision support system-driven system', Journal of Management and Sustainability 4(1), 96. https://doi.org/10.5539/jms.v4n1p96 [ Links ]
Ashrafi, R., Sharma, S.K., Al-Bedi, A.H. & AlGharbi, K., 2014, 'Achieving business success through information and communication technologies adoption by small and medium enterprises in Oman', Middle-East Journal of Scientific Research 22(1), 138-146. [ Links ]
Awa, H.O., Ojiabo, O.K. & Emecheta, B.C., 2015, 'Integrating TAM, TPB and TOE frameworks and expanding their characteristic constructs for e-commerce adoption by SMEs', Journal of Science & Technology Policy Management 6(1), 76-94. https://doi.org/10.1108/JSTPM-04-2014-0012 [ Links ]
Baker, J., 2012, The technology-organization-environment framework. Information systems theory, pp. 231-245, Springer, New York, NY.
Bank, T.W., 2016, Entrepreneurs and small businesses spur economic growth and create jobs, viewed 24 Febrauary 2018, from http://www.worldbank.org/en/news/feature/2016/06/20/entrepreneurs-and-small-businesses-spur-economic-growth-and-create-jobs.
Borgman, H.P., Bahli, B., Heier, H. & Schewski, F., 2013, 'Cloudrise: Exploring Cloud Computing Adoption and Governance with the TOE Framework', 2013 46th Hawaii International Conference on System Sciences, Wailea, Maui, HI, January 7-10, 2013, pp. 4425-4435. https://doi.org/10.1109/HICSS.2013.132
Chinomona, R. & Dubihlela, D., 2014, 'Does customer satisfaction lead to customer trust, loyalty and repurchase intention of local store brands? The case of Gauteng Province of South Africa', Mediterranean Journal of Social Sciences 5(9), 23-32. [ Links ]
Chiu, C.-Y., Chen, S. & Chen, C., 2017, 'An integrated perspective of TOE framework and innovation diffusion in broadband mobile applications adoption by enterprises', International Journal of Management, Economics and Social Sciences (IJMESS) 6(1), 14-39. [ Links ]
Dahnil, M.I., Marzuki, K.M., Langgat, L. & Fabeil, N.F., 2014, 'Factors influencing SMEs adoption of social media marketing', Procedia - Social and Behavioral Sciences 148, 119-126. https://doi.org/10.1016/j.sbspro.2014.07.025 [ Links ]
Djatikusumo, D.S., 2014, Determinants of SMEs' adoption of information communication technology (ICT) and their impact on organizational performance in Indonesia, University of Canberra, Canberra.
Dlodlo, N. & Dhurup, M., 2013, 'Drivers of e-marketing adoption among small and medium enterprises (SMEs) and variations with age of business owners', Mediterranean Journal of Social Sciences 4(14), 53-66. https://doi.org/10.5901/mjss.2013.v4n14p53 [ Links ]
Department of Trade and Industry, Republic of South Africa (DTI), 2005, Integrated strategy on the promotion of entrepreneurship and small enterprises, DTI, Pretoria.
Findik, D., 2013, ICT adoption, software investment and firm efficiency in Turkey, the Graduate School of Social Sciences of Middle East Technical University, Ankara.
Gareeb, P.P. & Naicker, V., 2015, 'Determinants for South African SMEs to adopt broadband Internet technologies', The Electronic Journal of Information Systems in Developing Countries 68(1), 1-24. https://doi.org/10.1002/j.1681-4835.2015.tb00491.x [ Links ]
Ghobakhloo, M. & Hong Tang, S., 2013, 'The role of owner/manager in adoption of electronic commerce in small businesses: The case of developing countries', Journal of Small Business and Enterprise Development 20(4), 754-787. https://doi.org/10.1108/JSBED-12-2011-0037 [ Links ]
Gono, S., Harindranath, G. & Özcan, G.B., 2016, 'The adoption and impact of ICT in South African SMEs', Strategic Change 25(6), 717-734. https://doi.org/10.1002/jsc.2103 [ Links ]
Hill, H., Yeen, T.S. & Zin, R.H.M., 2013, Malaysia's development challenges: Graduating from the middle, Routledge, London.
Hu, L.T. & Bentler, P.M., 1999, 'Cutoff criteria for fit indexes in covariance structure analysis: Conventional criteria versus new alternatives', Structural Equation Modeling: A Multidisciplinary Journal 6(1), 1-55. https://doi.org/10.1080/10705519909540118 [ Links ]
Hung, S-Y., Tsai, J.C-A. & Chou, S-T., 2016, 'Decomposing perceived playfulness: A contextual examination of two social networking sites', Information & Management 53(6), 698-716. [ Links ]
International Telecommunication Union (ITU), 2016, ITU releases 2016 ICT figures, viewed 02 February 2018, from https://www.itu.int/en/mediacentre/Pages/2016-PR30.aspx.
Ismail, N.A. & King, M., 2014, 'Factors influencing the alignment of accountig information systems in small- and medium-sized Malaysian manufacturing firms', Journal of Information Systems and Small Business 1(1-2), 1-20. [ Links ]
Jeyaraj, A., Rottman, J.W. & Lacity, M.C., 2006, 'A review of the predictors, linkages, and biases in IT innovation adoption research', Journal of Information Technology 21(1), 1-23. https://doi.org/10.1057/palgrave.jit.2000056 [ Links ]
Kilangi, A.M., 2012, The determinants of ICT adoption and usage among SMEs: The case of the tourism sector in Tanzania, PhD thesis, VU University, Amsterdam.
Kossaï, M. & Piget, P., 2014, 'Adoption of information and communication technology and firm profitability: Empirical evidence from Tunisian SMEs', The Journal of High Technology Management Research 25(1), 9-20. https://doi.org/10.1016/j.hitech.2013.12.003 [ Links ]
Lutfi, A.A., Idris, K.D. & Mohamad, R., 2016, 'The influence of technological, organizational and environmental factors on accounting information system usage among Jordanian small- and medium-sized enterprises', International Journal of Economics and Financial Issues 6(7S), 240-248. [ Links ]
Maduku, D.K., Mpinganjira, M. & Duh, H., 2016, 'Understanding mobile marketing adoption intention by South African SMEs: A multi-perspective framework', International Journal of Information Management 36(5), 711-723. https://doi.org/10.1016/j.ijinfomgt.2016.04.018 [ Links ]
Makore, M.P., 2014, Exploring the use of mobile banking services: Case study of Wizzit Bank, South Africa, University of KwaZulu-Natal, Durban.
Malak, J., 2016, An analysis of the technological, organizational, and environmental factors influencing cloud adoption, PhD thesis, Walden University, Minneapolis, MI.
Metaxiotis, K., 2009, 'Exploring the rationales for ERP and knowledge management integration in SMEs', Journal of Enterprise Information Management 22(1/2), 51-62. https://doi.org/10.1108/17410390910922822 [ Links ]
Miraz, M.H. & Habib, M., 2016, 'ICT adoption in small and medium enterprises: An empirical evidence of service sectors in Bangladesh', Journal of Economics, Business and Management 4(8), 482-485. [ Links ]
Mpofu, K.C., Milne, D. & Watkins-Mathys, L., 2013, ICT adoption and development of E-business among SMEs in South Africa', Buckinghamshire New University, Buckinghamshire, UK.
Mutula, S.M. & Van Brakel, P., 2006, 'E-readiness of SMEs in the ICT sector in Botswana with respect to information access', The Electronic Library 24(3), 402-417. https://doi.org/10.1108/02640470610671240 [ Links ]
Nguyen, T. & Petersen, T.E., 2017, Technology adoption in Norway: Organizational assimilation of big data, Norwegian School of Economics, Bergen.
Niebel, T., 2018, 'ICT and economic growth - Comparing developing, emerging and developed countries', World Development 104, 197-211. https://doi.org/10.1016/j.worlddev.2017.11.024 [ Links ]
Nuamah-Gyambrah, K., Agyeiwaa, F. & Offei, M., 2016, 'Role of CT in the survival of small and medium scale enterprises in Ghana evidence from selected small and medium scale enterprises in New Juaben Municipality Koforidua', International Journal of Managing Public Sector Information and Communication Technologies (IJMPICT) 7(1), 1-14. https://doi.org/10.5121/ijmpict.2016.7101 [ Links ]
Oliveira, T. & Martins, M.F., 2011, 'Literature review of information technology adoption models at firm level', Electronic Journal of Information Systems Evaluation 14(1), 110-121. [ Links ]
Pantano, E., Priporas, C.-V., Sorace, S. & Iazzolino, G., 2017, 'Does innovation-orientation lead to retail industry growth? Empirical evidence from patent analysis', Journal of Retailing and Consumer Services 34, 88-94. https://doi.org/10.1016/j.jretconser.2016.10.001 [ Links ]
Pillay, P., 2016, Barriers to information and communication technology (ICT) adoption and use amongst SMEs: A study of the South African manufacturing sector, Wits Business School, Johannesburg.
Ramdani, B., Kawalek, P. & Lorenzo, O., 2009, 'Predicting SMEs' adoption of enterprise systems', Journal of Enterprise Information Management 22(1/2), 10-24. https://doi.org/10.1108/17410390910922796 [ Links ]
Rogers, E., 1995, Diffusion of innovations, 4th edn., The Free Press, New York.
Sadok, M., Chatta, R. & Bednar, P., 2016, 'ICT for development in Tunisia: "Going the last mile"', Technology in Society 46, 63-69. [ Links ]
Samuelson, O. & Björk, B.-C., 2014, 'A longitudinal study of the adoption of IT technology in the Swedish building sector', Automation in Construction 37, 182-190. https://doi.org/10.1016/j.autcon.2013.10.006 [ Links ]
Small Enterprise Development Agency (SEDA), 2016, The small, medium and micro enterprise sector of South Africa, viewed 24 May 2018, from http://www.seda.org.za/Publications/Publications/The%20Small,%20Medium%20and%20Micro%20Enterprise%20Sector%20of%20South%20Africa%20Commissioned%20by%20Seda.pdf
Strategies, U.B., 2006, Integrated Strategy on the Promotion of Entrepreneurship and Small Business. Department of Trade and Industry, Pretoria.
Sustainable Development Goals (SGD), 2017, SGD Goal 9: Industry, innovation, infrastructure, viewed 18 Feburary 2018, from http://www.sdgfund.org/goal-9-industry-innovation-infrastructure.
Tarutė, A. & Gatautis, R., 2014, 'ICT impact on SMEs performance', Procedia - Social and Behavioral Sciences 110(0), 1218-1225. https://doi.org/10.1016/j.sbspro.2013.12.968 [ Links ]
The Banking Association of South Africa (TBASA), 2018a, Small business definition, viewed 15 May 2018, from http://www.banking.org.za/what-we-do/sme/sme-definition.
The Banking Association of South Africa (TBASA), 2018b, SME enterprise, viewed 23 July 2018, from http://www.banking.org.za/what-we-do/sme/sme-enterprise.
Tornatzky, L.G., Fleischer, M. & Chakrabarti, K., 1990, Processes of technological innovation, Lexington Books, Lexington, MA.
Ying, H. & Lee, S., 2016, 'Survey of the research of ICT applications in the AEC industry: A view from two mainstream journals', in Proceedings of the 16th International Conference on Construction Applications of Virtual Reality, The Hong Kong University of Science and Technology, Hong Kong, December 11-13, 2016, pp. 471-483. https://hub.hku.hk/bitstream/10722/241035/1/Content.pdf
Yong, A.G. & Pearce, S., 2013, 'A beginner's guide to factor analysis: Focusing on exploratory factor analysis', Tutorials in Quantitative Methods for Psychology 9(2), 79-94. https://doi.org/10.20982/tqmp.09.2.p079 [ Links ]
Yoon, T., 2012, An empirical investigation of factors affecting organizational adoption of virtual worlds, The Florida State University, FL.
Yousefi, A., 2015, 'A Panel Granger causality test of investment in ICT capital and economic growth: Evidence from developed and developing countries', Economics World 3(5-6), 109-127. https://doi.org/10.17265/2328-7144/2015.0506.001 [ Links ]
 Correspondence:
Correspondence:
Joseph Jere
jeren@ukzn.ac.za
Received: 04 Nov. 2019
Accepted: 21 May 2020
Published: 08 Sept. 2020
ORIGINAL RESEARCH
Rural-based Science, Technology, Engineering and Mathematics teachers' and learners' acceptance of mobile learning
David Mutambara; Anass Bayaga
Department of Maths, Science and Technology Education, Faculty of Education, University of Zululand, Richards Bay, South Africa
ABSTRACT
BACKGROUND: Science, Technology, Engineering and Mathematics (STEM) is faced with many challenges resulting in learners' poor performance at matriculation level in South Africa. However, prior research has shown that mobile learning (m-learning) can be used to alleviate the challenges of STEM education. Prior research focused on tertiary institutions' students and lecturers, in developed countries. However, very little is known about rural school STEM teachers' and learners' acceptance of m-learning.
OBJECTIVES: The article investigates factors that rural-based STEM teachers and learners consider important when adopting mobile learning. Furthermore, the study also seeks to examine if there is a statistically significant difference between teachers' and learners' acceptance of mobile learning.
METHOD: The research employed a quantitative approach. Stratified random sampling was used to select 350 teachers and learners to participate in the survey. Valid questionnaires received were 288 (82%), and data were analysed using partial least squares structural equation modelling.
RESULTS: The proposed model explained 64% of the variance in rural-based STEM teachers' and learners' behavioural intention to use m-learning. Perceived attitude towards use was found to be the best predictor of teachers' and learners' behavioural intention. The results also showed no significant difference between teachers' and learners' path coefficients.
CONCLUSION: The research recommends that awareness campaigns, infrastructure, mobile devices and data need to be made available for m-learning to be successfully adopted in rural areas.
Keywords: technology acceptance model; perceived social influence; perceived resources; STEM; perceived usefulness; perceived ease of use; perceived ease to collaborate.
Introduction
Science, Technology, Engineering and Mathematics (STEM) Task Force (2014:9) in America adopts the view that STEM education is far more than a 'convenient integration of its four disciplines; rather, it encompasses 'real-world, problem-based learning' that integrates the disciplines through cohesive and active teaching and English learning approaches'. What can be learnt from this view is that STEM education aims at teaching learners to solve real-world problems, collaborate and integrate these four disciplines rather than learning these disciplines in isolation, just as they do not exist in isolation in the real world.
However, STEM is faced with many challenges resulting in learners' poor performance at the matriculation level in South Africa. According to Bosman and Schulze (2018), this poor performance is because of the mismatch between the teaching style and the learners' learning styles in the classroom. Bosman and Schulze (2018) suggest that teachers are still using traditional face-to-face instruction, which can only cater for 20% of the class and fails to stimulate deep holistic learning experiences. On the other hand, Visser, Juan and Feza (2015) attribute this poor performance, particularly in rural areas, to lack of textbooks and learning material. Additionally, Mboweni (2014) blamed poor performance in STEM-related subjects to a high rate of learner absenteeism. Mboweni (2014) noted among others, poverty, HIV/AIDS, social grants pay out days, lack of parental involvement, teenage pregnancy and unstable family backgrounds as the leading causes of learners' absenteeism in rural areas. Based on the aforementioned studies, one can conclude that there is no effective teaching and learning of STEM-related subjects in rural areas.
Regardless of the work of Bosman and Schulze (2018), Visser et al. (2015) and Mboweni (2014) on the challenges of STEM education, prior studies have also shown that mobile learning (m-learning) can be used to mitigate these challenges (Alrajawy et al. 2017; Bourgonjon, Valcke & Soetaert 2010; Criollo-C, Luján-Mora & Jaramillo-Alcázar 2018). There are several reasons attributed to the need for m-learning, hence this study. The view is that m-learning increases contact time between teachers and learners (Alrajawy et al. 2017). Another view is that through the use of m-learning, absent learners can still learn what was covered as content can be made available anywhere and anytime, as learning will be no longer confined to the classroom. Consequently, Bourgonjon et al. (2010) noted that m-learning changes lessons from teacher-centred to learner-centred. Accordingly, m-learning provides teachers with different pedagogies such as educational games, quiz and access to mobile virtual worlds to cater to different learners' needs. Furthermore, m-learning brings many advantages into the classroom such as making study material available to learners anytime and anywhere (Criollo-C et al. 2018).
Lessons that can be drawn from the studies (Alrajawy et al. 2017; Bourgonjon et al. 2010; Criollo-C et al. 2018) are that even though rural high school STEM education is faced with challenges such as lack of learning material and textbooks, teaching and learning styles mismatch, and high rate of learner absenteeism, learners can still benefit from m-learning as they will be able to have easy and fast access to learning material anytime and anywhere. Additionally, m-learning will enable teachers to vary their teaching styles, to meet the learning needs of different learners.
Sánchez-Prietoa et al. (2019) stated that the rate of adoption of m-learning into the classroom is far below the expected level considering the benefits it brings into the classroom. Users' attitude is key for any acceptance of any information system (IS) (Davis 1989). Based on the assessment by Davis (1989), one can argue that the acceptance of m-learning in rural high schools depends on learners' and teachers' attitudes towards it.
A plethora of studies has been conducted to identify factors that affect the acceptance of m-learning (Bourgonjon et al. 2010; Nikou & Economides 2018; Sánchez-Prietoa et al. 2019; Saroia & Gao 2019; Sivo, Ku & Acharya 2018). However, most of these studies focused on tertiary institutions' students (Sánchez-Prietoa et al. 2019; Saroia & Gao 2019; Sivo et al. 2018) and lecturers (Al-dheleai et al. 2019; MacCallum & Jeffrey 2014). It can be urged that for m-learning to be successfully implemented in rural high schools, a lot of acceptance studies need to be carried out. However, very few acceptance studies were carried out in high schools, especially in the rural African context (Bourgonjon et al. 2010; Nikou & Economides 2018).
Despite previous studies conducting investigations on high school teachers and learners' acceptance of m-learning (Bourgonjon et al. 2010; Nikou & Economides 2018; Siyam 2019), these studies focused on the acceptance of mobile assessment (Nikou & Economides 2018), special education (Siyam 2019) and acceptance of digital game-based learning (Bourgonjon et al. 2010). All these studies were carried out in urban areas of developed countries.
Very little is known about the rural school STEM teachers' and learners' acceptance of m-learning. According to Ford and Botha (2010), South Africa should carry out its acceptance studies and should not blindly follow examples from developed countries. Based on the argument thus far, this study sought to examine the rural high schools STEM teachers' and learners' perceptions towards m-learning. This is primarily because, collectively, Nikou and Economides (2018) and Bourgonjon et al. (2010) did not focus on the perceptions of rural high school STEM teachers' and learners' attitude towards m-learning. Additionally, they did not compare teachers' and learners' perceptions of m-learning.
Identifying and understanding factors that rural high school STEM teachers and learners consider important in adopting m-learning is key to its successful implementation. Therefore, this study used the technology acceptance model (TAM) to investigate the factors that influence rural high school STEM learners' and teachers' behavioural intention (BI) to use m-learning for STEM learning. Specifically, this study aimed to give answers to the following research questions (RQs):
RQ1: What is the effect of teachers' and learners' perceived usefulness, perceived ease of use, perceived attitude towards the use, perceived resources (PR), perceived ease to collaborate (PETC) and perceived social influence (PSI) on their behavioural intention to use m-learning?
RQ2: Is there a statistically significant difference between rural based STEM teachers' and learners' acceptance models?
For the study to be able to sufficiently provide answers to these two RQs, this study proposes and validates a hypothetical model that combines psychosocial, behavioural and technology-related elements. The findings of this study may provide more insight on high school teachers' and learners' m-learning acceptance and help policy-makers and the Department of Basic Education (DBE) on how to successfully implement m-learning in rural areas.
Literature review and model development
Technology acceptance model variables
In attempting to identify and understand factors that affect users' acceptance of ISs, several models have been proposed (Davis 1989; Fishbein & Ajzen 1975; Venkatesh et al. 2003; Venkatesh & Davis 2000). However, in the m-learning context, TAM and the Unified Technology of Acceptance and Use Theory (UTAUT) are the commonly used models. Venkatesh et al. (2003) criticised UTAUT for its failure to predict behaviours that are not completely within an individual's volitional control. M-learning can be implemented, and teachers and learners can be forced to use it. As UTAUT cannot predict the behaviours that are beyond an individual's control, it cannot be used in this study. The TAM was selected because it is considered to be robust in predicting users' technology acceptance in many different contexts and is the commonly used model in the study of acceptance of m-learning (Nikou & Economides 2018; MacCallum & Jeffrey 2014; Siyam 2019).
The TAM was developed for elucidation and predicting users' acceptance of IS by examining users' attitudes and beliefs (Davis 1989). The model proposes that perceived usefulness (PU) and perceived ease of use (PEOU) are the main pillars that determine users' attitudes towards the use of an IS. Perceived attitude towards (ATT) the use of an IS to determine BI, which subsequently impacts the actual use of IS (Siyam 2019). Venkatesh et al. (2003) suggested that more variables that are context related should be added to the TAM, to improve its explanatory power of the acceptance of the technology in question (Li et al. 2019).
Behavioural intention to use
Fang, Kayad and Misieng (2019:18) defined BI as, 'the cognitive representation of a person's readiness to perform a given behaviour'. Behavioural intention is considered to be the best single predictor of behaviour (Davis 1989; Venkatesh 2000). In the m-learning context, the study by Joo, Kim and Kim (2016) confirmed the findings of Venkatesh (2000) and Davis (1989) who collectively reported that users' BI predicts the actual usage.
Perceived attitude towards
Siyam (2019) defined attitudes as the user's feelings and views towards a psychological matter. Thoughts and feelings play a very important part in rejecting or accepting an IS. Several studies have found that teachers and learners have positive attitudes towards m-learning (Joo et al. 2016; Osakwe, Nomusa & Jere 2017; Siyam 2019). This study aims at investigating rural-based STEM teachers' and learners' attitudes towards m-learning. The following hypothesis answers the first RQ:
H1: Rural-based STEM teachers' and learners' ATT the use has a positive influence on their BI to use m-learning.
Perceive usefulness
Cheng (2019) defined PU in the m-learning context as a person's perception that using m-learning will improve his or her teaching or learning. One of the main reasons why teachers and learners adopt m-learning is their perception that it will improve teaching and learning (Joo et al. 2016; Osakwe et al. 2017; Siyam 2019). Siyam (2019) studied the effect of special education teachers' PU on their ATT and BI. Siyam (2019) found that special education teachers' PU positively affects their ATT and BI. Their results were also consistent with Alshmrany and Wilkinson (2017) who found that learners' PU directly affects their ATT and BI. If rural-based STEM teachers and learners anticipated improvement of performance in STEM-related subjects as a result of using m-learning, their attitude towards it will be more positive. Hypotheses H2 and H3 are as follows:
H2: Rural-based STEM teachers' and learners' PU significantly and positively affects their ATT the use of m-learning.
H3: Rural-based STEM learners' and teachers' PU significantly and positively affects their BI to use m-learning.
Perceived ease of use
Perceived ease of use was defined as the extent to which an individual believes that adopting a particular IS would be free from effort (Davis 1989). There is some contradiction in the body of knowledge on the effect of PEOU on BI (Saroia & Gao 2019; Siyam 2019). Saroia and Gao (2019) found that PEOU does not necessarily have a direct effect on BI, while Siyam (2019) reported that PEOU has a positive direct effect on BI. Perceived ease of use has a positive effect on PU and ATT (Saroia & Gao 2019). If high school STEM teachers and learners could experience m-learning and find it easy to use, they would be likely to find m-learning useful and develop a positive BI to use m-learning for learning STEM-related subjects. Hypotheses H4-H6 are as follows:
H4: Rural-based STEM teachers' and learners' PEOU has a positive effect on their PU.
H5: Rural-based STEM teachers' and learners' PEOU has a positive effect on their BI to use.
H6: Rural-based STEM teachers' and learners' PEOU has a positive effect on their ATT the use.
Perceived resources
Perceived resources is defined as 'the extent to which an individual believes that he or she has the personal and organisational resources needed to use an IS'. (Mathieson, Peacock & Chin 2001:89). The availability of the resources influences a user's perception of the difficulty or ease of performing a task using an IS (Alshmrany & Wilkinson 2017). In rural high schools, resources needed for m-learning include mobile devices, network connectivity, computer technical support and mobile platforms. Perceived resources was found to have a positive effect on PU, PEOU and ATT (Lim & Khine 2006; Sivo et al. 2018; Teo, Lee & Chai 2008). Lim and Khine (2006) investigated the effects of the availability of resources on teachers' acceptance of information and communication technology (ICT) into the classroom. They found that lack of laptops, computer technical support and support from peers negatively affected the integration of ICT into the classroom. Rural-based STEM teachers' and learners' PR has a significant effect on their PEOU and influence their BI to use m-learning. Without a supportive environment, it is very difficult for rural high school STEM teachers and learners to plan to adopt m-learning, regardless of how much they might like to (Mutambara & Bayaga 2020). Hypotheses H7-H9 are as follows:
H7: Rural-based STEM teachers' and learners' PR has a positive effect on their BI to use m-learning.
H8: Rural-based STEM teachers' and PR has a positive effect on their PEOU.
H9: Rural-based STEM teachers' and PR has a positive effect on their ATT the use.
Perceived social influence
Perceived social influence is similar to the theory of reasoned action's subjective norm (Fishbein & Ajzen 1975:45), which was defined as 'a person's perception that most people who are important to him or her think that he or she should or should not perform the behaviour in question'. In this study, PSI is when rural high school STEM learners and teachers consider the opinion of those who are important to them whether they should or should not use m-learning. Learners and teachers in rural areas are influenced by messages about m-learning. This was suggested by Venkatesh (2000) who stated that people internalise the views of other people and make them part of their belief system. If STEM teachers and learners think that their community, learner's parents and department officials are expecting them to use m-learning, they would have a positive attitude towards m-learning. Hypotheses H10-H12 are as follows:
H10: Rural-based STEM teachers' and learners' PSI has a positive effect on their PU.
H11: Rural-based STEM teachers' and learners' PSI has a positive effect on their ATT to the use of m-learning.
H12: Rural-based STEM teachers' and learners' PSI has a positive effect on their PEOU.
Perceived ease to collaborate
In a collaborative learning environment, learners are encouraged to be interdependent, and every learner is accountable for his or her own and others' learning process (Dillenbourg 1999). This is achieved by giving learners the chance to receive other learners' perspectives and enhance an individual's critical thinking skills by comparing and evaluating opposing viewpoints (Liu 2016). Studies show that m-learning supports collaborative learning, and it enhances individual knowledge development, as well as group knowledge sharing (Bazelais & Doleck 2018; Demir & Akpinar 2018; Padmanathan & Jogulu 2018). When rural-based STEM teachers and learners perceive that it is easy to collaborate in an m-learning environment, they are likely to realise the usefulness of m-learning. Hypothesis H13 is as follows:
H13: Teachers' and learners' PEC has a positive effect on their PU of m-learning.
Based on the theoretical underpinning and what prior studies have established, a hypothetical model is shown in Figure 1. Figure 1 shows the model used in this study to examine rural-based STEM teachers' and learners' acceptance of mobile learning.
Methods
Research design
This study employed a survey design. According to Creswell (2013), a survey design provides a quantitative description of attitudes or opinions of a population by studying a sample of that population. In this study, a survey design was used to provide a quantitative description of rural-based STEM teachers' and learners' attitudes towards mobile learning. The survey design was preferred in this study as it was cheap, and it provides rapid turnaround in data collection. The data were collected at one point in time (cross-sectional survey). A questionnaire was used to collect data. Demographic and opinion-related data were collected from grade 12 STEM teachers and learners using a questionnaire. First, descriptive statistics were used to analyse data from the respondents. Second, partial least squares-structural equation model (PLS-SEM) was used to test the model.
Participants
To collect data, this study adopted stratified random sampling, where all rural high schools in King Ceshwayo District were grouped using their quintiles. To ensure that homogenous elements form a stratum, schools in the same quintile were grouped. Schools in rural areas fall into three quintiles, and thus, three strata were formed. Simple random sampling was then used to select four schools in each stratum. Two hundred grade 12 STEM learners were then shortlisted from the selected schools using simple random sampling. Simple random sampling was also used to select 150 STEM teachers. The selected respondents were given questionnaires and 288 (82%) valid questionnaires were collected. Of the 288 valid questionnaires, 176 (61%) were collected from rural-based STEM learners, and the remaining 112 (39%) were from rural-based STEM teachers. The range of the age of learners was 17 to 21. There were 73 (41%) female STEM learners who took part in the study and the remaining 103 (59%) were male learners.
In this study, 61 (54%) rural-based STEM teachers who responded to the questionnaires were men, while 51 (46%) were women. Of the 112 teachers who participated, 21 (19%) of them were less than 30 years, 28 (25%) were between 30 and 40 years, 43 (38%) were between 40 and 50 years and 20 (18%) were above 50 years old.
Perceived ease of use was the construct with most items. Perceived ease of use had five items. Using Hair et al.'s (2017) recommendation of 10 times larger than the number of items of the construct with most items, the recommended minimum sample size is 50. The sample size of this study exceeds the recommended 50.
Measures
The questionnaire was divided into two sections. Section A required the respondents to fill in their demographical information. In Section B, rural-based STEM teachers and learners answered the main part of the questionnaire, which comprised scales measuring the constructs of the proposed model. Items to measure BI, PEOU and PU were adapted from previously validated and reliable instruments (Alrajawy et al. 2018). To measure ATT, PSI and PR, this study adapted items from Sivo et al. (2018), Siegel (2008) and Venkatesh et al. (2003) and modified them to suit the needs of this study. The items of the construct perceived ease to collaborate (PEC) were newly created in this study. The measurement instrument consists of 7 constructs (BI, PEOU, PU, PR, ATT, PSI and PEC) making a total of 24 items. All items were measured on a 7-point Likert-type scale with 1 corresponding to 'strongly disagree' and 7 to 'strongly agree'.
Analysis technique
Partial least squares structural equation modelling was used to analyse data making use of the software SmartPLS 3. Partial least squares-structural equation model was used for predicting rural-based STEM teachers' and learners' BI to use m-learning and to assess if there was a significant difference between teachers' and learners' acceptance of m-learning. The study followed a two-step approach to model analysis (Hair et al. 2017). First step is the evaluation of reliability and validity of the construct measures. In the next step, the relationships within the inner model was evaluated by assessing the significance of the relationships, predictive power of different variables and explained variance of the dependent variables (Hair et al. 2017).
Ethical consideration
The study received ethical clearance from the University of Zululand Research Ethics Committee. Number: UZREC 171110-030.
Data analysis results
Measurement model assessment
The measurement model describes the association between indicators and the latent variables. Following the suggestion by Hair et al. (2017) of assessing reflectively measurement models, the study examined composite reliability (CR), outer loadings, average variance extracted (AVE) and discriminant validity. First, the factor loadings and CR were used to test for item reliability and convergent validity, respectively. The results (Table 1) showed that almost all outer loadings were higher than 0.7 (Chin 1998) except PSI3 (0.646). The item was not removed because of the exploratory nature of the study and removing it did not increase the CR (Garson 2016). Items that were removed from the model because of having outer loadings lower than 0.7 were: PEOU4, PEOU5, ATT5, PR3 and PEC3. When these items were removed from the model, the CR of their respective constructs increased above the recommended threshold of 0.7 (Hair et al. 2017). The results confirmed item reliability. Composite reliability values show the extent to which the items indicate the latent variable. Table 1 shows that all the CR values exceeded the recommended value of 0.7 (Garson 2016). Second, the AVE values were used to assess convergent validity. Convergent validity assesses the degree to which measures of the same constructs positively correlates with each other (Hair et al. 2017). The AVE values indicate the average commonality for each construct in a reflective model (Chin 1998). All the AVE values were greater than the recommended 0.5 (Garson 2016). Third, the Heterotrait-Monotrait ratio of correlations (HTMT) and the Fornell-Larcker criterion were used to assess discriminant validity. Discriminant validity assesses the degree to which a construct is truly different from other constructs (Hair et al. 2017). Table 2 shows that all the HTMT values were under 0.9, and all the square roots of AVE were higher than the inter-construct correlations (Garson 2016). The results confirm discriminant validity.
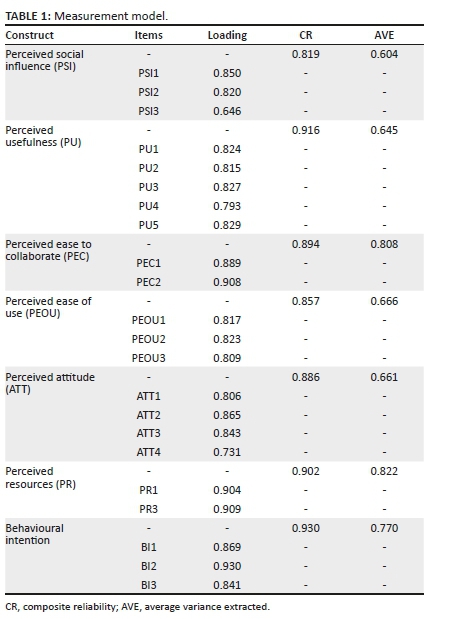
Overall, the indicator reliability, internal consistency reliability, convergent validity and discriminant validity tests conducted on the measurement model were satisfactory.
Structural model assessment
After confirming the suitability of the outer model, the inner model was examined. Before assessing the structural model, the variance inflation factor (VIF) was used to assess multicollinearity issues. Multicollinearity in ordinary least squares regression inflates standard errors, makes significance tests of exogenous latent variables unreliable and makes it difficult to assess the relative importance of one exogenous variable compared to another. The VIF values ranged from 1.715 to 2.196. The VIF values were all less than 4 (Garson 2016) indicating that multicollinearity issues were not going to influence the model results.
Table 3 and Figure 2 summarised the inner model and the hypotheses testing results. Figure 2 shows the R2 of the model. According to Chin (1998), the model explained moderate variances of 48% of perceived attitude towards the use, 60% of PU and 64% of the variance of rural-based STEM learners' and teachers' BI to use m-learning. This means that the total contribution of PEC, PEOU, ATT, PU, PR and PSI on learners' and teachers' BI to accept m-learning was 64%. As recommended by Garson (2016), the significance level of the proposed hypotheses was tested using the bootstrapping procedure with 5000 subsamples, and the results are shown in Table 3. The significant level was set to 0.1 because of the exploratory nature of the study (Garson 2016). The results show that the only relations that were not supported were PR to ATT, PR to BI and PEOU to BI. Furthermore, Table 3 also shows the effect size (f2) of these relations. Three relations (PR to PU, ATT to BI and PEC to PU) had large effect sizes, two relations (PSI to ATT and PU to BI) had medium effect sizes, while the last eight had small effect sizes (Chin 1998). The blindfold method was adopted to assess the predictive relevance of the model (Hair et al. 2017). The q2 values range from 0.248 to 0.568, indicating a medium to large predictive relevance (Garson 2016; Hair et al. 2017). All the q2 values were greater than zero indicating that the model can be used to predict teachers' and learners' acceptance of m-learning. The teachers' and learners' m-learning acceptance structural model consists of seven constructs. Perceived resources and PSI had a direct effect on PU, ATT and PEOU. Perceived ease to collaborate had a direct effect on PU. Perceived usefulness, ATT, PR and PEOU influenced BI.
To answer RQ2, a non-parametric multigroup analysis (MGA) was used to test if there was a significant difference between rural-based learners' and teachers' path coefficients. Table 4 shows the results of MGA.
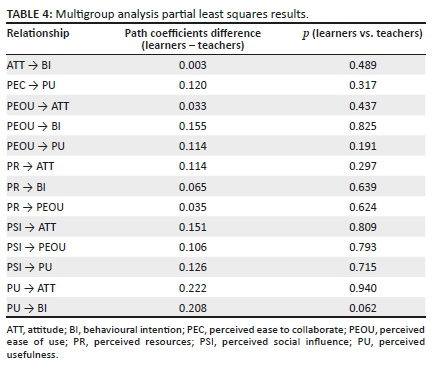
The results showed that all relationships differ insignificantly across the two groups (teachers and learners). This means that the same PLS structural path model applied to both teachers and learners.
Discussion
Research question 1 (RQ1): This study sought to examine the effects of rural-based STEM learners' and teachers' PEC, PSI, PU, PEOU, ATT and PR on their BI to use m-learning for learning STEM. The results showed that the model was appropriate for determining rural high school learners' and teachers' acceptance of m-learning, as it explained 64% of the variance in BI. The variance explained was considered to be moderate (Chin 1998). It was found that all the antecedents predict BI to use m-learning. However, the current results are consistent with the findings of Saroia and Gao (2019) who found that only PU and ATT have a direct effect on BI. A plausible reason might be that rural-based STEM learners' and teachers' BI to use m-learning was reinforced by their positive feelings and the utility of m-learning. Therefore, m-learning platforms need to contain as much learning and assessments material as possible.
Contrary to the findings of Davis (1989), this study found that PEOU (H6: β = 0.301, p < 0.05) predicts ATT, better than PU (H2: β = 0.143, p < 0.05). This shows that rural-based STEM teachers and learners consider the utility less important than the effort required for learning to use m-learning for STEM teaching and learning. This also shows that if m-learning is proved to be easy to use, rural-based STEM teachers and learners are more likely to adopt it for STEM teaching or learning. It is interesting to note that PEOU (H5: β = -0.089, p > 0.05) does not have a direct effect on BI. This might mean that both rural-based STEM teachers and learners do not perceive ease of use as a critical factor they consider important when accepting m-learning. Perceived ease of use has a direct positive influence on both ATT and PU (Venkatesh & Davis 2000). The result that PEOU directly affects ATT is consistent with Saroia and Gao (2019). It is reasonable to infer that the effort needed to learn to use m-learning positively affects rural STEM teachers' and learners' attitude towards the use. Contrary to the findings of Saroia and Gao (2019) findings, PEOU (H4: β = 0.167, p < 0.05) directly influences PU. This means that for both rural-based STEM teachers and learners, the utility of m-learning is promoted by less perceived effort required to learn to use the system. This finding might relate to participants in this study, who were in an examination-class, teaching or learning STEM-related subjects, which are considered difficult. Any m-learning platform that is difficult to learn increases the pressure on them, and the likelihood that they will not utilise it. Therefore, m-learning developers need to develop m-learning platforms that are easy to use.
Perceived social influence had a direct positive effect on PU (H10: β = 0.274, p < 0.05), ATT (H11: β = 0.329, p < 0.05) and PEOU (H12: β = 0.118, p < 0.05). Perceived social influence has already been found to influence PU (Nikou & Economides 2018). Our results imply that when rural-based STEM learners and teachers know that their colleagues, school management, parents and educational authorities approve of and perceive the benefits of m-learning, they perceive it as useful and easy to learn. Additionally, the finding implies that rural-based STEM teachers and learners value the voices of people important to them concerning the learning of STEM using m-learning. Therefore, the Department of Basic Education should provide teachers and learners with an awareness of the potential benefits of m-learning for STEM-related subjects.
The results showed that PR (H8: β = 0.647, p < 0.05) had a positive effect on PEOU, and this result is in-line with the finding of Nikou and Economides (2018). The availability of resources enhances the ease of use of m-learning. It is interesting to note that PR does not affect ATT (H9: β = 0.098, p > 0.05) and BI (H7: β = 0.108, p > 0.05). This means that the scarcity of resources does not affect rural-based STEM teachers' and learners' acceptance of m-learning. A reasonable reason for that is that the respondents were an examination-class, and they perceived the benefits of m-learning more important than the cost involved. Examination-classes are always under pressure to perform and as a result, anything that can improve learners' performance is welcomed. Perceived resources might not have a direct effect on acceptance of m-learning, but rather it has an impact on its actual use. Thus, for a successful implementation of m-learning for STEM learning, resources need to be provided in rural areas.
Perceived ease to collaborate (H13: β = 0.487, p < 0.05) positively influences PU. The usefulness of m-learning is determined by how easy it is for teachers and learners to collaborate. M-learning platforms that enable teachers and learners to easily work together are most likely to be perceived useful.
Research Question (RQ2): Our results showed that there was no significant difference between teachers' and learners' path coefficients. This is in contradiction to the findings of (Osakwe et al. 2017) who found that learners were more positive towards m-learning than their teachers. However, our results showed that the structural model can be used to predict m-learning acceptance for both teachers and learners. This means that teachers and learners consider the same factors when accepting m-learning.
Recommendations
Based on the results of this study, the following recommendations can be made to mobile developers and the DBE:
-
Mobile developers should make m-learning platforms that contain as much STEM learning material and assessment as possible.
-
Additionally, the platforms should be user-friendly. This is primarily because the utility and ease of use are considered important when adopting m-learning by rural-based STEM teachers and learners.
-
The DBE should provide awareness workshops on the usefulness of m-learning for STEM learning.
· Additionally, the DBE should provide the infrastructure that can support m-learning. This is because for both teachers and learners the availability of resources affects their ease of use, which in turn affects their attitude towards and the usefulness of m-learning.
One limitation of this study is that it focused on rural areas only. Consequently, the generalisation of the findings of this study to all high schools both in rural areas and urban should be done with caution. Future studies should replicate this study in urban areas and compare the findings. It will be interesting to carry the same study in the same area but using learners and teachers of other subjects that are not STEM-related and considering other classes which are not an examination class.
Conclusion
The model explained 64% of rural high school STEM teachers' and learners' BI to use m-learning. The results confirm the findings of Davis (1989) that learners' and teachers' PEOU influences both ATT and PU, which in turn affect their BI. Furthermore, the results support the suggestion by Venkatesh et al. (2003) who proposed that external variables of TAM need to be identified and examined to ensure that TAM is a feasible model for the context. In this study, PSI, PEC and PR were added to TAM. The results showed that the TAM can be used to predict the acceptance of m-learning. Additionally, the added variables had an indirect effect on rural-based STEM teachers' and learners' BI to use m-learning. According to Garson (2016) predictive relevance; q2 values of PSI, PEC and PR were considered large, meaning that the added constructs are important in predicting rural-based STEM learners' and teachers' adoption of m-learning in rural areas. The lessons that can be drawn from this study are that rural high school STEM teachers' and learners' needs are similar when it comes to the adoption of m-learning. Teachers and learners consider the utility and attitude towards the use as the most important factors when adopting m-learning. Furthermore, awareness campaigns, infrastructure, mobile devices and data need to be made available for mobile learning to be successfully adopted in rural areas.
Acknowledgements
The authors would like to thank Constance Chiza and Nenyasha Mutambara for their support and encouragement.
Competing interests
The authors have declared that no competing interests exist.
Author's contributions
All authors contributed equally to this work.
Funding Information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The datasets generated during and/or analysed during this study are available from the corresponding author on reasonable request.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Al-dheleai, Y.M., Baki, R., Tasir, Z. & Al-rahmi, W.M., 2019, 'What hinders the use of ICT among academic staff at Yemen's public universities?', International Journal of Humanities and Innovation (IJHI) 2(1), 7-12. https://doi.org/10.33750/ijhi.v2i1.30 [ Links ]
Alrajawy, I., Daud, N.M., Isaac, O. & Mutahar, A.M., 2017, 'Examine factors influencing the intention to use mobile learning in Yemen public universities', Asian Journal of Information Technology 16(2), 287-297. [ Links ]
Alshmrany, S. & Wilkinson, B., 2017, 'Factors influencing the adoption of ICT by teachers in primary schools in Saudi Arabia', Education (Mohe) 27, 143-156. https://doi.org/10.14569/IJACSA.2017.081218 [ Links ]
Alrajawy, I., Isaac, O., Ghosh, A., Nusari, M., Al-Shibami, A.H. & Ameen, A.A., 2018, 'Determinants of Student's intention to use Mobile learning in Yemeni public universities: Extending the technology acceptance model (TAM) with anxiety', International Journal of Management and Human Science 2(2), 1-9. [ Links ]
Bazelais, P. & Doleck, T., 2018, 'Investigating the impact of blended learning on academic performance in a first semester college physics course', Journal of Computers in Education 5(1), 67-94. https://doi.org/10.1007/s40692-018-0099-8 [ Links ]
Bosman, A. & Schulze, S., 2018, 'Learning style preferences and Mathematics achievement of secondary school learners', South African Journal of Education 38(1), 1-8. https://doi.org/10.15700/saje.v38n1a1440 [ Links ]
Bourgonjon, J., Valcke, M., Soetaert, R. & Schellens, T., 2010, 'Students' perceptions about the use of video games in the classroom', Computers and Education 54(4), 1145-1156. https://doi.org/10.1016/j.compedu.2009.10.022 [ Links ]
Cheng, E.W., 2019, 'Choosing between the theory of planned behavior (TPB) and the technology acceptance model (TAM)', Educational Technology Research and Development 67(1), 21-37. https://doi.org/10.1007/s11423-018-9598-6 [ Links ]
Chin, W.W., 1998, The partial least squares approach for structural equation modeling, Lawrence Erlbaum Associates, Hillsdale, NJ.
Creswell, J.W., 2013, Research design: Qualitative, quantitative, and mixed methods, Sage, Los Angeles, CA.
Criollo-C, S., Luján-Mora, S. & Jaramillo-Alcázar, A., 2018, 'Advantages and disadvantages of M-learning in current education', in 2018 IEEE World Engineering Education Conference (EDUNINE), pp. 1-6, March, IEEE.
Davis, F.D., 1989, 'Perceived usefulness, perceived ease of use, and user acceptance of information technology', MIS Quarterly 13(3), 319-340. https://doi.org/10.2307/249008 [ Links ]
Demir, K. & Akpinar, E., 2018, 'The effect of mobile learning applications on students' academic achievement and attitudes toward mobile learning', Malaysian Online Journal of Educational Technology 6(2), 48-59. https://doi.org/10.17220/mojet.2018.02.004 [ Links ]
Dillenbourg, P. (ed.), 1999, 'What do you mean by collaborative learning?', in Collaborative learning: Cognitive and computational approaches, pp. 1-19, Elsevier, Oxford.
Fang, C.S.O.Y., Kayad, F. & Misieng, J., 2019, 'Malaysian undergraduates' behavioural intention to use LMS for online English learning: An extended Self-Directed Learning Technology Acceptance Model (SDLTAM)', Journal of ELT Research 4(1), 8-25. https://doi.org/10.22236/JER_Vol4Issue1pp8-25 [ Links ]
Fishbein, M. & Ajzen, J., 1975, Beliefs, attitudes, intention, and behavior: An introduction of theory and research reading, Addison Wesley Publishing, Reading, MA.
Force, S.T., 2014, Innovate: A blueprint for science, technology, engineering, and mathematics in California public education, Californians Dedicated to Education Foundation, Dublin, CA.
Ford, M. & Botha, A., 2010, 'A pragmatic framework for integrating ICT into education in South Africa', in 2010 IST-Africa, May 19, 2010, pp. 1-10, IEEE, Durban, South Africa.
Garson, G.D., 2016, Partial least squares: Regression & structural equation models, Statistical Publishing Associates, Asheboro, NC.
Hair, J.F., Hult, G.T.M., Ringle, C.M. & Sarstedt, M., 2017, A primer on partial least squares structural equation modeling (PLS-SEM), Sage Publications, Los Angeles, CA.
Joo, Y.J., Kim, N. & Kim, N.H., 2016, 'Factors predicting online university students' use of a mobile learning management system (m-LMS)', Educational Technology Research and Development 64(4), 611-630. https://doi.org/10.1007/s11423-016-9436-7 [ Links ]
Li, R., Meng, Z., Tian, M., Zhang, Z., Ni, C. & Xiao, W., 2019, 'Examining EFL learners' individual antecedents on the adoption of automated writing evaluation in China', Computer Assisted Language Learning 32(7), 784-804. https://doi.org/10.1080/09588221.2018.1540433 [ Links ]
Lim, C.P. & Khine, M., 2006, 'Managing teachers' barriers to ICT integration in Singapore schools', Journal of Technology and Teacher Education 14(1), 97-125. [ Links ]
Liu, S.H., 2016, 'The perceptions of participation in a mobile collaborative learning among pre-service teachers', Journal of Education and Learning 5(1), 87-94. https://doi.org/10.5539/jel.v5n1p87 [ Links ]
MacCallum, K. & Jeffrey, L., 2014, 'Factors impacting teachers' adoption of mobile learning', Journal of Information Technology Education 13, 141-162. https://doi.org/10.28945/1970 [ Links ]
Mathieson, K., Peacock, E. & Chin, W.W., 2001, 'Extending the technology acceptance model: The influence of perceived user resources', ACM SIGMIS Database: The DATABASE for Advances in Information Systems 32(3), 86-112. https://doi.org/10.1145/506724.506730 [ Links ]
Mboweni, L., 2014, 'Challenges and factors contributing to learner absenteeism in selected primary schools in Acornhoek', Doctoral dissertation, University of South Africa. [ Links ]
Mutambara, D. & Bayaga, A., 2020, 'Understanding rural parents' behavioral intention to allow their children to use mobile learning', in Conference on e-Business, e-Services and e-Society, April 06, 2020, pp. 520-531, Springer, Cham.
Nikou, S.A. & Economides, A.A., 2018, 'Mobile-based micro-learning and assessment: Impact on learning performance and motivation of high school students', Journal of Computer Assisted Learning 34(3), 269-278. https://doi.org/10.1111/jcal.12240 [ Links ]
Osakwe, J.O., Nomusa, D. & Jere, N., 2017, 'Teacher and learner perceptions on mobile learning technology: A case of Namibian high schools from the Hardap Region', Online Submission 1(1), 13-41. https://doi.org/10.26762/he.2017.30000002 [ Links ]
Padmanathan, Y. & Jogulu, L.N., 2018, 'Mobile learning readiness among Malaysian Polytechnic students', Journal of Information Systems and Technology Management 3(8), 113-125. [ Links ]
Sánchez-Prieto, J.C., Hernández-García, Á., García-Peñalvo, F.J., Chaparro-Peláez, J. & Olmos-Migueláñez, S., 2019, 'Break the walls! Second-order barriers and the acceptance of mLearning by first-year pre-service teachers', Computers in Human Behavior 95, 158-167. https://doi.org/10.1016/j.chb.2019.01.019 [ Links ]
Saroia, A.I. & Gao, S., 2019, 'Investigating university students' intention to use mobile learning management systems in Sweden', Innovations in Education and Teaching International 56(5), 569-580. https://doi.org/10.1080/14703297.2018.1557068 [ Links ]
Siegel, D.M., 2008, 'Accepting technology and overcoming resistance to change using the motivation and acceptance model', Doctor of Philosophy, University of Central Florida. [ Links ]
Sivo, S.A., Ku, C.H. & Acharya, P., 2018, 'Understanding how university student perceptions of resources affect technology acceptance in online learning courses', Australasian Journal of Educational Technology 34(4), 72-91. https://doi.org/10.14742/ajet.2806 [ Links ]
Siyam, N., 2019, 'Factors impacting special education teachers' acceptance and actual use of technology', Education and Information Technologies 24(3), 2035-2057. https://doi.org/10.1007/s10639-018-09859-y [ Links ]
Teo, T., Lee, C.B. & Chai, C.S., 2008, 'Understanding pre-service teachers' computer attitudes: Applying and extending the technology acceptance model', Journal of Computer Assisted Learning 24(2), 128-143. https://doi.org/10.1111/j.1365-2729.2007.00247.x [ Links ]
Venkatesh, V., 2000, 'Determinants of perceived ease of use: Integrating control, intrinsic motivation, and emotion into the technology acceptance model', Information Systems Research 11(4), 342-365. [ Links ]
Venkatesh, V. & Davis, F.D., 2000, 'A theoretical extension of the technology acceptance model: Four longitudinal field studies', Management Science 46(2), 186-204. https://doi.org/10.1287/isre.11.4.342.11872 [ Links ]
Venkatesh, V., Morris, M.G., Davis, G.B. & Davis, F.D., 2003, 'User acceptance of information technology: Towards a unified view', MIS Quarterly 27(1), 425-478. https://doi.org/10.1287/mnsc.46.2.186.11926 [ Links ]
Visser, M., Juan, A. & Feza, N., 2015, 'Home and school resources as predictors of mathematics performance in South Africa', South African Journal of Education 35(1), 1-10. https://doi.org/10.15700/201503062354 [ Links ]
 Correspondence:
Correspondence:
Anass Bayaga
bayagaa@unizulu.ac.za
Received: 06 Feb. 2020
Accepted: 24 June 2020
Published: 18 Sept. 2020
ORIGINAL RESEARCH
Digitalisation strategies in a South African banking context: A consumer services analysis
Candice Louw; Cecile Nieuwenhuizen
Johannesburg Business School, College of Business and Economics, University of Johannesburg, Johannesburg, South Africa
ABSTRACT
BACKGROUND: In the advent of the fourth industrial revolution, Internet-only/digital-only banks are offering alternative approaches to facilitating online transactions and banking in the absence of physical branches. As a result, traditional, offline banks may possibly experience increased pressure in growing and retaining their customer base.
OBJECTIVES: The objective of this study is to understand the fundamental differences between traditional and digital-only banks' business models and digital user experience strategies from a consumer services perspective. As a result, in this research, we established to what extent traditional South African banks have embraced service digitalisation and compared this to the services offered by South Africa's first digital-only bank (launched in early 2019).
METHOD: By means of convenience sampling, we selected the five biggest traditional banks and the first digital-only bank in South Africa (as recorded at the start of July 2019) and conducted a comparative analysis of the core digital services that were offered to consumers.
RESULTS: Overall, mobile-optimised services were identified as a key digital business strategy, thereby highlighting the importance of a mobile-first approach not only to traditional and digital-only banking services strategies but also to digital business model formulation in general.
CONCLUSION: While the overall South African banking landscape and banking user experience may be moving towards digital-first and mobile-first, the need for access to banking technology and services 7 days a week necessitate not only mobile-first, but accessible-foremost (i.e. access to infrastructure that facilitates access to online banking technologies, both remotely and on premise) banking business models.
Keywords: digital banking; digitalisation; online banking; mobile banking; user experience; consumer services.
Introduction and literature review
With the growth and increased adoption of the Internet and online technologies over the past few decades, many opportunities for business digitalisation and new digital business model formulation have arisen (Louw & Nieuwenhuizen 2019). As a result, businesses worldwide are being reinvented and reconfigured with the advent of the Fourth Industrial Revolution (4IR), with banks being no exception to the rule.
Banking consumer services (i.e. services that are delivered to consumers through digital channels such as websites, Internet banking portals and smartphone applications [apps]) in particular are becoming increasingly more reliant on technology. There is a chance that banks may miss out on the value benefits as offered by traditional human (in-person) connects, facilitated by the traditional business models that necessitate customers visiting a bank branch (Kulkarni & Dambe 2019). Moreover, the unique characteristics of digital services imply that there exist different consumer evaluation processes from those used when assessing tangible goods (Hill 1986).
As such, organisations are realising that the intangible aspects of a relationship that are facilitated through digital channels and services are not easily duplicated by competition, thus providing a sustainable competitive advantage (Roberts, Varki & Brodie 2003). When focussing on banking consumer services in particular, value outcomes (tangible as well as ones perceived by consumers) become key pillars upon which the business subsequently stands (Kulkarni & Dambe 2019). A business model that caters to diverse human characteristics and values (through digital channels) becomes a key factor for consideration during the digitalisation process of a bank's consumer services (Kulkarni & Dambe 2019).
Based on this observation, it is arguable that digital technologies are fundamentally changing the global banking industry by blurring the traditional lines that define product, market and customer base (Pyun, Scruggs & Nam 2002), thereby liberating and harmonising financial systems on a global scale (Mercieca, Schaeck & Wolfe 2007). As a result, when setting banks against a background of far-reaching structural change and technological enhancement, their responses to the changing competitive environment most often include seeking out diversification, vertical product differentiation and consolidation (Goddard et al. 2007).
In certain instances, however, new technologies and services may threaten replacing traditional banks in their entirety. Internet- or digital-only banks offer alternative approaches to online transacting and banking by making services available exclusively through online channels (websites) or by means of smartphone apps, thereby challenging traditional banking business models by eliminating the need to establish and maintain physical bank branches. Technology has fundamentally altered the creation, delivery, reception and utilisation of these financial products (Pyun et al. 2002), with convenience and economic efficiency already having had positive effects on consumers' adoption intention and continuance intention of international digital-only banks (Lee & Kim 2020).
In response to this, and with the advent of the 4IR, traditional (offline) banks may arguably experience increased pressure in growing and retaining their customer base while also addressing the heterogeneity expected by customers by means of digitalisation of consumer services (Pallant, Sands & Karpen 2020). As a result, the continuous adoption of innovative offline, online and mobile value-added services is core to ensuring customer satisfaction, retention and arguably business continuity (Goddard et al. 2007).
With the rapid pace of technological evolution, making the correct choice of digital platforms and tools to implement becomes critical to ensuring widespread user adoption, acceptance and overall success (Louw & Nieuwenhuizen 2019). There is, however, an inherent risk (most notably from a cyber and information security perspective) when adopting new technologies or tools. As first and fast movers accept and manage this risk, more pressure may be placed on competitors to follow suit (Roberts et al. 2003). As more key industry stakeholders begin to adopt similar technology-first initiatives, trends may arise, thereby ultimately defining customer expectation.
Despite the aforementioned perceived risks, digital-only banks challenge the status quo in the traditional banking industry through launching new and more affordable products into the market because of lower running costs achieved by outsourcing operational premises to affiliates (such as supermarkets) with existing infrastructure and a wide reach (Business Tech 2019a; Kulkarni & Dambe 2019). By leveraging the opportunities of outsourcing major infrastructure in this way, the provision of bank accounts that require very little to no monthly maintenance fees is, in turn, possible. The growth of these unexpected players emerging in the financial services industry has subsequently created a 'marketplace without boundaries' (Camarante & Brinckmann 2017). This implies that non-traditional players are increasingly exploring new opportunities, enabling them to challenge incumbents and continually changing the state of financial services in South Africa (Camarante & Brinckmann 2017).
It is thus arguable that traditional banking business models (that predominantly require clients to visit a physical branch) as whole are being challenged; however, because of the very recent (in 2019) introduction of the digital-only banking concept in South Africa, very little to no research literature is available on the topic from a South African perspective.
To address this shortcoming in existing South African research literature, we survey the South African banking landscape and analyse the trends in digital consumer services on offer from a selection of traditional, offline banks. We subsequently compare our findings with the services offered by the first South African digital-only bank launched in 2019, noting the expectations of consumers and the differences in business models from a consumer services perspective (i.e. services that are delivered to consumers through digital channels such as websites, Internet banking portals, smartphone applications, mobile banking and also services that facilitate process digitisation such as point of sale [POS] devices that may be used to process digital payments) across both types of banks.
This research is novel in its kind as the concept of a digital-only bank in South Africa is still a very recent introduction (launched in 2019). The value of the research stems from the fact that early trend analysis and identification in a South African context, supported by technological advancement, is sure to liberate the digital banking landscape to a further extent, thereby providing guidance and supporting the development of further digital-only banking services and initiatives not only within South Africa (by analysing trends and encouraging further development), but possibly also on a global scale. This may further advance and contribute to the theory on digital business model formulation from a South African perspective.
These observations subsequently support the formulation of our research aim (RA), which was to determine if there were similarities between traditional and digital-only South African banks' digitalisation efforts from a consumer services perspective. This includes services that are delivered to consumers through digital channels such as websites, Internet banking portals, smartphone applications, mobile banking and also services that facilitate process digitisation such as POS devices (terminals that may be used to process digital payments).
To address our RA, we identified two research questions (RQs):
-
Research question 1 (RQ1) - Which digital consumer services are offered by traditional South African banks?
-
Research question 2 (RQ2) - Which digital consumer services are offered by digital-only South African banks?
The rest of the article is organised as follows: We begin with a discussion on the chosen research method and design, followed by a presentation of research results. This is followed by an interpretive discussion section, while the conclusion is found in the last section.
An overview of the chosen research method and design follows next.
Research method and design
Per analysis of the South African banking industry, it was noted that in February 2019, South Africa recorded 19 registered banks, four mutual banks, four co-operative banks, 15 local branches of foreign banks and 30 foreign banks with approved local representative offices (South African Reserve Bank Prudential Authority 2019). Although there is a strong representation of both locally and internationally owned traditional banks, 2019 saw the country's first fully licensed digital-only bank launched into the market in February (Business Tech 2019a).
By analysing the total population of traditional banks in South Africa, a non-probability sampling method was chosen to select a sample of five traditional banks and one digital-only bank that were operational in February 2019. By means of convenience sampling, the five biggest 'traditional' banks in South Africa (hereafter collectively referred to as 'traditional banks') were subsequently chosen in February 2019 (Business Tech 2019b), as well as the first digital-only bank in South Africa. Although some of the chosen traditional banks that form part of the sample may be foreign-owned, the focus of this study was on including the banks that are favoured by a majority of South African consumers, regardless of the bank's origin and/or ownership.
Through further qualitative analysis and individual inspection of secondary data, a combination of online and offline sources (including research databases, publications, printed material, bank websites, online resources, digital publications and smartphone application-hosting platforms) were consulted on a first-hand basis to identify the digital consumer services offered by each bank. Data and results obtained for each bank were tabulated, commonalities and differences were identified and the results were consolidated into a single table. From a reliability and validity perspective, it was confirmed that the selected banks and services were still operational and delivered at the end of the second quarter of 2019 (i.e. end of June 2019), thereby justifying their inclusion in the sample.
By means of a comparative analysis, similarities (resulting in trends) and differences (identifying possible opportunities) in digital consumer services offerings were identified, noted and summarised by comparing the traditional banks with each other and also by comparing the traditional banks with the digital-only bank. As a result, the findings from the analysis from the comparative analysis of both traditional banks with traditional banks, and traditional banks with the digital-only bank, were tabulated separately. The presentation and discussion of these results follows in more detail next.
Ethical consideration
This article followed all ethical standards for research without direct contact with human or animal subjects.
Results
As traditional banks have been around longer than digital-only banks, the analysis of digital services offered to consumers by traditional banks is discussed firstly.
As web banking technologies are certainly crucial to banks to be found in the digital age, it is imperative to have a web presence (Louw & Nieuwenhuizen 2020). South African banks have subsequently ensured that they are visible online, with all five banks (100%) having implemented a website.
With a great variety of different Internet-enabled devices being capable of accessing websites, ensuring that bank websites are optimised for accessibility on any device becomes important (Louw 2017). As such, all five banks have opted for a responsive website design that allows their particular website to adjust to the width of the screen of the device it is being viewed on. This makes it easier to find important information, regardless of whether the website is viewed on a smartphone, tablet or computer screen. Optimising a website's layout to be responsive to the device it is being viewed on can be performed automatically (four out of five banks) or manually (one out of five banks) by the end user (depending on the device they have chosen to view the website on) through selection of on-screen options.
Once a user can find a bank's website, they may also be inclined to conduct their actual banking online. The demand for this is reflected by Internet banking services being offered by all five banks (100%).
When moving away from web technologies and focussing on mobile and smartphone technologies, banking smartphone applications (apps) for Android and iOS devices are provided by all five banks (100%). Additionally, three out of five banks provide an app for Windows Phone devices, although three out of five banks also provide an app for BlackBerry devices. At a bare minimum, a smartphone app that is supported by at least two major platforms, most notably Android and iOS, is provided by each bank.
All five banks (100%) also offer their smartphone app as a zero-rated data app which means that no data usage costs will be incurred (as agreed upon by Internet service providers and mobile network providers) for end users when making use of the app to conduct their banking (Futter & Gillwald 2015). This is arguably a major benefit of making use of smartphone apps in an environment where broadband data are still relatively expensive (Geerdts et al. 2016), and this offers further incentive for banks to adopt a mobile-first strategy.
To make use of any of these smartphone apps, however, end users would need to be in possession of a supported smartphone. As smartphones are typically more expensive than feature phones (especially in developing economies such as South Africa) and in certain cases may also be perceived as being more complicated to use (thereby defining an undesirable user experience, i.e. the overall experience of a person using a product and determining how easy or pleasing it is to use) than feature phones, users may choose to not be in possession of a smartphone (Louw & Von Solms 2018; Louw 2017; User Experience n.d.). This choice thereby excludes these users from making use of the smartphone app features on offer. Fortunately, however, mobile banking via unstructured supplementary service data (USSD) has been adopted by all five banks (100%). This makes mobile banking possible to those who do not possess a smartphone (and subsequently cannot download a mobile app onto their device), but are in possession of a more basic mobile or feature phone instead (which allows them to access banking services through dialling dedicated mobile banking numbers by means of their device's keypad and interacting with on-screen prompts). This ensures that a wide spectrum of users may benefit from the conveniences offered by South African banks through a mobile phone.
When exploring further opportunities that smartphones have to offer in a traditional South African banking context, POS technologies become of particular interest. A mobile POS system that can connect to a supported smartphone may further open up a world of small business prospects for entrepreneurs. This may not only assist with digitising informal trading, but also enhance an emerging economy by embracing a safer, cashless society. As it currently stands, however, only three out of the five banks (60%) have this service available. Fortunately, for larger organisations, all banks (100%) offer a standard POS system that they may make use of to process payments.
Overall, mobile- or smartphone-first banking does seem to be a strongly pursued component of the digital transformation trend in South African banks. This is evident from Table 1, where seven digitalisation items are identified, six of which are either directly or indirectly optimised for usage with a smartphone. These include a responsive website and Internet banking, a smartphone app, USSD banking, zero-rated smartphone apps and a smartphone-powered POS device.
From the discussion and data presented in Table 1, three major categories of technologies can be identified including:
1. web banking technologies (website, Internet banking)
2. smartphone banking technologies (smartphone applications, mobile or USSD banking, zero-rated data)
3. point of sale banking technologies (smartphone POS and standard POS).
Moreover, from these three major categories that were identified, that is, web banking technologies (website, Internet banking), smartphone banking technologies (smartphone applications, zero-rated data, mobile or USSD banking) and POS banking technologies (smartphone POS and POS), a smartphone-related element or optimisation is present in each. This is summarised in Table 2.
Although not all banks offer all of the listed products and some may only offer a subset thereof, an undeniable mobile-first trend can be identified in each bank's case. This is further exasperated by the '#datafree' movement that allows certain apps, including banking apps, to be listed as zero-rated (i.e. not incurring data usage and download costs when transacting on the app to make mobile banking more affordable and accessible to all) on most major local network providers (Futter & Gillwald 2015).
As smartphones are typically more expensive than feature phones and in certain cases may be perceived as being more complicated to use than feature phones (Louw 2017), users may choose to not be in possession of a smartphone. As such, banking through USSD ensures that users with more basic feature phones are also able to benefit from the conveniences offered by the mobile-first banking movement. As previously recorded in other industries, this suggests that local market circumstances - such as Internet penetration and mimicking behaviour - play a major role (Bleyen & Van Hove 2007).
This observation is specifically applicable in the South African banking context with all (100%) banks having chosen to support Android and iOS smartphone apps - the two most popular smartphone operating systems (OSs) not only in South Africa and Africa, but also in the world (Statcounter Global Stats 2019). This is an important aspect to take into account when possibly considering expansion into further markets. Mobile-first, localised banking services will arguably thus play an increasingly important role in the consumer banking industry going forward and form an integral part of any bank's overall customer experience.
With a thorough understanding of traditional banks' digital services on offer, we now revisit RQ1 (which digital consumer services are offered by traditional South African banks?) by stating that traditional banks have embraced digital service technologies specifically from a consumer services perspective by delivering a selection of web banking technologies, smartphone banking technologies and POS banking technologies. The majority of these services have notably also been optimised for use with mobile and smartphone devices.
The digital-only bank's consumer services are subsequently summarised in Table 3.
With a better understanding of the digital-only bank's digital services on offer, we now revisit RQ2 (which digital consumer services are offered by digital-only South African banks?) by stating that the first digital-only bank has embraced digital service technologies specifically from a consumer services perspective by delivering predominantly web banking technologies and smartphone banking technologies.
As a result, we now address the RA (to determine if there were similarities between traditional and digital-only South African banks' digitalisation efforts from a consumer services perspective) by noting that in both cases, web banking technologies and smartphone banking technologies are not only a similarity, but also a priority. Both of these approaches arguably facilitate banking anytime, anywhere. This, in turn, highlights the elements of convenience and economic efficiency that have been found to have positive effects on consumer's adoption intention and continuance intention of digital services (Lee & Kim 2020) to hold true in a South African context too.
In the case of both the digit-only bank as well as the traditional banks in South Africa, the move to mobile applications to facilitate convenient consumer services delivery is thus undeniable. These results certainly highlight the early trends, arguably also defining minimum requirements for further market liberalisation and possible new market entrants. A discussion on these and other business implications follows in more detail next.
Discussion
Key findings from this research indicate that at the end of the second quarter of 2019, all participating traditional banks offered users access to the bank's website (responsive design), Internet banking services (via the aforementioned website), access to (at least) an Android and iOS smartphone app, local, zero-rated data rights for these smartphone banking apps, mobile banking via USSD options and POS systems.
A similar approach has been followed by South Africa's first digital-only bank with emphasis (early in the race) being on making access available to the bank's website (responsive design), Internet banking services (via the aforementioned website), access to an Android smartphone app (possibly because of Android currently being the most popular OS worldwide [Statcounter Global Stats 2019]) and local, zero-rated data rights for this smartphone banking app.
By revisiting our RA (to determine if there were similarities between traditional and digital-only South African banks' digitalisation efforts from a consumer services perspective), it is possible to note that in both the cases of the traditional banks and the digital-only bank, mobile-optimised services were identified as a key digital business strategy thereby highlighting the importance of a mobile-first approach to not only banking services, in particular, but also digital business model formulation in general. This can be seen as the primary, practical implication resulting from this study.
This research has arguably thus achieved what was originally aimed for, with the research findings arguably also supporting the earlier discussion which indicated that with the advent of the 4IR, traditional (offline) banks may arguably experience increased pressure in growing and retaining their customer base while also addressing the heterogeneity expected by customers by means of digitalisation of consumer services (Pallant et al. 2020). From a South African banking perspective, however, mobile-optimised services including a responsive website, Internet banking facilities and a smartphone application (for at least Android and iOS devices) are what consumers expect at a minimum.
Despite mobile-optimised services arguably playing a big role in not only digital banking, but also general digital business model formulation going forward, mobile-first initiatives may, however, be perceived differently by different generations of users as follows (Murphy 2018):
-
Generation Z, or the digital age, are digital natives that usually prefer interactions through mobile.
-
Generation X, or the optimist, are ready to learn how to use and interact through digital and mobile channels.
-
Baby boomers, or pragmatists, are open to using digital channels and interacting through them to see if it is an improved experience.
-
Senior users (older generations), often referred to as the digital doubters, prefer more traditional banking interactions (such as going to a physical branch), but will try digital for certain activities if it proves to be helpful and easy enough.
As such, banks that are pursuing major digital- and mobile-first transformations should ensure that the needs of the full spectrum of customers are taken into account and consider delivering level-appropriate training and awareness to not intimidate or overwhelm non-technical customers such as seniors or digital doubters (Louw 2017). Although digitalisation might not necessarily prove to be a perfect solution for all generations of customers (especially seniors or digital doubters), mobile- or smartphone-first banking does seem to be a strongly pursued component of the digital transformation trend in South African banks as a whole.
As mentioned previously, however, technology (such as smartphones, tablets and phablets) to access these services are typically more expensive and may be perceived as intimidating or overwhelming from a user experience perspective (Louw & Von Solms 2018; Louw 2017). Users who are not in possession of such devices may therefore be excluded from making use of digital banking features and services.
Dedicated access to infrastructure (such as a branch, technology devices, etc.) that allows access to digital banking facilities should thus not be completely disregarded in the move to digital. This has been acknowledged by a traditional South African bank that has experienced the most growth over the past 5 years - not only is it the youngest entrant to the market and offers fewer services than what its traditional bank competitors offer, but it also provides consumers access to selected dedicated branches 7 days a week as opposed to the 6 days a week that most competitors offer (bank number 2 in Table 1). Similarly, although the digital-only bank does not have any physical bank branches, access to digital banking technology infrastructure is available 7 days a week at selected affiliate supermarkets' premises.
In both the cases of the new entrant traditional bank and the digital-only bank, fewer services are offered than those of some competitors (see bank 2 in Table 1 and bank D1 in Table 2), but prolonged hours of access to infrastructure that encourages the use of the respective banks' banking services may (speculatively) be providing a competitive edge.
These findings are, however, limited to only a select few South African banks and may not be representative of the South African banking landscape in its entirety - a limitation of this research. Despite this limitation, our research findings arguably imply that mobile-first, localised banking services are playing an increasingly important role in digital consumer banking.
Furthermore, while the overall South African banking landscape may be moving towards digital- and mobile-first, the need for physical access to technology and services, whether because of circumstance (lack of funds or resources) or by choice (technology avoidance), may necessitate not only mobile-first, but also accessible-foremost banking business models (i.e. 7 days a week, on-premises access to infrastructure and support that facilitates access to online banking technologies).
Conclusion
With the advent of the 4IR, many industries, including the banking industry, consider pursuing digitalisation across their business models and services to remain relevant. Traditional South African banks have acknowledged this fact by offering consumers access to their bank's website (responsive design), Internet banking services (via the aforementioned website), access to (at least) an Android and iOS smartphone app, local, zero-rated data rights for these smartphone banking apps, mobile banking via USSD options and POS systems.
South Africa's first digital-only bank has followed suit and provided consumers access to the bank's website (responsive design), Internet banking services (via the aforementioned website), access to an Android smartphone app and local, zero-rated data rights for users making use of this smartphone banking app.
Although digitalisation might not necessarily prove to be a perfect solution for certain generations of customers (often referred to as digital doubters), mobile- or smartphone-first banking does seem to be a strongly pursued component of the digital transformation trend in South African banks. This arguably implies that a mobile-first user experience design across all digital channels is key to remain relevant with the advent of the 4IR. Furthermore, while the overall South African banking landscape may be moving towards digital- and mobile-first, the need for physical access to technology and services, whether because of circumstance (lack of funds or resources) or by choice (technology avoidance), may necessitate not only digital- and mobile-first, but accessible-foremost banking business models (i.e. 7 days a week, on-premises access to infrastructure and support that facilitates access to online banking technologies).
Despite the research being limited to only a select few South African banks and not necessarily being representative of the South African banking landscape in its entirety, the value of the research stems from the fact that early trend analysis and identification is sure to liberate the digital banking landscape to a further extent, thereby supporting the development of more digital-only services and digital-related entrepreneurial initiatives on a broader scale. This research has contributed to understanding the trends in South African digital banking, specifically from a consumer services perspective.
Future work could include focussing on analysing the entire South African banking population (and not just a sample) to provide a more holistic view of trends and expectations across all traditional and digital-only banks that operate in the country. This may be followed by conducting similar studies for international banks, thereby offering an opportunity to identify global digital banking trends.
Acknowledgements
The authors would like to thank Brenda Lotriet Louw for proofreading this article.
Competing interests
The authors declare that they have no financial or personal relationships that may have inappropriately influenced them in writing this article.
Authors' contributions
All authors contributed equally to this work.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The authors confirm that the data supporting the findings of this study are available within the article.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Bleyen, V. & Van Hove, L., 2007, 'Western European newspapers and their online revenue models: An overview', First Monday, The Peer-Reviewed Journal on the Internet 12(12), 1-13. https://doi.org/10.5210/fm.v12i12.2014 [ Links ]
Business Tech, 2019a, These are the banks South Africans are most satisfied with, viewed 06 September 2019, from https://businesstech.co.za/news/banking/303548/these-are-the-banks-south-africans-are-most-satisfied-with/.
Business Tech, 2019b, Battle of the banks: South Africa's big 5 banks compared, viewed 08 September 2019, from https://businesstech.co.za/news/banking/339319/battle-of-the-banks-south-africas-big-5-banks-compared/.
Camarante, J. & Brinckmann, S., 2017, A marketplace without boundaries. The future of banking: A South African perspective, viewed 26 August 2019, from https://www.pwc.co.za/en/assets/pdf/strategyand-future-of-banking.pdf.
Futter, A. & Gillwald, A., 2015, Zero-rated internet services: What is to be done?, viewed 25 May 2020, from https://researchictafrica.net/2016/01/25/zero-rated-internet-services-what-is-to-be-done/.
Geerdts, C., Gillwald, A., Calandro, E., Chair, C., Moyo, M. & Rademan, B., 2016, Developing smart public Wi-Fi in South Africa, viewed 06 September 2019, from https://www.researchictafrica.net/publications/Other_publications/2016_Public_Wi-Fi_Policy_Paper_-_Developing_Smart_Public_Wi-Fi_in_South_Africa.pdf.
Goddard, J., Molyneux, P., Wilson, J.O.S. & Tavakoli, M., 2007, 'European banking: An overview', Journal of Banking & Finance 31(7), 1911-1935. https://doi.org/10.1016/j.jbankfin.2007.01.002 [ Links ]
Hill, D.J., 1986, 'Satisfaction and consumer services', in R.J. Lutz (ed.), Advances in consumer research, vol. 13, no. 1, pp. 311-315, Association for Consumer Research, Provo, UT.
Kulkarni, A. & Dambe, S., 2019, 'Innovating Digital Consumer Services in Wealth Management Ecosystem an Anthropomorphic Approach', in M. Tuba, S. Akashe & A. Joshi (eds.), Information and Communication Technology for Sustainable Development. Advances in Intelligent Systems and Computing, vol. 933, pp. 268-277, Springer Nature, Singapore, viewed 28 August 2019, from https://doi.org/10.1007/978-981-13-7166-0_24
Lee, J. & Kim, H., 2020, 'Determinants of adoption and continuance intentions toward Internet-only banks', International Journal of Bank Marketing 38(4). https://doi.org/10.1108/IJBM-07-2019-0269 [ Links ]
Louw, C., 2017, 'Towards a smartphone application user security competency evolution model', Doctoral thesis, University of Johannesburg Library and Information Centre, Theses and dissertations, viewed 12 Augustus 2020, from hdl.handle.net/10210/261505. [ Links ]
Louw, C. & Nieuwenhuizen, C., 2019, 'Online, community-driven E-commerce platforms and the rise of lifestyle commerce: A conceptual study', Seventh annual winter global business conference, 28 January - 1 February 2019, Tignes. ISSN: 2584-6302
Louw, C. & Nieuwenhuizen, C., 2020, 'Digitalization strategies for SMEs: A cost vs. skill approach for website development', African Journal of Science, Technology, Innovation and Development 12(2), 195-202. https://doi.org/10.1080/20421338.2019.1625591 [ Links ]
Louw, C. & Von Solms, B., 2018, 'Smartphone usage and security maturity: A South African student evaluation', in A. Jøsang (ed.), ECCWS 2018, 17th European conference on cyber warfare and security, 28-29 June 2018, pp. 268-277, Oslo.
Mercieca, S., Schaeck, K. & Wolfe, S., 2007, 'Small European banks: Benefits from diversification?', Journal of Banking & Finance 31(7), 1975-1998. https://doi.org/10.1016/j.jbankfin.2007.01.004 [ Links ]
Murphy, C., 2018, 5 ways banks can create a digital mindset, viewed 03 August 2019, from https://www.mobilepaymentstoday.com/blogs/5-ways-banks-can-create-a-digital-mindset/.
Pallant, J., Sands, S. & Karpen, I., 2020, 'Product customization: A profile of consumer demand', Journal of Retailing and Consumer Services 54(2020), 102030. https://doi.org/10.1016/j.jretconser.2019.102030 [ Links ]
Pyun, C.S., Scruggs, L. & Nam, K., 2002, 'Internet banking in the U.S., Japan and Europe', Multinational Business Review 10(2), 73-81. [ Links ]
Roberts, K., Varki, S. & Brodie, R., 2003, 'Measuring the quality of relationships in consumer services: An empirical study', European Journal of Marketing 37(1/2), 169-196. https://doi.org/10.1108/03090560310454037 [ Links ]
South African Reserve Bank Prudential Authority, 2019, Selected South African banking sector trends February 2019, viewed 28 August 2019, from https://www.resbank.co.za/Lists/News%20and%20Publications/Attachments/9136/02%20February%202019.pdf.
Statcounter Global Stats, 2019, Mobile operating system market share worldwide 2018, viewed 25 August 2019, from https://gs.statcounter.com/os-market-share/mobile/worldwide/#monthly-201801-201812.
User Experience, n.d., Lexico powered by OXFORD dictionary, viewed 25 May 2020, from https://www.lexico.com/definition/user_experience.
 Correspondence:
Correspondence:
Candice Louw
candicel@uj.ac.za
Received: 24 Sept. 2019
Accepted: 24 June 2020
Published: 05 Oct. 2020
ORIGINAL RESEARCH
Information and communication technologies: Use and factors for success amongst academics in private and public universities in Nigeria
Adefunke O. Alabi; Stephen Mutula
Discipline of Information Studies, School of Social Sciences, College of Humanities, University of KwaZulu-Natal, Pietermaritzburg, South Africa
ABSTRACT
BACKGROUND: The higher education sector is making a conscious effort to integrate information and communication technologies (ICTs) into the academe with a view to improving teaching, learning and access to knowledge. Unfortunately, the use of ICTs in teaching by academics in Nigerian universities is far below expectation.
OBJECTIVES: The aim of this article was to report on a study that examined the underlying factors determining the use of ICTs in teaching by academics in private and public universities in Nigeria by using the unified theory of acceptance and use of technology (UTAUT) as a theoretical lens.
METHOD: A mixed method approach involving the use of questionnaires and semi-structured interviews was adopted for the study. Data were collected from 267 academics in 3 faculties and 10 key informants who were in managerial positions at the University of Ibadan and Covenant University.
RESULTS: Regression analyses indicated that only facilitating conditions (FCs) (β = −0.345, t = −3.221, p = 0.002) have significant influence on the use of ICT in teaching at the University of Ibadan. However, both effort expectancy (EE) (β = 0.380, t = 3.116, p = 0.003) and FCs (β = −0.281, t = −2.327, p = 0.023) have significant influence on the use of ICT by academics in Covenant University. The qualitative study explicates these factors: institutional policy, technological infrastructure, simplicity of use, fund and organisational support as success factors for ICT use in teaching. Further findings revealed that age had an effect on EE and FCs amongst academics at the University of Ibadan, but out of all the demographic factors, age emerged as the only variable that had an effect on social influence amongst academics in Covenant University.
CONCLUSION: The study concludes that stakeholders in higher institutions should give adequate attention to these underlying factors: FCs and EE for optimal success of ICT use in teaching. The findings of this study have far-reaching implications for policy makers within the educational environs and intervention strategies on the part of the university stakeholders in supporting ICT use in teaching
Keywords: information and communication technologies; ICT use; academics; universities; UTAUT; e-learning; Nigeria.
Introduction
Information and communication technologies (ICTs) provide limitless opportunities for universities in developing countries to overcome many of the impediments to the successful delivery of higher education (Njoku 2015). The term ICT denotes a wide array of digital technologies used in the creation, processing and transmission of information (Mbatha, Ocholla & Roux 2011). Examples include computers and their peripheral devices, radio, television, mobile phones, the Internet, Web 2.0 tools, communication technologies, databases, word processors, databases and learning management systems (LMSs). The advent of ICTs and their application in different sectors of life has not just turned the world into a global village, but also transmuted 'the mode of access to information and how academics in universities worldwide use information in teaching' (Okon, Ngulube & Onyancha 2014:52). This study operationalises ICTs as all forms of digital technologies used in education to significantly change the traditional mode of teaching in all higher institutions of learning.
Information and communication technologies' diffusion into higher education can be found in infrastructural development, equipping lecture theatres with the latest multimedia facilities and establishment of centres for ICT and ICT policy (Willis et al. 2013). Moreover, Miller (2017) explained that the United States government supported ICT use in teaching as far back as 1990. There is also the prevalence of extensive training in the form of short courses, seminars and workshops on digital literacy and pedagogical use of various learning (Almpanis 2015). Researchers have assessed the extent to which universities in the United Kingdom, United States of America and Saudi Arabia have tried to infuse ICT into teaching and learning (Alhabeeb & Rowley 2017; Barrette 2015; Buchanan, Sainter & Saunders 2013).
Information and communication technology uptake in Nigeria began in 1999 with the African Information Society Initiative (AISI) action plan of 1999 known as National Information and Communication Infrastructure (Ibara 2014). This was followed by the approval of a national policy on ICT by the Federal government in 2001 and establishment of initiatives such as National Information Technology Development Agency (NITDA), Education Trust Fund (ETF) and School Net Nigeria (Mattheew, Joro & Manasseh 2015). With these initiatives, ICTs such as computers and other various hardware, mobile phones, the Internet and software are now available in Nigerian universities, government departments and their parastatals, industries and banks (Ibara 2014). The potential for ICT-based teaching is supported by numerous factors such as the Internet, broadband connectivity, mobile telephones and networked computers (Lawal, Chatwin & Hasan 2018). There have also been a series of initiatives on the part of government through the Nigerian Universities Commission (NUC) to ensure that there are ICT facilities such as computers, interactive boards, multimedia projectors and the LMS in Nigerian universities (Gambari & Okoli 2007).
Despite the relevance of ICTs in the academic success of the students, Yushau and Nannim (2018) noted that there is under-utilisation of ICTs for teaching purposes amongst academics in terms of diversity, frequency and pace. Moreover, previous related studies relied majorly on quantitative approach (Alharbi & Drew 2014; Ntemana & Olatokun 2012). This study differentiates itself from previous studies through a combination of quantitative and qualitative research methods to understand the underlying success factors for ICT use in teaching in a developing nation such as Nigeria.
Purpose of the study
The study reported on in this article examines the factor(s) with the most significant influence on ICT use in teaching amongst academics in public and private university in Nigeria. Without identifying the decisive factors affecting ICT use in teaching by academics, efforts by stakeholders in the education sector on ICT policy formulation will remain futile. The study would be beneficial to university stakeholders in developing a reform agenda necessary for making the university environment more enabling for academics to integrate ICT into teaching. Moreover, the result of this study will add to the body of existing literature on technology adoption, acceptance, use and success of information system (IS).
Research question
This research question was developed to guide this study: What are the underlying factor(s) for ICT use in teaching amongst academics in public and private universities in Nigeria?
Research hypothesis
Demographic variables (age, gender and academic qualification) have no effect on the determinants of ICT use in teaching amongst academics.
Literature review
The use of ICT in teaching is an integral part of inclusive education as indicated in the sustainable development goals. Vega-Hernández, Patino-Alonso and Galindo-Villardón (2018) explained that the integration of ICT into teaching improves the learning process. It also leads to the development of 21st-century skills, necessary for the survival of students in a rapidly changing labour market (Van Laar et al. 2017). Therefore, 21st-century academics are to use ICT for lecture preparation and delivery and self-paced and engaging learning opportunities for their students (Elçi 2019). An improvement on the extent of ICT use in teaching in Nigeria and other developing nations should be sought after, to enable graduates compete favourably with their counterparts the world over (Onwuagboke & Singh 2016).
Evidence of ICT infusion in the educational sector proliferates with academics enjoying access to up-to-date information resources, course materials, communication with colleagues and expansion of learning preferences for students (Herath & Hewagamage 2015). Research also shows that the use of specialised software such as the LMS becomes essential because it has features capable of improving learning outcomes and courses offered by universities (Marks, Maytha & Rietsema 2016). Despite the suitability of ICT in teaching and learning, Lawrence and Tar (2018) expressed concern about the low attainment of the intended educational outcomes achieved so far. Studies emanating from educational scenarios especially from developing countries elucidate that several factors are responsible for the low integration of ICT in teaching (Okyere-Kwakye, Nor & Ologbo 2016). According to Stephen et al. (2016), the obstacles to ICT integration into teaching are the high cost of computer hardware and software, inadequate and poor technological infrastructure and low budgetary allocation to higher education. Researchers further argue that academics who have positive belief towards technology can overcome these impediments (Ertmer et al. 1999).
Nnazor (2009) posit that those in charge of university management should create an environment that is enabling physically and psychologically, through restructuring so as to allow for all-out use of ICT in teaching. Previous scholars (Ansari & Zuberi 2010; Edoru 2019; Porter & Graham 2016) note that the prevalence of technological infrastructure would most meaningfully influence the use of ICTs by academics. Contrary to this standpoint, Afshari et al. (2009) argued that the use of ICT in any academia is influenced by several inter-related factors. Putting these factors into perspectives, the determinants of ICT use can be classified into four factors, namely environmental, technological, organisational and individual (Macharia & Pelser 2014). However, some other scholars explained that insight into how these factors influence each other is highly desirable (Bower 2019). Beyond the understanding that ICT use is predicated on many inter-related factors, going by the submission of Adetimirin (2020), academics are to use ICTs, in particular the electronic resources in line with ethical guidelines to avoid being liable to offences such as copyright infringement and plagiarism. A study led by Ahmed and Kurshid (2015) demonstrated that individual attributes such as age, qualification and designation of academics significantly influence ICT use. The authors established that younger academics use ICT more than those who are older, but those in the professorial cadre use ICT more frequently than assistant professors. Lubis et al. (2017) added that the area of specialisation of academics also influences the use of ICT in teaching. David and Rahim (2012) researched into the impact of unified theory of acceptance and use of technology (UTAUT) on the use of ICT amongst academics in Adamawa State University, Nigeria. Findings revealed that perceived usefulness (PU) and perceived ease of use (PEOU) were the most influential factors associated with ICT use in teaching. However, the study of David and Rahim focussed on academics in a public university, where the use of ICT in teaching was not mandatory compared with many private owned institutions.
Theoretical lens for the study
There are many models and theories of information systems (ISs) that have been used to explain success factors for acceptance and the use of ICTs. But the one adopted as the theoretical lens for this study is the UTAUT proposed by Venkatesh et al. (2003). This is because of its suitability in educational settings, especially within Africa (Liebenberg, Benade & Ellis 2018). Moreover, UTAUT is an integrated theory resulting from the constructs of eight individual theories of IS, namely theory of planned behaviour (TPB), technology acceptance model (TAM), innovation diffusion theory (IDT), social cognitive theory (SCT), theory of reasoned action (TRA), the model of PC utilisation (MPCU), combined TAM and TPB (C-TAM-TPB) and motivational model (MM) motivation theory. Unified theory of acceptance and the use of technology engages a more pragmatic approach in providing a better understanding of the factors that could predict the success of technology use than other IS theories and models (Samaradiwakara & Gunawardena 2014). Similar studies (Kocaleva, Stojanovic & Zdravev 2015; Ouedraogo 2017; Oye, Iahad & Rahim 2014) have used the UTAUT model to examine the factors determining ICT acceptance and use. These studies demonstrate that the UTAUT consists of robust and valid parameters that may be used by researchers interested in understanding success factors for technology acceptance and use. Venkatesh et al. (2003) discussed four core constructs of UTAUT, namely performance expectancy (PE), effort expectancy (EE), social influence (SI) and facilitating conditions (FCs), which play a more prominent role in determining the success of ICT use in any organisation. Unified theory of acceptance and the use of technology also postulate that gender, age, experience and voluntariness of use act as moderating variables in determining the influence of the core constructs of UTAUT on technology adoption and use. This study focussed on PE, EE, SI and FC in determining the success of ICT use in an academic environment. The four core factors of UTAUT are described as follows:
-
PE: It refers to 'the degree to which the user expects that using the system will help him or her to attain gains in job performance' (Venkatesh et al. 2003:447). It is analogous with PU, extrinsic motivation, job-fit and relative advantage.
-
EE: It is defined as 'the degree of ease associated with the use of the system' (Venkatesh et al. 2003:450). It is related to PEOU, complexity and ease of use.
-
SI: It refers to 'the degree to which an individual perceives that important others believe he or she should use the new system' (Venkatesh et al. 2003:451). It refers to the subjective norm in TRA, TAM, TPB and C-TAM-TPB, social factors in MPCU and images in IDT.
-
FC: It denotes 'the degree to which an individual believes that an organisational and technical infrastructure exists to support use of the system' (Venkatesh et al. 2003:453).
Research method
The study was carried out in south-west Nigeria. South-west Nigeria is made up of six states: Lagos, Ogun, Oyo, Osun, Ondo and Ekiti states. Two universities, the University of Ibadan (UI), a public university in Oyo state, and Covenant University (CU), a private university situated in Ogun state, were purposively selected as the study sites. The UI was founded in 1948, whereas CU was established in 2002 as a result of the reformation in the educational sector in Nigeria. The UI was selected because it is the first and oldest public university in Nigeria, and both universities have made laudable efforts in ICT investment. Academics from three faculties (Arts, Science and Technology) that comprise the majority of disciplines that are common to both universities were purposively chosen.
A mixed method approach consisting of a survey and semi-structured interview were used to collect quantitative and qualitative data. The quantitative aspect was dominant and the qualitative was engrained within it. The mixed method approach was found to be the most suitable for this study's purpose as it helps to minimise the shortcomings of both approaches and provide a better understanding of research questions (Creswell 2014). This view is supported by Oshinaike and Adekunmisi (2012) who also adopted the mixed-methods research approach. The population of the study was 502 academics for the UI and for CU it is 230, making a total of 732 academics from both universities. By using Israel's (1992) sample sizes table, 267 academics made up the sample size for this study. Respondents in the survey were chosen by using the systematic random sampling technique. The questionnaire was adapted from Venkatesh et al. (2003) and Birch and Irvine (2009). It comprises items of the UTAUT and four main constructs, namely PE, EE, SI and FC, with minimal rephrasing to suit the purpose of the study. Prior to data collection, the internal consistency and reliability of the items of the instrument developed for this research were determined in a pilot study conducted at the University of Lagos amongst 30 academics and 3 university management staff, chosen because of the similarity in characteristics with the sample population. The Cronbach alpha results obtained were 0.97 for PE, 0.80 for EE, 0.74 for SI and 0.74 for FC.
A total of 183 questionnaires were distributed at the UI, 162 were returned, but only 131 were found suitable for the purpose of data analysis. The researcher administered 84 questionnaires at CU and all of them were returned and found useful for the purpose of data analysis. Overall, 267 questionnaires were distributed, and 246 were returned out of which 215 questionnaires were found suitable for data analysis. For the qualitative study, an interview guide was used for consistency of questions and responses. The interviewees were deans of the selected faculties, the director for centre for ICT and the university librarian, and data were collected through the census from 10 out of 11 participants. This category of people were considered key informants because they are involved in strategic decision-making, policy development and implementation in the university. The interview reponses were recorded by using a research diary and a handheld device with due consent of the interviewees. The quantitative data were analysed by using the Statistical Package for Social Sciences (SPSS) software to generate both descriptive (frequencies and percentages) and inferential statistics. The semistructured interview data were analysed by using content analysis. An ethical guideline that involved the use of informed consent, voluntariness of participation in the study, protection of respondents' identities and freedom to withdraw from the study at any time as proposed by Creswell (2014) was adopted for this study.
Ethical consideration
An ethical guideline that involved use of informed consent, voluntariness of participation in the study, protection of respondents' identities and freedom to withdraw from the study at any time as proposed by Creswell (2014) was adopted for this study (Ethical Clearance Number: HSS/1484/014D).
Results
Demographic profile of respondents
The study found that more male respondents participated in the study with (95% or 72.5%) from the UI and 62 (73.8%) from CU than female academics. A majority of the respondents were in the age of 36-46 years with the UI having a proportion of 67 (51.1%) and CU had 45 (53.6%), whereas those between 58 and 68 years had the least proportion. Results further showed that the designation of the respondents ranged from assistant lecturers to those in the professorial cadre. A majority of the academics were in the lecturer grade II category with 36 (27.5%) at the UI and 23 (27.5%) from CU followed by assistant lecturer cadre. Further findings showed that a majority of the respondents with 91 (69.5%) from the UI and 37 (44.0%) from CU had a PhD degree as their highest educational qualification. The study found that a majority of the respondents are from the Faculty of Science/Natural and Applied Science, with the UI having 64 (48.8%) whereas CU had 39 (46.4%) as shown in Table 1. The findings showed considerable combination across demographic variables; hence, data collected can be regarded as reliable for the purpose of this study.
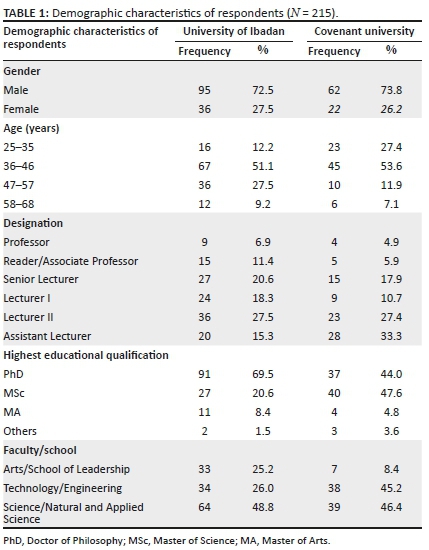
Findings: Descriptive analysis
Performance expectancy
Performance expectancy was measured by using five items out of which a descriptive analysis of the average score of the statement 'I find ICTs useful in teaching' with the highest mean score, and the least deviation from the mean (0.799) followed by 'ICTs enable me to accomplish tasks such as teaching more efficiently' with x = 4.52 and SD = 0.815 and 'use of ICTs enhances my teaching in terms of content and delivery' with x = 4.51 and SD = with x = 4.52 and SD = 0.815 indicate that the use of ICT in teaching is beneficial to academics in both private and public universities.
Effort expectancy
The mean value of responses to the variable EE showed that 'learning to use ICTs is easy for me' (x = 4.07 and standard deviation 0.971); 'ICTs are generally easy to use' (x = 4.00 and SD = 0.985); and 'I do not find the use of ICTs in my teaching a frustrating endeavour' (x = 3.88 and SD = 0.989) had the highest means. The results indicate that more academics perceive ICTs to be easy to use.
Social influence
Social influence was measured with four items out of which the statement 'people who are important to me such as my Dean, HOD and my colleagues think I should use ICTs in my teaching' (x = 3.85 and SD = 1.167) had the highest mean. This was followed by the statement 'my students particularly think I should use ICTs in my teaching' with x = 3.87 and SD = 1.117.
Facilitating conditions
With a mean score of 3.64 and standard deviation of 1.331, the respondents indicated that 'my institution should make more ICT resources (such as computers, projectors, internet connectivity, LMS, e-resources, etc.) available for use in the department/faculty'. This was followed by the statement 'my institution has people in ICT section who are available to provide assistance with difficulty on the use of ICTs' with x = 3.54 and SD = 1.217.
F-statistic test
The F-test allows for evaluation of two competing regression models in their ability to explicate the variance in the dependent variable. Therefore, to determine if the association between the independent variables (PE, EE, SI and FC) and the dependent variable (ICT use in teaching) is statistically significant, the p value was taken into consideration. Table 2 shows that for academics at the UI with F (4, 126) = 3.776, p = 0.006 and at CU with F (4, 79) = 3.311, p = 0.015, regression model is significantly better at predicting the use of ICT in teaching at the UI and CU from PE, EE, SI and FC with p < 0.05.
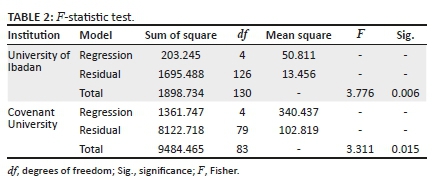
Regression analysis
Table 3 shows the results that only FCs (β = −0.345, t = −3.221, p = 0.002) have significant influence on the use of ICT in teaching at the UI, whereas EE, SI and PE are poor predictors of the use of ICT in teaching by academics at the UI. However, both EE (β = 0.380, t = 3.116, p = 0.003) and FCs (β = −0.281, t = −2.327, p = 0.023) have significant influence on the use of ICT by academics in CU. Findings also reveal that PE and SI are poor predictors of the use of ICT in teaching in CU.
To complement these findings, the deans, the directors of Centre for Information and Technology System (CITS) and the two library directors (university librarians) were asked to express their thoughts on factors they consider most imperative for success in ICT use in teaching. This elicited several responses as shown in Table 4.
Test of hypothesis
Hypothesis 1
Demographic variables (age, gender and academic qualification) have no effect on the determinants of ICT use in teaching amongst academics.
Spearman's correlation coefficient was used for determining the relationship between the demographic variables (age, gender and academic qualification) and the determinants of ICT use. At the UI, the correlation between age and EE (r = 0.194, N = 131, p = 0.026) was significant. This implies a positive relationship between age and EE. A positive relationship also exists between age and FC (r = 0.232, N = 131, p = 0.008). Therefore, age had an effect on EE and FC amongst academics at the UI. However, the relationship was not significant between gender and all the determinants of ICT use, as well as academic qualification and all the determinants of ICT use (PE, EE, SI and FC) with p > 0.05 (see Table 5). Further findings show that age had a statistically significant correlation with SI amongst academics at CU (r = −0.236, N = 84, p = 0.031). This implies that out of all the demographic factors, age emerged as the only variable that had an effect on FC amongst academics at UI. Age also had an effect on SI amongst academics at CU (see Table 5).
Discussion of findings
This section discusses the major findings of the study.
Facilitating condition
The results of the study reveal that FC is a significant determinant of ICT use in teaching at the UI. Findings also show that both EE and FC are the major determinants of ICT use amongst academics in CU. The results from this study suggest that EE and FC are the variables that significantly influence academics' use of ICTs in teaching. However, FC is the most important underlying factor for ICT use in teaching amongst academics in a public university, whereas EE and FC are requisite for ICT use amongst academics in private university. Similar to this finding, Kocaleva et al. (2015) found that FC and EE have a stronger influence on technology use. Facilitating condition is the degree to which an individual believes that organisational and technical infrastructure exist to support the use of technology (Venkatesh et al. 2003). Going by the submission of Alshmrany and Wilkinson (2017), FC is a supportive environment, which reduces any difficulty in technology adoption and use. In institutions of learning, FCs are availability of technical assistance, infrastructure, hardware and software (Bingimlas 2009) in any organisation. Facilitating condition, according to Yoo, Han and Huang (2012), usually serves as a source of motivation in technology adoption and use. In this study, another important finding is that age had an effect on EE and FC amongst academics at UI. This implies that academics who are older put more emphasis on FCs than those who are younger.
Effort expectancy
It was found that academics from CU perceived EE, aside from FC to be a fundamental determinant of ICT use. The results further confirmed that EE, a construct analogous to ease of use in TAM, has a strong influence on ICT use. This result is not unexpected, as previous studies (Venkatesh et al. 2003) pointed out that EE is a subset of FC. The strength of this construct in predicting technology use in other contextual settings such as e-government, e-commerce and healthcare has been demonstrated in various empirical studies (Ozkan & Kanat 2011; Yang 2010). As EE had influence on ICT use in teaching, Haslaman, Mumcu & Usluel (2008) pointed out the need for an internal helpdesk, whose job will be provision of support services to academics on the use of ICT in teaching. The strength of the UTAUT constructs in predicting technology acceptance and use is further supported by the result of this study.
Interviews with the deans, the directors of CITS and the two library directors (university librarians) revealed that management at both private and public universities are aware of the major factors influencing the use of ICT in teaching and learning. One of the deans of faculty totally opines that:
… it is more of infrastructural support than any of these factors put together, if the technological infrastructures are not there, ICT adoption and use is not possible in the first instance instance!' (R3, UI, Dean of Faculty)
Overall, the qualitative aspect of this study showed that institutional policy, technological infrastructure, simplicity of use, fund and organisational support were requisites for ICT use. Related studies (Al-Mobaideen 2009) found similar factors in Jordanian universities, indicating that the concerns raised by respondents in Nigerian universities about critical success factors for ICT use in teaching are largely similar to those of scholars from other parts of the world.
Performance expectancy
Findings showed that PE had no significant influence on the use of ICT in teaching amongst academics in both public and private universities. The descriptive analysis showed that out of all of the individual items used in measuring the construct academics from both UI and CU, the statement 'I find ICTs useful in teaching' emerged with the highest mean score and the least deviation from the mean. This finding implies that academics are not disputing the usefulness of ICT in teaching. In the context of this study, academics in both private and public universities do not attach much importance to PE as a decisive factor in ICT use.
Social influence
Social influence is defined by Venkatesh et al. (2003:451) as: 'the degree to which an individual perceives that important others believe he or she should use the new system'. The findings of this study showed that SI had no significant influence on the ICT use in teaching. The result is divergent from previous research, which found SI to have a significant relationship with behavioural intention to use technology (Moussaïd et al. 2013). Further findings revealed that age had a significant correlation with SI amongst academics in a private university (CU). This finding suggests that the older academics are more likely to believe that their image and reputation will improve with the use of ICT in teaching (Rogers 2003).
Conclusion and recommendations
Today's academics must use ICTs in teaching to better position themselves within the learning curve as facilitators and not the sole custodians of knowledge. In finding support for ICT use in teaching, the possibility lies in unwavering effort towards provision of an enabling environment. This article concludes that stakeholders in higher institutions should give adequate attention to these underlying factors: FCs and EE for optimal success of ICT use in teaching.
Implication of the study for policy makers
The implications of these findings is that stakeholders in higher institutions should be more involved in helping academics to develop a greater sense of ICT use in teaching through provision of a supportive environment, most especially provision of infrastructure, hardware, software, technical assistance and regular training. The study makes significant contribution to IS theory by revealing the analytical power of the UTAUT in determining the underlying success factors for ICT use in an educational setting.
Limitation of study
The limitation of this study lies in its inability to include academics from higher institutions in other geopolitical zones in Nigeria, and as such, the results cannot be applied to settings other than areas where the study was conducted, except when replicated over time. Future studies should include other academics from other disciplinary backgrounds and from universities other than those used in this study.
Acknowledgements
This article reports on part of the findings of a doctoral study that was completed at the University of KwaZulu-Natal in 2016.
Competing interests
The authors have declared that no competing interests exist.
Authors' contributions
A.O.A. carried out the research for her PhD study and S.M. supervised the PhD research.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Adetimirin, A., 2020, 'Technology adoption for teaching: The ethical considerations', in Handbook of research on diverse teaching strategies for the technology-rich classroom, pp. 70-78, IGI Global, Hershey, PA.
Afshari, M., Bakar, K.A., Luan, W.S., Samah, B.A. & Fooi, F.S., 2009, 'Factors affecting teachers' use of information and communication technology', Online Submission 2(1), 77-104. [ Links ]
Ahmed, H. & Kurshid, F., 2015, 'Use of Information and Communication Technology (ICT) among public and private sector universities in teaching and learning process', Scholedge International Journal of Multidisciplinary & Allied Studies 2(4), 25-36. https://doi.org/10.2139/ssrn.2583373 [ Links ]
Alhabeeb, A. & Rowley, J., 2017, 'Critical success factors for eLearning in Saudi Arabian universities', International Journal of Educational Management 31(2), 131-147. https://doi.org/10.1108/IJEM-01-2016-0006 [ Links ]
Alharbi, S. & Drew, S., 2014, '"Using the technology acceptance model in understanding academics" behavioural intention to use learning management systems', International Journal of Advanced Computer Science and Applications 5(1), 143-155. https://doi.org/10.14569/IJACSA.2014.050120 [ Links ]
Al-Mobaideen, H.O., 2009, 'Assessing information and communication technology in Jordanian universities: Building critical success factors' (CSF) model of ICT diffusion', Doctoral dissertation, Leeds Metropolitan University. [ Links ]
Almpanis, T., 2015, 'Staff development and institutional support for technology enhanced learning in UK universities', Electronic Journal of E-Learning 13(5), 366-375. [ Links ]
Alshmrany, S. & Wilkinson, B. 2017, 'Factors influencing the adoption of ICT by teachers in primary schools in Saudi Arabia', Education (Mohe) 8(12), 143-156. https://doi.org/10.14569/IJACSA.2017.081218 [ Links ]
Ansari, M.N. & Zuberi, B.A., 2010, 'Use of electronic resources among academics at the University of Karachi', Library Philosophy and Practice, viewed 16 April 2019, from https://digitalcommons.unl.edu/libphilprac/385.
Barrette, C.M., 2015, 'Usefulness of technology adoption research in introducing an online workbook', System 49, 133-144. https://doi.org/10.1016/j.system.2015.01.005 [ Links ]
Bingimlas, K.A., 2009, 'Barriers to the successful integration of ICT in teaching and learning environments: A review of the literature', Eurasia Journal of Mathematics, Science & Technology Education 5(3), 235-245. https://doi.org/10.12973/ejmste/75275 [ Links ]
Birch, A. & Irvine, V., 2009, '"Preservice teachers" acceptance of ICT integration in the classroom: Applying the UTAUT model', Educational Media International 46(4), 295-315. https://doi.org/10.1080/09523980903387506 [ Links ]
Bower, M., 2019, 'Technology-mediated learning theory', British Journal of Educational Technology 50(3), 1035-1048. https://doi.org/10.1111/bjet.12771 [ Links ]
Buchanan, T., Sainter, P. & Saunders, G., 2013, 'Factors affecting faculty use of learning technologies: Implications for models of technology adoption', Journal of Computing in Higher Education 25(1), 1-11. https://doi.org/10.1007/s12528-013-9066-6 [ Links ]
Creswell, J.W., 2014, Research design: Qualitative, quantitative and mixed methods approaches, 4th edn., Sage, Thousand Oaks, CA.
David, O.N. & Rahim, N.Z.A., 2012, 'The impact of UTAUT model and ICT theoretical framework on university academic staff: Focus on Adamawa state university, Nigeria', International Journal of Computers & Technology 2(2), 102-111. https://doi.org/10.24297/ijct.v2i2b.2640 [ Links ]
Edoru, M.J., 2019, Information and communication technology in Ugandan higher education, Kabale University, Kabale.
Ertmer, P.A., Paul, A., Molly, L., Eva, R. & Denise, W., 1999, 'Examining teachers' beliefs about the role of technology in the elementary classroom', Journal of Research on Computing in Education 32(1), 54-72. [ Links ]
Elçi, A., 2019, 'Faculty development centers for digital teaching and learning: Implementation of institutional strategy and infrastructure', in Handbook of research on faculty development for digital teaching and learning, pp. 417-437, IGI Global, Hershey, PA.
Gambari, A.I. & Okoli, A., 2007, 'Availability and utilization of information and communication technology (ICT) facilities in higher institutions in Niger State, Nigeria', Information Technology 4(1), 34-46. https://doi.org/10.4314/ict.v4i1.31973 [ Links ]
Haslaman, T., Mumcu, F.K. & Usluel, Y.K., 2008, 'Integration of ICT into the teaching-learning process: Toward a unified model', in Proceedings of World Conference on Educational Multimedia, Hypermedia and Telecommunications 2008, pp. 2384-2389, AACE, Chesapeake, VA.
Herath, H.M. & Hewagamage, C., 2015, 'Analysis of ICT usage for the teaching and learning process by the academics', International Journal of Computer and Information Technology 4(05), 803-808. [ Links ]
Ibara, E.C., 2014, 'Information and communication technology integration in the Nigerian education system: Policy considerations and strategies', Educational Planning 21(3), 5-18. [ Links ]
Israel, G.D., 1992, Determining sample size, University of Florida Cooperative Extension Service, Institute of Food and Agriculture Sciences, EDIS, viewed 16 April 2019, from http://sociology.soc.uoc.gr/.
Kocaleva, M., Stojanovic, I. & Zdravev, Z., 2015, 'Model of e-learning acceptance and use for teaching staff in higher education institutions', International Journal of Modern Education and Computer Science (IJMECS) 7(4), 23-31. https://doi.org/10.5815/ijmecs.2015.04.03 [ Links ]
Lawal, L.S., Chatwin, C.R. & Hasan, R., 2018, 'The communications satellite industry as an element in Nigeria's attempt to modernise its economy and society', International Journal of African and Asian Studies 51, 30-39. [ Links ]
Lawrence, J.E. & Tar, U.A., 2018, '"Factors that influence teachers" adoption and integration of ICT in teaching/learning process', Educational Media International 55(1), 79-105. https://doi.org/10.1080/09523987.2018.1439712 [ Links ]
Liebenberg, J., Benade, T. & Ellis, S., 2018, 'Acceptance of ICT: Applicability of the Unified Theory of Acceptance and Use of Technology (UTAUT) to South African students', The African Journal of Information Systems 10(3), 160-173. [ Links ]
Lubis, A.H., Zulkarnain, S., Idrus, S. & Asiah, S., 2017, 'The use of ICT among university's lecturers in Medan, Indonesia: A comparative study', Journal of Human Development and Communication 6, 63-76. [ Links ]
Macharia, J.K. & Pelser, T.G., 2014, 'Key factors that influence the diffusion and infusion of information and communication technologies in Kenyan higher education', Studies in Higher Education 39(4), 695-709. https://doi.org/10.1080/03075079.2012.729033 [ Links ]
Marks, A., Maytha, A.A. & Rietsema, K., 2016, 'Learning management systems: A shift toward learning and academic analytics', International Journal of Emerging Technologies in Learning (IJET) 11(04), 77-82. https://doi.org/10.3991/ijet.v11i04.5419 [ Links ]
Matthew, D., Joro, I.D. & Manasseh, H., 2015, 'The role of information communication technology in Nigeria educational system', International Journal of Research in Humanities and Social Studies 2(2), 64-68. [ Links ]
Mbatha, B.T., Ocholla, D.N. & Roux, J.L., 2011, 'Diffusion and adoption of ICTs in selected government departments in KwaZulu-Natal, South Africa', Information Development 27(4), 251-263. https://doi.org/10.1177/0266666911424864 [ Links ]
Miller, E.R., 2017, Predicting the use of instructional technology among community college instructors: An extension of the Technology Acceptance Model (TAM), University of South Alabama, Mobile, AL.
Moussaïd, M., Kämmer, J.E., Analytis, P.P. & Neth, H., 2013, 'Social influence and the collective dynamics of opinion formation', PLoS One 8(11), e78433. https://doi.org/10.1371/journal.pone.0078433 [ Links ]
Njoku, C., 2015, 'Information and communication technologies to raise quality of teaching and learning in higher education institutions', International Journal of Education and Development using ICT 11(1), 122-147. [ Links ]
Nnazor, R., 2009, 'A conceptual framework for understanding use of information and communication technology in teaching in universities', International Journal of Instructional Technology & Distance Learning 6(1), 47-58. [ Links ]
Ntemana, T.J. & Olatokun, W., 2012, 'Analyzing the influence of diffusion of innovation attributes on lecturers' attitudes toward information and communication technologies', Human Technology 8(2), 179-197. https://doi.org/10.17011/ht/urn.201211203034 [ Links ]
Okon, A.E., Ngulube, P. & Onyancha, B., 2014, 'Accessibility and utilization of electronic information resources for research by academic staff at selected Nigerian universities between 2005 and 2012', International Information & Library Review 46(1-2), 51-60. https://doi.org/10.1080/10572317.2014.922858 [ Links ]
Okyere-Kwakye, E., Nor, K.M. & Ologbo, A.C., 2016, 'Technology acceptance: Examining the intentions of Ghanaian teachers to use computer for teaching', African Journal of Library, Archives & Information Science 26(2), 119-132. [ Links ]
Onwuagboke, B.B.C. & Singh, T.K.R., 2016, 'Faculty attitude and use of ICT in instructional delivery in tertiary institutions in a developing nation', International Journal of Research Studies in Educational Technology 5(1), 77-88. https://doi.org/10.5861/ijrset.2016.1428 [ Links ]
Oshinaike, A.B. & Adekunmisi, S.R., 2012, Use of multimedia for teaching in Nigerian university system: A case study of university of Ibadan, viewed 16 April 2019. from http://www.webpages.uidaho.edu/*mbolin/oshinaike-adekunmisi.htm.
Ouedraogo, B., 2017, 'Model of Information and Communication Technology (ICT) acceptance and use for teaching staff in sub-saharan Africa public higher education institutions', Higher Education Studies 7(2), 101-118. https://doi.org/10.5539/hes.v7n2p101 [ Links ]
Oye, N.D., Iahad, N.A. & Rahim, N.A., 2014, 'The history of UTAUT model and its impact on ICT acceptance and usage by academicians', Education and Information Technologies 19(1), 251-270. https://doi.org/10.1007/s10639-012-9189-9 [ Links ]
Ozkan, S. & Kanat, I.E., 2011, 'e-Government adoption model based on theory of planned behavior: Empirical validation', Government Information Quarterly 28(4), 503-513. https://doi.org/10.1016/j.giq.2010.10.007 [ Links ]
Porter, W.W. & Graham, C.R., 2016, 'Institutional drivers and barriers to faculty adoption of blended learning in higher education', British Journal of Educational Technology 47(4), 748-762. https://doi.org/10.1111/bjet.12269 [ Links ]
Rogers, M.E., 2003, Diffusion of Innovations (5th ed.), Free Press, New York, NY.
Samaradiwakara, G.D.M.N. & Gunawardena, C.G., 2014, 'Comparison of existing technology acceptance theories and models to suggest a well improved theory/model', International Technical Sciences Journal 1(1), 21-36. [ Links ]
Stephen, E.D., Yakubu, M., Omale, A. & Musa, A., 2016, 'Utilization of information and communication technology resources by academics staff and students in colleges of education in Nigeria', International Journal of Academic Library and Information Science 4(1), 1-10. [ Links ]
Van Laar, E., Van Deursen, A.J., Van Dijk, J.A. & De Haan, J., 2017, 'The relation between 21stcentury skills and digital skills: A systematic literature review', Computers in Human Behavior 72(1), 577-588. https://doi.org/10.1016/j.chb.2017.03.010 [ Links ]
Vega-Hernández, M.C., Patino-Alonso, M.C. & Galindo-Villardón, M.P., 2018, 'Multivariate characterization of university students using the ICT for learning', Computers & Education 121(1), 124-130. https://doi.org/10.1016/j.compedu.2018.03.004 [ Links ]
Venkatesh, V., Morris, M.G., Davis, G.B. & Davis, F.D., 2003, 'User acceptance of information technology: Toward a unified view', MIS Quarterly 27(3), 425-478. https://doi.org/10.2307/30036540 [ Links ]
Willis, C., Kestell, C., Grainger, S. & Missingham, D., 2013, 'Encouraging the adoption of education technology for improved student outcomes', Australasian Journal of Engineering Education 19(2), 109-117. https://doi.org/10.7158/D12-012.2013.19.2 [ Links ]
Yang, K., 2010, 'Determinants of US consumer mobile shopping services adoption: Implications for designing mobile shopping services', Journal of Consumer Marketing 27(3), 262-270. https://doi.org/10.1108/07363761011038338 [ Links ]
Yoo, S.J., Han, S.H. & Huang, W., 2012, 'The roles of intrinsic motivators and extrinsic motivators in promoting e-learning in the workplace: A Case from South Korea', Computers in Human Behavior 28(3), 942-950. https://doi.org/10.1016/j.chb.2011.12.015 [ Links ]
Yushau, B. & Nannim, F.A., 2018, 'ICT facilities and their utilization for educational purposes in Nigerian universities: A review of literatures from 2004 to 2018', ATBU Journal of Science, Technology and Education 6(1), 237-263. [ Links ]
 Correspondence:
Correspondence:
Adefunke Alabi
alabia@ukzn.ac.za
Received: 17 July 2019
Accepted: 24 June 2020
Published: 06 Oct. 2020
ORIGINAL RESEARCH
When rain clouds gather: Digital curation of South African public records in the cloud
Amos Shibambu; Mpho Ngoepe
Department of Information Science, Faculty of Arts, University of South Africa, Pretoria, South Africa
ABSTRACT
BACKGROUND: Many scholars lament of poor infrastructure for the management and preservation of digital records in the public sector in South Africa. For example, in South Africa, the national archives repository and its subsidiary provincial archives do not have infrastructure to ingest digital records into archival custody. As a result, digital records are left to the creating agencies to manage and preserve. The problem is compounded by the fact that very few public sector organisations in South Africa have procured systems to manage digital records.
OBJECTIVE: This study investigated whether government departments in South Africa entrust their records to cloud storage. The study asked the questions: How are digital records managed and stored in these organisations? Do government departments entrust their records to the cloud as an alternative storage?.
METHOD: Qualitative data were collected through interviews with purposively chosen chief information officers, records managers and IT managers from public entities that implemented e-government services, as well as officials from the National Archives and Services of South Africa, which is charged with the statutory regulatory role of records management in governmental bodies and the State Information Technology Agency, a public sector Information Communication Technology (ICT) company established in 1999 to consolidate and coordinate the state's information technology resources.
RESULTS: The key findings suggest that although public servants informally and unconsciously save some records in the cloud, government departments in South Africa are sceptical to entrust their records in the cloud because of a number of reasons such as lack of trust in the cloud storage, jurisdiction, legal implications, privacy and security risks related to Minimum Information Security Standards, as well as lack of policy and legislative framework, specifically regarding cloud storage.
CONCLUSION: Because of lack of infrastructure for management and preservation of digital records, for the purpose of increased storage and access, this study recommends that government departments should cautiously consider exploring the possibility of storing their records in a trusted digital repository cloud as an interim solution whilst observing legal obligations. As cloud storage is not very prevalent amongst government departments in South Africa, given the present challenges in managing digital records, it would be advantageous to have cloud storage tested rigorously before embarking on the exercise.
Keywords: digital curation; cloud storage; public records; e-government; South Africa.
Introduction and background to the problem
The title of this article was inspired by the classical novel by Bessie Head (2013) titled When rain clouds gather. The story of the novel is set in a fictional village in a remote area on the eastern side of Botswana. The country, or even so the fictional village, is dominated by the Kalahari Desert and the land is barren because of below average rainfall, often accompanied by severe drought. In her novel, Bessie Head uses the nation's constant desire for water as a backdrop for the hopes and aspirations of the people she describes. Despite the harshness of the land, people constantly look with hopefulness for rain clouds. This scenario can apply to the situation of records storage in the cloud in South Africa.
In South Africa, the responsibility of regulating government records falls under the auspices of the National Archives and Records Services (NARSSA) in the Department of Arts and Culture (DAC), which according to Ngoepe (2017) does not have the necessary infrastructure to manage and preserve digital records. As a result, digital records are left to the creating agencies to manage and preserve. The problem is compounded by a lack of government policy or legislation that regulates the storage and digital curation of records in the cloud. As a result, policies that regulate the storage of records in the cloud do not exist, which leaves government departments to put away paper-based records in an inaccessible storage with only few authorised users to access such records (Higgins 2011). This leaves government departments to face challenges like limited access to data in the provision of improved service delivery, as well as a lack of storage space for both paper and digital records. The alternative for this could be cloud storage. Neelima and Padma (2014) defined cloud storage as a storage medium that maintains data, manage and backup remotely and makes data available to users over the network or internet. Cloud storage has become an increasingly viable storage option for organisations that are unable to afford or maintain in-house, private electronic infrastructure suitable for long-term preservation of digital holdings. A reliable cloud archive that meets the requirements and expectations of a trustworthy repository is still in the early stages of conception.
The significance of cloud storage to e-government is well documented, and it improves ways of providing services to the citizens of a country. For example, Paquette, Jaeger and Wilson (2010) indicated that former president of the United States of America, Barak Obama, is of the view that cloud computing is capable of opening up the government to its citizens. The contribution of cloud storage to e-government services has the potential to merge distance and space and reduce time, which makes the transactions of public service more effective. For example, a citizen can apply for identity document or passport online without visiting the concerned government department or a potential tourist of the country can apply for a visa online without visiting the embassy. Following their impressive work, Shen, Yang and Keskin (2012) traced the conception of cloud computing back to 1961 when John McCarthy, whilst giving a speech to publicly celebrate the Massachusetts Institute of Technology's (MIT) centennial, that computation may someday be organised as a public utility. Just like electricity and telephones, subscribers will need to pay for the capacity of the usage of the space they acquired from the cloud service providers (CSPs). The situation leads to more storage for digital records on the cloud.
In the context of public administration, storing records in the cloud seems to be a cost-effective means of delivering e-government services towards ensuring efficiency, effectiveness, transparency, interoperability, cooperation, sharing and security. Bouaziz (2008:12) mentioned that the popular roles of e-government services are to allow collaboration of the government and its citizens (G2C) and to enable inter-agency relationships (G2G). However, that is achievable in the presence of cloud computing and digital preservation, which enable retrieval of records in various places at the same time. Carter and Bélanger (2005:5) observed that one of the primary functions of e-government is to ensure accessibility of government services to citizens and to promote a cost-effective government. Its success is solely reliant on a platform of cloud storage. In all organisations, data ostensibly have a strategic tool that is needed to support e-government. Given that the South African government envisions the offerings of government services through e-government services and has already partially realised the vision (application of identity documents, passport online, as well as filing of tax returns), it is necessary to have digital preservation in the cloud in order to support such services (Katuu & Ngoepe 2015).
Whilst the findings of iResearch of 2012 indicated that cloud storage service is already technically matured, its promotion is still in its infancy and that can be ostensibly seen in the way record keeping is handled. South African government departments have their records in their registries where they are accessed manually because they are stored predominantly in the form of paper, audio-visual and microfilm (Ngoepe 2012). Notwithstanding the importance of cloud storage, the challenge with the current practice in the context of the South African government still remains as records are stored on the premises of each department's registries manned by untrained registry clerks. Only a few governmental bodies have automated their records management programme (Ngoepe 2017). Pickover and Harris (2001) maintained that traditional paper-based records are likely to be inefficiently provided with resources, manned by junior records practitioners with little status and subject to high turnover rates, and incorrectly connected, if at all, to a parallel or similar electronic records management system. Rightly so, cloud storage is not prevalent amongst government departments in South Africa. Kuiper et al. (2014:1) opined that despite the potential advantages offered by cloud computing such as cost reduction in setting up cloud storage infrastructure, increased flexibility and agility when sharing archived records, the public sector in South Africa lags behind.
Problem statement
Despite a myriad of potential opportunities officered by the cloud storage, the current practice suggests that the South African government stores archival records on the government premises. This is informed by the NARSSA Act of 1996, which does not promote the use of cloud in favour of local digital storage, for example, external hard drives, compact discs, to mention but a few that are securely locked on the premises. However, on-site storage hinders ubiquitous access of records. Kuiper et al. (2014) pointed out that such practice does not promote the rollout of e-government service that is envisioned by the South African government. Obrustky (2016) and Galloway (2013) suggested that one key advantage of cloud storage is that the organisations can access information from any location, even if they do not have access to their organisation's network. This view is confirmed by Rajan and Shanmugapriyaa (2012) who stated that the strategies of cloud storage are capable of transforming the way in which current organisation's infrastructure is constituted and managed. Whilst providing easy access of records from anywhere, such strategies can save the organisations' capital expenditure and focus on operational expenditure. Given the evolution of technology, the use of cloud storage can save the organisation from the obsolescence of either the storage devices or stored information. In that view, there is a need for the South African government to review its physical storage model of records in favour of cloud in order to improve accessibility that is not limited by time and location.
Purpose and objectives of the study
The purpose of this study was to explore digital curation of records in the cloud to support e-government services in South Africa. The specific objectives were to:
-
analyse policies and legislative framework for records storage in the cloud;
-
determine if the public sector entrusts records in the cloud for storage and preservation; and
-
suggest a framework for digital curation of records in the cloud.
Literature review
Literature for this study is focused on the types of cloud storage, policy and legislative framework, storage and digital preservation of records in the cloud.
Cloud storage and preservation
Since its introduction, the cloud has become one of the fastest growing business for the storage of data. It involves storing data with cloud service provider rather than on local systems such as external hard-drive, compact disc, to mention but a few. Galloway (2013) pointed out that with the use of cloud storage consumers can access data from any location even if they do not have access to the network of an organisation.
Some organisations are now relying on the cloud for their record-keeping and preservation needs (Leveille 2015). It is indeed a viable storage option for organisations that are unable to afford or maintain in-house storage and preservation infrastructure. Instead of the traditional in-house records storage infrastructure, records are hosted virtually by the cloud service provider. In the past, storage of records has been an in-house activity. This, according to Cunningham (2019), offers the greatest degree of control and maximum opportunity for aligning to local policies. On the other hand, contracting, especially with CSPs, can provide organisations with access to the richest technical resources. However, this entails the risk of loss of control and knowledge of how preservation is carried out. This is compounded by the fact that cloud services may also run afoul of legal requirements regarding data residency, data protection, privacy and intellectual property rights (Cunningham 2019).
It is common for public sector organisations to encourage the use of cloud services. Cunningham (2019) recommended that when considering cloud storage, users should take into consideration the governance of data as it is the key factor in ensuring the security of information; compliance, especially with regard to the jurisdiction of the cloud service provider; trust; architecture; access management and software isolation; incident response and availability in case a court orders a seizure of equipment.
According to Pearce-Moses (2019), cloud storage is the storing, processing and use of data on remotely located computers accessed over the internet. Given the nature of its design, data in the cloud storage cannot be accessed in the absence of network connection. Bazi, Hassanzadeh and Moeini (2017) identified three types of service models: software as a server (SaaS): (1) a model where software and other solutions are delivered to the end-users as a service using the internet rather than as a product that can be installed on users' computers or mobile devices (Park & Ryoo 2012:161); (2) platform as a service (PaaS): an extension of SaaS that provides a platform to build and run application packages using an Application Programming Interface (API) that is supported by CSP; and (3) infrastructure as a service (IaaS), which is hosted by CSPs. All of these are accessed using the internet as a principal communication channel. Bazi et al. (2017) suggested that this pay-as-you-go platform allows an organisation to outsource its entire IT infrastructure to a CSP in support of its day-to-day operations such as servers, software, technical support and storage. It allows users to control or manage computing resources such as storage, networks and computing power so that they can deploy and run arbitrary software.
Each of the above service models can be deployed onto one of four variables types of clouds identified as follows:
-
Public cloud model: It is a deployment model that is accessible to anyone and is deemed to be less secure because of its openness (Bhandari, Gupta & Das 2016). Some examples of public cloud are Microsoft Azure, Google Cloud and Amazon. It should be noted that the term 'public' does not always associate with 'free', despite being fairly cheap.
-
Private cloud model: It is dedicated to organisations where the computing infrastructure cannot be shared (Leveille 2015). Considering that the organisation or third party on site or off site can manage it, it is more appealing to the organisations that require more control over their data and additional IT infrastructure investment (Sprott 2012).
-
Hybrid cloud: This model is an amalgamation of public and private cloud models where some resources are hosted and controlled externally by a third party, whilst some resources are used only by the organisation (Sprott 2012).
-
Community cloud model: This is a deployment model shared by organisations of the same community (Leveille 2015) that have shared concerns, for example, mission, security requirements, or compliance considerations. Bhandari et al. (2016) argued that community cloud is not really a deployment model as it is like private cloud, with the difference that in this case systems and services are accessible by a group of organisations.
Digital curation encompasses the processes and controls that enable digital objects to survive over time. The challenges for digital curation of records include both intentional and accidental corruption and loss throughout their existence. This requires that the records, even if entrusted to the cloud, are controlled under an unbroken chain of preservation (Duranti 2005). McLeod (2019) identified three strategies for preserving records in the cloud as involving the service provider to assume preservation responsibility, building a framework for preservation and access that can be implemented through a series of interconnected but independent services and, lastly, harnessing the emerging blockchain technology.
Policy and legislative framework
This section reviews literature from a legislative and regulatory framework perspective and explores some of the fundamental issues in managing records in a digital environment where cloud computing is gaining prominence. In the face of all these developments, the challenge is whether the legislative and regulatory framework in South Africa is adequate to facilitate the management of digital records in public institutions. Digital records are a reality for all public sector institutions, both in the national government and in other public sector institutions. In South Africa's myriad laws and regulations relating to the management of public records, electronic communications, privacy and data security are largely based on the principle of territoriality (Katuu 2015). A key concern is the loss of jurisdictional control over public records that may be managed and stored in disparate locations, including outside the country. Katuu (2015) identified three legislative instruments that 'control information' across all public institutions as: the archival legislation, which is NARSSA Act; the freedom of information legislation, which is the Promotion of Access to Information Act; and the privacy legislation, which is the Protection of Personal Information Act. The NARSSA Act imbues the national archivist with the power to determine the conditions of properly managing and reproducing electronic records.
Ngoepe and Saurombe (2016) pointed out that the legislation contains an important function, particularly on how records are stored in a networked environment in any country. In order to facilitate the management of digital information there are several additional legislative instruments, two of which are the Electronic Communications and Transactions (ECT) Act that was promulgated in 2002 and that facilitates ECT and the Regulation of Interception of Communications Act (RICA) that was promulgated in 2002 and regulates the interception of certain telephonic as well as internet communication. The NARSSA Act provides that governmental bodies are required to put the necessary infrastructure, policies, procedures and systems in place to ensure that records in all formats are managed in an integrated manner. However, in reality, this is not the case because, according to Ngoepe (2012), records management programmes in governmental bodies in South Africa are on the brink of collapse because of lack of infrastructure. The situation is worse in the digital environment. This contradicts the Constitution of South Africa, which promotes that records must be stored where transparency is promoted. Indeed, South Africa's laudable attempts to legislate and regulate digital records are not without their shortcomings. Katuu (2015) provided a summary of these efforts by stating that the NARSSA first published a set of policies and guidelines for managing digital records in 2000 and revised them in 2006. From the early 2000s, the NARSSA sought to assist public sector institutions in managing their digital records more efficiently. However, the transfer of digital records from public institutions into archival custody has not happened in any systematic manner because the national archival system has struggled to effectively manage such records and facilitate their long-term preservation (Katuu & Ngoepe 2015). Even before the emergency of cloud computing as option, the transfer of digital records from public institutions into archival custody has not happened in any systematic manner.
Research methodology
This qualitative case study utilised interviews and document analysis as data collection tools. The study was not informed by predetermined variables, but the researchers explored a phenomenon with an open mind depending on the opinions and response of participants to draw inferences and formulate a framework. The target sample of this study constituted of chief information officers (CIOs) and archive or records practitioners purposively selected from the national government departments. These officials have expertise in their respective areas of competency, for example, IT and records services within their organisations. The CIOs have capability to influence the virtual storage of the organisation's records, whilst the records practitioners are responsible for the footprints of the organisation by ensuring that records are stored and remain authentic. In the evolution of technology, records practitioners rely on CIOs to intervene when storage formats change. National government departments that have implemented some of the electronic services such as the Department of Sports, Arts and Culture, Department of Home Affairs, the Department of Science and Technology, as well as the Department of Basic Education were targeted. In this regard, 12 participants were interviewed. Furthermore, an official from the NARSSA of South Africa was also chosen as NARSSA is charged with the statutory regulatory role of records management in governmental bodies. So is the State Information Technology Agency (SITA), a public sector ICT company established in 1999 to consolidate and coordinate the state's information technology resources in order to achieve cost savings through scale, increase delivery capabilities and enhance interoperability. Interview data were augmented through document analysis of legislation and policies pertaining to data storage. The interviews for this study were arranged according to the objectives and, where necessary, follow-up questions were asked to obtain the in-depth information. As the participants were guaranteed anonymity and confidentiality, their names were coded as Participant A, B, C and so on. All the interviews were conducted in English at the participants' workplace at a date and time they determined appropriate. Only one participant declined to be recorded, but offered to speak slowly in order to give the researcher the opportunity to take notes. To provide quality to the study, questions were asked randomly depending on the responses provided by the participants. The legislation that has an impact on cloud storage was analysed to augment interview data. Data were analysed thematically and interpreted in accordance with the objectives of the study. In some instances, interview information is presented verbatim.
Ethical consideration
The study received ethical clearance from the University of South Africa's Department of Information Science Ethics Review Committee. (Reference number: 2018-DIS-0006).
Findings and discussions
This section provides an interpretation and a discussion of the findings presented in line with research objectives of this study.
Policy and legislative framework
The objective was intended to establish the policy and legislative framework used to store records in the cloud. Legislative framework plays a crucial role in the digital storage of the public sector. It ensures the protection of records from being damaged or used wrongly by unwanted sources. Digital storage must be guided by legislation and international standards of records management to ensure reliable governance. A lifecycle approach to the management of digital materials enables successful curation and long-term preservation, which should be performed within the ambit of legislation. Findings of this study revealed that the government departments do not have a specific legislation to govern cloud storage. Participant A, a CIO, indicated that his department consults various pieces of legislation with regard to cloud storage.
When asked to identify legislation that has a bearing on records storage in the cloud, participants indicated that although the NARSSA Act has overall bearing on record-keeping, they do not necessarily follow legislative framework but internal ICT policies. For example, Participant J explained that:
'Currently, we do not have a specific legislation for cloud storage, but there are various pieces of legislation that are applicable like ECT Act (it has provisions on how you manage digital records/data), the NARSA itself has some bearing on how public records must be managed. Other legislation like POPI and PAIA also make provision for management of records. Ideally, as a country we need to get to a point where we develop some legislation specifically about cloud. So you have to read the bits and pieces of legislation to make clear way on how to approach the cloud issue. If you look at SITA Act, there are mandatory services from SITA like networks. Now SITA is implementing the government cloud, which means we are now forced to use SITA cloud. Therefore, you need to read various pieces of legislation in order to come up with a business case for your environment'. (Participant J, IT Manager, 03 April 2019, Pretoria)
Other pieces of legislation identified include ECT Act, Promotion of Access to Information Act and Protection of Personal Information Act. Upon analysis of the legislation, the NARSSA Act makes only two provisions for the management of electronic records in terms of section 13(2)(b)(ii) and section 13(2)(b)(iii) that the national archivist shall determine the conditions subject to which electronic records systems shall be managed and the conditions under which records may be reproduced electronically. The first provision is about the system for the management of electronic records, whilst the second is about imaging or conversion of paper-based records into an electronic system. The Act is silent about custody entrusted to a third party such as cloud storage. An interview with a participant from the NARSSA and SITA revealed that the NARSSA has not yet issued directives to government departments with regard to cloud storage. This implies that the discretion lies with the relevant department regarding whether to entrust their records to the cloud or not. There is also no guiding document that is available for government departments in this regard. The participants agreed that the NARSSA Act supported digital records in conditions where the records are in devices like computers and servers that are stored securely on the government premises. Participants from IT sections indicated that the use of cloud services, such as email hosting, was taking place without the support of legislation. According to McLeod (2019), three strategies for preserving records in the cloud involve the service provider to assume preservation responsibility, building a framework for preservation and access that can be implemented through a series of interconnected but independent services and, lastly, harnessing emerging blockchain technology. However, the participants from both IT and registry sections revealed their reliance on ARSSA Act, which was considered outdated because it focused on microfilm, audio-visual and paper-based records that are securely locked on government premises. Kuiper et al. (2014) cautioned that storing records in such manner does not promote the rollout of e-government services, which is envisioned by the South African government.
Storage and preservation of records in the cloud
The DCC lifecycle model indicates that digital storage and preservation are necessary in the life of a record. In this objective, it was revealed that government departments store digital records on computerised devices that are safely locked on the government premises. This method of storage has contributed to the mushrooming of more than one registry in the government departments. Ngoepe and Van der Walt (2010) pointed out that decentralised registries are usually established if there would be unnecessary delays in accessing files if they were not kept near individuals working with them. However, decentralised registries can give rise to inconsistent systems and records management practices and duplication of files. In relation to this study, this type of storage isolates the citizens that stay far away from these storage premises.
The participants indicated that they prefer to store records on government premises to avoid transgression of archival legislation. However, there were those like Participant L, an IT manager, who indicated that he stores his personal records in the cloud such as Google Drive and sometimes even work-related records. However, record managers admitted to keeping records in platforms such as Dropbox, but were not aware that those were cloud storage.
Contrary to the fears of using the cloud, participants holding senior positions in IT indicated that they have email services hosted by the CSP. They have entered into service-level agreements on behalf of their departments with the CSP where they are billed for their allocated space. However, because of mistrust of privately owned cloud, the participants mentioned that they store personal information in privately owned clouds, but do not want to risk government records by storing it in privately owned clouds, for example, Dropbox. The participants listed some of the following factors that create hindrances when considering migration to the cloud adoption:
-
Lack of cloud legislation
-
Bankruptcy of the service provider
-
Enemy of super powers
-
Lack of trust in third party
-
Selling of personal information
-
Hindrances of cloud were on sovereignty
-
Cross-border jurisdiction
-
Loss of control over records
Despite the advantages from a business perspective, cloud computing also presents challenges, particularly regarding the mistrust of users to put their data on computers that they cannot control. Participant D, an IT manager, indicated that:
'We prefer to have control over our information to prevent fraud, misuse, etc. We also need access to the information whenever required so any interruptions or delays, e.g.: retrieval downtimes, may hamper activities. Location and access to cloud servers remain a barrier, as well as managing the destruction, retention, backup and migration processes'. (Participant D, IT manager, 14 April 2019, Pretoria)
Similarly, Obrustky (2016) pointed out that security is synonymous with cloud storage in view that records could be stolen or viewed by unauthorised people. The risk increases when customers are not in control of their records. However, Galloway (2013) suggested that following handing over of records to the cloud service provider, data transfer using encryption technology must be considered.
Participant F, an IT manager, indicated that because of a lack of cloud storage policy, records could not be entrusted to the cloud. The participants suggested that only when SITA is in charge could they move records to the cloud. This is informed by that SITA is a known agency responsible for ICT matters for the government. Currently, there is no policy or prototype guideline to advise regarding the ownership of data, security, availability of service (downtime and uptime), location of the cloud servers, backup and recovery and legal hold or e-discovery, to mention just a few issues. The concerns raised were not only limited to technology but also included organisation management, human behaviour, regulation and records management, as the participating CIO, revealed that they experienced a number of nontechnology issues with cloud computing, including a lack of control over employees' cloud computing use, a lack of internal regulations on cloud computing use, implementation difficulties, and a lack of transparency of providers' service.
Whilst security risk continues to be the paramount factor impeding cloud adoption, Participant F, an IT manager, indicated that integrity and security could be achieved by:
'… ensuring the cloud storage complies with ISO standards. In this regard we can conduct regular compliance tests/audits to ensure there are no breaches and have a quality control process built into the workflow to authenticate records'. (Participant F, IT manager, 22 March 2019, Pretoria)
Other mitigating factors mentioned by participants include: use of strong passwords, knowing legal obligations and retaining ownership.
Framework for digital curation of records in the cloud
Based on the findings, South Africa does not have a policy or legislative framework for cloud storage. This study proposes a framework in Figure 1, which is made up of the following elements: cloud legislation and policy framework, preservation, storage and disposal. Central to this proposed framework is digital curation of records. The line outside the figure shows how cloud legislation has influence over other elements and ultimately at the provision of e-government services. The arrows inside have been used to show how they relate to one another. All those coming from the legislation and policy framework indicate the influence that legislation has on each element that supports digital curation of records. The reliability of the system is dependent on the IT infrastructure, for example, LAN/WAN provided by the IT section and compliance with documents uploaded by the records management practitioners. The framework anticipates providing virtual access as digital preservation ensures that the content in digital format remains accessible over time, reliable and authentic. In the event that records are not accessible, the IT section and the records management division will work together to resolve the glitches.
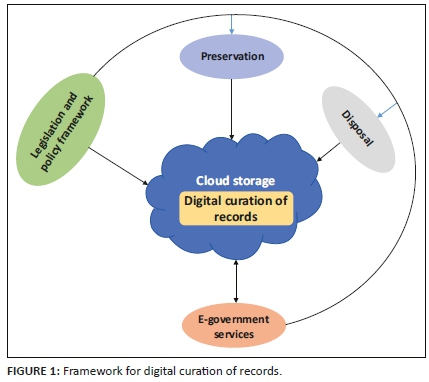
Legislation and policy framework: Given the proliferation of ICT, records need to be accessed virtually by the citizens of the country in a time convenient to them. However, there is a need for cloud legislation that makes provision for cloud storage. According to Ngoepe and Saurombe (2016), legislation has a huge impact on how records are stored in any country. Franks (2013) also argued that an effective records management programme should comprise records management policy and procedures, well-trained personnel, advanced information systems and reduced risks within the records management environment. As reflected in the framework, the implementation of this legislation should be driven to all government departments, nationally and provincially by the NARSSA, which is charged to manage government records. The legislation makes provision for the migration of born digital and digitalised records to the cloud. The Act should prescribe how the current records are digitalised in preparation for migration to the cloud. Issues to be included in the legislation include but are not limited to: governance of data, compliance, especially with regard to the jurisdiction of cloud service provider, trust, architecture, access management and software isolation, incident response and availability in case a court orders a seizure of equipment (Cunningham 2015).
Cloud storage: The government has born digital and digitised records stored on computer devices that are safely locked on government premises. This storing method supports digital curation of records only in a local environment. The use of these devices limits access of the citizens to information from anywhere at any time. Obrustky (2016) pointed out that one key advantage of cloud storage is that the organisations can access information from any location, even if they do not have access to their organisation's network. Introducing cloud to the government would fulfil what Paquette et al. (2010) indicated as former president of the United States of America, Barak Obama, emphasised that cloud computing, which offers cloud storage is capable of opening up the government to its citizens. Storing records in the cloud opens the government to the citizens through e-government services. However, the government does not have a state-owned cloud storage. The current option that the government has for cloud storage is to use the CSP. However, the government's chances to control CSPs on how to use its cloud are minimal as the providers have their own rules. This creates suspicion in using the CSP when considering that the service provider could be entangled in a legal battle leading to the loss of records. The viability of the cloud has been noticed when various government departments hosted their electronic mail services with CSP in order to communicate anywhere at any time. The government, through SITA and NARSSA, should develop a state-owned cloud where all government departments can subscribe storage spaces. Stuart and Bromage (2010) pointed out that whilst the widespread usage of cloud is not common, some governments such as United Kingdom have developed a secure cloud infrastructure named G-Cloud for public sector bodies. The migration can commence with the already digitalised and born-digital records stored on computer devices.
Destruction and preservation: This stage is about disposal of records, which according to NARSSA Act, consists of destruction and permanent preservation of records. The current way used by the government to dispose is performed on the government premises. Stuart and Bromage (2010) opined that secure retention and disposal of records is for most organisations a legal requirement. This is necessary to demonstrate not only that those records were legally disposed but also how it was performed. In the case of disposal in the form of preservation, access is limited to those who can reach the physical archival holdings, where those records are safely locked and full access is not given to everyone. It is preferred that the digitalisation and disposal committee section guide the process. The records need to be curated digitally and accessed in a cost-effective way. Digital records of enduring value, once identified as such by NARSSA, should be transferred to the cloud created by SITA and managed by NARSSA. Such records can be made accessible to the public online. Records of ephemeral nature that are entrusted to the cloud can be destroyed once they are no longer needed by a government department.
E-government services: Records entrusted to the cloud facilitate e-government. Contribution of cloud storage to e-government services has the potential to merge distance and space, as well as reduce time, which makes the transactions of public service more effective. According to Bouaziz (2008), popular roles of e-government services allow collaboration of the government and its citizens and enable inter-agency relationship. All the records that are digitally curated can be accessed as determined by the digitalisation and disposal section. The vision of the South African government is to improve government services through government services that are protected by the law. Furthermore, there will be a huge improvement in accessing information through e-government services if this framework were to be implemented. This area depicts the public access to records or interaction between government and citizens. Failure to address the situation will mean that records management is isolated from citizens and the world because the records are accessed manually by visiting the storage premises.
Conclusion and recommendations
This study has demonstrated the lack of infrastructure for curation of digital records, which has been equated to shortage of rain. The study argued that cloud storage offers hope to archivists to address the shortage of records storage. Cloud storage offers the accessibility of records irrespective of time and distance. The study investigated legislation and policy framework of cloud storage and digital curation of public records in the cloud. The National Archives and Records Services Act of 1996 is the primary legislation for records management in South Africa, and it was revealed that it does not make provision for cloud storage. It is clear from the discussion that current archival legislation was created with paper records in mind, demonstrated by the rule that all records should be saved for 20 years. As technology progresses at an increasingly rapid rate, this is no longer tenable. To avoid consulting various pieces of legislation when considering cloud storage, the government, through SITA and NARSSA, should update the NARSSA Act to make provision for cloud storage. This is so because the study revealed that public sector officials are hesitant to migrate to the cloud for digital curation, as it is not legislated. As the South African legislative and regulatory instruments are still largely based on the principle of territoriality (Katuu & Ngoepe 2015), the concern for the participants is the loss of control over public records held by cloud providers. Indeed, whilst the cloud storage option holds many attractions, the complications that may occur as a result of the services being provided from disparate geographical locations that are subject to different legal jurisdictions may result in unexpected but significant legal consequences and need to be carefully considered in determining whether cloud computing is an appropriate option. In this digital age, organisations need awareness of cloud storage in order to create space for other activities within the organisation. Following the updating of the NARSSA Act to cater for cloud storage, government departments can develop policies and procedures.
Because of the lack of infrastructure for management and preservation of digital records for the purpose of increased storage and access, this study recommends that government departments should cautiously consider exploring the possibility of storing their records in a trusted digital repository cloud as an interim solution whilst observing legal obligations. As cloud storage is not very prevalent amongst government departments in South Africa, given the present challenges in managing digital records, it would be advantageous to have cloud storage tested rigorously before public entities embark on the exercise. Paper-based records can also be converted to digital objects and stored in the cloud. This will help to alleviate the problem of space and provide accurate access to records in the public sector in South Africa. It emerged from this study that in the event the government thinks of cloud storage, the services of a third-party cloud have to be purchased from the third-party provider. The records practitioners are uncomfortable with using third-party cloud because of security and legal issues. The study revealed that the government departments are confident to use the cloud storage in which the government is involved. Therefore, the government, through SITA, should consider developing a state-owned private cloud and allocate storage spaces for government departments.
Acknowledgements
The authors acknowledge the participants of this study.
Competing interests
The authors have declared that no competing interests exist.
Authors' contributions
A.S. and M.N. conceptualised the study. A.S. conducted literature review, collected data and wrote the article. M.N. supervised the study.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The data that support the findings of this study are available from the corresponding author, M.N., upon reasonable request.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Bazi, H.R., Hassanzadeh, A. & Moeini, A., 2017, 'A comprehensive framework for cloud computing migration using meta-synthesis approach', The Journal of Systems and Software 128, 87-105. https://doi.org/10.1016/j.jss.2017.02.049 [ Links ]
Bhandari, A., Gupta, A. & Das, D., 2016, 'A framework for data security and storage in cloud computing', Article Read at the International Conference on Computational Techniques in Information and Communication Technology, New Delhi, 11-13th March.
Bouaziz, F., 2008, 'Public administration presence on the web: A cultural explanation', The Electronic Journal of e-Government 6(1), 11-22. [ Links ]
Carter, L. & Bélanger, F., 2005, 'The utilization of e-government services: Citizen trust, innovation and acceptance factors', Information Systems Journal 15(1), 5-25. https://doi.org/10.1111/j.1365-2575.2005.00183.x [ Links ]
Cunningham, A., 2015. 'Postcustodialism', in L. Duranti & P.C. Franks (eds.), Encyclopedia of Archival Science, pp. 274-278, Rowman & Littlefield, London.
Cunningham, A., 2019, 'Exploring digital preservation in the cloud', in L. Duranti & C Rogers (eds.), Trusting records in the cloud, pp. 179-206, Facet Publishing, London.
Duranti, L., 2005, The long-term preservation of authentic electronic records: Findings of the inter PARES project, Archilab, San Miniato.
Franks, P.C., 2013, Records and information management, Neal-Schuman, Chicago, IL.
Galloway, J.M., 2013, 'A cloud architecture for reducing costs in local parallel and distributed virtualised cloud environments', PhD thesis, University of Alabama, Alabama. [ Links ]
Head, B., 2013, When rain clouds gather, Waveland Press, Inc., Long Grove, IL.
Higgins, S., 2011, 'Digital curation: The emergence of a new discipline', International Journal of Digital Curation 6(2), 78-88. https://doi.org/10.2218/ijdc.v6i2.191 [ Links ]
Katuu, S., 2015, 'Managing records in South Africa's public sector - A review of literature', Journal of the South African Society of Archivists 48(1), 1-13. https://doi.org/10.17234/INFUTURE.2015.16 [ Links ]
Katuu, S. & Ngoepe, M., 2015, 'Managing digital records within South Africa's legislative and regulatory framework', in B.E. Popovsky (ed.), Proceedings of the 3rd International Conference on Cloud Security and Management ICCSM, pp. 59-70, Academic Conferences and Publishing International Limited, Tacoma, WA.
Kuiper, E., Van Dam, F., Reiter, A. & Janssen, M., 2014, 'Factors influencing the adoption of and business case for cloud computing in the public sector', viewed 18 December 2019, from https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.981.4981&rep=rep1&type=pdf
Leveille, V., 2015, 'Cloud archives', in L. Duranti & P.G. Franks (eds.), Encyclopaedia of archival science, pp. 136-139, Rowman & Littlefield, New York, NY.
McLeod, J., 2019, 'The cloud - Challenges and issues', in L. Duranti & C. Rogers (eds.), Trusting records in the cloud, pp. 13-36, Facet Publishing, London.
Neelima, M.L. & Padma, M., 2014, 'A study on cloud storage', International Journal of Computer Science and Mobile Computing 3(5), 966-971. [ Links ]
Ngoepe, M., 2012, 'Fostering a framework to embed the records management function into the auditing process in the South African public sector', PhD thesis, University of South Africa, Pretoria. [ Links ]
Ngoepe, M., 2017, 'Archival orthodoxy of post-custodial realities for digital records in South Africa', Archives and Manuscripts 45(1), 31-44. https://doi.org/10.1080/01576895.2016.1277361 [ Links ]
Ngoepe, M. & Saurombe, A., 2016, 'Provisions for managing and preserving records created in networked environments in the archival legislative frameworks of selected member states of the Southern African development community', Archives and Manuscripts 44(1), 24-41. https://doi.org/10.1080/01576895.2015.1136225 [ Links ]
Ngoepe, M. & Van der Walt, T., 2010, 'A framework for a records management programme: Lessons from the Department of Cooperative Governance and Traditional Affairs in South Africa', Mousaion 28(2), 83-107. [ Links ]
Obrustky, S.T., 2016, Cloud: Advantages, disadvantages and enterprise solutions for business, Eastern Institute of Technology, Hawke's Bay.
Paquette, S., Jaeger, P.T. & Wilson, S.C., 2010, 'Identifying the security risks associated with governmental use of cloud computing', Government Information Quarterly 27(3), 245-253. https://doi.org/10.1016/j.giq.2010.01.002 [ Links ]
Park, S.C. & Ryoo, S.Y., 2012, 'An empirical investigation of end-users switching toward computing: A two-factor theory perspective', Computer in Human Behaviour 29(1), 160-170. https://doi.org/10.1016/j.chb.2012.07.032 [ Links ]
Pearce-Moses, R., 2019, 'Inter PARES trust terminology', in L. Duranti & C. Rogers (eds.), Trusting records in the cloud, pp. 267-286, Facet Publishing, London.
Pickover, P. & Harris, V., 2001, Freedom of information in South Africa: A far off reality, South African History Archive, Johannesburg, viewed 14 December 2019, from http://www.wits.ac.za/saha/publications/FOIP_1_4_PickoverHarris.pdf
Rajan, R.A.P. & Shanmugapriyaa, S., 2012, 'Evolution of cloud storage as cloud computing infrastructure service', IOSR Journal of Computing Engineering 1(1), 38-45. https://doi.org/10.9790/0661-0113845 [ Links ]
Shen, Y., Yang, J. & Keskin, T., 2012, 'The evolution of IT towards cloud computing in China and US', Article Presented at International Conference on Computational Problem-Solving, Leshan, 19-21 October.
Sprott, A.A., 2012, 'Let me in the cloud analysis of the benefit and risk assessment of cloud platform', Journal of Financial Crime 20(1), 6-24. https://doi.org/10.1108/13590791311287337 [ Links ]
Stuart, K. & Bromage, D., 2010, 'Current state of play: Records management and the cloud', Records Management Journal 20(2), 2017-2225. https://doi.org/10.1108/95656981080001364 [ Links ]
 Correspondence:
Correspondence:
Mpho Ngoepe
ngoepms@unisa.ac.za
Received: 13 Feb. 2020
Accepted: 16 July 2020
Published: 07 Oct. 2020
ORIGINAL RESEARCH
Insight into ethical cyber behaviour of undergraduate students at selected African universities
Nurudeen A. Aderibigbe; Dennis N. Ocholla
Department of Library and Information Science, Faculty of Arts, University of Zululand, KwaDlangezwa, Empangeni, South Africa
ABSTRACT
BACKGROUND: Worldwide, immoral cyberspace users have continued to use the Internet to commit crimes; this has caused unease and has called for quick response to the problem especially within the educational sector. The practical value of this study is in its benefit to other researchers who may be attempting to understand South African or Nigerian cyber technology user's behaviour; it may also help relevant educational authorities to get relevant understanding of behaviour in the realm of cyberspace.
OBJECTIVES: This study examined undergraduate students in relation to cyber technology at the University of Zululand (UNIZULU), South Africa, and the Federal University of Agriculture in Abeokuta (FUNAAB), Nigeria.
METHOD: A survey design, questionnaire as the tool for data collection was adapted and samples for the study were drawn from undergraduate students in two conveniently selected universities in South Africa and Nigeria. Overall, 450 undergraduate students were invited to participate in the survey; 380 respondents completed and returned the questionnaire, resulting in a response rate of 84.4%.
RESULTS: Most of the respondents from the sampled universities reported that they were aware of what constitutes unethical cyber behaviour. Furthermore, the participants revealed that they hardly received orientation at the universities on cyber behaviour. The challenges that the students faces were reported.
CONCLUSION: This study recommends that universities should sustain orientation and/or training programmes on cyber-ethics and cyber security awareness at the start of each academic year. The results of this study may spark further discussions and research on cyber technology access and use in contemporary society.
Keywords: cyber-ethics; ethical behaviour; South Africa; Nigeria; undergraduate students; 4th industrial revolution; Internet of things.
Introduction
Increasingly, universities strive to provide an enabling academic environment in which students can use cyber technology for educational purposes. Students in Nigeria and South Africa use information and cyber technologies on a daily basis to perform a broad range of academic tasks. There are ethical guidelines that govern the use of such technologies, and these, to some extent, guard against ethical violations. However, research indicates that students, generally, lack the understanding and awareness of the ethical use of cyber technology, leading to decisions taken without foreknowledge about ethical responsibilities and consequences (Aderibigbe 2020). Some of these unwholesome behaviours include intellectual property violations, copyright infringement, digital piracy and plagiarism. This new breed of intellectual property issues that are provoked by the steady commercialisation of the Internet and the proliferation of websites and information reflects unfair dealing and trespass on the ownership rights of intellectual property in the information utilisation chain. The levels of software piracy and counterfeiting in films, music, videos, books and images, amongst many other vices, have become increasingly troubling in recent years (Cummings 2017; Liu 2018; Okojie & Umoru 2017). These unethical cyber practices have become a common feature amongst students in the university environment and may have implications on their professional status in the larger corporate society.
There are relatively few research publications on cyber-ethics in an African context, and the current interest in unethical behaviour in research is relatively new in developing countries. Although there is a strong development of information ethics in Africa1 through African Network on Information Ethics (ANIE) and African Centre of Excellence for Information Ethics (ACEIE) based at the University of Pretoria in South Africa, not much has been published on the impact of information communication and technology (ICT) on African societies and the ethical use of these technologies (Ponelis & Holmner 2015). Furthermore, most studies on cyber-ethics as a concept in the literature and ICT, from an ethical point of view, draw their perspectives from the western philosophical tradition. A decade long (2006-2016) search on the open access database, Scopus, on cyber-ethics and related terms in the fields of computer science, social science, engineering, arts and humanities, medicine, business management and accounting produced a total of 137 publications, while the Web of Science produced 160 publications. The search analysis of these publications revealed that none of these research works emanated from Africa, particularly South Africa and Nigeria.
Universities perform the crucial role of bringing about change in society. Ethical and moral standards of integrity and responsibility cannot be divorced from the context in which this role is carried out. This applies to academic staff as well. In one incident, highly placed academic staff members were relieved of their jobs over plagiarism and falsification of data (Omotayo 2013). Thus, undergraduate students, as future leaders, cannot afford to neglect acceptable ethical responsibilities, which are central to their role as agents of change. It is in light of this that we felt the need to investigate unethical cyber behaviour in a bid to contribute to the existing body of knowledge in the field of cyber-ethics. Our study is informed by knowledge, experience and personal observations during the interaction with other academic staff on the issue of ethical violations. The study was motivated by the desire to contribute to solving the problem of unethical cyber behaviour by finding ways to motivate students towards strict adherence to ethical guidelines.
In view of the limited research output in this research area within Nigeria and South Africa, this study was designed to determine the cyber behaviour of students in the two countries, to further support the ongoing efforts to curb the unethical use of cyber technologies in academia. The primary aim of this study was to determine the awareness and challenges of cyber-ethics behaviour among students from two selected universities in Nigeria and South Africa.
Purpose of the study
The objectives of this study were to:
-
determine undergraduate students' awareness of cyber-ethics requirements at the University of Zululand, South Africa, and at the Federal University of Agriculture in Abeokuta, Nigeria
-
identify the types of unethical cyber behaviour that are prevalent in the studied universities
-
verify the influence of the Theory of Planned Behaviour (TPB) on ethical cyber behaviour
-
identify the challenges faced by undergraduate students in their efforts to act ethically in cyberspace at the two universities.
Literature review
The phrase cyber technology ethics was chosen because it reflects the current trend in research attention to ICT. The review of cyber technology ethics or cyber-ethics was based on the more established fields of computer and information ethics. Computer and information ethics, which as a branch of applied ethics, can be understood 'as that field of study that analyses social and ethical impacts of ICT' (Bynum 2008:32). The more specific term, cyber-ethics, is a dynamic field of study that identifies:
Ethical issues in the use of cyber technology, the corresponding moral, legal and social implications and the evaluation of the social policies and laws that are framed in response to issues generated by its impact on the society. (Tavani 2013:6)
The study of cyber-ethics, which includes computer ethics, has grown significantly since the early 1980s, when Moor (1985) and Johnson (1985) published seminal papers that helped define the field, and ever since, the field has grown in strength and recognition amongst communities of Information Science (IS) scholars (Onyancha 2015). Cyber-ethics, as a field of applied ethics, is related to information ethics, a more general field, which includes computer ethics, media ethics, library ethics and bioinformation ethics (Brey 2009).
Research has correlated cyber-ethics to various disciplines, and attitudes and behaviours related to cybercrime, such as software program piracy, online porn, non-accredited surveillance, identification robbery and privacy violation, hacking/carding, right/left on-line extremism, spamming, plagiarism and copyright infringement, fraudulent online banking, cybersquatting and cyber stalking, flaming and trolling, writing and dissemination of viruses (ed. Quigley 2005; Tavani 2013). These violations all point to the concept of cyber-ethical behaviour, as expressed in academic environments.
It has been found that the property of cyber technology leads to unavoidable ethical problems as a result of policy and conceptual vacuums; most challenges of these impacts are in the realms of privacy, accuracy, property and accessibility (Mason 1986; Moor 1985). In this consideration, unethical cyber behaviours, such as computer hacking and digital or Internet piracy, are the concerns of this study. Recent studies conducted in multiple countries revealed that computer hacking and digital piracy have become more prevalent amongst undergraduate students (Burruss, Holt & Bossler 2019; Udris 2017).
Various studies conducted in the university context have examined factors influencing cyber-ethical behaviour (Alleyne, Soleyn & Harris 2015; Marcum, Higgins & Nicholson 2017; Martin & Woodward 2011; Thomas & Ahyick 2010). Generally, the results from these studies revealed that students did not regard unethical use of cyber technology as any form of violation. Lau, Yuen and Park (2013) pointed out that unethical behaviours are typical and prevalent, yet understudied and/or underexplored among IS researchers in developing countries. As such, further attention is needed to address the literature gap.
Theoretical approaches to cyber-ethical studies have relied on social psychology models of behaviour change that seek to identify determinants and pathways of the influence of cyber-ethics behaviour, such as ethical and unethical use of cyber technology (Aderibigbe & Ocholla 2018). To extend the frontier of knowledge in the study of cyber-ethical behaviour, this study adapted the TPB of Ajzen (1991, 2011) to provide a more elaborate and practical factors that could contribute to cyber-ethical issues in Africa. We have discussed TPB in detail in a recent publication (Aderibigbe, Ocholla & Britz in press).
The TPB (Ajzen 1985, 1991) is an extension of the Theory of Reasoned Action (TRA) (Ajzen & Fishbein 1980). The TRA assumes that attitude and subjective norms are the determinants of the individual intentions to carry out a given behaviour. In other words, the intentions to perform behaviour correlate with actual behaviour. This theory has provided a strong support for determining volitional behaviour and has been used by researchers in various fields of human endeavour to understand the social cognitive processes of human behavioural decision-making.
The addition of Perceived Behavioural Control (PBC) to the TRA brought about the TPB (Ajzen 1991). The TPB assumes that behavioural intention is the strongest determinant of actual behaviour, whilst the direct determinants of individual behavioural intentions are their attitudes, subjective norms and PBC (Ajzen 1991). The TPB (Ajzen 1991) and its predecessor the TRA (Ajzen & Fishbein 1980) have been used extensively in research on a wide range of social and human behavioural studies, particularly those associated with the ethical use of cyber technology (Attuquayefio & Addo 2014; Goles et al. 2008; Taylor & Todd 1995); digital piracy (Liao, Lin & Lin 2010; Yoon 2010); unethical behaviour (Chatterjee, Suprateek & Joseph 2015); perception of cyber technology ethics (Chiang & Lee 2011); academic dishonesty (Harding et al. 2007) and cyber data privacy (Morgan 2015).
In practice, researchers have generally considered the TPB as a choice for explaining behaviours where ethical considerations are an issue (Aderibigbe & Ocholla 2018). In addition, the theory is widely applied to multitude of fields such as medicine, geography and public relations. In conclusion, the TPB leans to diversify and theory application, because it has been widely applied to cyber-ethical research and shows a strong predictor for behavioural intention and behaviour (Aderibigbe 2020; Aderibigbe et al. in press).
Methodology
The study adopted the pragmatic - both quantitative and qualitative - research methods, particularly survey research. Using cluster sampling, sample for the study was drawn from undergraduate students in two selected universities in South Africa and Nigeria, where each of the selected institution was a cluster, that is, University of Zululand (UNIZULU) and Federal University of Agriculture in Abeokuta (FUNAAB). The respondents were drawn from all the faculties in UNIZULU and all the colleges in FUNAAB. Data collected using the quantitative instrument were coded, and the analyses were carried out using the statistical packages for social sciences (SPSS), version 25.0. Overall, 450 undergraduate students were invited to participate in the survey; 380 respondents completed and returned the questionnaire, resulting in a response rate of 84.4%.
Given that the total number of undergraduate students at the UNIZULU 2016/2017 (UNIZULU Fact & Figure 2017) was 15 542, and the total number of undergraduate students at the Federal University of Agriculture, Abeokuta, 2017, was 15 847, the total population of the two universities was calculated as 15 542 + 15 847 = 31 389. Furthermore, to ensure that each respondent had an equal chance of being surveyed (Neuman 2011), the study adopted probability proportionate to size (PPS) in the selection of sample from each cluster (Nueman 2011) (see Table 1).
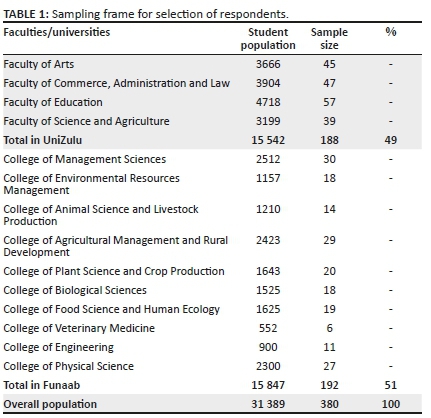
The overall total numbers of the study population at both universities were 31 389. The study aimed at a minimum sample size of 380, at a confidence level of 95% and a confidence interval of 5% based on the sample size calculation. However, we invited up to 450 to make provisions for setting aside incomplete and unreliable responses.
Ethical consideration
The study received ethical clearance from the University of Zululand's Research Ethics Committee: UZREC 17110-030 PGD 2016/116
Findings
This section focuses on the four research questions as follows.
What is the level of awareness of unethical cyber behaviour amongst students at the University of Zululand, South Africa and at the Federal University of Agriculture in Abeokuta, Nigeria?
The questionnaire responses revealed that the undergraduate students were mostly aware of unethical behaviour with regard to cyber technology at the selected universities in South Africa and Nigeria. This was corroborated by the interview results, which established that students from both universities under investigation were mostly aware of unethical cyber behaviour. With respect to orientation and training, it was revealed that most students had received training in their first year at both universities on the use of cyber technology for educational purposes only and not on ethical use of cyber technology. It is noteworthy that the respondents only received training on the application of computers, laptops and other hand-held devices for learning purposes. Whilst this helps students to understand the benefits of the devices, the implication is that the negative applications of those devices to the network, which could address issues of cyber-ethics, were not included in the orientation programmes. The institutions' orientation programmes were observed to be too focused on technological skills and the educational applications of those skills, rather than the consideration of the implications of the risks that could arise from unethical cyber behaviour. In other words, the programmes do not address the risk to the integrity of the cyber infrastructure and the image of the universities.
What are the types of unethical cyber behaviour exhibited by undergraduate students in the two universities?
The impressive and remarkable nature of cyber technology, which serves students as a revolutionary medium of expression and provides access to globalised information, comes with new challenges. The increasingly limitless access to the Internet on university campuses has made cyber piracy and other forms of unethical cyber behaviour amongst students prevalent. Multinational studies have underscored the difficulties in identifying and policing cyber infringements, especially where the policies and laws are flexible (International Centre for the Prevention of Crime ICPC 2018:121; International Telecommunication Union ITU 2012:75).
Table 2 reveals the most prevalent form of unethical cyber behaviour amongst undergraduate students at the two universities to be cyber piracy, which produced the highest mean score of m = 3.6, SD = 1.5 and m = 3.6, SD =1.3 amongst students in Nigeria and South Africa, respectively. This indicates that cyber piracy is the common practice at the two universities. Following this is cyber smearing with m = 3.6, SD = 1.4 for Nigeria and m = 3.7, SD = 1.3 for South Africa and cybersex behaviour, with m = 3.5, SD = 1.4 for Nigeria, and m = 3.2, SD = 1.5 for South Africa. These findings are corroborated in several studies that have underscored the prevalence of cyber piracy and other forms of cyber violations amongst undergraduate students (Chavarria et al. 2016; Cilliers 2017). The use of cyber technology, especially computers, smart devices and the Internet, has become part of the daily routine at most university campuses. The frequency of this usage has led to the escalating nature of ethical issues among students.
What is the impact of the theory of planned behaviour on the ethical cyber intention of undergraduate students in the two universities?
As also discussed elsewhere (Aderibigbe et al. in press), overall, the significant levels of the results established that the three variables (attitude, subjective norms and PBC) were individually statistically significant in influencing students' ethical cyber behaviour. The regression results established an adjusted R2 value of 0.517 for Nigeria and 0.543 for South Africa. Both were significant at the 0.05 level (0.000 < 0.05). These results indicate that the three independent variables (attitude, subjective norms and PBC of ethical cyber behaviour) jointly (as indicated by the R2) explained or predicted 51.7% of the variations in the influence of the TPB on undergraduate ethical cyber behaviour in Nigeria, and 54.3% of the variations in the influence of the TPB on undergraduate ethical cyber intention and eventual behaviour in South Africa.
Secondly, the standardised coefficients (beta values), which indicated the relative strength of each factor in the prediction of ethical intention, showed that PBC contributed the most to the prediction of ethical cyber intention and eventual behaviour of undergraduate students in Nigeria (beta value = 0.747) and in South Africa (beta value = 0.601). These results imply that all three constructs of the TPB exert significant influence on predicting ethical cyber intention and behaviour.
Subjective norms are an important attribute when determining ethical intention with respect to cyber technology. Hence, it is logical to assume that reference groups, such as parents, friends or faculty members, who students perceive to be important in their daily routines, have influential roles to play in their formation of ethical and unethical cyber behaviour. In other words, subjective norms may represent the 'social pressure' necessary to encourage either positive or negative intention in the cyber behaviour of students. Accordingly, this research suggests targeting these important reference groups when planning a campaign strategy or creating a persuasive message against unethical cyber behaviour. Role models, such as parents in the home and staff members in the ICT sector or university faculties, could act as a good starting point for effectively instilling negative attitudes towards the misuse of cyber technology by students.
What are the challenges faced by undergraduate students in their efforts to act ethically in cyberspace at the two universities?
Many challenges were identified as represented on Table 3.
The findings in Table 3 revealed that undergraduate students in Nigeria face more challenges in their efforts to act ethically correct in cyberspace than those in South Africa. The challenges include:
-
social negative influence
-
ease of performing illegal activities
-
lack of adequate security measure to ensure compliance with cyber-ethics policy
-
lack of enough orientation and education on implications of ethical violations
-
over-packed teaching and learning curriculum
-
contradiction between copyright and freedom of information
-
lack of cyber morality and ethical conduct in the use of cyber technology
-
management bureaucratic processes
-
breaches in confidentiality and network security
-
lack of time and commitments
-
lack of publicised policies about misuse of cyber technology
-
lack of ethical consideration and consequence of violations
-
lack adequate training for teaching cyber-ethics
-
institutional growth is taxing existing cyber infrastructure
-
financial constraints
-
risk of anonymity of users.
Only in the lack of policy guidance on appropriate cyber behaviour do students in South Africa have higher level of prevalence. This implies that Nigerian undergraduate students are more prone to various cyber-ethical challenges that affect their behaviour. A similar pattern of results was obtained by Ocholla (2009) on the challenges of information ethics in Africa, in which he also cited inadequate legislation and weak enforcement, lack of expertise, and lack of space in the curriculum, among others.
The findings of this study also cast a new light on the previous findings by National Cyber-ethics, Cybersafety, Cybersecurity Baseline (2009), in which it was also revealed that financial constraints, time commitments, bureaucratic processes and over-packed curriculum were the challenges frustrating ethically correct behaviour of university students. Similarly, Walczak et al. (2010) in their study showed that the faculty lack adequate training and understanding to teach cyber-ethics. They equally noted the inconsistency in policy instruments, within the academic, that could deal with cyber-ethical misbehaviour.
This bolsters the works of Monahan (2012) that ethical or unethical behaviour takes place as a result of ethical dilemma, which could also be the various challenges confronting the efficient use of cyber technologies. This could be one of the major reasons why studies such as those of Vallor (2010); Zhang, Lesley and Geoffrey (2010); Calvani et al. (2012); Baykara, Demir and Yaman (2015) and Plaisance (2013) noted the need for the consideration of moral dimensions in cyber technology usage, especially among students. This supports the work by the University of North Carolina (2014) that students are faced with various cyber-ethical problems occasioned by personal and situational factors that influence against acting ethically correct in the cyberspace of universities.
Conclusion
Based on the results, the most relevant conclusions are the following: students appeared to be unaware of ethical cyber-ethics requirements and training at the selected universities. Amongst the several types of unethical cyber behaviour, cyber piracy, cybersex/pornography and privacy violation 'lead the pack'. The constructs of the TPB were found to have a significant influence on the ethical cyber behaviour of undergraduate students in this study, as the three variables (attitude, subjective norms, and PBC and intention) were individually statistically significant in influencing students' cyber behaviour. The study has highlighted many challenges (Table 2) that require attention. The findings in this report are subject to at least two limitations. Firstly, there was insufficient explanation as to why some moral philosophies did not impact the ethical judgement and behavioural intention of the students in cyber technology use and behaviour. The use of English, as a second or third language of all the respondents in this study, could also have led to the misinterpretation of some parts of the questionnaire.
The study recommends the following: extensive and regular awareness education; the development of policies dealing specifically with cyber-ethics and the responsible use of cyber technology; devising appropriate methodology to educate the students; the use of education rather than punishment; and other strategies that can be used to train users on how to behave ethically in cyberspace. Cyber-ethics awareness would be more effective if it could account for the factor of self-efficacy of the students as cyber technology users and provide some reward to those who adhere to ethical conduct on the university network. This study should inform cyber-ethics research, policy, teaching and learning, largely within the academic environments.
Acknowledgements
A shorter version of this article was presented at the Fifth International Professional Forum 'Book, Culture, Education, Innovation', Crimea 2019, Russia. The authors wish to acknowledge the University of Zululand (UNIZULU) in South Africa, and Federal University of Agriculture in Abeokuta, Nigeria, for supporting the PhD study in different ways, particularly the UNIZULU for funding the research and travel for this conference presentation.
Competing interests
The authors have declared that no competing interests exist.
Authors' contributions
All authors contributed equally to this work.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Aderibigbe, N.A., 2020, 'Cyber ethical behaviour of university students: An overview of university of Zululand, South Africa and Federal university of agriculture, Abeokuta, Ogun state, Nigeria', Journal of Applied Information Science and Technology 13(1), 86-106. [ Links ]
Aderibigbe, N.A. & Ocholla, D.N., 2018, 'Cyber-ethics and behavioural theories: A literature review', in International Conference on Information and Knowledge Management 2nd: 2018, The Technical University of Kenya, Nairobi, Kenya, August 21-24, 2018, pp. 268-277.
Aderibigbe, N.A., Ocholla, D.N. & Britz, J., (in press), 'Differences in ethical cyber behavioural intention of Nigerian and South African students: A multi-group analysis based on the theory of planned behaviour', Libri-International Journal of Libraries and Information Studies.
Ajzen, I., 1985, 'From intentions to actions: A theory of planned behaviour', In J. Kuhl, J. Beckmann (eds.), Action control, Springer, Berlin, pp. 11-39.
Ajzen, I., 1991, 'The theory of planned behaviour', Organizational Behaviour and Human Decision Processes 50(2), 179-211. https://doi.org/10.1016/0749-5978(91)90020-T [ Links ]
Ajzen, I., 2011, 'The theory of planned behaviour: Reactions and reflections', Psychology and Health 26(9), 1113-1127. https://doi.org/10.1080/08870446.2011.613995 [ Links ]
Ajzen, I. & Fishbein, M., 1980, Understanding attitudes and predicting social behaviour Prentice-Hall, Englewood Cliffs, N.J.
Alleyne, P., Sherlexis, S. & Terry, H., 2015, 'Predicting accounting students' intentions to engage in software and music piracy', Journal of Academic Ethics 13(4), 291-309. https://doi.org/10.1007/s10805-015-9241-7 [ Links ]
Attuquayefio, S.N. & Addo, H., 2014, 'Using the UTAUT model to analyse students' ICT adoption', International Journal of Education and Development using ICT 10(3), 75-86. [ Links ]
Baykara, Z.G., Demir, S.G. & Yaman, S., 2015, 'The effect of ethics training on students recognizing ethical violations and developing moral sensitivity', Nursing Ethics 22(6), 661-675. https://doi.org/10.1177/0969733014542673 [ Links ]
Brey, P.A.E., 2007, 'Computer ethics in (higher) education', in G. Dodig-Crnkovic, S. Stuart (eds.), Computation, information cognition: The Nexus and the Liminal, pp. 341-363, Cambridge Scholars Press, Cambridge.
Burruss, G.W., Holt, T.J. & Bossler, A., 2019, 'Revisiting the suppression relationship between social learning and self-control on software piracy', Social Science Computer Review 37(2), 178-195. https://doi.org/10.1177/0894439317753820 [ Links ]
Bynum, T.W., 2008, 'Milestones in the history of information and computer ethics', in The handbook of information and computer ethics, vol. 25.
Bynum, T.W., 2008, 'Milestones in the history of information and computer ethics', in K.E Himma & H.T Tavani (eds.), The handbook of information and computer ethics, pp. 25-48, John Wiley & Sons Inc, New Jersey, NY.
Calvani, A., Fini, A., Ranieri, M. & Picci, P., 2012, 'Are young generations in secondary school digitally competent? A study on Italian teenagers', Computers & Education 58(2), 797-807. https://doi.org/10.1016/j.compedu.2011.10.004 [ Links ]
Chatterjee, S., Suprateek, S. & Joseph, S.V., 2015, 'The behavioural roots of information systems security: Exploring key factors related to unethical IT use', Journal of Management Information Systems 31(4), 49-87. https://doi.org/10.1080/07421222.2014.1001257 [ Links ]
Chavarria, J.A., Andoh-Baidoo, F.K., Midha, V. & Hughes, J., 2016, 'Software piracy research: A cross-disciplinary systematic review', Communications of the Association for Information Systems 38(1), 31. https://doi.org/10.17705/1CAIS.03831 [ Links ]
Chiang, L. & Lee, B., 2011, 'Ethical attitude and behaviours regarding computer use', Ethics & Behaviour 21(6), 481-497. https://doi.org/10.1080/10508422.2011.622181 [ Links ]
Cilliers, L., 2017, 'Evaluation of information ethical issues among undergraduate students: An exploratory study', South African Journal of Information Management 19(1), a767. https://doi.org/10.4102/sajim.v19i1.767 [ Links ]
Cummings, A.S., 2017, Democracy of sound: Music piracy and the remaking of American copyright in the twentieth century, Oxford University Press, New York, NY.
Goles, T., Jayatilaka, B., George, B., Parsons, L., Chambers, V., Taylor, D. & Brune, R., 2008, 'Softlifting: Exploring determinants of attitude', Journal of Business Ethics 77(4), 481-499. https://doi.org/10.1007/s10551-007-9361-0 [ Links ]
Harding, T.S., Matthew, J.M., Finelli, C.J. & Carpenter, D.D., 2007, 'The theory of planned behaviour as a model of academic dishonesty in engineering and humanities undergraduates', Ethics & Behaviour 17(3), 255-279. https://doi.org/10.1080/10508420701519239 [ Links ]
International Centre for the Prevention of Crime, 2018, 6th international report on crime prevention and community safety: Preventing Cybercrime 2018, International Centre for the Prevention of Crime, Montreal, Canada, (ICPC), p. 1.
International Telecommunication Union, 2012, Understanding cybercrime: Phenomena, challenges and legal response September2012, International Telecommunication Union (ITU), Geneva, p. 1.
Johnson, D.G., 1985, Computer ethics, Prentice Hall, Englewood Cliffs, NJ.
Lau, G.K.K., Yuen, A.H.K. & Park, J., 2013, 'Toward an analytical model of ethical decision making in plagiarism', Ethics & Behaviour 23(5), 360-377. https://doi.org/10.1080/10508422.2013.787360 [ Links ]
Liao, C., Hong-Nan, L. & Yu-Ping, L., 2010, 'Predicting the use of pirated software: A contingency model integrating perceived risk with the theory of planned behaviour', Journal of Business Ethics 91(2), 237-252. https://doi.org/10.1007/s10551-009-0081-5 [ Links ]
Liu, H., 2018, 'In the shadow of criminalisation: Intellectual property criminal law, enforcement institutions and practices in China and the United States', Information & Communications Technology Law 27(2), 185-220. https://doi.org/10.1080/13600834.2018.1458451 [ Links ]
Marcum, C.D., Higgins, G.E. & Nicholson, J., 2017, 'I'm watching you: Cyber stalking behaviors of university students in romantic relationships', American Journal of Criminal Justice 42(2), 373-388. https://doi.org/10.1007/s12103-016-9358-2 [ Links ]
Martin, N.L. & Woodward, B.S., 2011, 'Computer ethics of American and European information technology students: A cross-cultural comparison', Issues in Information Systems 12(1), 78-87. [ Links ]
Mason, R.O., 1986, 'Four ethical issues of the information age', MIS Quarterly 10(1), 5-12. https://doi.org/10.2307/248873 [ Links ]
Monahan, K., 2012, 'A review of the literature concerning ethical leadership in organizations', Emerging Leadership Journeys 5(1), 56-66. [ Links ]
Moor, J.H., 1985, 'What is computer ethics?', Metaphilosophy 16(4), 266-275. https://doi.org/10.1111/j.1467-9973.1985.tb00173.x [ Links ]
Morgan, J.A., 2015, 'Exploring senior citizen perceptions of their cyber data privacy and security', in Doctoral dissertation, Capella University, viewed from https://search.proquest.com/openview/63a8733c41122f856c1d20c5b1680c46/1?pq-origsite=gscholar&cbl=18750&diss=y. [ Links ]
National Cyber Security Alliance, 2009, National cyber-ethics, cybersafety, Cybersecurity Baseline Study, viewed from http://staysafeonline.mediaroom.com/index.php?s=67&item=44.
Neuman, W.L., 2011, 'Field research and focus group research', in Social Research Methods: Qualitative and Quantitative Approaches, pp. 420-463, Pearson, Boston, MA.
Ocholla, D.N., 2009, 'Information ethics education in Africa. Where do we stand?', The International Information & Library Review 41(2), 79-88. [ Links ]
Okojie, A.E. & Umoru, G.L., 2017, 'Counterfeiting and piracy: Challenges to effective protection of intellectual property rights in Nigeria', South African Intellectual Property Law Journal 5(1), 115-142. [ Links ]
Omotayo, A., 2013, 'Intellectual property rights protection and how to avoid the trap of plagiarism', [Pamphlet], Federal University of Agriculture, Abeokuta.
Onyancha, O., 2015, 'An informetrics view of the relationship between internet ethics, computer ethics and cyber-ethics', Library Hi Tech 33(3), 387-408. https://doi.org/10.1108/LHT-04-2015-0033 [ Links ]
Plaisance, P.L., 2013, Media ethics: Key principles for responsible practice, Sage, Thousand Oaks, CA.
Ponelis, S.R. & Holmner, M.A., 2015, 'ICT in Africa: Building a better life for all', Information Technology for Development 21(2), 163-177. https://doi.org/10.1080/02681102.2015.1010307 [ Links ]
Quigley, M. (ed.), 2005, Information security and ethics: Social and organizational issues, Idea Group Inc (IGI), Hershey, PA.
Tavani, H.T., 2013, 'Cyber-ethics', in A.L.C. Runehov & L. Oviedo (eds.), Encyclopaedia of sciences and religions, pp. 565-570, Springer, Dordrecht.
Taylor, S. & Todd, P.A., 1995, 'Understanding information technology usage: A test of competing models', Information Systems Research 6(2), 144-176. https://doi.org/10.1287/isre.6.2.144 [ Links ]
Thomas, T. & Ahyick, M., 2010, 'Can we help information systems students improve their ethical decision making?', Interdisciplinary Journal of Information, Knowledge & Management 5, 209-224. https://doi.org/10.28945/1160 [ Links ]
Udris, R., 2017, 'Psychological and social factors as predictors of online and offline deviant behavior among Japanese adolescents', Deviant behavior 38(7), 792-809. https://doi.org/10.1080/01639625.2016.1197689 [ Links ]
University of North Carolina, 2014, Student services: Responding to issues and challenges: The fifth compendium of papers, University of North Carolina, General Administration, Chapel Hill, NC.
Vallor, S., 2010, 'Social networking technology and the virtues', Ethics and Information technology 12(2), 157-170. https://doi.org/10.1007/s10676-009-9202-1 [ Links ]
Walczak, K., Finelli, C., Holsapple, M., Harding, T., Carpenter, D., Errington, T.M. et al., 2010, 'Institutional obstacles to integrating ethics into the curriculum and strategies for overcoming them', in ASEE Annual Conference and Exposition 16(3), 15. 749, 1-14. [ Links ]
Yoon, C., 2010, 'Ethical decision-making in the Internet context: Development and test of an initial model based on moral philosophy', Computers in Human Behaviour 27(6), 2401-2409. https://doi.org/10.1016/j.chb.2011.08.007 [ Links ]
Zhang, A.T., Lesley, P.L. & Geoffrey, D., 2010, 'Key influences of cyberbullying for university students', viewed 22 September 2016, from http://www.pacis-net.org/file/2010/S01-01.pdf.
 Correspondence:
Correspondence:
Nurudeen Aderibigbe
rabshittu@yahoo.com
Received: 20 July 2019
Accepted: 16 July 2020
Published: 08 Oct. 2020
1 . The first African Information Ethics Conference were held in Tshwane, South Africa, 05-07 February 2007.
^rND^sAderibigbe^nN.A.^rND^sAjzen^nI.^rND^sAjzen^nI.^rND^sAlleyne^nP.^rND^sSherlexis^nS.^rND^sTerry^nH.^rND^sAttuquayefio^nS.N.^rND^sAddo^nH.^rND^sBaykara^nZ.G.^rND^sDemir^nS.G.^rND^sYaman^nS.^rND^sBurruss^nG.W.^rND^sHolt^nT.J.^rND^sBossler^nA.^rND^sCalvani^nA.^rND^sFini^nA.^rND^sRanieri^nM.^rND^sPicci^nP.^rND^sChatterjee^nS.^rND^sSuprateek^nS.^rND^sJoseph^nS.V.^rND^sChavarria^nJ.A.^rND^sAndoh-Baidoo^nF.K.^rND^sMidha^nV.^rND^sHughes^nJ.^rND^sChiang^nL.^rND^sLee^nB.^rND^sCilliers^nL.^rND^sGoles^nT.^rND^sJayatilaka^nB.^rND^sGeorge^nB.^rND^sParsons^nL.^rND^sChambers^nV.^rND^sTaylor^nD.^rND^sBrune^nR.^rND^sHarding^nT.S.^rND^sMatthew^nJ.M.^rND^sFinelli^nC.J.^rND^sCarpenter^nD.D.^rND^sLau^nG.K.K.^rND^sYuen^nA.H.K.^rND^sPark^nJ.^rND^sLiao^nC.^rND^sHong-Nan^nL.^rND^sYu-Ping^nL.^rND^sLiu^nH.^rND^sMarcum^nC.D.^rND^sHiggins^nG.E.^rND^sNicholson^nJ.^rND^sMartin^nN.L.^rND^sWoodward^nB.S^rND^sMason^nR.O.^rND^sMonahan^nK.^rND^sMoor^nJ.H.^rND^sOcholla^nD.N.^rND^sOkojie^nA.E.^rND^sUmoru^nG.L.^rND^sOnyancha^nO.^rND^sPonelis^nS.R.^rND^sHolmner^nM.A.^rND^sTaylor^nS.^rND^sTodd^nP.A.^rND^sThomas^nT.^rND^sAhyick^nM.^rND^sUdris^nR.^rND^sVallor^nS.^rND^sWalczak^nK.^rND^sFinelli^nC.^rND^sHolsapple^nM.^rND^sHarding^nT.^rND^sCarpenter^nD.^rND^sErrington^nT.M.^rND^sYoon^nC.^rND^1A01^nAlfred H.^sMazorodze^rND^1A01^nSheryl^sBuckley^rND^1A01^nAlfred H.^sMazorodze^rND^1A01^nSheryl^sBuckley^rND^1A01^nAlfred H^sMazorodze^rND^1A01^nSheryl^sBuckleyORIGINAL RESEARCH
A review of knowledge transfer tools in knowledge-intensive organisations
Alfred H. Mazorodze; Sheryl Buckley
School of Computing, College of Science, Engineering and Technology, University of South Africa, Pretoria, South Africa
ABSTRACT
BACKGROUND: Knowledge transfer is very important in knowledge-intensive organisations in both developed and developing countries. A knowledge-intensive organisation is an organisation whose operations depend on specialised knowledge. Knowledge-intensive organisations lose intellectual property when experienced employees retire from their jobs. To avoid knowledge loss, skills and expertise should be transferred from experts to non-experts on time. Knowledge transfer tools allow sharing of tacit knowledge between and amongst staff members. The study provides an analysis and review of the most effective knowledge transfer tools in knowledge-intensive organisations because an organisation's success is based on its ability to transfer knowledge.
OBJECTIVES: The study had two main objectives: to identify and review knowledge transfer tools used in knowledge-intensive organisations and to recommend the best knowledge transfer tool that can be used in organisations for the purpose of enhanced competitive advantage.
METHOD: A well-structured questionnaire was used to collect quantitative data from the research participants in knowledge-intensive organisations in Namibia.
RESULTS: The results indicate that the most effective knowledge transfer tool in knowledge-intensive organisations is a community of practice; 40% of the participants considered the tool effective, and 27% considered it to be very effective. This was followed by the mentoring tool, which was ranked 54% effective and 11% very effective by the participants because it exposes mentees to new ideas and new ways of thinking. Storytelling was ranked 28% effective and 17% very effective because it is a natural learning process. Succession plans were ranked 21% effective and 12% very effective because having succession plans in place on time is essential for organisational success. Coaching and knowledge repositories were ranked below 20% on knowledge transfer effectiveness. From the findings, we conclude that the most effective tool for knowledge transfer in knowledge-intensive organisations is communities of practice (CoP) followed by mentoring, storytelling, succession plans, coaching and finally knowledge repositories.
CONCLUSION: The most effective knowledge transfer tool in knowledge-intensive organisations is Communities of Practice, followed by mentoring, storytelling, succession plans and lastly coaching. Communities of Practice are important for knowledge transfer in that they encourage and promote teamwork through discussions and knowledge sharing amongst employees. The study therefore recommends the creation of such Communities of Practice in knowledge-intensive organisations for effective knowledge transfer and sharing.
Keywords: communities of practice; coaching; knowledge repositories; knowledge transfer; mentoring; storytelling; succession planning.
Introduction
Knowledge is an organisation's largest asset, and it must be managed effectively. Knowledge can be obtained either by transmission from the person who has it, by instruction or by extracting it from experience (Kim, Byung & Lee 2012). The European Framework for Knowledge Management (2015) define knowledge as an amalgamation of data and information, where expert opinion and experience are added to result in a valued asset that could be used to improve an organisation's decision-making capabilities. Data is described by Pearlson and Saunders (2004) as discrete and objective facts that are not organised and processed and do not have any specific meaning. Information is data that have been shaped into a form that is meaningful and useful to humans. Turban, Rainer and Potter (2005) stress that knowledge is data and/or information that has been processed and organised to convey understanding, experience and expertise as they apply to a current problem. Thus, knowledge consists of a mixture of information, values, rules and experiences from different sources. The much-needed knowledge resides in the heads of people, and it greatly influences organisational success.
According to Lievre and Tang (2015), knowledge transfer activities help employees to transfer expertise to others on time. During knowledge transfer, people collaborate and exchange important ideas. Some of the knowledge transfer tools or activities commonly used in knowledge-intensive organisations include communities of practice (CoP), succession plans, coaching, storytelling, knowledge repositories, mentoring and job rotation, amongst others (Wenger 2014; Whyte & Classen 2012). Knowledge transfer activities are necessary and can be fixed into the organisational structures and processes. We can therefore infer that knowledge transfer activities allow sharing of important knowledge in organisations, a point that Reiche (2011) also emphasises.
This review only looks at the knowledge transfer tools or activities that might accelerate innovation and boost productivity in knowledge-intensive organisations. It is important to highlight here that the knowledge transfer tools analysed and discussed here are not the end-all. The research was conducted with the following aims and objectives:
-
to identify and review the knowledge transfer tools used in knowledge-intensive organisations
-
to analyse and recommend the best knowledge transfer tool that can be used in knowledge-intensive organisations for the purpose of enhanced competitive advantage.
Theoretical framework and literature review
Nonaka and Takeuchi (1995) classify knowledge into two specific categories: 'tacit' and 'explicit'. Tacit knowledge is resident in an individual's mind. Tacit knowledge is deeply rooted in an individual's experiences, ideals, values and emotions (Nonaka & Takeuchi 1995:8). Explicit knowledge refers to knowledge that can be expressed and explained meaningfully in words and numbers (Davenport & Prusak 2000). Explicit knowledge can be communicated to other parties, and it can be processed by humans or machines programmed to perform the tasks. It is vital to understand these two types of knowledge and the mechanisms organisations engage to manage them. Becerra-Fernandez and Sabherwal (2010) made the useful observation that it was difficult to explicate tacit knowledge and then make it accessible for use by others.
Tacit knowledge can be transferred through mentorship and coaching (Davenport & Prusak 2000). With explicit knowledge, knowledge transfer is performed via services and documented processes, through which one appropriates the protocols and eventually takes ownership of this explicit knowledge. Knowledge transfer involves the focussed and purposeful communication of knowledge from the sender to a known receiver (King 2006). Knowledge transfer is considered by Knowledge Management (KM) practitioners as an integral part of every organisation. Knowledge Management practitioners (Grant 1996; Jang & Ko 2014; Leibowitz 2012; Liu 2016; Nonaka & Takeuchi 1994) concur that for knowledge to have an organisational impact, it must be transferred or shared. Kalling (2003) maintains that the organisation's success can be based on its ability to transfer knowledge. In line with this view, Hendriks (2009) contends that knowledge transfer provides opportunities to enhance the organisation's competitive advantage.
Literature review
McDonald and Cater-Steel (2016) describe CoP as an integrated approach for transferring knowledge through formal and/or informal groups. Schiavone (2013) adds that CoP can be formally established or can evolve spontaneously. Wenger (2014) adds that CoP are powerful manifestations of informal learning. Communities of practice are therefore effective knowledge transfer tools, as they permit employees to manage change by clarifying their roles in those organisations. These CoP have the ability to link professionals for knowledge-sharing purposes in knowledge-intensive organisations. A CoP can be Information Technology (IT)-based or non-IT, depending on the characteristic considerations of the community members (Heeyoung & Ilsang 2014). According to Durst and Wilhelm (2012), succession plans identify and develop employees to fill in positions in organisations at the right time. Knowledge-intensive organisations lose the knowledge and skills of experts when they retire from their jobs. Rothwell (2010) argues that the heart of succession plans is the epicentre of KM. Succession plans are an ongoing process that focusses on the knowledge transfer necessitated by an ageing workforce. Knowledge transfer through succession plans represents a proactive step towards employee empowerment, which leads to increased organisational responsiveness.
Coaching is a knowledge transfer tool that focusses on immediate problems and opportunities. Abbott (2014) argues that coaching entails guiding the trainee so as to fuse the operational knowledge that increases organisational performance. Management Mentors (2019) underscore the significance of coaching to perfect employee skills in an organisation. Stuhlmann (2012) defines storytelling as narratives that constitute operational knowledge. Research by Whyte and Classen (2012) proves that storytelling is a vital tool for transferring tacit knowledge, allowing sharing of deeper knowledge, which may boost the organisation's knowledge. An organisation that shares knowledge amongst its staff will certainly benefit from the knowledge-sharing efforts. Leblanc and Hogg (2010) argue that storytelling as a knowledge transfer technique allows organisations to discover tacit knowledge, as it is a natural learning process. Moreover, storytelling can be used to share lessons learnt from projects with coworkers who did not participate in the activity. Thus, storytelling can be used to build a shared understanding amongst employees in an organisation.
As defined by Leibowitz (2012), knowledge repositories are online storehouses of expertise and documentation about a particular domain. Knowledge repositories can be considered online self-help, as they make it easy to find relevant information and resources. Liu (2016) advises that organisations must develop means of documenting organisational knowledge. Relational databases are some of the technologies commonly used in building knowledge repositories for increased organisational efficiency. The American Productivity and Quality Center (APQC) (2010) adds that knowledge repositories support artificial intelligence technologies, including those used for electronic discussion groups, decision support systems, databases, expert systems and best practices. Mentoring is also considered a vital tool for knowledge transfer from experts to non-experts (Young 2013). The main aim of mentoring is to encourage that the individual reflect on the job as a whole (Rooney 2014). In most modern organisations, mentoring creates an organisational culture, which improves organisational performance. Knowledge transfer is highly likely to take place in a decentralised organisational structure, a point which is quite consistent in the literature (Liu 2016). Thus, mentoring provides specialised socialisation and personal support to facilitate knowledge transfer amongst employees.
The passion to share by and amongst the employees is very important for improving organisational performance (Wang & Noe 2010). Knowledge sharing and transfer generates new ideas, increases operational efficiency and helps employees to stay motivated. These knowledge-transferring activities should be linked to a proper organisational strategy that is aligned with the organisational objectives. The strategy should be based on the best possible design for creating, maintaining, transferring and applying organisational knowledge to reach the defined goals as advised by Grant (1996). From the submissions by various authors above, it becomes very clear that knowledge transfer simulates growth and innovation in organisations. Liu (2016) is of the view that knowledge transfer reduces the loss of an organisation's know-how.
Research design and methodology
A survey strategy was used to collect data from purposefully selected research participants in Namibia, a developing country in southern Africa. The participants were drawn from selected public and private knowledge-intensive organisations in Namibia. Quantitative data were collected by using paper-based questionnaires and analysed by using the Microsoft Office Excel 2016 package. Tests for internal consistency were performed to increase the validity and reliability of the findings. The sample had 112 participants from the knowledge-intensive organisations identified, and interestingly, the response rate was 100%.
Results and discussion
The participants responded to the questions asked as shown in Table 1. The question asked was 'How effective are the following activities for knowledge transfer in your organisation?' The question sought to measure the usefulness of the knowledge transfer tools in the selected public and private organisations.
According to the data shown in Table 1, the most effective knowledge transfer activity is a CoP, which was classified as very effective (27%) and effective (40%) by the participants. This was followed by mentoring, which was ranked based on a percentage as very effective (11%) and effective (54%). Succession plans were ranked based on a percentage as very effective (12%) and effective (21%). Storytelling was also considered an effective knowledge transfer tool, with 17% of the participants considering the tool as effective and 28% as very effective. Coaching and knowledge repositories were not considered very useful tools for knowledge transfer, and both had less than 20% representation. The following sections present and analyse the information in Table 1 in the form of pie charts for each knowledge transfer tool or activity.
Communities of practice
According to the data gathered from the participants and presented in Figure 1, CoP were found to be effective in organisations by 40% of the participants. This was followed by 27% of the participants who considered CoP as very effective. It emerged that 24% of the participants had no opinion on the effectiveness of CoP; 6% and 3% considered CoP as somewhat effective and not effective, respectively. Considering a CoP 40% effective as adjudged by the participants might mean that the participants to some extent share a common sense of purpose. According to Jang and Ko (2014), knowledge assessment determines the need for a CoP, with its three elements of the domain, the community and the practice. Community of practice objectives should be established and linked to the organisational objectives. Membership penetration and growth should be analysed in a CoP to see how the community has grown. A knowledge transfer activity does not assess whether learning occurs, perhaps that is why some 3% of the participants considered a CoP as not effective for transferring knowledge in an organisation.
Succession planning
Succession plans were considered 21% effective by the participants. Correspondingly, 12% of the participants reflected that succession plans were very effective, whilst the other 37% had no opinion on the effectiveness of succession plans. Moreover, 4% of the participants considered succession plans as somewhat effective, whilst the other 26% considered succession plans not effective at all. When employees retire, organisations face the loss of intellectual and institutional experience, memory and capital for problem-solving. One way of overcoming this challenge is to introduce succession plans to maintain organisational knowledge. Knowledge is the foundation of human capital, and the ability to attract and retain knowledge is an important component of innovation (Young 2013). Succession plans ensure an ongoing availability of talent. The responses from the participants are presented in Figure 2.

Coaching
Coaching refers to an interactive process through which managers aim to solve performance problems (Graduate Mentoring Guidebook 2015). From the empirical evidence gathered from the participants, it was found that coaching was very effective and effective by 14% and 5% of the respondents, respectively. The main goal of coaching is to correct inappropriate behaviour, improve performance and impart practical skills. A small percentage of 10% considered coaching as not effective, and 15% considered coaching as somewhat effective. A median percentage (56%) had no opinion on the effectiveness of coaching. According to the Management Mentors (2019), coaching is task oriented and is short term, which is performance driven. The focus of coaching is on immediate problems and opportunities; thus coaching increases productivity by fostering a positive work culture. At individual level, coaching results in the development of self-awareness and greater responsibility. Most importantly, coaching motivates people and facilitates the adoption of a new organisational culture. The responses elicited from the participants are presented in Figure 3.
Storytelling
Storytelling is used to transfer experts' knowledge to the junior and younger generation of employees (Whyte & Classen 2012). Moreover, storytelling is used to share lessons learnt from projects with coworkers and other peers. In this study, 17% and 28% of the participants considered storytelling as very effective and effective, respectively. It emerged that 30% of the participants considered storytelling as somewhat effective. On the other hand, 6% of the participants did not see storytelling as effective; thus they considered the tool not effective at all. The actual percentages of the responses from the participants are shown in Figure 4. According to Whyte and Classen (2012), storytelling is a vital tool for transferring tacit knowledge, and it has been found to allow for sharing of deeper information and knowledge. Arguably, storytelling is one of the best ways to transfer tacit knowledge, in the sense that the storyteller is able to transfer knowledge in a way that people understand easily. Most learning processes take place through storytelling; hence, the participants considered the tool so effective.

Knowledge repositories
Leibowitz (2012) defines knowledge repositories as online storehouses of expertise and documentation about a specific domain and discipline. Very few of the participants at the organisations studied had used knowledge repositories, and because of this, they had no opinion on the effectiveness of knowledge repositories (73%). Out of the total participants, 14% considered knowledge repositories as somewhat effective. Only 6% considered knowledge repositories as effective. The individual responses about the effectiveness of knowledge repositories from the participants are shown in Figure 5. Concisely, knowledge repositories are private databases that manage enterprise information. From an organisational perspective, knowledge repositories make it easy to find relevant information and knowledge. Knowledge repositories help organisations connect people with expertise via discussion forums and online searchable libraries. Some sources, like the Data Mining Techniques (Alton 2011), refer to knowledge repositories as data warehouses. Most importantly, knowledge repositories reduce training time for new staff, and they also help uncover automation opportunities via online self-help. Despite all the visible advantages of knowledge repositories, a great percentage of participants had no opinion on knowledge repositories.
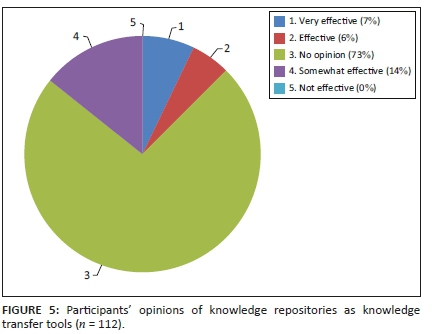
Mentoring
Mentoring was found to be effective at the specific organisations studied. In this study, 54% of the participants considered mentoring as effective because skills have to be transferred from more experienced workers to less experienced workers though mentorship. None of the participants considered mentoring as ineffective. Twenty-two per cent had no opinion on the effectiveness of mentoring, and only 11% of the participants considered mentorship as very effective. The other 13% considered mentoring as somewhat effective. The actual responses from participants are shown in Figure 6. Mentoring provides professional socialisation to facilitate knowledge transfer in knowledge-intensive organisations. Mentoring in organisations is needed to increase skill levels; hence 54% of the participants identified the tool as effective in knowledge transfer. To the mentees, mentoring improves self-confidence and encourages reflection on their practice (Management Mentors 2019). To the mentors, mentoring provides opportunities for reflecting on their own practice and enhancing peer recognition.
Conclusion
In knowledge-intensive organisations, it has been found that the most effective knowledge transfer tool is CoP; 40% of the participants considered this tool to be effective, and 27% considered it very effective. Communities of practice are important for knowledge transfer in that they encourage and promote teamwork through discussions and knowledge sharing amongst employees (Wenger 2014). This was followed by the mentoring tool, which was ranked 54% effective and 11% very effective by the participants. Mentoring exposes mentees to new ideas and new ways of thinking, which may accelerate and boost organisational effectiveness. Storytelling was ranked 28% effective and 17% very effective because it is a natural teaching and learning tool in organisations, which improves communication. Succession plans were ranked 21% effective and 12% very effective because the loss of organisational memory should not be underestimated. Having succession plans in place on time is essential for organisational success. Coaching and knowledge repositories were ranked below 20% effective. We can therefore conclude that the most effective tool for knowledge transfer in knowledge-intensive organisations is CoP followed by mentoring, storytelling, succession plans, coaching and finally knowledge repositories. The study therefore recommends the creation of CoP in knowledge-intensive organisations for effective knowledge transfer and knowledge sharing. In a CoP, people collaborate regularly to share information, improve their skills and actively work on advancing the general knowledge of the domain.
Acknowledgements
The authors thank all the participants who participated in this study and the language editor who edited this piece of work.
Competing interests
The authors declare that no competing interests exist.
Authors' contributions
A.H.M. collected the data from the knowledge-intensive organisations in Namibia and wrote the article. S.B. assisted by giving direction and the necessary support in writing the research article. Both authors approved the final version of the manuscript.
Ethical consideration
The study received ethical clearance from the university of South Africa's College of Science, Engineering and Technology's Research and Ethics Committee, with reference number: 009/AHM/2017/CSET_SOC.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abbott, G.N., 2014, 'Cross-cultural coaching: A paradoxical perspective', in E. Cox, T. Bachkirova & D. Clutterbuck (eds.), The complete handbook of coaching, 2nd edn., pp. 295-317, Sage, London.
Alton, L., 2011, The 7 Most Important Data Mining Techniques, viewed 20 August 2020, from https://www.datasciencecentral.com/profiles/blogs/the-7-most-important-data-mining-techniques
American Productivity & Quality Center (APQC), 2010, Best practice report, Measuring the Impact of Knowledge Management, Arlington, TX.
Becerra-Fernandez, I. & Sabherwal, R., 2010, Knowledge Management systems and processes, Armonk, New York, NY.
Davenport, T.H. & Prusak, L., 2000, Working knowledge: How organizations manage what they know, Harvard Business School Press, Boston, MA.
Durst, S. & Wilhelm, S., 2012, 'Knowledge management and succession planning in SMEs', Journal of Knowledge Management 16(4), 637-649. https://doi.org/10.1108/13673271211246194 [ Links ]
European Framework for Knowledge Management, 2015, Business Knowledge Management: A study on market prospects, business needs and technological trends: Final report, viewed 15 August 2018, from https://ec.europa.eu/information_society/doc/library/business_knowledge_management.pdf
Graduate Mentoring Guidebook, 2015, viewed 10 May 2015, from http://www.unl.edu/mentoring/introduction
Grant, R.M., 1996, 'Towards a knowledge-based theory of the firm', Strategic Management Journal 17(2), 109-122. https://doi.org/10.1002/smj.4250171110 [ Links ]
Heeyoung, J. & Ilsang, K., 2014, 'The factors influencing communities of practice activities and their impact on relationship commitment and individual performance', Journal of Knowledge Management 18(1), 75-91. https://doi.org/10.1108/JKM-06-2013-0233 [ Links ]
Hendriks, P., 2009, 'Why share knowledge? The influence of ICT on the motivation for knowledge sharing', Knowledge and Process Management 6(2), 91-100. [ Links ]
Jang, O. & Ko, K., 2014, 'Factors influencing CoP and their impact on relationship commitment and individual performance', Journal of Knowledge Management 18(1), 75-91. https://doi.org/10.1108/JKM-06-2013-0233 [ Links ]
Kalling, T., 2003, 'Organization-internal transfer of knowledge and the role of motivation: A qualitative case study', Knowledge and Process Management 10(2), 115-126. [ Links ]
Kim, H., Byung, G.K. & Lee, S., 2012, 'An integrated view of knowledge management for performance', Journal of Knowledge Management 16(2), 183-203. https://doi.org/10.1108/13673271211218807 [ Links ]
King, W.R., 2006, 'Knowledge Management and Organizational Learning', Annals of Information Systems 4, 3-13. https://doi.org/10.1007/978-1-4419-0011-1_1 [ Links ]
Leblanc, S.M. & Hogg, J., 2010, Storytelling in knowledge management: An effective tool for uncovering tacit knowledge, viewed 20 May 2017, from http://www.tlainc.com/articl222.htm
Leibowitz, J., 2012, Knowledge management handbook: Collaboration and social networking, 2nd edn., CRC Press, Taylor and Francis Group, Boca Raton, FL.
Lievre, P. & Tang, J., 2015, 'SECI and inter-organizational and intercultural knowledge transfer: A case-study of controversies around a project of co-operation between France and China in the health sector', Journal of Knowledge Management 19(5), 1069-1086. [ Links ]
Liu, S., 2016, Introduction to knowledge management, viewed 21 May 2017, from http://web.archive.org/web/20160319233812/Introduction_to_Knowledge_Management.html
Management Mentors, 2019, Building strong workforce with mentoring, viewed 22 September 2020, from https://www.mentoringcomplete.com/
McDonald, J. & Cater-Steel, A. (eds.), 2016, Communities of practice: Facilitating social learning in higher education, Springer, Singapore.
Nonaka, I. & Takeuchi, H., 1994, 'A dynamic theory of organizational knowledge creation', Organization Science 5(1), 14-37. [ Links ]
Nonaka, I. & Takeuchi, H., 1995, The Knowledge-creating company: How Japanese companies create dynamics of innovation, Oxford University Press, New York, NY.
Pearlson, K.E. & Saunders, C.S., 2004, Managing and Using Information Systems: A Strategic Approach, Wiley, New York, NY.
Reiche, B.S., 2011, 'Knowledge transfer in multinationals: The role of in patriates' boundary spanning', Human Resource Management 50(3), 365-389. https://doi.org/10.1002/hrm.20423 [ Links ]
Rooney, J., 2014, 'Knowledge management and organisational learning', Proceedings of the 11th International Conference on Intellectual Capital, University of Sydney, Sydney.
Rothwell, W.J., 2010, Effective succession planning: Ensuring leadership continuity and building talent from within, 4th edn., Amacom, New York, NY.
Schiavone, F., 2013, Communities of Practice and Vintage Innovation. A Strategic Reaction to Technological Change, Springer, New York, NY. https://doi.org/10.1007/978-3-319-01902-4
Stuhlmann, D.D., 2012, Knowledge management terms, viewed 15 May 2017, from http://home.earthlink.net/~ddstuhlman/defin1.htm.
Turban, E., Rainer, R.K. & Potter, R.E., 2005, Introduction to information technology, Wiley, New York, NY.
Wang, S. & Noe, R.A., 2010, 'Knowledge sharing: A review and directions for future research', Human Resource Management Review 20(2), 115-131. https://doi.org/10.1016/j.hrmr.2009.10.001 [ Links ]
Wenger, E., 2014, Learning in landscapes of practice: Boundaries, identity, and knowledgeability in practice-based learning, Routledge, Abingdon.
Whyte, G. & Classen, S., 2012, 'Using storytelling to elicit tact knowledge from SMEs', Journal of Knowledge Management 16(6), 950-962. https://doi.org/10.1108/13673271211276218 [ Links ]
Young, R., 2013, Knowledge management for the public sector, Asian Productivity Organization, Tokyo.
 Correspondence:
Correspondence:
Alfred Mazorodze
mazorodzeah@yahoo.com
Received: 30 July 2019
Accepted: 16 July 2020
Published: 09 Oct. 2020
ORIGINAL RESEARCH
Predicting communication constructs towards determining information security policies compliance
Tsholofelo Rantao; Kennedy Njenga
Department of Applied Information Systems, College of Business and Economics, University of Johannesburg, Johannesburg, South Africa
ABSTRACT
BACKGROUND: Ineffective communication using inappropriate channels and poor listening skills have resulted in poor compliance with information security (InfoSec) policies. Lack of compliance with InfoSec policies minimises employee proficiency whilst also exposing organisations to business risk.
OBJECTIVES: This research addresses management's concern regarding why employees do not comply with InfoSec policies and proposes that how policies are communicated is integral to compliance and that effective communication can serve to ameliorate compliance
METHOD: The research adopts communication theories from knowledge management, psychology and information systems to draw on important constructs which are then tested in order to identify those that can strongly predict InfoSec policy compliance. The research was quantitative and used a survey to elicit responses from a sample of 100 employees selected from 6 organisations.
RESULTS: Our findings suggest that of the 10 communication constructs used in the miscellany of perception and determinism (MPD) framework, half of these (five) constructs strongly predicated compliance, namely reasons for communication, media appropriateness, non-conflicting interpretations, feedback immediacy and personal focus. The rest of the constructs were weak predictors or could not predict compliance.
CONCLUSION: The research advances InfoSec literature by adapting the MPD model as integral to the development, communication and importantly, compliance with InfoSec policies. The MPD model is pertinent as it aggregates theories of communication from a number of academic disciplines and underpinnings not considered before, thereby improving our understanding on how we communicate InfoSec policies for better compliance.
Keywords: information security; policies; compliance; perception theories; determinism theories.
Introduction
Information security (InfoSec) policy formulation and compliance lies at the heart of addressing how personally identifiable information (PII) is treated by organisations (Siponen, Mahmood & Pahnila 2009). Personally identifiable information is any online information relating to identifying a person. However, it is a cause of concern that users of technology are increasingly revealing personal information in an attempt to enhance and ascertain their online presence using tools such as LinkedInTM to create e-profiles for discoverability (Adriaanse & Rensleigh 2017a). On 25 May 2018, an important zeitgeist arose that dictated new ways that organisations should adopt to treat personal information (Tikkinen-Piri, Rohunen & Markkula 2018). From this period onwards, the handling and protection of personal information became a concern for the executive board of companies through enactment of privacy laws that protect personal information, specifically the General Data Protection Regulation (GDPR) (Tikkinen-Piri et al. 2018). This prerogative has been daunting considering that advanced knowledge-sharing technologies have resulted to user's e-visibility embodied by online presence on the World Wide Web, making discoverability via e-profiles relatively easy (Adriaanse & Rensleigh 2017b).
It is the relative ease by which PII may be obtained online that compliance with privacy laws has been henceforth considered important in order to protect personal information of the users. Not complying with InfoSec policies can now constitute a business risk (Kandeh, Botha & Botha 2018). FacebookTM was unfortunately showcased as the first casualty under this requirement for non-compliance with GDPR. Lawmakers were angry because FacebookTM was reportedly involved in a breach that affected over 87 million individuals worldwide (Isaak & Hanna 2018). FacebookTM had failed to justify why their application improperly shared users' personal data with the political consultancy firm Cambridge AnalyticaTM (Isaak & Hanna 2018). Of concern was that Cambridge AnalyticaTM had gained access to FacebookTM users' personal data for nefarious reasons such as data harvesting (Sanders & Patterson 2019). In order not to fall victim of GDPR guidelines, organisations have embarked on measures to address business risk by instituting InfoSec policies that prescribe the best way to handle personal data. In South Africa, where this study is domiciled, the right to privacy is granted by the constitution and common law (Borena, Belanger & Dedefa 2015). Common law considers privacy harm carried out to an individual's personhood as wrong. However, the 'personhood' in this definition is highly influenced by the Ubuntu philosophy where not only can a person determine his or her personhood, but so can others (Borena et al. 2015).
InfoSec policies are meant to protect an individual's privacy but studies show that these requirements are overlooked (Poullet 2006). Importantly, the compliance to InfoSec policies has been complicated by the introduction of many mobile devices that users now bring to organisations (Musarurwa & Flowerday 2018). What is troubling as well is that many users neither seem to adhere to, nor follow InfoSec policies regardless of their understanding of the need to do so (Puhakainen & Siponen 2010). Employees at times ignore policies (Vance & Siponen 2012) or even worse, violate policies deliberately (Lowry & Moody 2015). Part of the reason for non-compliance of policies is that there is a disconnect between how policies are communicated, interpreted and implemented (Odine 2015). The direct causes of ineffective communication include poor conceptualisation of policies, using inappropriate platforms to present these policies and poor listening skills (Odine 2015). Communication failure is a major concern that is responsible in-part for non-compliance (Kirlappos, Parkin & Sasse 2014) and less attention has been given in research to the diverse communication approaches that are present.
Need for research in communicating InfoSec policies
This research therefore addresses management's concern for low employee compliance to InfoSec policies using a miscellany of theories that address communication drawn from various disciplines such as knowledge management, psychology and information systems to explain how appropriate communication may ameliorate compliance. As employees are considered the weakest link to the implementation and protection of information across organisations, (Aurigemma 2013) much attention needs to be placed on how InfoSec policies are communicated to this group (Susmilch 2019). By addressing communication, researchers may have a better understanding of why important InfoSec policies are not followed.
Understanding communication in depth would be achieved by identifying theories and developing a framework that addresses the efficacy of the communication process regarding InfoSec policies to users. In this regard, we present a compelling opportunity to model a quantitative framework anchored on selected communication theories and testing this framework. In doing so, firstly, we cautiously consider various communication theories present by reviewing literature and by identifying the main theories that would address our objective. This is done in the following section of this work. Following this, we then formulate the miscellany of perception and determinism (MPD) framework that aggregates discourse regarding communication in such a way as to develop and test hypothesis. We finally outline how MPD can be applied in an organisational setting to encourage proper communication of policies and thus encourage compliance.
Literature review
Information security protects an organisation's information assets from unauthorised access and threats to decrease the level of risk directly connected with those assets (Williams 2001). Infosec cannot be fully effective with only the implementation of technical tools and interventions and requires people to be part of the process (Herath & Rao 2009). For InfoSec to be holistic, it must therefore integrate technology, people as well as processes through a robust InfoSec architecture (Eloff & Eloff 2005), with information and the flexible architecture being regarded as a core capability of the organisation for it to remain competitive (Niemand & Mearns 2020).
Research has drawn a link between corporate InfoSec and compliance leading to competitive intelligence (Fitzpatrick & Burke 2003) with studies proposing that considerable value should be placed on competitive intelligence regarding how this construct can contribute to strategy development, decision-making and enhancing the organisational performance (Du Plessis & Gulwa 2016). What is disconcerting is that, employees undermine organisational performance by not complying with organisational policies (Whitman 2003). Compliance regarding any policy ensures that business processes set out by management are performed as expected (Cannon & Byers 2006). A growing number of organisations are concerned about abiding by statutory provisions in order to avoid fines for non-compliance. Avoiding fines is not the only consideration and proactive organisations aim at continuous improvements of their procedures. Indeed continuous improvement is an issue that many organisations sometimes avoid as it identifies areas lacking business excellence (Mthembu & Du Plessis 2018).
According to Cannon and Byers (2006) addressing compliance as business process is often challenging. Siponen, Mahmood and Pahnila, (2009) hold this view as well and suggest that compliance can be improved if the desired practices and normative expectations are visible to all. As suggested, compliance can be attributed to social pressure and visibility. Studies show that the visibility of InfoSec policies influences adherence. In particular, social norms significantly shape compliance when InfoSec policies become part of employees' conversations (Siponen et al. 2009). Understanding why employees do not comply with InfoSec policies may be challenging as employees work under different organisational contexts, under different management practices, different laws, regulations and guidelines and at times using different technology. The following section elaborates on literature around compliance with InfoSec policies.
Compliance with InfoSec policies
Attempting to understand compliance has been a subject of research for many years (Vance & Siponen 2012). The majority of the published research has focused on the reasons why users do not comply with InfoSec policies (Posey, Roberts & Lowry 2015). Most of these studies with the exception of a few, do not address the importance of the communication process, as a way to predict compliance. The following InfoSec studies present reasons for not complying (in order of most recent study) as shown in Table 1.
As shown in Table 1, few studies explicitly address the communication process that predict compliance. Most studies address other important considerations. Sharma and Warkentin (2018) as an example, postulated that not complying with InfoSec policies is partly driven by employment status and differentiates between temporary workers and permanent workers, with the former less likely to comply with InfoSec policies because of the level of investment in the organisation. It has also been argued that when InfoSec policies are seen as restrictive, users will tend not to comply in order to re-establish a sense of control that is seemingly lost (Lowry & Moody 2015). Interestingly, past behaviour and the tendency to be conditioned by that behaviour can influence compliance as shown by Lowry and Moody (2015). Work overload and stress has also been a factor that influences compliance as it encourages employees to be morally disengaged with policies (D'Arcy, Herath & Shoss 2014). Personal gain has equally been suggested as a reason for lack of compliance (Hu et al. 2011) and the nature of penalties and sanctions to be meted out (D'Arcy et al. 2009). This latter study partly addresses communication, with the main focus being on how sanctions and penalties are to be communicated when users violate policies.
Having this in mind, the importance of communication as a predictor of compliance is to be understood in order to minimise any risk business organisations may face for non-compliance. The study therefore endeavours to examine communication more deeply by drawing on useful constructs from theories that can be tested. The following section addresses a miscellany of theories that consider communication in depth, namely media synchronicity theory (MST), communication theory and media richness theory. These three theories present different lenses on the communication process.
Media synchronicity theory
Media synchronicity theory drawn from the discipline of knowledge management and information system advocates for a shared understanding of what is being communicated and requires convergence and conveyance (Dennis, Fuller & Valacich 2008). Understanding convergence and conveyance has been shown to increase communication performance. On the one hand, conveyance is based on the transmission of large amounts of raw information and retrospective analysis. This means that individuals do not have to transmit and process the information at the same time (information processing time). On the other hand, convergence is based on the transmission of higher-level abstraction of information, which requires less deliberation. This means that for individuals with shared mental models, the encoding and decoding of new messages is faster (Dennis et al. 2008). Burke and his colleagues stated that synchronous communication is a significant factor affecting interpersonal communication and teamwork. Various types of media may be used synchronously meaning communication takes place at the same time (Dennis et al. 2008). According to MST, the familiarity of individuals with the duties or activities they are supposed to be performing will affect the relative amounts of convergence and conveyance. Frasier et al. (2019) showed that familiarity and communication will influence each other. We therefore propose the following:
H1: Familiarity of InfoSec policies will predict compliance with InfoSec policies.
Research work by Chen, Srinivasan and Mahmassani (1999) showed that information quality and quantity are strong predictors of compliance behavior. Chen and Chang (2018) addressed information quality and contend that quality is an important precursor to understanding value. We use the construct quality applied in media synchronicity and propose the following:
H2: Information quality will predict compliance with InfoSec policies.
Early work at the University of Michigan draws on the constructs of information process time and accuracy and suggests a relationship and trade-off, known as the speed-accuracy trade-off (SAT) (Swanson & Briggs 1969). Media synchronicity theory can predict InfoSec policy failure partly because the information used to define the policies and procedures at the higher levels of management is not related to the lower levels of the organisation. This creates 'broken telephone' communication. By the time information reaches the top management, it has lost its essence and depth (Dennis et al. 2008). We therefore propose the following:
H3: Time taken to process information will predict compliance with InfoSec policies.
In MST, individuals with shared mental models will use reason to encode and decode new messages faster (Dennis et al. 2008). Individual actions based on reason, can help support synchronicity, which is a shared pattern of co-ordinated behaviour among employees as they collaborate (Dennis et al. 2008). According to Burgemeestre, Hulstijn and Tan (2011), collaboration and compliance can be achieved 'by design'. This may be through instituting a rational system of controls consisting of information systems and procedures. Their work uses argumentation theory into the compliance domain and shows that value-based argumentation and reason are an important facet for compliance. We therefore propose the following:
H4: Reason for communicating (InfoSec policy) will predict compliance with InfoSec policies.
Media can influence user behaviour by making it easier for them to either interact or make it harder for them to interact. Media that fits well within the user's needs (media appropriateness) is more likely to be adopted and used. Positive past experiences and social norms can also affect the likelihood of that media being adopted (Dennis et al. 2008). We therefore propose the following:
H5: Media appropriateness will predict compliance with InfoSec policies.
Communication theory
Communication, espoused by psychologists in the psychology domain is central to human interaction and will consist of intrapersonal and interpersonal communication. Intrapersonal communication is an internal dialogue with self and consists of different subconscious reasoning processes that an individual takes on whilst thinking about a specific subject. This includes contemplating alternatives, deciding between options, weighing up facts and determining how truthful the statement is. It also considers evaluating the intentions behind the actions of individuals, attitude, analysing, thinking, introspecting and self-talking (McQuail 2010). Interpersonal communication takes place when two individuals engage with each other. Formal and informal exchanges form part of interpersonal communication.
Communicating InfoSec policies will require two main players. The first player would be the person formulating and disseminating policy (sender) and the second player would be the person to receive and to comply with policy (receiver). The sender, in this case management may formulate an appropriate InfoSec policy by selecting words, gestures and mediums to compose the message. The encoding process can take the form of verbal, non-verbal or written language (Lunenburg 2010). Messages are carried through an appropriate medium such as telephonic, face-to-face, email or a written report depending on context. The evolution of technology has made email the most frequent and popular medium of choice in many organisations. For effectiveness, all components of communication must be interdependent and when there is a problem with one of these components, the whole communication process becomes flawed (Lunenburg 2010). We therefore propose the following:
H6: Communication media will predict compliance with InfoSec policies.
Media richness theory
Media richness theory drawn from the information systems discipline is rooted on the assumption that organisations process information in order to decrease the level of uncertainty and equivocality. According to Dennis and Kinney (1998) an ambiguous task may cause conflicting interpretation because people may lack the necessary information to process such a task (Dennis & Kinney 1998). In other words, the more InfoSec policies there are, the more uncertainty and equivocality these create and ultimately, this will create an impact on compliance. On the one hand, written media such as written InfoSec policies have been preferred for certain tasks that have clear messages. On the other hand, face to face InfoSec policies have been preferred for messages containing equivocality (Dennis & Kinney 1998). Media richness is hierarchical and will include four media groups, namely: (1) face-to-face, (2) telephone, (3) addressed documents, and (4) unaddressed documents (Daft, Lengel & Trevino 1987). Media richness theory postulates that information richness will influence how the message is interpreted, as this avoids ambiguity. We therefore propose the following:
H7: Non-conflicting interpretations will predict compliance with InfoSec policies.
Reducing uncertainty is an important aspect that is required when pieces of information is lacking. This can be addressed by collecting more information in a less ambiguous environment. Communication can thus be managed by using less-rich media (Donabedian 2006). We therefore propose the following:
H8: Certainty will predict compliance with InfoSec policies.
It can be noted that richer media will be able to elicit immediate feedback, which can either be concurrent feedback or sequential feedback. Concurrent feedback usually takes place simultaneously with the communication of a message, whilst sequential feedback usually takes place when the receiver interrupts the sender to indicate understanding of a message (Kahai & Cooper 2003). We therefore propose the following:
H9: Feedback immediacy will predict compliance with InfoSec policies.
Personalisation is seen as using a technology and information in customised content aimed at matching individual needs and satisfaction and will require a personal focused approach (Hsu & Kulviwat 2006). The same can be said about any policy formulated that must be matched to individual and organisational needs for an effective compliance. We therefore propose the following:
H10: Personal focused (InfoSec policy) will predict compliance with InfoSec policies.
Theoretical framework
From the above literature review we were able to formulate the MPD framework from archetypes of communication theories and surrogates as shown in Figure 1 and to determine the strengths of each of these archetypes.
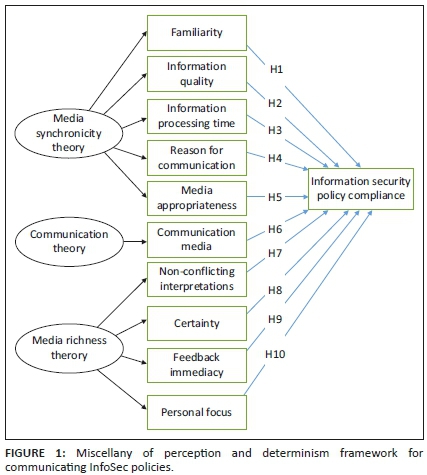
Methodology
The study followed a quantitative approach to test the MPD framework, whilst using a probability sample of 100 individuals. The target sample comprised of employees working in organisations who had developed and communicated recent InfoSec policy documents to its employees. We used probability sampling because this approach was deemed suitable in covering an equal representation of the population (Pallant 2007). A closed-ended five point Likert-scale questionnaire was used as the primary data collection instrument. It contained constructs derived from communication, media synchronicity and media richness theories. A five point Likert scale was used to rate employee's perceptions, regarding how InfoSec policies were communicated and the strengths of the process leading to compliance or non-compliance. The questionnaires were sent for ethical clearance prior to distribution and upon receipt of ethical clearance, distributed to six different organisations operating in Johannesburg, South Africa. Data collected were anonymised and could not be traced back to a specific individual.
Ethical consideration
The research adhered to all ethical clearance procedures stipulated and approved by the School of Consumer Intelligence and Information Systems Ethics committee at the University of Johannesburg (2018SCiiS 01).
Data analysis
Statistical Package for the Social Sciences (SPSS), a computerised statistical analysis software was used for data analysis. The analysis enabled interpretation of results quantitatively, as well as presenting a logical flow of results. We noted instances where one respondent did not answer certain sections in the questionnaire (revealing academic qualifications) and this constituted missing data. We used SPSS frequency analysis to compute system missing data for each specific case, before further analysis was done. Upon examination, missing data did not constitute more than 1% of sample size, and we used SPSS factor procedure, pairwise deletion to exclude the variable that had a missing value (Norušis 2006). Table 2 shows Cronbach's alpha values elicited and reliability of data that was presented. This analysis takes cognisance of missing data. Cronbach's alpha values greater than or equal to 0.9 suggests that internal consistency (correlation) is excellent. If the Cronbach's alpha value is less than or equal to 0.5, internal consistency (correlation) is very low and revising the items in the research instrument is recommended. Table 2 shows that familiarity, non-conflicting interpretations, information process time, feedback immediacy and personal focus have higher correlation values of above 0.8.
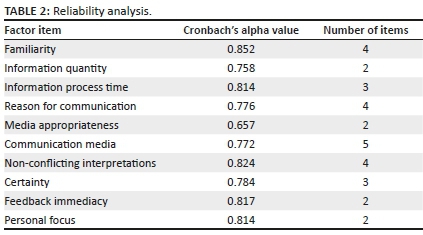
Descriptive statistics
Figure 2 describes the age of the participants. The majority of participants were between the ages of 25 and 34, which represented 64% of the sample.
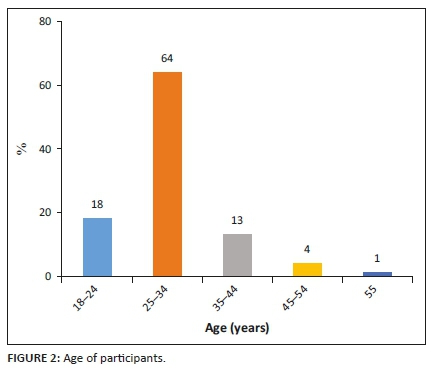
Those aged between 18 and 24 represented 18% of the sample, whilst those aged between 35 and 44 represented 13% of the sample. The smallest group of participants were aged between 45 and 55 years old and this group represented 4% of the sample. Figure 3 describes the qualification levels of participants and shows that 49% of those sampled held an honours degree, whilst 28%, held a baccalaureate degree. The less qualified of the sample included those who held a diploma, constituting 16% of the sample and those holding a matric certificate at only 1% of sample. The most qualified held masters or doctorate degree, and this represented 5% of the sample. A total of 1% of the respondents (missing data) did not disclose this information.
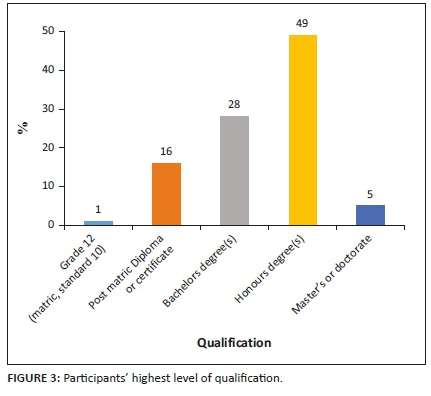
Importantly, the majority of those sampled in the study worked in an organisation that housed 1000 or more employees consisting of 75% of sample. This is shown in Figure 4.
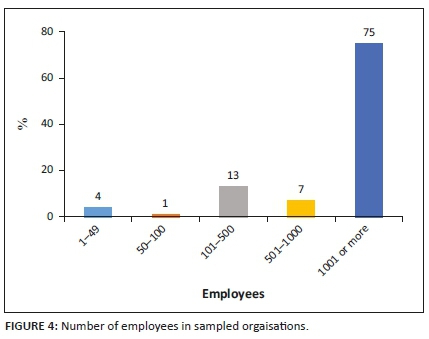
A total of 13% of respondents worked in an organisation that housed the number of employees ranging between 101 and 500. Less than 7% of those sampled worked for an organisation with less than 500 employees and 4% worked for an organisation with 1 and 49 employees. Only 1% of those sampled worked in an organisation housing 50 and 100 employees.
Factor analysis
Ten key constructs drawn from the MDP framework, namely familiarity, information quantity, information process time, reason for communication, media appropriateness, communication media, non-conflicting interpretations, certainty, feedback immediacy and personal focus that were proposed to predict compliance of InfoSec were considered. We carried out a factor analysis to reduce the underlying variables associated with each of these constructs. We used SPSS, factor analysis (principal component analysis) for this purpose. We used Bartlett's test of sphericity to test construct validity. In addition, in order to analyse the strength existing between variables, Kaiser-Mayer-Olkin's (KMO) measure of sampling adequacy was used. Kaiser-Mayer-Olkin's results were used to determine whether factor analysis would be a good method to use for dimension reduction and multicollinearity of values ranging between 0 and 1. Our values were above 0.5 and close to 1.0 indicating that a factor analysis would be useful. The KMO values are presented in Table 3.
From the KMO results indicating that factor analysis would be useful, we carried out a factor analysis and rotated components for better interpretation and the elimination of ambiguity (Pallant 2007) as indicated by Table 4 and Table 5. Factor rotation's main purpose is to create a simplified structure that enables all items to load based on a minimal number of factors (Yong & Pearce 2013). The results of factor analysis were used to measure the suitability of the data and of sampling adequacy for variables identified within the theoretical model.
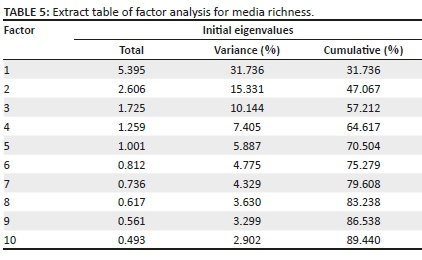
Component extraction and factor loadings
Media synchronicity
Six factors were extracted. These six factors had an eigenvalues greater than one and together, they accounted for 71% of the variability in the original variables.
Communication
We did not carry out a factor analysis for this construct and used all five items for explaining the single item communication media. Using SPSS, we transformed these into a single factor by computing average means.
Media richness
Only five factors having eigenvalues greater than one were extracted, and together these accounted for 71% of the variability in the original variables.
Regression
A multiple regression analysis that describes the relationship and strength between the dependent variable, compliance of InfoSec policies, and the 10 independent variables under study was carried out. The purpose was to estimate the coefficient of the 10 independent variables, on the variable compliance of InfoSec policies. The results of the regression analysis are shown in Table 6.
Discussion
Based on the outcomes of the tests, the overall significance of the research model was justified. However, five of the following hypotheses, namely familiarity, information quality, information process time, communication media and certainty were rejected because of their insignificant values (where p < 0.0005), whilst those propositions that were accepted have a bearing on compliance as presented in Figure 5. It is important to note that although the 'reject' lexicon has been used, this simply means that the results were non-significant with no way to determine if these five could predict compliance (Ghauri, Grønhaug & Strange 2020).
From the linear regression analysis communication archetypes of reasons for communication, media appropriateness, non-conflicting interpretations, feedback immediacy and personal focus tended to significantly predict compliance with InfoSec policies as opposed to other archetypes that were disproved in the MPD model. We address each of these variables as follows: Reason for communication was statistically significant towards predicting InfoSec policy compliance, beta = 0.306 and significant value < 0.5. When organisations re-emphasise the reason why certain policies are important, employees are more likely to comply. Importantly, regarding media appropriateness, (beta = 0.280 and significant value < 0.5) when the choice of media of communication is deemed appropriate by employees, the security compliance is predictably higher and when the choice of media is inappropriate chances of non-compliance are heightened. This study confirms the finding of other studies carried out that give preference and significance to explicit forms of communication such as email (Fonseca & Normann 2012). With regard to the variable non-conflicting interpretations, (beta = 0.306 and significant value < 0.5.) data results suggest that if policies are ambiguous, then this tends to predict non-compliance. If InfoSec policies are non-conflicting and unambiguous, then this tends to predict compliance. According to Buthelezi, Van Der Poll and Ochola (2016), InfoSec policies may often not be followed nor complied with because of the very nature of the policy documents themselves, which may lend themselves to misinterpretation. Indeed ambiguity in wordings in such documents makes it hard for users to comply. This work presents a similar view-point from those observations and shows ambiguity will limit compliance. Feedback immediacy (where beta = 0.288 and significant value < 0.5) was statistically significant and also tended to predict security compliance. Indeed, when the media selected enables real-time or immediate feedback from both sender and receiver, the InfoSec policy being sent is more likely to be complied with (Keil & Johnson 2002). Significantly, studies have drawn a link between performance and communication frequency, when feedback is received repeatedly (McLarnon et al. 2019) and this study confirms this as well. Our findings and therefore proposition is that these five variables will ameliorate InfoSec policy compliance more intensely if keen attention is given to these by management and practitioners.
Contribution
The MPD framework developed in this work, offers new communication predilections that can shape InfoSec policy compliance in ways not considered before in InfoSec literature. These communication predications are characterised by non-conflicting interpretations, reasons for communication, media appropriateness, feedback immediacy and personal focus. The MPD framework compels InfoSec practitioners to understand communication much more deeply and to leverage the medium and message in order to ameliorate InfoSec policy compliance.
Implications of study
InfoSec practitioners in South Africa and those in management may find the MPD framework useful in providing actionable insights into managing how InfoSec policies should be communicated in order to inspire high compliance. As we have shown, compliance with InfoSec policies is necessary to avoid business risk. The findings of this study can be broadly generalised and transferable to contexts outside of South Africa. In terms of a theoretical implication, the research advances InfoSec literature by adapting the MPD model as integral to the development and communication of policies. The MPD model is pertinent as it aggregates theories of communication from a number of academic disciplines and underpinnings not considered before, thereby improving our understanding on how we communicate InfoSec policies.
Conclusion
InfoSec policies are designed primarily to ensure that users of organisations' information assets abide by, and follow, specified prescriptions in order to protect information assets from threats. Notably, users have been shown to be less compliant with InfoSec policies thus compelling a need to investigate why this is so. Following through a literature review and focusing on how policies are communicated to users whom literature has identified as threats, this research was undertaken to present a communication model that could predict InfoSec policy compliance. The research aggregates theories of communication and develops the MPD framework, which was considered pertinent as it draws insights from a number of academic disciplines and underpinnings not considered before. It is through the MPD framework that our understanding regarding how we communicate InfoSec policies is improved. The inferences of the MPD framework show that there is a strong positive relationship between InfoSec compliance (and non-compliance) that is shaped by reasons for communication, media appropriateness, non-conflicting interpretations, feedback immediacy and personal focus. These five constructs predict 61.3% of InfoSec compliance. The remaining five constructs, namely familiarity, information quality, information processing time, communication media and certainty were tested and found to be weak predictors or could not predict compliance. In light of these findings, this work has made several suggestions to organisations such as the need to reemphasise the reason why certain policies are important, availing immediate feedback when there are signs non-compliance is imminent and importantly carefully determining the appropriate media to use when communicating InfoSec policies. This work opens up possibilities for important future research where the MPD model needs to be tested in multiple settings as communication of InfoSec policies may vary under different settings. The MPD framework would have gone unnoticed without this empirical initiative.
Acknowledgements
Competing interests
The authors have declared that no competing interests exist.
Authors' contributions
All authors contributed equally to this work.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
The authors confirm that the data supporting the findings of this study are available within the article.
Disclaimer
The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Adriaanse, L.S. & Rensleigh, C., 2017a, 'E-visibility to enhance knowledge sharing', in Africa Research Group Conference, Mauritius, August 29-31, 2017.
Adriaanse, L.S. & Rensleigh, C., 2017b, 'E-visibility of environmental science researchers at the University of South Africa', South African Journal of Libraries and Information Science 83(2), 30-41. https://doi.org/10.7553/83-2-1636 [ Links ]
Aurigemma, S., 2013, From the weakest link to the best defense: Exploring the factors that affect employee intention to comply with information security policies, ProQuest LLC, Manoa, HI.
Borena, B., Belanger, F. & Dedefa, D.E., 2015, 'Information privacy protection practices in Africa: A review through the lens of critical social theory', in 48th Hawaii International Conference on System Sciences, HICSS 2015, Kauai, Hawaii, USA, January 05-08, 2015. IEEE Computer Society 2015, 3490-3497. https://doi.org/10.1109/HICSS.2015.420
Burgemeestre, B., Hulstijn, J. & Tan, Y.H., 2011, 'Value-based argumentation for justifying compliance', Artificial Intelligence and Law 19(2-3), 149. https://doi.org/10.1007/s10506-011-9113-4 [ Links ]
Buthelezi, M.P., Van der Poll, J.A. & Ochola, E.O., 2016, 'Ambiguity as a barrier to information security policy compliance: A content analysis', in Proceedings of the International Conference on Computational Science and Computational Intelligence (CSCI), December 15-17, 2016, pp. 1360-1367, IEEE, Las Vegas, NV.
Cannon, J.C. & Byers, M., 2006, 'Compliance deconstructed', Queue, 4(7), 30-37. https://doi.org/10.1145/1160434.1160449 [ Links ]
Chen, C.C. & Chang, Y.C., 2018, 'What drives purchase intention on Airbnb? Perspectives of consumer reviews, information quality, and media richness', Telematics and Informatics 35(5), 1512-1523. https://doi.org/10.1016/j.tele.2018.03.019 [ Links ]
Chen, P.S.T., Srinivasan, K.K. & Mahmassani, H.S., 1999, 'Effect of information quality on compliance behavior of commuters under real-time traffic information', Transportation Research Record 1676(1), 53-60. https://doi.org/10.3141/2162-07 [ Links ]
D'Arcy, J., Herath, T. & Shoss, M.K., 2014, 'Understanding employee responses to stressful information security requirements: A coping perspective', Journal of Management Information Systems 31(2), 285-318. https://doi.org/10.2753/MIS0742-1222310210 [ Links ]
D'Arcy, J., Hovav, A. & Galletta, D., 2009, 'User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach', Information Systems Research 20(1), 79-98. https://doi.org/10.1287/isre.1070.0160 [ Links ]
Daft, R.L., Lengel, R.H. & Trevino, L.K., 1987, 'Message equivocality, media selection, and manager performance: Implications for information systems', MIS Quarterly 11(3), 355-366. https://doi.org/10.2307/248682 [ Links ]
Dennis, A.R. & Kinney, S.T., 1998, 'Testing media richness theory in the new media: The effects of cues, feedback, and task equivocality', Information Systems Research 9(3), 219-301. https://doi.org/10.1287/isre.9.3.256 [ Links ]
Dennis, A.R., Fuller, R.M. & Valacich, J.S., 2008, 'Media, tasks, and communication processes: A theory of media synchronicity', MIS Quarterly 32(3), 575-600. https://doi.org/10.2307/25148857 [ Links ]
Donabedian, B., 2006, 'Optimization and its alternative in media choice: A model of reliance on social-influence processes', Information Society 22(3), 121-135. https://doi.org/10.1080/01972240600677771 [ Links ]
Du Plessis, T. & Gulwa, M., 2016, 'Developing a competitive intelligence strategy framework supporting the competitive intelligence needs of a financial institution's decision makers', South African Journal of Information Management 18(2), 1-8. https://doi.org/10.4102/sajim.v18i2.726 [ Links ]
Eloff, J.H.P. & Eloff, M.M., 2005, 'Information security architecture', Computer Fraud & Security 2005(11), 10-16. https://doi.org/10.1016/S1361-3723(05)70275-X [ Links ]
Fitzpatrick, W.M. & Burke, D.R., 2003, 'Competitive intelligence, corporate security and the virtual organization', Journal of Competitiveness Studies 11(1), 20-30. [ Links ]
Fonseca, M.A. & Normann, H.T., 2012, 'Explicit vs. tacit collusion - The impact of communication in oligopoly experiments', European Economic Review 56(8), 1759-1772. https://doi.org/10.1016/j.euroecorev.2012.09.002 [ Links ]
Frasier, L.L., Quamme, S.R.P., Ma, Y., Wiegmann, D., Leverson, G., DuGoff, E.H. et al., 2019, 'Familiarity and communication in the operating room', Journal of Surgical Research 235, 395-403. https://doi.org/10.1016/j.jss.2018.09.079 [ Links ]
Ghauri, P., Grønhaug, K. & Strange, R., 2020, Research methods in business studies, Cambridge University Press, Cambridge.
Herath, T. & Rao, H., 2009, 'Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness', Decision Support Systems 47(2), 154-165. https://doi.org/10.1016/j.dss.2009.02.005 [ Links ]
Hsu, H.S. & Kulviwat, S., 2006, 'An integrative framework of technology acceptance model and personalisation in mobile commerce', International Journal of Technology Marketing 1(4), 393-410. https://doi.org/10.1504/IJTMKT.2006.010734 [ Links ]
Hu, Q., Xu, Z., Dinev, T., Ling, H., 2011, 'Does deterrence work in reducing information security policy abuse by employees?', Communications of the ACM 54(6), 54-60. https://doi.org/10.1145/1953122.1953142 [ Links ]
Isaak, J. & Hanna, M.J., 2018, 'User data privacy: Facebook, Cambridge analytica, and privacy protection', Computer 51(8), 56-59. https://doi.org/10.1109/MC.2018.3191268 [ Links ]
Kahai, S.S. & Cooper, R.B., 2003, 'Exploring the core concepts of media richness theory: The impact of cue multiplicity and feedback immediacy on decision quality', Journal of Management Information Systems 20(1), 263-299. https://doi.org/10.1080/07421222.2003.11045754 [ Links ]
Kandeh, A.T., Botha, R.A. & Futcher, L.A., 2018, 'Enforcement of the Protection of Personal Information (POPI) Act: Perspective of data management professionals', South African Journal of Information Management 20(1), 1-9. [ Links ]
Keil, M. & Johnson, R.D., 2002, 'Feedback channels: Using social presence theory to compare voice mail to e-mail', Journal of Information Systems Education 13(4), 4. [ Links ]
Kirlappos, I., Parkin, S. & Sasse, M.A., 2014, Learning from 'Shadow Security': Why understanding non-compliance provides the basis for effective security, OpenAIRE, UK. http://doi.org/10.14722/usec.2014.23007
Lowry, P.B. & Moody, G.D., 2015, 'Proposing the control reactance compliance model (CRCM) to explain opposing motivations to comply with organisational information security policies', Information Systems Journal 25(5), 433-463. https://doi.org/10.1111/isj.12043 [ Links ]
Lunenburg, F., 2010, 'Communication: The process, barriers, and improving effectiveness', Schooling 1(1), 1-11. [ Links ]
McLarnon, M.J., O'Neill, T.A., Taras, V., Law, D., Donia, M.B. & Steel, P., 2019, 'Global virtual team communication, coordination, and performance across three peer feedback strategies', Canadian Journal of Behavioural Science / Revue canadienne des sciences du comportement 51(4), 207-218. https://doi.org/10.1037/cbs0000135 [ Links ]
McQuail, D., 2010, McQuail's mass communication theory, Sage, Newbury Park, CA.
Mthembu, M. & Du Plessis, T., 2018, 'Maturity mapping for continuous improvement: A case study of a revenue services institution', South African Journal of Economic and Management Sciences 21(1), 1-10. https://doi.org/10.4102/sajems.v21i1.2044 [ Links ]
Musarurwa, A. & Flowerday, S., 2018, 'The BYOD information security challenge for CIOs', in Proceedings of the 12th International Symposium on Human Aspects of Information Security & Assurance, August 29-31, 2018, p. 246, Dundee, Scotland.
Niemand, C.J. & Mearns, M., 2020, 'Elements of a flexible information architecture: A South African perspective', South African Journal of Information Management 22(1), 1-7. https://doi.org/10.4102/sajim.v22i1.1007 [ Links ]
Norušis, M.J., 2006, SPSS 14.0 guide to data analysis, Prentice hall, Upper Saddle River, NJ.
Odine, M., 2015, 'Communication problems in management', Journal of Emerging Issues in Economics, Finance and Banking (JEIEFB) 4(2), 1615-1630. [ Links ]
Pallant, J., 2007, 'SPSS survival manual', in J. Pallant (ed.), SPSS survival manual, p. 146, Open University Press, Maidenhead.
Posey, C., Roberts, T.L., Lowry, P.B., 2015, 'The impact of organizational commitment on insiders' motivation to protect organizational information assets', Journal of Management Information Systems 32(4), 179-214. https://doi.org/10.1080/07421222.2015.1138374 [ Links ]
Poullet, Y., 2006, 'EU data protection policy, the directive 95/46/EC: Ten years after', Computer Law & Security Report 2(2), 206-217. https://doi.org/10.1016/j.clsr.2006.03.004 [ Links ]
Puhakainen, P. & Siponen, M., 2010, 'Improving employees' compliance through information systems security training: An action research study', MIS Quarterly 34(4), 757-778. https://doi.org/10.2307/25750704 [ Links ]
Sanders, J. & Patterson, D., 2019, Facebook data privacy scandal: A cheat sheet, Tech Republic, viewed 14 May 2020, from https://www.techrepublic.com/article/facebook-data-privacy-scandal-a-cheat-sheet/
Sharma, S. & Warkentin, M., 2018, 'Do I really belong?: Impact of employment status on information security policy compliance', Computers & Security 87, 101397. https://doi.org/10.1016/j.cose.2018.09.005 [ Links ]
Siponen, M., Mahmood, A. & Pahnila, S., 2009, 'Are employees putting your company at risk by not following information security policies?', Communication of the ACM 52(12), 145-147. https://doi.org/10.1145/1610252.1610289 [ Links ]
Susmilch, C., 2019, Let's talk - communication strategies that engage employees and improve compliance, Sumerra, viewed 30 May from https://www.sumerra.com/lets-talk-communication-strategies-that-engage-employees-and-improve-compliance/
Swanson, J.M. & Briggs, G.E., 1969, 'Information processing as a function of speed versus accuracy', Journal of Experimental Psychology 81(2), 223-229. https://doi.org/10.1037/h0027774 [ Links ]
Tikkinen-Piri, C., Rohunen, A. & Markkula, J., 2018, 'EU general data protection regulation: Changes and implications for personal data collecting companies', Computer Law & Security Review 34(1), 134-153. https://doi.org/10.1016/j.clsr.2017.05.015 [ Links ]
Vance, A. & Siponen, M.T., 2012, 'IS security policy violations: A rational choice perspective', Journal of Organizational and End User Computing (JOEUC) 24(1), 21-41. https://doi.org/10.4018/joeuc.2012010102 [ Links ]
Whitman, M.E., 2003, 'Enemy at the gate: Threats to information security', Communications of the ACM 46(8), 91-95. https://doi.org/10.1145/859670.859675 [ Links ]
Williams, P., 2001, 'Information security governance', Information Security Technical Report 6(3), 60-70. https://doi.org/10.1016/S1363-4127(01)00309-0 [ Links ]
Yong, A. & Pearce, S., 2013, 'A beginner's guide to factor analysis: Focusing on exploratory factor analysis', Tutorials in Quantitative Methods for Psychology 9(2), 79-94. https://doi.org/10.20982/tqmp.09.2.p079 [ Links ]
 Correspondence:
Correspondence:
Kennedy Njenga
knjenga@uj.ac.za
Received: 26 Feb. 2020
Accepted: 16 July 2020
Published: 12 Oct. 2020
ORIGINAL RESEARCH
Modelling the intended use of Facebook privacy settings
Kimberley Read; Karl van der Schyff
Department of Information Systems, Faculty of Commerce, Rhodes University, Grahamstown, South Africa
ABSTRACT
BACKGROUND: The ineffective use of Facebook privacy settings has become commonplace. This has made it possible for corporates not only to harvest personal information but also to persuade or influence user behaviour in a manner that does not always protect Facebook users.
OBJECTIVES: The objective of this article was to develop a research model that could be used to evaluate the influence of subjective norms, information security awareness and the process of threat appraisal on the intention to use Facebook privacy settings.
METHOD: In this article, the authors made use of a qualitative approach. Literature pertaining to subjective norms, information security awareness and threat appraisal was thematically analysed using Atlas.ti. Through a process of inductive reasoning, three propositions were developed.
RESULTS: This study found that it is likely that an individual's intention to use Facebook privacy settings will be influenced by subjective norms, information security awareness and the process of threat appraisal. To evaluate the behavioural influence of these selected constructs and relationships, a research model was developed based on both the theory of planned behaviour and protection motivation theory.
CONCLUSION: In this article, it is argued that the ineffective use of Facebook privacy settings may be because of the behavioural influence of subjective norms. This is compounded by the fact that most users are unaware of privacy threats. This makes these users vulnerable to Facebook-based privacy threats because the process of threat appraisal is conducted with incomplete, inaccurate or missing information.
Keywords: Facebook; information privacy; threat appraisal; theory of planned behaviour; information security awareness; norms; protection motivation theory.
Introduction
Social interaction via the use of Facebook has become part of over 2 billion users' daily lives (Symeonidis et al. 2018). In some respects, this may be attributed to the fact that users are able to build not only social relationships but also a shared personal identity. Such interaction enables users to engage with Facebook on a psychological level, which in turn satisfies that most users seek, namely recognition and belonging (Debatin et al. 2009). This is exemplified in a recent study, which revealed that, on average, Facebook users check their accounts roughly 14 times a day (Kusyanti et al. 2017). These users also tend to construct their Facebook identities based on the influence of their peers (Strater & Lipford 2008). However, if not protected using Facebook privacy settings, such approaches to self-disclosure often lead to unintended consequences, one being the misuse of personal information. This is especially pertinent given that privacy threats are believed to be a composite result of oversharing personal information paired with the insufficient use of privacy settings. Subjective forces, such as the need to accumulate more Facebook friends, imply that in practice many platform users befriend others who are in actual fact absolute strangers (Govani & Pashley 2014).
As a result, these so-called Facebook friends have access to a number of pieces of personal information. This includes not only those aspects that remain relatively static (i.e. a user's age and gender) but also their thoughts and ideas in the form of Facebook posts and likes. Together, these aspects of a user's profile not only make it possible to enhance Facebook's ability to sell advertising space, but also enable Facebook to monitor and, to some extent, predict a user's online behaviour.
Although targeted advertising has the potential to increase the revenues of social media companies, it is the prediction of user behaviour that allows Facebook to misuse user data. In fact, the ability to monitor content with the intent to manipulate user behaviour is profound (Amer & Noujaim 2019). One only has to consider the numerous voter-profiling campaigns carried out by Cambridge Analytica to appreciate the significance of influencing behaviour by way of posting tailored content to users classified as persuadable (Amer & Noujaim 2019). Such classification can only be carried out by harvesting as much personal information as is needed to determine a user's preferences, and possibly even their dominant personality traits. Given that companies like Cambridge Analytica have been able to harvest enough personal information to influence these co-called persuadables, it makes sense to understand the behavioural aspects that influence Facebook users' intentions to enact protective behaviour.
Within the context of this article, such protective behaviour is understood as a Facebook user's intention to use privacy settings effectively. It is believed that the use of these settings would limit the inadvertent disclosure and misuse of personal information. To model this influence, the authors of this article have adapted the theory of planned behaviour (TPB) by replacing perceived behavioural control (PBC) with information security awareness, and also incorporated an element of protection motivation theory (PMT), namely threat appraisal. These constructs are conceptualised as follows: the authors argue that an individual's threat appraisal will influence their intention to use the privacy settings. If an individual is aware of privacy threats, they will likely be more inclined to use the privacy settings. Conversely, if they are not aware of privacy threats, they will be more likely to avoid using privacy settings. Information security awareness is conceptualised as the knowledge an individual possesses regarding privacy threats. It is therefore argued that information security awareness controls the effectiveness of an individual's threat appraisal. If they possess little or no knowledge of privacy threats, the process of threat appraisal will be ineffective.
The authors also argue in favour of the behavioural influence of subjective norms. In this context, subjective norms are conceptualised as an individual's susceptibility to the views of their peers with respect to the use of privacy settings. If an individual is influenceable, their peers' privacy behaviour will likely influence theirs. In other words, if their peers avoid using privacy settings, so will they.
Together, the behavioural implications of the model described above enable this study to contribute to known theory because few Facebook privacy studies have merged PMT and the TPB in this manner. Although Stern and Salb (2015) evaluated the influence of norms, they did so by incorporating both descriptive and subjective norms, modelling their influence on the intended use of Facebook instead of focusing on privacy settings.
Facebook privacy settings in perspective
Facebook allows users to control their personal information (and profile) through an elaborate system of settings, commonly referred to as Facebook privacy settings. These settings allow users to control the extent to which their peers, and even strangers, can access their personal information (Lewis, Kaufman & Christakis 2008). Users can also see the activities of other users and friends-especially if the content is marked as public (Zlatolas et al. 2015). Some personal information is also made public by default. This includes a user's name, gender, profile picture, cover photo, language, country and age. These pieces of personal information are made available to individuals who may not even have a Facebook profile (Facebook 2019), hence the ease with which companies like Cambridge Analytica can find personal information to misuse or to persuade individuals. To make matters worse, many users are unaware that the default privacy settings allow this type of access.
Nevertheless, users still disclose personal information, making this a relevant and persistent problem. Several explanations have been put forward as possible reasons why the privacy settings are not being used. Some researchers argue in favour of social conformance, implicit trust, poor interface design and permissive default settings (Strater & Lipford 2008). Given the use of threat appraisal, this article investigates an individual's perception of threats, specifically threats that pertain to the safety of individuals' social media based personal information. To this extent, a study by Govani and Pashley (2014) found that whilst students were aware of threats (i.e. identity theft, stalking and general misuse), they were still inclined to provide the information and failed to implement protective measures. Research points to three possible reasons why the Facebook privacy settings are not adequately used:
-
Users are unaware of any threats.
-
Users are apathetically aware of privacy threats.
-
Facebook privacy settings are too difficult to use and are therefore avoided.
Dickinson and Holmes (2008) found that individuals are likely to become more evasive and adopt maladaptive coping responses if the threat level is high, as opposed to proactively reducing the effect of the threat (Marett, Vedadi & Durcikova 2019). Often, fear motivates action in these cases, which may take the form of self-protective or avoidant responses (Witte & Allen 2000).
Whilst privacy options and settings have become more sophisticated (Haynes, Bawden & Robinson 2016), research has found these tools to be underutilised (Boyd & Hargittai 2010; Golbeck & Mauriello 2016). Therefore, the technological aspects of security cannot solely guarantee a secure environment for personal information. Researchers also have to take human aspects into consideration (Safa & Von Solms 2016). Overall, studies have found that users find the Facebook privacy settings confusing, time-consuming and challenging to use. This may in turn result in the accidental or unintentional disclosure of personal information regardless of the additional forms of control users have.
Methodology
This article adopted a qualitative approach as the authors performed in-depth thematic analysis of secondary data.
Data collection
The purpose of this article was to collect data on the behavioural influence of subjective norms, information security awareness and threat appraisal. This entailed collecting and thematically analysing secondary data obtained from a variety of academic databases as part of a scoping review. These databases included ScienceDirect, Taylor & Francis, Oxford Academic and the AIS Senior Scholars Basket, which include journals like the European Journal of Information Systems, Information Systems Journal, Information Systems Research and MIS Quarterly. A scoping review is generally used to identify and map available evidence as it relates to a topic of interest (Munn et al. 2018). This required a series of structured searches using phrases such as information security awareness, threat appraisal, subjective norms, Facebook privacy settings and social media. After screening the titles and abstracts, 42 articles were thematically analysed, as illustrated in the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) diagram shown in Figure 1.
Method of analysis
As part of the analysis process, a series of thematic maps were created, one for each of the propositions. This process also involved a more focused review and rereading of the 42 articles - a common practice when conducting thematic analysis (Bowen 2009). Such rereading not only illuminates prominent themes that were not apparent during the initial screening process (Joffe 2012) but also enables researchers to recognise specific patterns. In turn, these patterns may become categories to guide analysis within identified themes. For example, it is reasonable to assume that most (if not all) of the selected studies employed specific research methods. These methods of analysis may become one such analysis category. This entire process was conducted inductively so as to emphasise the researcher's understanding of the broader phenomena pertaining to the use of Facebook privacy settings (Braun & Clarke 2006). A deductive approach was deemed inappropriate for this study, given that the objective of the article was to develop the research model and not to test it using statistical means. As part of the inductive analysis a five-phased approach was used, as outlined by Braun and Clarke (2006). These phases are described as follows:
-
becoming acquainted with the data by reading and rereading the selected articles
-
developing initial codes (short phrases) in Atlas.ti to describe one or more textual extracts from the selected articles (see Table 1)
-
collating codes into potential (or candidate) themes (code groups in Atlas.ti)
-
reviewing themes in relation to coded extracts, as well as merging themes if required
-
defining and naming these themes, culminating in the development of thematic maps (networks in Atlas.ti).
As part of phase 1, the articles were read in detail to develop an overall understanding of the core aspects (influence of subjective norms and information security awareness) of this study. In phase 2, interesting codes were identified based on the nature and the additional behavioural understanding gained after executing phase 1.
Following this, several codes were collated into candidate themes. Phase 3 culminated in the development of three candidate themes, namely threat appraisal, normative influence and the influence of information security awareness. Using these candidate themes as a starting point, phase 4 further refined these themes by removing extraneous coded extracts. This culminated in the formal specification of three thematic maps (see Figure 2 for one example). It is from these thematic maps that the resultant propositions were developed (i.e. as part of phase 5).
Development of propositions
This section first provides an outline of how the TPB (amongst others) and PMT have been used in related studies, followed by a discussion that outlines the development of the propositions for this study.
Theoretical framework
This study utilised both the TPB and PMT. Ajzen (1985), who developed the TPB, conceptualised the strength of intention as an immediate antecedent of behaviour (Kautonen, Van Gelderen & Fink 2015). Thus, the TPB is based on the assumption that most human behaviour takes place as a result of intent, as influenced by personal attitudes, subjective norms and PBC (Grimes & Marquardson 2019; Ham, Jeger & Ivković 2015).
Within the context of this study, attitude is defined as the extent to which an individual either positively or negatively value the use of Facebook privacy settings. Subjective norms is defined as the social pressure that influences whether an individual will make use of the Facebook privacy settings. Information security awareness is defined as the extent to which an individual is aware of the privacy threats that their personal information is exposed to. Protection motivation theory, on the other hand, proposes that behavioural intentions are motivated by the processes of both threat and coping appraisal (Rogers 1975). Note that this study only argues in favour of the behavioural influence of threat appraisal. In this context, threat appraisal necessitates judging the severity of and the vulnerability attached to not making use of Facebook privacy settings. For example, if a Facebook user determines that their level of self-efficacy is particularly high, they may forgo the privacy settings because they believe they are adequately equipped to ameliorate future threats (i.e. misuse of personal information). Additionally, PMT has been found to adequately explain individuals' behavioural intention to engage in protective actions (Ifinedo 2012).
The research model for this study merges these two theories by arguing the influence of threat appraisal, specifically in terms of the role played by fear appeals in the appraisal process. In other words, the research model posits that it is likely that an individual will increase their knowledge of (in terms of avoidance) specific threats as they become aware of vulnerabilities. For example, a Facebook user may wish to find out how they can avoid inadvertently sharing personal information because they fear that it may be misused.
This combination of theoretical constructs not only contributes theoretically but also enables researchers to evaluate the role of fear appeals (one part of threat appraisal) within the context of Facebook privacy settings. The integration of subjective norms further increases the explanatory power of the research model (Tsai et al. 2016). Having said this, other studies have also combined these two theories (Grimes & Marquardson 2019; Ifinedo 2012).
The process by which individuals weigh up the costs and benefits of using privacy settings can also be explained by deterrence theory (DT) or simply cost-benefit analysis, both of which involve a cognitive process of weighing up the potential costs and benefits of enacting specific behaviour (Min & Kim 2015). More specifically, DT is based on the belief that sanctions affect an individual's intention to participate in deviant behaviour, depending on the sanction severity, celerity and certainty of the particular behaviour (Abed & Weistroffer 2016). As such, individual behaviour is assumed to be driven by some punishment associated with not performing the required behaviour. Because the use of Facebook privacy settings cannot be enforced, theories that imply forms of sanction (such as DT) are not deemed relevant in this context.
The behavioural influence of subjective norms
Research provides evidence of two distinct sub-types of social norms, namely subjective and descriptive norms (Lapinski & Rimal 2005). Descriptive norms are those perceptions of the behaviour that an individual's peers are enacting. As such, they describe a behaviour that has taken or is taking place. Conversely, subjective norms are those behaviours believed to be desired by an individual's peers (Kautonen et al. 2015). Subjective norms therefore assume that individuals are more likely to enact a behaviour that they believe is desired or expected by their peers (Saeri et al. 2014).
Both descriptive and subjective norms are believed to drive an individual's behaviour towards social acceptance (Min & Kim 2015). Such acceptance even takes place to the extent that individuals may adjust their norms if they differ from the normative required behaviour. These adjustments may reinforce or counter the normative behaviour depending on how closely individuals identify with their peers (White et al. 2009). If, for example, an individual's peers do not place much emphasis on sustainability, they may avoid associated behaviours.
It should be noted that although subjective norms influence behaviour, they depend on the user population (and use case) in question. For example, subjective norms have been found to significantly influence game use but not the use of blogs (Baek, Kim & Bae 2014). Because the use of games and blogs includes voluntary settings, Baek et al.'s argument relates to how strongly individuals perceive general behavioural rules to exist within these contexts. Individuals might perceive sanctions to exist if normative behaviour is not followed in gaming, which is not the case when using blogs.
From a social media perspective, subjective norms have been found to affect the problematic use of Facebook, specifically amongst adolescents (Marino et al. 2016). Some research suggests that this is the result of adolescents being more concerned about having their personal information accessed by people who hold immediate power over them (i.e. parents or teachers) (Boyd & Hargittai 2010). To substantiate the latter, Foltz Newkirk and Schwager (2016) found that although subjective norms positively influenced Master of Business Administration (MBA) students' intention to use social media privacy settings, they exerted a relatively weak influence on intent.
Previous research has reported mixed outcomes regarding the behavioural influence of subjective norms; specifically, whether it negatively or positively influences intent. Whilst some research has found subjective norms to be the weakest predictor of intention (Ham et al. 2015; Min & Kim 2015), other studies have concluded that they have a significant influence on intention (Grimes & Marquardson 2019) and that they shape not only behavioural intentions but also the subsequent behaviour of an individual (Chung & Rimal 2016). This discrepancy in the literature may depend on the type of behaviour under consideration, the individual involved or how closely the individual identifies with significant others (White et al. 2009). It may also depend on perceptions regarding the perceived costs of non-conformance (Min & Kim 2015). Previous studies also suggest that norms are only meaningful to the extent that individuals perceive that their violation will result in some punishment or repercussion (e.g. the misuse of their personal information) (Chalub, Santos & Pacheco 2006). Given the discussion thus far, the following proposition is made:
Proposition 1 (P1): Subjective norms will influence an individual's intention to use Facebook privacy settings.
The influence of information security awareness
The literature is replete with evidence that information security awareness influences behaviour as a form of control (hence substituting it for PBC in this article). The more aware and knowledgeable a user becomes with regard to possible privacy threats, the more control they might wish to have in this regard, one such control mechanism being the Facebook privacy settings. The authors therefore argue that individuals can only take adequate protective measures once they have been made aware of the threats associated with exercising no control over their personal information (Öʇütçü, Testik & Chouseinoglou 2016). If users are not aware of the tools to protect them against threats (i.e. misuse of personal information), they will not acquire the requisite knowledge to adopt effective protective measures. Instead, these users may be unaware that Facebook provides them with tools such as the Privacy Checkup tool. This may lead to protective behaviours being enacted under false assumptions of security (Golbeck & Mauriello 2016), which may increase overall vulnerability. This affects not only these individuals but also their peers (i.e. the bidirectional relationship indicated by the dotted lines in Figure 3). Conversely, it stands to reason that if a Facebook user acts on the information received from peers (therefore increasing awareness), they may develop intentions to use the privacy settings. In doing so, this individual also inadvertently influences their peers to enact the same protective behaviour.
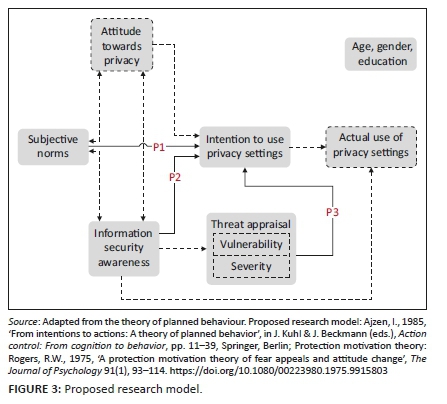
Although the bidirectional relationship between an individual's attitude towards privacy and awareness is not argued in this article, it plays a vital role when viewing the use of privacy settings holistically. In other words, the behavioural influence of the various theoretical constructs proposed by this study does not affect the intended use in a mutually exclusive manner. In general, awareness has been found to contribute to the behaviour of individuals in several contexts. Park, Kim and Park (2017) found that awareness of patient privacy amongst nursing students has a significant impact on behaviours to enact protective behaviour when considering the security of patients' personal information. Within the context of this article, awareness is assumed to have the same effect on the use of privacy settings.
Therefore, information security awareness measures the extent to which users are informed about their privacy on social networking sites, as well as the extant privacy problems, policies, violations and procedures (Zlatolas et al. 2015). Uninformed users fail to evaluate the privacy risk and information disclosure benefits rationally and thoroughly. As a result, lack of awareness is viewed as a root cause of information security incidents (Safa et al. 2018). Grimes and Marquardson (2019) found that if a user does not perceive any threats arising as a result of a particular action or behaviour, no protective measures will be taken. Therefore, in order to promote more secure online behaviour, as mentioned, users first need to be made aware of both the threats associated with the disclosure of personal information and the tools available to protect against those threats (e.g. privacy settings).
In industry, awareness programmes have been implemented to improve users' compliance and promote secure user behaviour. Bauer et al. (2017) indicate that a user's level of policy knowledge affects their intentions to comply with such policies. Businesses like Facebook have also begun relying on privacy policies as a self-regulatory mechanism in an attempt to reassure users that their personal information is secure (Benson, Saridakis & Tennakoon 2015).
Conversely, in a study by Govani and Pashley (2014), it was found that even though 84% of participants were aware that they could change their privacy settings, only 48% actually used these settings. Additionally, respondents did not change their privacy settings even after being educated on how to do so. Users therefore seemingly accept that their personal information will be misused, regardless of whether they enact protective behaviour (i.e. Facebook privacy settings). Respondents' awareness and the consequent privacy concerns only resulted in the adoption of protective behaviour if they have had a negative experience in this regard. As such, knowledge, awareness and especially experience are seen to directly influence the intention to adopt protective behaviour such as Facebook privacy settings. The authors of this article therefore argue that:
Proposition 2 (P2): Information security awareness will influence an individual's intention to use Facebook privacy settings.
The behavioural influence of threat appraisal
The authors also argue that that the adoption of protective behaviour goes beyond merely making users aware. They posit that the acquired knowledge (via awareness) has to be personally relevant if individuals are to respond appropriately (Marett et al. 2019). Additionally, the individual should be willing and able to respond effectively.
Because PMT is concerned with how and why individuals decide to adopt protective behaviour (e.g. adopting privacy settings), the authors argue that it will also influence the extent to which such protective behaviour is enacted. This stems from the fact that an individual's threat appraisal involves the measurement of the perceived vulnerability and the severity of the threat. Therefore, if an individual does not perceive a threat to be particularly severe (because of their level of knowledge and awareness), they may forgo using privacy settings. Previous research has found user perceptions to be particularly important when facing decisions relating to protective behaviour - especially within the context of fear appeals (Johnston et al. 2016). It is believed that should threat appraisal produce a sufficient amount of fear, the individual will be more likely to enact protective behaviour. This means that their level of fear - as a result of threat appraisal - may influence their intention to use privacy settings.
Similar to Hanus and Wu (2016), this study focuses on both awareness and threat appraisal as antecedents to the intended use of Facebook privacy settings. Hanus and Wu's (2016) study also demonstrates that it is not enough for users to be aware of the threats associated with a particular behaviour. Users are also influenced by their perceptions of how vulnerable they may be in this regard. The same applies to the countermeasures used to address the perceived threats. As such, awareness alone does not help promote secure behaviour, which is why the model proposed in this article also theorises the behavioural influence of threat appraisal.
Several recent studies have found evidence that attests to the behavioural influence of threat appraisal. For example, Strycharz et al. (2019) found that threat appraisal (specifically perceived severity) significantly influenced respondents' intentions to turn off personalisation in terms of the ads they are exposed to. Similarly, Feng and Xie (2019) found that respondents' control over privacy settings significantly influenced their intention to use virtual try-on (i.e. of clothing) apps. The additional controls enabled respondents to perceive themselves to be less vulnerable to threats. Vishwanath, Xu and Ngoh (2018) found that perceived threat severity significantly influences both expressive privacy and information privacy. Additionally, perceived vulnerability was found to influence accessibility privacy. Ernst, Pfeiffer and Rothlauf (2015) also found threat appraisal to exert a significant and positive influence on the intention to use the privacy settings, specifically in terms of selectivity in connections, refusal and setting strictness. Whilst a heightened threat appraisal is associated with fear (Grimes & Marquardson 2019), a user can only evaluate a risky situation if they are aware of the risks. The authors of this article therefore propose:
Proposition 3 (P3): The process of threat appraisal will influence a Facebook user's intention to use privacy settings.
Ethical consideration
This article followed all ethical standards for a research without direct contact with human or animal subjects.
Discussion
The proposed research model is an adapted version of both the TPB and PMT (see Figure 3). In this model, the construct PBC is replaced by information security awareness. Both subjective norms and threat appraisal are modelled as having a direct influence on the construct intention to use privacy settings. Note that the authors do not directly argue the behavioural influence of the dotted lines in the proposed research model. This also applies to the sub-components of the construct threat appraisal (i.e. vulnerability and severity) and demographic aspects, including negative privacy experiences. The influence of information security awareness on the actual use of privacy settings is also outside the scope of this article.
The use of this research model allows researchers to understand how both threat appraisal (P3) and information security awareness (P2) influence the use of Facebook privacy settings. The model also allows for the evaluation of the influence exerted by subjective norms (P1). The authors argue that awareness alone is not enough to understand individuals' intentions to enact protective behaviour. Instead, the authors posit that even though individuals are aware of information misuse, they may still avoid the use of privacy settings because they do not perceive the threat to be severe. Therefore, the personal information they disclose is not perceived as sufficiently important to misuse, and even if it is misused, not much harm can be done. The authors argue that this is not necessarily the case, especially if one considers that the influence exerted may have far-reaching implications beyond just the use of Facebook and personal information. Consider the use of cleverly designed posts that appear only to individuals deemed susceptible. Here, even just sharing one's gender can be used to display messages that may invoke sympathy or higher than usual levels of fear. Abnormal levels of fear, resulting from raised levels of awareness, could be used to manipulate users. Recent evidence in the form of voter profiling is but one example. Additionally, it is known that women are more sympathetic and generally more concerned about what their peers think of their behaviour and are thus influenceable (Tifferet 2019). By using the proposed research model, researchers will be able to get some indication of the extent to which subjective norms influence not only these individuals but also their peers. In doing so, the message is perpetuated, resulting in successful persuasion of an individual deemed persuadable, as alluded to in the 'Introduction' section.
Because the proposed model does not focus on other individual differences and specific psychological aspects, it is useful in instances where even a minimal amount of information is not adequately protected by the privacy settings. This makes it particularly useful in providing researchers with an initial description as to what to focus on going forward. Further statistical evaluation of this model may indicate that fear appeals, as evoked during the process of threat appraisal, do not exert a significant influence on the intended use of privacy settings.
The thematic analysis further suggests that subjective norms will exert a significant influence on the intention to use privacy settings. Given the social nature of Facebook, this is not only expected but is also important to model - especially in relation to demographic aspects. The results could be used to make Facebook users aware of the extent that even minimal amounts of personal information could be used to manipulate their behaviour, which inadvertently also influences their peers. Results may indicate that this is more pronounced for women. Thus, models like the one the authors propose here could be useful to social media platforms in that it is their responsibility to educate and make users aware of their level of susceptibility. This is exactly what Mark Zuckerberg (chief executive officer of Facebook) alluded to in his senate hearing (Timberg, Romm & Dwoskin 2018), where he essentially stated that the company did not do enough to prevent the misuse of its users' personal information. The use of similar models may thus assist in this regard.
Limitations
Because this study developed a research model from thematic interpretations, the resultant arguments are influenced by the authors' ideological frame of reference. It stands to reason that future work may develop similar models using different arguments. Additionally, although this study conducted a scoping review, as opposed to a more rigid structured review, only a limited number of secondary sources formed part of the thematic analysis. Moreover, arguments supporting the other theoretical relationships (indicated by the dotted lines in Figure 3) were omitted because of space limitations. Lastly, no statistical measures were developed and aligned with the constructs of the research model in this article.
Conclusion and future research
In this article, the authors used a thematic approach to inductively analyse a set of secondary data sources. This in turn resulted in the identification of three themes and associated thematic maps (see Figure 2). Using these thematic maps, three corresponding propositions were developed and integrated into an adapted research model consisting of components of both the TPB and PMT. To deductively evaluate the adapted research model, future research could conduct appropriate statistical analyses. For example, a covariance approach to structural equation modelling (CB-SEM) could be used to evaluate the predictive power (R2) of the resultant structural model. The use of a CB-SEM approach is particularly important, because the proposed model is recursive in nature, as opposed to a non-recursive version (i.e. without the bidirectional relationships), which could also be evaluated using a partial least squares path modelling.
Acknowledgements
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
All authors contributed equally to this work.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Abed, J. & Weistroffer, H.R., 2016, 'Understanding deterrence theory in security compliance behavior: A quantitative meta-analysis approach', in Proceedings of the Southern Association for Information Systems Conference, SAIS, pp. 1-7, St. Augustine, FL.
Acquisti, A. & Gross, R., 2006, 'Imagined communities: Awareness, information sharing, and privacy on the Facebook', Privacy Enhancing Technologies 4258, 36-58. https://doi.org/10.1007/11957454_3 [ Links ]
Ahluwalia, P. & Merhi, M.I., 2018, 'Moral and subjective norms: How do they effect information security compliance?', in Proceedings of the 24th Americas Conference on Information Systems, AMCIS, pp. 1-10, New Orleans, LA.
Ajzen, I., 1985, 'From intentions to actions: A theory of planned behavior', in J. Kuhl & J. Beckmann (eds.) Action control: From cognition to behavior, pp. 11-39, Springer, Berlin.
Amer, K. & Noujaim, J., 2019, 'The great hack', Netflix, viewed n.d., from https://www.netflix.com/za/title/80117542.
Baek, Y.M., Kim, E.M. & Bae, Y., 2014, 'My privacy is okay, but theirs is endangered: Why comparative optimism matters in online privacy concerns', Computers in Human Behavior 31, 2414-2419. https://doi.org/10.1016/j.chb.2013.10.010 [ Links ]
Bauer, S., Bernroider, E.W.N. & Chudzikowski, K., 2017, 'Prevention is better than cure! Designing information security awareness programs to overcome users' non-compliance with information security policies in banks', Computers & Security 68, 145-159. https://doi.org/10.1016/j.cose.2017.04.009 [ Links ]
Benson, V., Saridakis, G. & Tennakoon, H., 2015, 'Information disclosure of social media users: Does control over personal information, user awareness and security notices matter?', Information Technology and People 28(3), 426-441. https://doi.org/10.1108/ITP-10-2014-0232 [ Links ]
Bowen, G.A., 2009, 'Document analysis as a qualitative research method', Qualitative Research Journal 9(2), 27-40. https://doi.org/10.3316/QRJ0902027 [ Links ]
Boyd, D. & Hargittai, E., 2010, 'Facebook privacy settings: Who cares?', First Monday: Peer-Reviewed Journal on the Internet 15(8). https://doi.org/10.5210/fm.v15i8.3086 [ Links ]
Braun, V. & Clarke, V., 2006, 'Using thematic analysis in psychology', Qualitative Research in Psychology 3(2), 77-101. https://doi.org/10.1191/1478088706qp063oa [ Links ]
Chalub, F.A.C.C., Santos, F.C. & Pacheco, J.M., 2006, 'The evolution of norms', Journal of Theoretical Biology 241(2), 233-240. https://doi.org/10.1016/j.jtbi.2005.11.028 [ Links ]
Chung, A. & Rimal, R.N., 2016, 'Social norms: A review', Review of Communication Research 4, 1-28. [ Links ]
Debatin, B., Lovejoy, J.P., Horn, A.-K. & Hughes, B.N., 2009, 'Facebook and online privacy: Attitudes, behaviors, and unintended consequences', Journal of Computer-Mediated Communication 15(1), 83-108. https://doi.org/10.1111/j.1083-6101.2009.01494.x [ Links ]
Dickinson, S.J. & Holmes, M., 2008, 'Understanding the emotional and coping responses of adolescent individuals exposed to threat appeals', International Journal of Advertising 27(2), 251-278. https://doi.org/10.1080/02650487.2008.11073054 [ Links ]
Ernst, H., Pfeiffer, J. & Rothlauf, F., 2015, 'Privacy protecting behavior in social network sites', in C-P.H. Ernst (ed.), Factors driving social network site usage, pp. 1-9, Springer, Wiesbaden.
Facebook, 2019, What is public information on Facebook?, viewed 01 April 2020, from https://www.facebook.com/help/203805466323736
Feng, Y. & Xie, Q., 2019, 'Privacy concerns, perceived intrusiveness, and privacy controls: An analysis of virtual try-on apps', Journal of Interactive Advertising 19(1), 43-57. https://doi.org/10.1080/15252019.2018.1521317 [ Links ]
Foltz, B.B., Newkirk, H.E. & Schwager, P.H., 2016, 'An empirical investigation of factors that influence individual behavior toward changing social networking security settings', Journal of Theoretical and Applied Electronic Commerce Research 11(2), 1-15. https://doi.org/10.4067/S0718-18762016000200002 [ Links ]
Golbeck, J. & Mauriello, M., 2016, 'User perception of Facebook app data access: A comparison of methods and privacy concerns', Future Internet 8(2), 9. https://doi.org/10.3390/fi8020009 [ Links ]
Govani, T. & Pashley, H., 2014, 'Student awareness of the privacy implications when using Facebook', Cyberpsychology 8(2), 1-17. [ Links ]
Grimes, M. & Marquardson, J., 2019, 'Quality matters: Evoking subjective norms and coping appraisals by system design to increase security intentions', Decision Support Systems 119, 23-34. https://doi.org/10.1016/j.dss.2019.02.010 [ Links ]
Ham, M., Jeger, M. & Ivković, A.F., 2015, 'The role of subjective norms in forming the intention to purchase green food', Economic Research-Ekonomska Istrazivanja 28(1), 738-748. https://doi.org/10.1080/1331677X.2015.1083875 [ Links ]
Hanus, B. & Wu, Y., 2016, 'Impact of users' security awareness on desktop security behavior: A protection motivation theory perspective', Information Systems Management 33(1), 2-16. https://doi.org/10.1080/10580530.2015.1117842 [ Links ]
Haynes, D., Bawden, D. & Robinson, L., 2016, 'A regulatory model for personal data on social networking services in the UK', International Journal of Information Management 36(6), 872-882. https://doi.org/10.1016/j.ijinfomgt.2016.05.012 [ Links ]
Ifinedo, P., 2012, 'Understanding information systems security policy compliance: An integration of the theory of planned behavior and the protection motivation theory', Computers & Security 31(1), 83-95. https://doi.org/10.1016/j.cose.2011.10.007 [ Links ]
Joffe, H., 2012, Qualitative research methods in mental health and psychotherapy: A guide for students and practitioners, pp. 209-223, Wiley-Blackwell, New York, NY.
Johnston, A.C., Warkentin, M., McBride, M. & Carter, L., 2016, 'Dispositional and situational factors: Influences on information security policy violations', European Journal of Information Systems 25(3), 231-251. https://doi.org/10.1057/ejis.2015.15 [ Links ]
Kautonen, T., Van Gelderen, M. & Fink, M., 2015, 'Robustness of the theory of planned behavior in predicting entrepreneurial intentions and actions', Entrepreneurship Theory and Practice 39(3), 655-674. https://doi.org/10.1111/etap.12056 [ Links ]
Kusyanti, A., Puspitasari, D.R., Catherina, H.P.A. & Sari, Y.A.L., 2017, 'Information privacy concerns on teens as Facebook users in Indonesia', Procedia Computer Science 124, 632-638. https://doi.org/10.1016/j.procs.2017.12.199 [ Links ]
Lapinski, M.K. & Rimal, R.N., 2005, 'An explication of social norms', Communication Theory 15(2), 127-147. https://doi.org/10.1111/j.1468-2885.2005.tb00329.x [ Links ]
Lewis, K., Kaufman, J. & Christakis, N., 2008, 'The taste for privacy: An analysis of college student privacy settings in an online social network', Journal of Computer-Mediated Communication 14(1), 79-100. https://doi.org/10.1111/j.1083-6101.2008.01432.x [ Links ]
Marett, K., Vedadi, A. & Durcikova, A., 2019, 'A quantitative textual analysis of three types of threat communication and subsequent maladaptive responses', Computers & Security 80, 25-35. https://doi.org/10.1016/j.cose.2018.09.004 [ Links ]
Marino, C., Vieno, A., Pastore, M., Albery, I.P., Frings, D. & Spada, M.M., 2016, 'Modeling the contribution of personality, social identity and social norms to problematic Facebook use in adolescents', Addictive Behaviors 63, 51-56. https://doi.org/10.1016/j.addbeh.2016.07.001 [ Links ]
Min, J. & Kim, B., 2015, 'How are people enticed to disclose personal information despite privacy concerns in social network sites? The calculus between benefit and cost', Journal of the Association for Information Science and Technology 66(4), 839-857. https://doi.org/10.1002/asi.23206 [ Links ]
Munn, Z., Peters, M.D.J., Stern, C., Tufanaru, C., McArthur, A. & Aromataris, E., 2018, 'Systematic review or scoping review? Guidance for authors when choosing between a systematic or scoping review approach', BMC Medical Research Methodology 18(143), 1-7. https://doi.org/10.1186/s12874-018-0611-x [ Links ]
Öʇütçü, G., Testik, Ö.M. & Chouseinoglou, O., 2016, 'Analysis of personal information security behavior and awareness', Computers & Security 56, 83-93. https://doi.org/10.1016/j.cose.2015.10.002 [ Links ]
Park, E.H., Kim, J. & Park, Y.S., 2017, 'The role of information security learning and individual factors in disclosing patients' health information', Computers & Security 65, 64-76. https://doi.org/10.1016/j.cose.2016.10.011 [ Links ]
Rogers, R.W., 1975, 'A protection motivation theory of fear appeals and attitude change', The Journal of Psychology 91(1), 93-114. https://doi.org/10.1080/00223980.1975.9915803 [ Links ]
Saeri, A.K., Ogilvie, C., La Macchia, S.T., Smith, J.R. & Louis, W.R., 2014, 'Predicting Facebook users online privacy protection: Risk, trust, norm focus theory, and the theory of planned behavior', Journal of Social Psychology 154(4), 352-369. https://doi.org/10.1080/00224545.2014.914881 [ Links ]
Safa, N.S. & Von Solms, R., 2016, 'An information security knowledge sharing model in organizations', Computers in Human Behavior 57, 442-451. https://doi.org/10.1016/j.chb.2015.12.037 [ Links ]
Safa, N.S., Maple, C., Watson, T. & Von Solms, R., 2018, 'Motivation and opportunity based model to reduce information security insider threats in organisations', Journal of Information Security and Applications 40, 247-257. https://doi.org/10.1016/j.jisa.2017.11.001 [ Links ]
Stern, T. & Salb, D., 2015, 'Examining online social network use and its effect on the use of privacy settings and profile disclosure', Bulletin of Science, Technology & Society 35(1-2), 25-34. https://doi.org/10.1177/0270467615596890 [ Links ]
Strater, K. & Lipford, H., 2008, 'Strategies and struggles with privacy in an online social networking community', in Proceedings of the 22nd British HCI Group Annual Conference on People and Computers: Culture, Creativity, Interaction, BCS-HCI, pp. 111-119, Liverpool.
Strycharz, J., Van Noort, G., Smit, E. & Helberger, N., 2019, 'Protective behavior against personalized ads: Motivation to turn personalization off', Cyberpsychology 13(2), 1-22. https://doi.org/10.5817/CP2019-2-1 [ Links ]
Symeonidis, I., Biczók, G., Shirazi, F., Pérez-Solà, C., Schroers, J. & Preneel, B., 2018, 'Collateral damage of Facebook third-party applications: A comprehensive study', Computers & Security 77, 179-208. https://doi.org/10.1016/j.cose.2018.03.015 [ Links ]
Tifferet, S., 2019, 'Gender differences in privacy tendencies on social network sites: A meta-analysis', Computers in Human Behavior 93, 1-12. https://doi.org/10.1016/j.chb.2018.11.046 [ Links ]
Timberg, C., Romm, T. & Dwoskin, E., 2018, 'Zuckerberg apologizes, promises reform as senators grill him over Facebook's failings', viewed 01 April 2020, from https://www.washingtonpost.com/business/technology/2018/04/10/b72c09e8-3d03-11e8-974f-aacd97698cef_story.html.
Tsai, H.Y.S., Jiang, M., Alhabash, S., LaRose, R., Rifon, N.J. & Cotten, S.R., 2016, 'Understanding online safety behaviors: A protection motivation theory perspective', Computers & Security 59, 138-150. https://doi.org/10.1016/j.cose.2016.02.009 [ Links ]
Vishwanath, A., Xu, W. & Ngoh, Z., 2018, 'How people protect their privacy on Facebook: A cost-benefit view', Journal of the Association for Information Science and Technology 69(5), 700-709. https://doi.org/10.1002/asi.23894 [ Links ]
White, K.M., Smith, J.R., Terry, D.J., Greenslade, J.H. & Blake, M., 2009, 'Social influence in the theory of planned behaviour : The role of descriptive, injunctive, and ingroup norms', Society 48(1), 135-158. https://doi.org/10.1348/014466608X295207 [ Links ]
Witte, K. & Allen, M., 2000, 'A meta-analysis of fear appeals: Implications for effective public health campaigns', Health Education & Behavior 27(5), 591-615. https://doi.org/10.1177/109019810002700506 [ Links ]
Zlatolas, L.N., Welzer, T., Heričko, M. & Hölbl, M., 2015, 'Privacy antecedents for SNS self-disclosure: The case of Facebook', Computers in Human Behavior 45, 158-167. https://doi.org/10.1016/j.chb.2014.12.012 [ Links ]
 Correspondence:
Correspondence:
Karl van der Schyff
k.vanderschyff@ru.ac.za
Received: 08 Apr. 2020
Accepted: 03 Aug. 2020
Published: 27 Oct. 2020
ORIGINAL RESEARCH
The effect of affective and normative commitment on helping behaviour in different online contexts
Mia Bothma
School of Management Sciences, Faculty of Economic and Business Management, North-West University, Potchefstroom, South Africa
ABSTRACT
BACKGROUND: Despite the benefits provided by online communities and online retailing, administrators and managers are faced with several challenges to successfully manage these platforms. Helping behaviours may assist to overcome these challenges; however, knowledge about this construct in different online environments is limited.
OBJECTIVES: To investigate the influence of affective and normative commitment on helping behaviour within non-commercial and commercial online environments.
METHOD: Data were collected through online questionnaires. The sample included residential online community members who actively participated in the community during the last 12 months (non-commercial sample) or had made an online purchase during the last 12 months (commercial sample). Non-probability sampling was used and the data analysis included descriptive statistics using SPSS and structural equation modelling using Mplus software.
RESULTS: In both online environments, affective commitment positively influenced the helping behaviours of online community members and online customers; however, the relationship between normative commitment and helping behaviour was only significant for the non-commercial online environment. Informational support, satisfaction and subjective norm were confirmed as antecedents of affective and normative commitment for both online environments.
CONCLUSION: Affectively committed online community members and online retail customers are likely to perform helping behaviours and will become affectively and normatively committed when the community and online retailer provide satisfactory service to the members and customers. Online community members who are normatively committed will help fellow members to use the service of the online community; and should online community members and online customers experience subjective norm, they will become normatively committed.
Keywords: affective commitment; normative commitment; online communities; online retailing; relationship marketing.
Introduction
During the past decade, online retailing and online communities have grown significantly. Using the internet, customers can make online purchases and join online communities where they reap benefits such as convenience, information, product variety and social- and functional support (Chiang, Lin & Huing 2018; Khan 2016). However, despite the benefits, online retailers and online community administrators are struggling to successfully manage these platforms. Online retailers face fierce competition, high switching and low customer retention (Chiu et al. 2011; Chou & Hsu 2016; Kaur & Kochar 2018), whereas administrators have the endless challenge to manage user participation and discourage inappropriate member behaviour (Kraut & Resnick 2011; Malinen 2015).
It seems that helping behaviours by individuals may help to overcome these challenges, because these behaviours result in reduced costs, increased satisfaction, the creation of a sense of belongingness and increased level of service delivery (Anaza 2014; Chu 2009; Yi, Gong & Lee 2013; Yu-Hong, Da-hai & Sheng-nan 2013). Initially introduced in the offline environment (Gruen, Summers & Acito 2000), technological innovations such as online self-services and social media are extending helping behaviours to online environments (Frasquet-Deltoro, Alarcón-del-Amo & Lorenzo-Romero 2019). In the absence of direct employee involvement, customers in a commercial context such as online retailing can now turn to fellow customers for help to use the retailer's online self-service (Van Tonder et al. 2018). Similarly, within a non-commercial environment, such as online communities, members are able to assist fellow members to use the community correctly (Malinen 2015).
Grounded in the social exchange theory, helping behaviours are viewed as a dimension of citizenship behaviour that are voluntary in nature and provide assistance to others (Bove et al. 2009; Yi & Gong 2013). Even though citizenship behaviour is a contemporary topic (Chiu et al. 2019; Godwin & Wright 2019), the helping behaviour dimension has received limited attention within the online environment. Commitment, grounded in relationship marketing, has been established as an antecedent of citizenship behaviour (Hashim & Tan 2015; Yong, Sachau & Lassiter 2011). However, prior research has generally narrowed the focus to only investigate the influence of affective commitment on citizenship behaviours (Curth, Uhrich & Benkenstein 2014; Mpinganjira 2016) and ignored the effect that normative commitment may have on helping behaviours.
The purpose of this study, is therefore, to provide more insight on the helping behaviours of individuals, as preceded by both affective and normative commitment and their relevant antecedents. The novel conceptual model was furthermore tested in diverse online contexts, which provided a unique contribution to the online retailing and online community environments. Ultimately, the research findings may provide a better understanding of the helping behaviour dimension that can assist managers and administrators to increase participation, purchases and social interaction. The research also aims to offer a comprehensive understanding of commitment, as a multidimensional construct by investigating both affective and normative commitment in a non-commercial and commercial environment. Through a better understanding of commitment, managers and administrators will be in a more favourable position to implement strategic tactics to increase the level of commitment of members and online customers.
Research background
An online community refers to a group of people who share a purpose, interest or goal on an online platform (Preece 2000). Since inception, online communities have evolved into a platform that has massive influences on diverse parts of the society such as the economy, government and cities (Baek & Kim 2015). Although different forms of online communities exist (Ling, Guo & Yang 2014; Stokburger-Sauer & Wiertz 2015), this study focuses on residential online communities on Facebook, which include residents of a city who share a common interest, for example, the 'Potchefstroom' Facebook group. Residential online communities provide a platform for members where they can become more aware of the city's activities and can ask fellow members for assistance and information. Local businesses advertise their products and solve problems, whilst the local government use online communities to communicate and interact with residents. Interactions on residential online communities are social in nature and these social interactions provide members with the opportunity to access and exchange information whilst resources are distributed in the community (Chen, Boh & Mo 2018).
Online retailing refers to the adoption of digital technology that allows for purchasing or selling transactions to take place (Okonkwo 2010). Compared to offline shopping, online shopping provides instantaneous and accurate information about each purchase, enable customisation through customer accounts and store all payment information (Chen, Sain & Guo 2012). Online retail purchases in South Africa have reached the R14-billion mark in 2018, representing 1.4% of total retail, with forecasts indicating that 2019 may see a 20% growth in online retail sales (World Wide Works 2018).
Theoretical framework
The key theories and constructs of the study are discussed in the subsequent sections.
Social exchange theory
The social exchange theory is based on the principles of voluntary actions where individuals are motivated by the expected returns from an interaction. This means that the social exchange by one individual in a relationship motivates the other individual to respond with benefits at their preference (Blau 1964). Reciprocity is viewed as a core element of the social exchange theory (Tanskanen 2015) because the beneficial deeds towards other people are reciprocated through service and expression of gratitude. Therefore, when customers benefit from other customers or the organisation, they feel obligated to react by performing behaviours that are not expected or required of them, which are also known as customer citizenship behaviours.
Customer citizenship and helping behaviours
Voluntary behaviour of customers that delivers value to the organisations but are not required to be performed by the customer is known as customer citizenship behaviour (Hau & Thuy 2016). Performed towards the organisation, employees or other customers, these behaviours positively influence the performance and experience of these stakeholders (Bove et al. 2009). Online community members are in an ideal position to assist fellow members by teaching, helping and giving advice of how to accurately and correctly use the online community (Chou & Hsu 2016; Yi & Gong 2013). Online retail customers also perform helping behaviours towards fellow customers (Anaza & Zhou 2013) when for instance they assist fellow online customers to make an online purchase (Ponnusamy 2015). Online customers can, for example, help other customers by showing or telling them how to make a purchase on the online retailer's website or who to contact when they want to return a product.
Relationship marketing
Relationship marketing refers to the process of 'attracting, maintaining and enhancing customer relationships in a multi-service organisation' (Berry 1983) that are characterised by long-term relationships between the customer and the organisation with a customer-participation focus (Gummerus, Van Koskull & Kowalkowski 2017).
Digital, mobile and social technological developments have impacted the dynamics of the customer-organisation relationships (Payne & Frow 2017). In the online environment, no face-to-face interaction takes place; and all exchanges are mediated by the internet, and relational exchanges that are facilitated by the internet and take place within a human-to-technology environment (Steinhoff et al. 2019).
Commitment
Commitment is a key underpinning of relationship marketing (Benouakrim & El Kandoussi 2013) and is viewed as a multidimensional construct that consists of affective, normative and continuous commitment (Meyer & Allen 1991). This study only includes affective and normative commitment because research has indicated that continuous commitment has a negative influence on citizenship behaviour (helping behaviour) and is therefore excluded.
Affective commitment
Affective commitment refers to the attachment, identification and involvement of the customer towards the organisation (Bansal et al. 2004). When an online community member has an emotional connection or attachment towards the community and can identify themselves with the community, the member is said to be affectively committed (Cheung & Lee 2009). In addition, affective commitment occurs in commercial online environments, where the online customer becomes affectively committed to the online retailer through the emotional connection formed between the parties (Boateng & Narteh 2016).
Normative commitment
Normative commitment indicates the individual's sense of obligation to continue with a relationship where the individual and organisation or brand share important norms and values (Fullerton 2011; Meyer & Allen 1991). Normative commitment with organisations therefore happens through the development of a strong correspondence between the values of the organisation and that of the customer (Fullerton 2014). Although limited research exists, both online community members and online customers can become normatively committed when they feel obligated to remain as a member of the online community or as a customer of the online retailer (Boateng & Narteh 2016; Cheung & Lee 2012).
Conceptual model and hypotheses development
The following section provides arguments for the development of the conceptual model.
Consequences of affective and normative commitment
Marketing scholars seem to agree that commitment facilitates citizenship behaviour (Hashim & Tan 2015; Yong et al. 2011). Online community members with a strong emotional attachment towards the online community will perform helping behaviours by replying to posts of fellow members (Bateman, Gray & Butler 2011), and affectively commitment online customers will act beyond only purchasing a product when they assist fellow customers to use the service of the online retailer (Van Tonder et al. 2018). Although not yet investigated within an online community and online retail environments, in offline environments, normative commitment has been established to positively and significantly influence citizenship behaviour (Fullerton 2011; Spik 2016).
For the present study, based on the above-mentioned research, it is plausible to argue that when a residential online community has personal meaning for the members and they feel emotionally attached to the community, then the members might be likely to perform helping behaviours. This same argument is also valid for online retail customers, where affectively committed online customers assist fellow customers when they need help to use the service of the online retailer.
Consequently, it is hypothesised that:
H1: Affective commitment has a positive effect on helping behaviour within a non-commercial and commercial online environment.
Although limited studies exist, based on the research by Spik (2016) and Fullerton (2011), when online community members and online retail customers become normatively committed towards the online community and online retailer, they may also perform helping behaviours towards fellow members or customers, where they assist, teach and help them to use the services correctly. Therefore, it is hypothesised that:
H2: Normative commitment has a positive effect on helping behaviour in a non-commercial and commercial online environment.
Factors influencing affective and normative commitment
Informational support
Part of the social support theory, informational support refers to the providing of guidance and/or information and takes place when an individual assists another individual to have a better understanding of a difficult event and what resources and coping strategies are needed to resolve the problem (Kim et al. 2008). Informational support in online communities is provided through messages, normally in the form of recommendations, advice or knowledge. The informational support by online community members are grounded in their own knowledge and past experience and can also act as a supplement to the organisation's information (Zhu, Sun & Chang 2016). Informational support in an online retail setting is provided when online customers, for example, communicate their experiences concerning the purchase of the product, the timing of the delivery and features of the product to fellow customers (Lal 2017).
When members of an online community offer suggestions and information to overcome problems, the receiving member will become more emotionally connected towards the online community (Chen et al. 2013). Confirmed by Mpinganjira (2016), affective commitment is positively influenced by informational support, as part of the social support construct. Even though the relationship between informational support and affective commitment within a commercial environment has not yet been tested, based on the above-mentioned studies, when online retail customers receive suggestions and information from fellow customers, these customers may also become emotionally attached to the online retailer. Therefore, it is hypothesised that:
H3: Informational support has a positive effect on affective commitment in a non-commercial and commercial online environment.
Satisfaction
Customer satisfaction is a post-consumption evaluation process, which indicates that the experience was as good as it was supposed to be (Oliver 1980). Viewed as a direct outcome of brand experience, customer satisfaction is emotional and psychological in nature and results from individual customer experiences (Chahal & Dutta 2015; Lin 2015). The satisfaction of online community members is dependent on the quality of interactions taking place; hence, the quality of the posts, comments and discussion topics will influence how satisfied an online community member is with the community (De Valck, Wan Bruggen & Weirenga 2009). A strong sense of satisfaction will therefore enhance the likelihood that an online community member continues to participate and engage with the community. When a member has a strong sense of satisfaction, they are likely to participate and engage with the community (Chiu et al. 2013). Customer satisfaction is regarded as one of the essential elements of organisational success because it is closely associated with an organisation's competitiveness and revenue creation (Liao et al. 2017).
Satisfaction positively influences affective commitment in various diverse contexts (Jin, Park & Kim 2010; Muhammad et al. 2014; Zhou et al. 2012). Satisfied online community members will become more affectively committed towards the community resulting in them feeling emotionally attached and having a strong sense of belonging towards the community (Jin et al. 2010; Zhou et al. 2012). In addition, based on the existing research mentioned, when online customers are satisfied with the service they receive from the online retailer, these customers may also become affectively committed towards the retailer. Subsequently, it is hypothesised that:
H4: Satisfaction has a positive effect on affective commitment in a non-commercial and commercial online environment.
The effect of satisfaction on normative commitment has not yet been extensively explored. However, within an organisational environment, a high level of job satisfaction will result in the employees feeling obligated to continue with their employment (Aydogdu & Asikgil 2011). In addition, offline banking clients become normatively committed towards their bank when they are satisfied with the service received (Fatima, Razzaque & De Mascio 2016).
Taking into consideration the mentioned research, the same positive relationship may also exist in a non-commercial and commercial environment. When online community members are satisfied with the service they receive from the residential online community, they may also feel obligated to continue using the online community and participate in discussions. Also, when online retail customers are satisfied with the service they receive from the online retailer, these customers may become normatively committed and feel obligated to continue using the online retailer. Therefore, it is hypothesised that:
H5: Satisfaction has a positive effect on normative commitment in a non-commercial and commercial online environment.
Subjective norm
The perception of a person that most of the individuals who are important to them are of the opinion that they should perform a certain behaviour, which is known as subjective norm (Ajzen 1991). This suggests the influence of expectations of other individuals and is often referred to as social normative compliance or social pressure to act in a certain way (Shen et al. 2011). The subjective norm of an online community member indicates the effect of another individual's opinion on the member's behaviour; hence, the member will participate in the community when they are of the opinion that influential individuals approve participation (Zhou 2011). Online customers also experience subjective norm in the form of referent individuals such as friends and family who want them to use an online retailer and, therefore, directly influence their purchase behaviour (Lin, Liu & Ngo 2016; Siti, Mohammed & Nik Kamariah 2012).
Research amongst customers of luxury brands (Shukla, Banerjee & Singh 2016) and users of online social networks (Chen et al. 2013) indicated that subjective norm has a positive and significant effect on normative commitment. The same result might also occur in the online community and online retail environments. Within these environments, when people who influence their behaviours, such as friends, are of the opinion that they should participate in discussions or that they should use the online retailer, then the members/customers may feel obligated to do so. Consequently, it is hypothesised that:
H6: Subjective norm has a positive effect on normative commitment in a non-commercial and commercial online environment.
Based on the aforementioned discussion, the conceptual model for the study is presented in Figure 1.
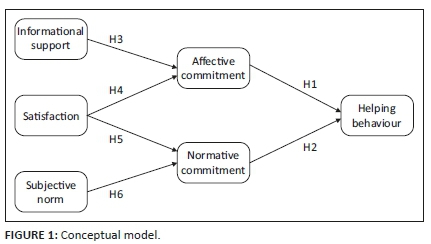
Research methodology
Population, research design, data collection and sampling approach
The non-commercial sample (online community members) included males and females older than the age of 18 years, who are currently active members of a residential online community on Facebook in South Africa. The commercial sample (online retailing) included male and female members of residential online communities on Facebook in Gauteng, Western Cape and Kwa-Zulu Natal, who are older than 18 years of age and have purchased products from online retailers during the last 12 months. Gauteng, Western Cape and Kwa-Zulu Natal were selected because these provinces are the most economically active provinces in South Africa and have the highest economic growth rate (Watkins 2019).
An explanatory research design was followed with the aim to explain the empirical relationship between the variables (Saunders, Lewis & Thornhill 2016). Quantitative data were collected using online self-administrated questionnaires that were posted on the different residential Facebook groups. Because no sample frame exists, the study employed non-probability sampling which included quota- and convenience sampling. For the non-commercial sample, the largest residential Facebook group in each province of South Africa was surveyed together with four smaller residential Facebook groups; and for the commercial sample, the biggest and four smaller residential groups in the Gauteng, Western Cape and Kwa-Zulu Natal provinces were selected. In addition, convenience sampling was used where the questionnaire was posted in the newsfeed of each Facebook group. The study included more than six constructs; hence a sample size of at least 400 respondents per contexts was obtained (Hair et al. 2014). A summary of the demographic information from the realised samples is presented in Table 1.
Measurement instrument
Existing, valid and reliable scales were adapted to develop the measurement instruments for two different environments. Respondents used a five-point Likert scale where '1' indicated 'strongly disagree' and '5' indicated 'strongly agree' to show their level of agreement with the statements measuring the different constructs in the study. The items measuring informational support, satisfaction and subjective norms were adapted from Chen et al. (2013) and Fatima et al. (2016); and the items measuring affective and normative commitment and helping behaviour were adapted from Chen et al. (2013) and Yi and Gong (2013).
Research findings
Measurement model validity and reliability
The scales were reliable, because all Cronbach alpha values were above 0.80 (Pallant 2013). Confirmatory factor analysis (CFA) indicated that the measurement items were valid and reliable (Fornell & Larcker 1981; Hair et al. 2014). Table 2 indicates that all factors loaded significantly on their respective constructs (p < 0.001), and all standardised factor loadings were above 0.70. The average variance explained (AVE) and composite reliability (CR) values of the constructs were higher than the cut-off values of 0.50 and 0.70, respectively (Hair et al. 2014).
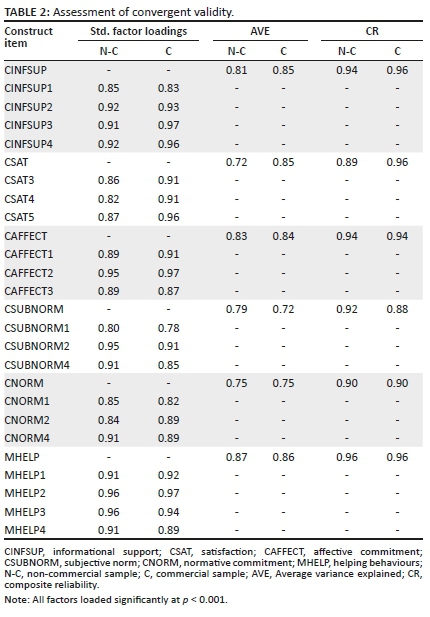
In order to access for discriminant validity, the recommendation by Fornell and Larker (1981) was used. As indicated in Table 3, all correlations between the latent constructs were significant (p < 0.001) and the AVE for any two individual constructs was greater than the squared correlation estimates between them.
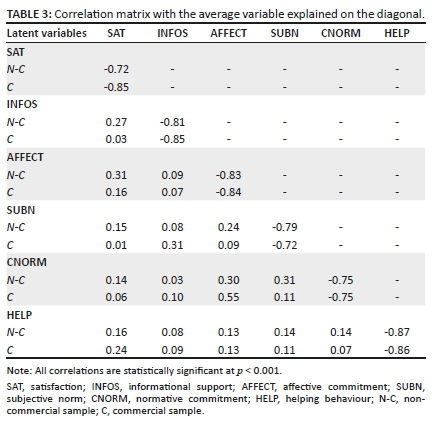
Subsequently to the confirmation of internal reliability and validity, the structural model was accessed. Adequate fit indices were obtained: Non-commercial sample: χ2/df = 2.67; comparative fit index (CFI) = 0.97; Tucker-Lewis index (TLI) = 0.97; root mean square error of approximation (RMSEA) = 0.055; and commercial sample: χ2/df = 4.39; CFI = 0.94; TLI = 0.92; RMSEA = 0.09 (Hair et al. 2014).
The structural relationships for the structural model were tested and are presented in Table 4.
Ethical consideration
The author confirms that the study has received the required ethical clearance from the Economic and Management Science Research Ethics Committee (EMS-REC) of North-West University. Ethical clearance number: NWU-00600-17-A4. Participation in this study was voluntary and confidential and participants were allowed to withdraw from the interview at any stage without any consequences. The questionnaire did not request any personal information from the respondent and no information was reported on an individual basis.
Discussion and implications
This study investigated the influence of affective and normative commitment on helping behaviours of online community members and online customers. The results indicated that for non-commercial environments such as online communities on Facebook, both affective and normative commitment positively and significantly influence the helping behaviours of the members. When members feel emotionally attached and/or have a sense of obligation towards the community, they will reciprocate by assisting fellow members to use the group correctly. The results extended the findings by Bateman et al. (2011) and studies within the offline environment (Fullerton 2011; Spik 2016) by indicating that within a residential online community on Facebook, the same relationship exists. The study furthermore provides a novel contribution by confirming that within a commercial environment, online customers will assist and help other customers to correctly use the service of the online retailer when they have had a sense of identification with and have developed an emotional connection with the online retailer.
Another original finding is that the relationship between informational support and affective commitment within the commercial context is both positive and significant. When online customers receive suggestions and information to use the online retailer's service, these customers will become more affectively committed towards the online retailer, which in turn will result in them performing helping behaviours. In agreement with the results of Muhammad et al. (2014), Jin et al. (2010) and Zhou et al. (2012), it was confirmed that in a non-commercial and commercial environment, when online community members and online customers are satisfied with their choice of provider and has an enjoyable experience, then they will become more affectively committed members and customers. Extending on studies within the organisational environment (Aydogdu & Asikgil 2011), it was also established that within both a commercial and non-commercial environment, satisfied online community members and online retail customers will continue to use the online community/online retailer out of a sense of duty and will feel guilty if they discontinue the relationship.
The subjective norm of online community members and online customers has not yet been extensively explored in literature. This study agreed with the findings of Shukla et al. (2016) and Chen et al. (2013) that when online community members are of the opinion that people who are important to them think that they should post and reply to post on the residential online community on Facebook, these members will feel obligated to continue using the service of the community. The same is true for online customers. When online customers experience the subjective norm of influential and important people, they will feel guilty if they stop using the online retailer and will use the online retailer partly out of a sense of duty.
It is vital that administrators of online communities acknowledge that online community members can become affective and normative committed towards the community, which will result in participation when members perform helping behaviours. Therefore, administrators should increase the level of satisfaction experienced by the members by introducing or welcoming new members to the community and identifying struggling members. In addition, administrators can also tag expert members in posts, to motivate members to assist and help fellow members when they ask a question. Because important and influential individuals of the members influence their participation in the online community, administrators can also launch a strategy such as refer a friend to increase membership numbers and level of participation.
As discussed, affective commitment online customers will perform helping behaviours that are beneficial to the online retailer. Therefore, online retail managers should aim to increase the information support provided and also the satisfaction levels of these customers. Online customers should be motivated and incentivised when they make suggestions and give information to fellow customers. In addition, online retail managers should get regular feedback from customers of how they can improve the online retail platform and should ensure that the correct product is delivered in a timeous manner.
Limitations and recommendations
Whilst this study provides various theoretical and managerial insights relating to helping behaviours in a commercial and non-commercial environment, the study also has some limitations. The study focused on affective and normative commitment and excluded continuous commitment; and therefore, it is recommended that future research should investigate continuous commitment, with the aim to provide a more comprehensive understanding of the multidimensional nature of commitment. Only one dimension of citizenship behaviour was included in the model. Various dimensions have been established in the literature and although no study has determined the most relevant and important dimension, future studies might investigate some of the other dimensions not tested in this study. The study focused on certain antecedents of affective and normative commitment, which the author deemed relevant to the environments of study. However, future studies may also investigate a wider range of antecedents. The study made use of non-probability sampling because no sample frame was available. Although non-probability sampling is widely accepted, it is recommended that future research should attempt to gain the contact details of online community members, as to utilise probability sampling. Additionally, stricter quota sampling is also recommended, to ensure the representativeness of the results.
Conclusion
Online communities and online retailing have grown substantially during the last decade and provide various benefits to members, customers, organisations, administrators and government. However, administrators and online retail managers are faced with various challenges to successfully manage their sites. The research aimed to provide knowledge that can assist managers with these challenges by investigating the influence of affective and normative commitment on helping behaviours in non-commercial and commercial environments. In both these environments, affective commitment is a key antecedent of helping behaviour; however, normative commitment also positively influences the helping behaviours of online community members. The study furthermore indicated that in a commercial environment, informational support and satisfaction have a positive influence on affective and normative commitment. However, it does seem that informational support received by online community members does not influence the level of affective commitment towards the community. Normative commitment has not received much attention in academic literature. This study, however, has indicated that normative commitment is relevant in both environments and that the subjective norm of online community members and online customers has a positive and significant influence on the normative commitment of these members and customers.
Acknowledgements
Competing interests
The author confirmed that no competing interests exist.
Author's contribution
The author declares that she is the sole author of this research article.
Funding information
This research received no specific grant from any funding agency in the public, commercial or not-for-profit sectors.
Data availability statement
Data sharing is not applicable to this article as no new data were created or analysed in this study.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Ajzen, I., 1991, 'The theory of planned behavior', Organisational Behavior and Human Decision Processes 50(2), 179-211. https://doi.org/10.1016/0749-5978(91)90020-T [ Links ]
Anaza, N.A., 2014, 'Personality antecedents of customer citizenship behaviours in online shopping situations', Psychology and Marketing 31(4), 251-263. https://doi.org/10.1002/mar.20692 [ Links ]
Anaza, N.A. & Zhao, J., 2013, 'Encounter-based antecedents of e-customer citizenship behaviors', Journal of Services Marketing 27(2), 130-140. https://doi.org/10.1108/08876041311309252 [ Links ]
Aydogdu, S. & Asikgil, B., 2011, 'An empirical study of the relationship among job satisfaction, organizational commitment and turnover intention', International Review of Management and Marketing 1(3), 43-53. [ Links ]
Baek, S.I. & Kim, Y.M., 2015, 'Longitudinal analysis of online community dynamics', Industrial Management & Data Systems 115(4), 661-677. https://doi.org/10.1108/IMDS-09-2014-0266 [ Links ]
Bansal, H.S., Irving, P.G. & Taylor, S.F., 2004, 'A three-component model of customer commitment to service providers', Journal of the Academy of Marketing Science 32(3), 234-250. https://doi.org/10.1177/0092070304263332 [ Links ]
Bateman, P.J., Gray, P.H. & Butler, B.S., 2011, 'Research note: The impact of community commitment on participation in online communities', Journal of Information Systems Research 22(4), 841-854. https://doi.org/10.1287/isre.1090.0265 [ Links ]
Benouakrim, H. & El Kandoussi, F., 2013, 'Relationship marketing: Literature review', International Journal of Science and Research 2(10), 148-152. [ Links ]
Berry, L.L., 1983, 'Relationship marketing', in L. Berry, G.L. Shostack & G.D. Upah (eds.), Emerging perspectives on services marketing, pp. 25-28, American Marketing Association, Chicago, IL.
Blau, P.M., 1964, Exchange and power in social life, Wiley, New York, NY.
Boateng, S.L. & Narteh, B., 2016, 'Online relationship marketing and affective customer commitment - The mediating role of trust', Journal of Financial Services Marketing 21(2), 127-140. https://doi.org/10.1057/fsm.2016.5 [ Links ]
Bove, L.L., Pervan, S.J., Beatty, S.E. & Shiu, E., 2009, 'Service worker role in encouraging customer organizational citizenship behaviors', Journal of Business Research 62(7), 698-705. https://doi.org/10.1016/j.jbusres.2008.07.003 [ Links ]
Chahal, H. & Dutta, K., 2015, 'Measurement and impact of customer experience in banking sector', Decision 42(1), 57-70. https://doi.org/10.1007/s40622-014-0069-6 [ Links ]
Chen, A., Lu, Y., Wang, B., Zhao, L. & Li, M., 2013, 'What drives content creation behavior on SNSs? A commitment perspective', Journal of Business Research 66(1), 2529-2535. https://doi.org/10.1016/j.jbusres.2013.05.045 [ Links ]
Chen, D., Sain, S.L. & Guo, K., 2012, 'Data mining for the online retail industry: A case study of RFM model-based customer segmentation using data mining', Journal of Database Marketing & Customer Strategy Management 19(3), 197-208. https://doi.org/10.1057/dbm.2012.17 [ Links ]
Chen, Y., Boh, W.F. & Mo, J., 2018, 'Heterogeneous interactions in online communities: Social and economic impact for online sellers', in M. Tanabu & D. Senoo (eds.), 22nd Pacific Asia Conference on Information Systems (PACIS), Yokohama, Japan, June 26-30, 2018, p. 326.
Cheung, C.M.K. & Lee, M.K.O., 2009, 'Understanding the sustainability of a virtual community: Model development and empirical test', Journal of Information Science 35(3), 279-298. https://doi.org/10.1177/0165551508099088 [ Links ]
Chiang, I.P., Lin, Y. & Huang, C.H., 2018, 'Measuring the effects of online-to-offline marketing', Contemporary Management Research 14(3), 167-189. https://doi.org/10.7903/cmr.18462 [ Links ]
Chiu, C.M., Cheng, H.L., Huang, H.Y. & Chen, C.F., 2013, 'Exploring individuals' subjective well-being and loyalty towards social network sites from the perspective of network externalities: The Facebook case', International Journal of Information Management 33(3), 539-552. https://doi.org/10.1016/j.ijinfomgt.2013.01.007 [ Links ]
Chiu, H.C., Hsieh, Y.C., Roan, J., Tseng, K.J. & Hsieh, J.K., 2011, 'The challenge for multichannel services: Cross-channel free-riding behavior', Electronic Commerce Research and Applications 10(2), 268-277. https://doi.org/10.1016/j.elerap.2010.07.002 [ Links ]
Chiu, T.S., Ortiz, J., Chih, W.H., Pang, L.C. & Huang, J.J., 2019, 'Antecedents of consumers' citizenship behaviour towards organic foods', Journal of Consumer Behaviour 18(4), 332-349. https://doi.org/10.1002/cb.1774 [ Links ]
Chou, S.W. & Hsu, C.S., 2016, 'Understanding online repurchase intention: Social exchange theory and shopping habit', Information Systems and e-Business Management 14(1), 19-45. https://doi.org/10.1007/s10257-015-0272-9 [ Links ]
Chu, K-M., 2009, 'A study of members' helping behaviours in online community', Internet Research 19(3), 279-292. https://doi.org/10.1108/10662240910965351 [ Links ]
Curth, S., Uhrich, S. & Benkenstein, M., 2014, 'How commitment to fellow customers affects the customer-firm relationship and customer citizenship behavior', Journal of Services Marketing 28(2), 147-158. https://doi.org/10.1108/JSM-08-2012-0145 [ Links ]
De Valck, K., Van Bruggen, G.H. & Wierenga, B., 2009, 'Virtual communities: A marketing perspective', Decision Support Systems 47(3), 185-203. https://doi.org/10.1016/j.dss.2009.02.008 [ Links ]
Fatima, J.K., Razzaque, M.A. & Di Mascio, R., 2016, 'Modelling satisfaction-commitment relationship in developing country context', International Journal of Quality and Reliability Management 33(7), 985-1001. https://doi.org/10.1108/IJQRM-01-2014-0013 [ Links ]
Fornell, C. & Larcker, D.F., 1981, 'Evaluating structural equations models with unobservable variables and measurement error', Journal of Marketing Research 18(1), 39-50. https://doi.org/10.1177/002224378101800104 [ Links ]
Frasquet-Deltoro, M., Alarcón-del-Amo, M.D.C. & Lorenzo-Romero, C., 2019, 'Antecedents and consequences of virtual customer co-creation behaviours', Internet Research 29(1), 218-244. https://doi.org/10.1108/IntR-06-2017-0243 [ Links ]
Fullerton, G., 2011, 'Creating advocates: The roles of satisfaction, trust and commitment', Journal of Retailing and Consumer Science 18(1), 92-100. https://doi.org/10.1016/j.jretconser.2010.10.003 [ Links ]
Fullerton, G., 2014, 'The moderating effect of normative commitment on the service quality-customer retention relationship', European Journal of Marketing 48(3/4), 657-673. https://doi.org/10.1108/EJM-06-2011-0333 [ Links ]
Godwin, B.J. & Wright, R., 2019, 'Understanding the antecedents of service decisions: an integration of service promiscuity and customer citizenship behaviour', International Journal of Services, Economics and Management 10(1), 34-54. https://doi.org/10.1504/IJSEM.2019.098927 [ Links ]
Gruen, T., Summers, J. & Acito, F., 2000, 'Relationship marketing activities: Commitment, and membership behaviours in professional associations', Journal of Marketing 64(1), 34-49. https://doi.org/10.1509/jmkg.64.3.34.18030 [ Links ]
Gummerus, J., Von Koskull, C. & Kowalkowski, C., 2017, 'Guest editorial - Relationship marketing: Past, present and future', Journal of Services Marketing 31(1), 1-5. https://doi.org/10.1108/JSM-12-2016-0424 [ Links ]
Hair, J.F., Black, W.C., Babin, B.J. & Anderson, R.E., 2014, Multivariate data analysis, Pearson, Essex.
Hashim, K.F. & Tan, F.B., 2015, 'The mediating role of trust and commitment on members' continuous knowledge sharing intention: A commitment-trust theory perspective', International Journal of Information Management 35(2), 145-151. https://doi.org/10.1016/j.ijinfomgt.2014.11.001 [ Links ]
Hau, L.N. & Thuy, P.N., 2016, 'Customer participation to co-create value in human transformative services: A study of higher education and health care services', Service Business 10(3), 603-628. https://doi.org/10.1007/s11628-015-0285-y [ Links ]
Jin, B., Park, J.Y. & Kim, H-S., 2010, 'What makes online community members commit? A social exchange perspective', Behaviour & Information Technology 29(6), 587-599. https://doi.org/10.1080/0144929X.2010.497563 [ Links ]
Kaur, H. & Kochar, R., 2018, 'A review of factors affecting consumer behavior towards online shopping', International Journal of Engineering and Management Research (IJEMR) 8(4), 54-58. https://doi.org/10.31033/ijemr.8.4.6 [ Links ]
Khan, A.G., 2016, 'Electronic commerce: A study on benefits and challenges in an emerging economy', Global Journal of Management and Business Research 16(1). https://journalofbusiness.org/index.php/GJMBR/article/view/1918 [ Links ]
Kim, J.W., Choi, J., Qualls, W. & Han, K., 2008, 'It takes a marketplace community to raise brand commitment: The role of online communities', Journal of Marketing Management 24(3/4), 409-431. https://doi.org/10.1362/026725708X306167 [ Links ]
Kraut, R.E. & Resnick, P., 2011, Building successful online communities: Evidence based social design, MIT Press, Cambridge.
Lal, P., 2017, 'Analyzing determinants influencing an individual's intention to use social commerce website', Future Business Journal 3(1), 70-85. https://doi.org/10.1016/j.fbj.2017.02.001 [ Links ]
Liao, C., Lin, H.N., Luo, M.M. & Chea, S., 2017, 'Factors influencing online shoppers' repurchase intentions: The roles of satisfaction and regret', Information & Management 54(5), 651-668. https://doi.org/10.1016/j.im.2016.12.005 [ Links ]
Lin, Y., 2015, 'Innovative brand experience's influence on brand equity and brand satisfaction', Journal of Business Research 68(11), 2254-2259. https://doi.org/10.1016/j.jbusres.2015.06.007 [ Links ]
Lin, Y.L., Liu, H.W. & Ngo, P.T., 2016, 'Silence is not golden: The effects of prohibitive voice on customer citizenship behaviors', International Business Research 9(9), 24-33. https://doi.org/10.5539/ibr.v9n9p24 [ Links ]
Ling, L., Guo, X. & Yang, C., 2014, 'Opening the online marketplace: An examination of hotel pricing and travel agency on-line distribution of rooms', Tourism Management 45(1), 234-243. https://doi.org/10.1016/j.tourman.2014.05.003 [ Links ]
Malinen, S., 2015, 'Understanding user participation in online communities: A systematic literature review of empirical studies', Computers in Human Behaviour 46(1), 228-238. https://doi.org/10.1016/j.chb.2015.01.004 [ Links ]
Meyer, J.P. & Allen, N.J., 1991, 'A three-component conceptualization of organizational commitment', Human Resource Management Review 1(1), 61-89. https://doi.org/10.1016/1053-4822(91)90011-Z [ Links ]
Mpinganjira, M., 2016, 'Antecedents of citizenship behaviour in online customer communities: An empirical investigation: Original research', South African Journal of Information Management 18(2), 1-9. https://doi.org/10.4102/sajim.v18i2.725 [ Links ]
Muhammad, Z., Yi, F., Naz, A.S. & Muhammad, K., 2014, 'An empirical study on exploring relationship among information quality, e-satisfaction, e-trust and young generation's commitment to Chinese online retailing', Journal of Competitiveness 6(4), 3-18. https://doi.org/10.7441/joc.2014.04.01 [ Links ]
Okonkwo, U., 2010, Luxury online: Styles, systems, strategies, Palgrave Macmillan, Hampshire.
Oliver, R.L., 1980, 'A cognitive model of the antecedents and consequences of satisfaction decisions', Journal of Marketing Research 17(4), 460-494. https://doi.org/10.1177/002224378001700405 [ Links ]
Pallant, J., 2013, SPSS: Survival manual, McGraw-Hill, Berkshire, CA.
Payne, A. & Frow, P., 2017, 'Relationship marketing: Looking backwards towards the future', Journal of Services Marketing 31(1), 11-15. https://doi.org/10.1108/JSM-11-2016-0380 [ Links ]
Ponnusamy, G., 2015, 'Customers as volunteers? E-customer citizenship behavior and its antecedents', Information Management and Business Review 7(3), 50-58. https://doi.org/10.22610/imbr.v7i3.1153 [ Links ]
Preece, J., 2000, Online communities: Designing usability and supporting sociability, Wiley, New York, NY.
Saunders, M., Lewis, P. & Thornhill, A., 2016, Research methods for business students, Pearson, Essex.
Shen, X-L., Cheung, C.M.K., Lee, M.K.O. & Chen, H., 2011, 'How social influence affects we-intention to use instant messaging: The moderating effect of usage experience', Information Systems Frontier 13(1), 157-169. https://doi.org/10.1007/s10796-009-9193-9 [ Links ]
Shukla, P., Banerjee, M. & Singh, J., 2016, 'Customer commitment to luxury brands: Antecedents and consequences', Journal of Business Research 69(1), 323-331. https://doi.org/10.1016/j.jbusres.2015.08.004 [ Links ]
Siti, O.N., Mohammed, A-J.A. & Nik Kamariah, N.M., 2012, 'Actual online shopping behavior among Jordanian customers', American Journal of Economics June(Special Issue), 125-129. https://doi.org/10.5923/j.economics.20120001.28 [ Links ]
Spik, A., 2016, 'Enthusiasts or trapped? Relations between organizational commitment profiles, organizational citizenship behavior and life satisfaction', Journal of Entrepreneurship, Management and Innovation 12(1), 7-34. https://doi.org/10.7341/20161211 [ Links ]
Steinhoff, L., Arli, D., Weaven, S. & Kozlenkova, I.V., 2019, 'Online relationship marketing', Journal of the Academy of Marketing Science 47(3), 369-393. https://doi.org/10.1007/s11747-018-0621-6 [ Links ]
Stokburger-Sauer, N.E. & Wiertz, C., 2015, 'Online consumption communities: An introduction', Psychology & Marketing 32(3), 235-239. https://doi.org/10.1002/mar.20776 [ Links ]
Tanskanen, K., 2015, 'Who wins in a complex buyer-supplier relationship? A social exchange theory based dyadic study', International Journal of Operations & Production Management 35(4), 577-603. https://doi.org/10.1108/IJOPM-10-2012-0432 [ Links ]
Van Tonder, E., Saunders, S.G., Lisita, I.T. & De Beer, L.T., 2018, 'The importance of customer citizenship behaviour in the modern retail environment: Introducing and testing a social exchange model', Journal of Retailing and Consumer Services 45(1), 92-102. https://doi.org/10.1016/j.jretconser.2018.08.011 [ Links ]
Watkins, G., 2019, National and regional economically active population - QLFS Q4 2018, viewed 16 April 2019, from www.workinfo.org/index.php/articles/item/2021-national-and-regional-economically-active-population-qlfs-q4-2018.
World Wide Works, 2018, Online retail reaches 1.4% of SA's total retail, viewed 28 March 2019, from www.worldwideworx.com/onlineretail2019/.
Yi, Y. & Gong, T., 2013, 'Customer value co-creation behavior: Scale development and validation', Journal of Business Research 66(9), 1279-1284. https://doi.org/10.1016/j.jbusres.2012.02.026 [ Links ]
Yi, Y., Gong, T. & Lee, H., 2013, 'The impact of other customers on customer citizenship behaviour', Psychology and Marketing 30(4), 341-356. https://doi.org/10.1002/mar.20610 [ Links ]
Yong, L., Sachau, D. & Lassiter, A., 2011, 'Developing a measure of virtual community citizenship behaviour', Knowledge Management & E-learning: An International Journal 3(4), 682-696. https://doi.org/10.34105/j.kmel.2011.03.044 [ Links ]
Yu-hong, Z., Da-hai, D. & Sheng-nan, L., 2013, 'Antecedents and the outcome of customer citizenship behavior in consumption virtual communities: A theoretical model', in P. Li (ed.), International Conference on education technology and management sciences, Nanjing, Jiangsu, China, June 8-9, 2013, pp. 614-617.
Zhou, T., 2011, 'Understanding online community user participation: A social influence perspective', Internet Research 21(1), 67-81. https://doi.org/10.1108/10662241111104884 [ Links ]
Zhou, Z., Fang, Y., Vogel, D.R., Jin, X.L. & Zhang, X., 2012, 'Attracted to or locked in? Predicting continuance intention in social virtual world services', Journal of Management Information Systems 29(1), 273-306. https://doi.org/10.2753/MIS0742-1222290108 [ Links ]
Zhu, D.H., Sun, H. & Chang, Y.P., 2016, 'Effect of social support on customer satisfaction and citizenship behavior in online brand communities: The moderating role of support source', Journal of Retailing and Consumer Services 31(1), 287-293. https://doi.org/10.1016/j.jretconser.2016.04.013 [ Links ]
 Correspondence:
Correspondence:
Mia Bothma
mia.bothma@nwu.ac.za
Received: 22 Jan. 2020
Accepted: 03 Aug. 2020
Published: 28 Oct. 2020
ORIGINAL RESEARCH
Using historical data to explore transactional data quality of an African power generation company
Patient Rambe; Johan Bester
Department of Business Support Studies, Faculty of Management Sciences, Central University of Technology, Bloemfontein, South Africa
ABSTRACT
BACKGROUND: In developing countries, despite large public companies' reliance on master data for decision-making, there is scant evidence to demonstrate their effective use of transactional data in decision-making because of its volatility and complexity. For the state-owned enterprise (SOE) studied, the complexity of generating high-quality transactional data manifests in relationships between customer call transactional data related to an electricity supply problem (captured by call centre agents, i.e. data creators) and technician-generated feedback (i.e. data consumers.
OBJECTIVES: To establish the quality of customer calls transactional data captured using source system measurements. To compare this data set with field technicians' downstream system transactions that indicated incorrect transactional data.
METHOD: The study compared historical customer calls transactional data (i.e. source system data) with field technician-generated feedback captured on work orders (i.e. receiving system) in a power generation SOE, to ascertain transactional data quality generated and whether field technicians responded to authentic customer calls exclusively to mitigate operational expenses.
RESULTS: Mean values of customer call transactional data quality from the source system and technician-generated feedback on work orders varied by 1.26%, indicating that data quality measurements at the source system closely resembled data quality experiences of data consumers. The SOE's transactional data quality from the source system was 80.05% and that of historical data set from evaluating feedback was 81.31% - percentages that exceeded average data quality measurements in literature.
CONCLUSION: Using a feedback control system (FCS) to integrate feedback generated by data consumers to data creators presents an opportunity to increase data quality to higher levels than its current norm.
Keywords: feedback control system; power generation; master data; transactional data quality; electricity supply problem; data management capabilities.
Introduction
Master data, which capture core information about an organisation's stakeholders, products and relationships amongst them (Haneem, Kama & Kazmi 2016), have been the staple discourse for explaining organisational operations (Infovest 2018). The concentration on master data has been accentuated by the recognition of big data as a strategic asset for organisations (Hagerty 2016) and increased business and data management capabilities in the digital economy (Bärenfänger, Otto & Gizanis 2015). These capabilities manifest in advanced analytics tools' capacity to generate insightful business information and enhance the provision of digital services to customers (Organisation for Economic Co-operation and Development [OECD] 2016). Such capabilities are also evident in digital technologies that avail and pool masses of data from multiple modes to one central place or distributed locations for in-depth analysis. Whilst these capabilities can increase data types that can be analysed by organisations, master data remain the preferred data sources because of the panoramic picture it renders on business operations (Entity Group 2016). The oversight on less strategic data forms, such as metadata and transactional data quality, is concerning (Palavitsinis 2013) because data quality is a strategic resource in prudent decision-making, especially in public institutions where scarce resources must be strategically harnessed to ensure the long-term sustainability of programmes (Alketbi 2014).
The limited application of transactional data in explaining business operations is attributed to its volume, volatility (Bester 2019) and complex connections with daily operations of organisations. The American Council for Technology-Industry Advisory Council (ACT-IAC) (2015) observes that the high volume of transactional data that government agencies deal with daily, complex business processes, complex policy requirements and ancient technology systems complicate the management of transactional data quality. The American Council for Technology-Industry Advisory Council (2015) elaborates that even within the same agency, different divisions apply the same data differently and how these data elements are defined within the same agency varies widely.
Literature on transactional data and its applications in large organisations has gained momentum even though such data should be used cautiously because of their complexities (Hand 2018). The increasing prominence of transactional data quality in explaining organisational operations arises from increasing programme funding accountability and effective monitoring of public programmes (Rothbad 2015), the need to render responsible customer experiences and the growing competitive intensity of knowledge-intensive industries (Biegel et al. 2018). Other considerations include the demand for data analytics to steer contemporary business operations and the need for comprehensive business insights (Hagerty 2016), the surging costs of surveys and transactional data's potential to generate insightful discoveries (Hand 2018).
The need for high transactional data quality has been accentuated by large secondary data sets used in secondary analysis (Hand 2018), and organisations' desire for richer understanding of customers to provide relevant, meaningful and efficient interactions (Biegel et al. 2018). Despite these developments, management executives are concerned about the paucity of sufficient, correct, reliable and timely data upon which to ensure sound organisational decisions and bemoan the depletion of quality information (Bester 2019).
One grey area regarding transactional data quality is whether and the extent to which data sets generated at the organisational sources (e.g. by call agents) are consistent with other data sources (e.g. feedback generated by field technicians who deal with customer queries on data quality). Addressing this issue contributes to improving data quality at multiple organisational levels by integrating various information from diverse sources (Rothbad 2015). Quality assurance (QA) processes should commence at the initial data entry stages and progress through the entire process of integrating data from multiple sources to build an integrated data system (Rothbad 2015). The failure to corroborate transactional data quality from multiple agent sources can lead to incongruence of data quality, imprudent decision-making within large publicly owned companies (Rambe & Bester 2016) and catastrophic social consequences such as massive power failures (Fürber 2015).
Providing in-built complementarities and coherence within and across transactional data from multiple agencies ensures appropriate evaluation of public programmes (Rothbad 2015). To establish the quality of transactional data, we examined the coherence of data generated by an African power generation and distribution company (APGDCO1) from two fronts: data generated from customer calls received at the call centre (customer calls transactional data) and technician feedback on customer transactions they executed. The study addressed the following questions:
-
What is the quality of transactional data captured from customer calls at APGDCO based on source system measurement?
-
How many downstream system transactions have feedback of field technicians that indicates incorrect transactional data?
Problem background
The African power generation and distribution company has many customers such as households, corporations, mines and city councils. Larger customers often have complex monitoring systems for measuring quality of electricity received and can alert APGDCO immediately when an interruption in electricity supply occurs. Small customers cannot afford monitoring systems and report electricity supply problem (ESP) cases to APGDCO's call centre whenever they experience electricity outages. Subsequently, call centre agents probe customer queries using call scripts or case-based reasoning to categorise an issue correctly. If agents conceive APGDCO's network as the source of the problem, an ESP case is logged and a field technician is dispatched to restore electricity supply.
Therefore, correct interpretation and classification of customer problems are paramount to utilising APGDCO's resources appropriately. Sometimes, call centre agents may misinterpret a customer's explanation of an issue or are misled by customers. Consequently, a fault caused by a customer's defective equipment can be logged as an ESP case, something that APGDCO should not respond to as it is the customer's responsibility to resolve. For each transaction ESP case logged, a work order is automatically generated in the receiving system and technicians mark on the work order the cause of the ESP and the action performed to restore supply. If the issue was caused by customer's faulty equipment, the technicians will mark the customer side fault, which signifies that call agents captured incorrect transaction data at the source. As a data consumer, the technician is the primary authority on data quality as transaction data quality measured by the contact centre agents may not present a true reflection of the data consumer's experience.
Theoretical framework
Systems theory considers a system as a set of inter-related and interdependent parts (Mele, Pels & Polese 2010). Cybernetics, generally used as a synonym for systems theory, is concerned with the communication and regulation of systems using a feedback control system (FCS) (Skyttner 2001). An FCS is configured to control itself, another system and feedback loops which are the mechanisms for exercising such control by facilitating desired outcomes. The simplest feedback loop is an open-loop system where input influences output via a control system (see Figure 1). Although such open-loop systems are cheap, simple to design and easy to maintain, their configuration is often inaccurate as no feedback is redirected into the system. Consequently, open-loop system can neither act on the output or external environment nor use it to influence subsequent outputs (ed. Liptak 2018).

A closed-loop system is a better configuration for a system to act on its external environment to regulate itself (see Figure 2). Whilst the system replicates an open-loop system, it has an appendage relaying feedback back to the input. Feedback can be used to adjust subsequent input or facilitate a desired output. A closed-loop system supports higher accuracy as it responds quickly to external and internal changes. However, this system is complex and expensive to create, maintain and often overcorrect itself if not designed carefully (ed. Liptak 2018).

Orr (1998) applied cybernetics to data quality by suggesting that an information system's data quality will be 100% if it represented data exactly as it existed in the real world and 0% if no conformity existed. Data quality changes over time and will not stay at a 100% level ad infinitum. Orr (1998) warns that the absence of an FCS will prevent continuous alignment between data in a system and the real world because feedback is the only valid mechanism that ensures the tracking of changes in the real world to related information systems. Even though Orr's (1998) application of cybernetics focussed on correcting existing master data records, an FCS can also improve the quality of transaction data.
Literature review
Data types
Data are defined as input of unprocessed items such as facts, figures, text, images, numbers, video and audio typically stored in a digital format (Epstein 2012; Nazim & Mukherjee 2016; Vermaat 2014). Consumer and brand-related data tend to be categorised into various types, namely, digital, terrestrial, transactional, emergent/speciality and identity data (Biegel et al. 2018). Other classifications include unstructured data such as e-mails, files and videos, and structured data that comprise master, reference, transactional, metadata, history and queue data (Arun & Jabasheela 2014). Master data refer to vital business information about products, suppliers and customers that has a low change frequency. Reference data describe a business entity such as a customer, product or supplier and do not change frequently. Historical data are data that relate to previous transactions, which include master, reference and transactional data and are retained for compliance purposes (Borek et al. 2014). Transactional data are captured during an interaction and are combined with master and/or reference data to form a transaction at a specific time and have high volume and changes frequently (Borek et al. 2014). Overall, master data are often accorded the highest priority in organisational settings as these capture diverse organisational information such as customers, suppliers, products and their inter-relationships and are shareable across multiple business units of public entities (Nelke et al. 2015).
However, the extraction of quality data is often laborious and dissociated with public service quality, such as patient care in emerging contexts (Marais 2017). The high volume and velocity of various data forms imply that new tools and methodologies are required to capture, manage and process them efficiently (Statistics Divisions of United Nations, Department of Economic and Social Affairs [UN/DESA] and UN Economic Commission for Europe 2015). Therefore, huge investments in human expertise, technology and infrastructure are necessary for organisations to leverage fully the benefits of such data. More so, the silo-based approach to the capturing, curation and management of master data in government organisations also increases the duplication of master data across departments, thereby accentuating government costs and wasting resources (Haneem et al. 2016).
Data quality
Wang and Strong (1996) define data quality as data that are fit for use from the consumer's perspective. Although data quality has traditionally been considered from an accuracy perspective (Lin, Gao, Koronios & Chanana 2007), completeness, timeliness and consistency have become over-riding dimensions of data quality in recent times (ACT-IAC 2015). Completeness describes the extent to which data captured all dimensions that they were created to capture. According to Cai and Zhu (2015), completeness denotes that the values of all components of a single datum are valid. They elaborate that completeness is measured by establishing whether the deficiency of a component will impact the use of the data, especially for data with multi-components and whether the deficiency of a component will impact data accuracy and integrity (Cai & Zhu 2015).
Validity implies that data must be generated from reliable sources. Grillo (2018) concurs that the validity of data deals with the trustworthiness of the data, which increases user engagement, sustains the functioning of a data warehouse and is a critical dimension in the development of a data quality scorecard (DQS) that measures the quality of data in the data warehouse. Consistency means that the same process or source must generate the same data and the same data values describing an object or event should be reflected across the entire organisation (ACT-IAC 2015). For databases, this means that the same data that are located in different storage areas should be considered to be equivalent or possessing equal value (Silberschatz, Korth & Sudarshan 2006). Consistency, therefore, points to whether the logical relationship between correlated data is correct and complete (Cai & Zhu 2015).
Timeliness denotes that data must be adequately current. It is the time delay from data generation and acquisition to its utilisation (McGilvray 2010) to allow for meaningful analysis. It points to the temporal difference between the time at which the data were collected and when they become available for analysis (Brackstone 1999; Keller et al. 2017). Accuracy implies that the appropriate values should be captured at the first time of data entry and should be retained throughout the enterprise (ACT-IAC 2015). Therefore, accuracy measures the degree to which data represent the phenomena they were designed to measure (Brackstone 1999) and whether their numerical value is within a specified threshold (Marev, Compatangelo & Vasconcelos 2018).
However, an improvement of one dimension of data quality may compromise another dimension. For instance, data can be provided timely but at the expense of its completeness. Moreover, whilst the use of data repositories may increase timeliness of access of data to scientists originally not involved in the initial data collection and experiments, access may be restricted if it violates information security and privacy, or accessibility of data may be restricted across organisations because of competitiveness across organisations (Milham 2012). Data completeness may be realised at the expense of their concise representation (Neely & Pardo 2002) and different data consumers may have varying evaluations of the same data quality (Lin et al. 2007). Moreover, the high data expenditures and their exponential growth in relation to media channels they are associated with (Biegel et al. 2018) imply that different organisational departments may undervalue certain data quality dimensions, such as comparability, thereby compromising data quality.
Transactional data quality
Oracle Corporation (2011) observes that transactional data quality captures automated business processes such as sales, service, order management, manufacturing and purchasing. Point-of-sale transactions involve data aspects such as product, place, time, price and name of sale agent and contribute directly to the complexity and volatility of transactional data (Baran & Galka 2016). Research highlights that South African customer data quality is problematic and hampers the quality of decision-making in firms (Burrows 2014). Neil Thorns, Informatica's territory manager for sub-Saharan Africa, contends that most South African companies have low transactional data quality with an average accuracy of 50% or less. This is lower than the 73% global mark advocated by Experian's (2017) latest survey on customer data. The poor data quality is attributed to few business rules and limited automation during data capturing because of limited high-technology adoption and resource constraints (Burrows 2014). The difficulty of upgrading multiple systems and departmental support systems through which data flow also contributes to low transactional data quality. One conundrum is that whilst the support systems through which data are captured are constantly changing, they may be run on antiquated programming languages, thereby making their interfacing with new programmes problematic, culminating in inaccurate transactional data (ACT-IAC 2015).
World Economics' Data Quality Index on the gross domestic product (GDP) of 154 countries employed five indicators - base year, system of national accounts, informal economy, quality of statistics and corruption - and ranked South Africa 49th, with an overall score of 77.1% (World Economics 2017). This ranking is higher than the 73% global mark set by Experian's (2017) survey on data quality. These contradictory statistics on South Africa's data quality raise perplexing questions about the quality of transactional data, thereby amplifying the need to conduct research on data quality.
Methodology
Research design
Because this research corroborated the perspectives of APGDCO's field technicians who resolved customer ESP queries with source data generated by APGDCO's call centre agents, a combination of a quantitative cross-sectional survey and historical transactional data was considered as the appropriate research design. Cross-sectional surveys serve to establish the prevalence of a phenomenon, attitudes and opinions from individuals to portray an overall picture at the time of conducting the study (Kumar 2014). To ascertain the quality of data, the study needed to compare the technicians' view with customer centre's data quality measurements. As such, the study employed historical data (i.e. work orders from the receiving system that were marked with customer-side fault) as the technicians' view and compared it with the contact centre's data quality measurements captured in the source system. The original data captured by call centre agents (i.e. historical transactional data) relating to client ESP data included call numbers, client locations and nature of ESP type. The historical data sets on transactional data employed in the study covered April 2012 to March 2017, a period that is conceived enough to detect trends in ESPs in the region the study covered.
Instrumentation
The structured questionnaire had two sections, namely, the demographic data section covering technicians' years of experience, the experience of using enterprise digital assistant (EDA) and transactional data quality section (customer-side fault). Historical transactional data encapsulated the followings: volume of work order distribution across various service centres, source system transactional data quality versus feedback on transactional data per financial year.
Data collection
The second author (J.B.) conducted a census on the 303 technicians who resolved customer queries in APGDCO over 2 months in 2017. The self-administered questionnaire comprised ordinal and ratio scales. Respondents completed (1) a hard copy questionnaire, scanned and emailed it to the second author, (2) an electronic version that they word processed and emailed or (3) a computer- or smartphone-based web browser version of the questionnaire. Despite numerous follow-ups made with APGDCO technicians, the census generated a 35% response rate (106 out of 303), mostly from the scanned copy sent via email. These data were coded and captured on an Excel spreadsheet and exported to Statistical Packages for the Social Sciences (SPSS) for a detailed data analysis.
Data preparation
The historical transactional data were extracted using Structured Query Language (SQL) from the company's ESP application database containing work order records. The normalisation and enrichment of the data involved checking of record descriptions for the wording 'customer fault' and any variations that indicated a customer fault. An interpretation of transaction dates allowed for the addition of fields and categorisation of data according to APGDCO's financial years. A precompiled report that indicated the mean of the transactional call and quality per month was referenced to indicate transactional data quality at the source system per secondary data record. All records were exported to an Excel spreadsheet for secondary data preparation and initial analysis before its exportation to SPSS for detailed analysis.
Data analysis
The study employed descriptive statistics to organise and summarise data based on sample demographics (Holcomb 2016). Frequency distributions, means and percentage analysis were used for the presentation and analysis of descriptive statistics. This study's frequency distribution covered work order amounts and data quality measured at source system and via feedback. Means were generated for the quality of source system data and feedback from technicians. Inferential statistics were instrumental in drawing conclusions about the population by determining the relationship amongst variables and making predictions about the population (McKenzie 2014). Correlation and regression analysis were used to determine the associative and predictive relations of variables examined.
Validity and reliability
Nieuwenhuis (2014) argues that validity requires the researcher to document procedures for evaluating the trustworthiness of the data collection and analysis. The statistician and researchers examined the conciseness and precision of questions to ensure face validity. The technicians' manager also appraised the questionnaire to ensure that the breadth of questions covered data quality issues (i.e. content validity). The researchers also verified raw data through availing questionnaires and field notes to respondents to correct factual errors (Nieuwenhuis 2014). For transactional data at the source, all compiled data sets were exchanged with data custodians (data analyst and manager of call centre agents) to authenticate data sources and ensure the credibility of results.
The researchers and the statistician shared all data sets to ensure consistency in the coding process, and where opinions varied, they met to clarify consistencies and generate consensus. This ensured intra- and inter-coder reliability. The instrument had an internal consistency of 0.638 even though two items had low consistency (see Table 1). The small number of items on transactional data quality perhaps explain the low internal consistency of construct on this instrument.

Presentation of findings
The results on years of experience at an APGDCO Customer Service Centre (CSC) in Figure 3 show that 40.566% of the technicians had 6-10 years, 27.358% had 0-5 years, 21.698% had more than 20 years, 8.491% had 11-15 years and only 1.887% had 15-20 years of experience. It is important to understand that all values were rounded to three decimals so that they add up to 100.000%. Although rounding them to one decimal seemed appropriate mathematically, it was not considered as the values would be too close to but not add up to 100%. Most of the technicians had more than 5 years of work experience and, therefore, had enough work exposure to fulfil their responsibilities.
The African power generation and distribution company adopted EDA devices in the 2011-2012 financial year. Thus, the maximum possible experience a technician had on EDA usage was around 5 years. The distribution analysis of EDA usage, depicted in Figure 4, reveals that only 8.491% of the technicians had EDA usage experience of 1 year or less, whilst 53.774% had more than 4 years of experience. It is important to note that even when expanded to three decimals, exact summation to 100.0000 occurs at fourth decimal only. Therefore, the EDA usage experience was enough for technicians' effective utilisation of these devices judging from the distribution analysis.

Figure 5 indicates that most technicians received less than 20 single customer dispatch work orders per month, 46.226% had 1-10 and 31.132% had 11-20 work orders. Therefore, 77.358% of technicians received an average of one customer dispatch work order per working day per month. Therefore, technicians were not overburdened with dispatch work orders and could properly evaluate work and provide feedback on the executed work.

Source system and feedback data quality
The descriptive summary in Table 2 shows a hierarchical breakdown of APGDCO's historical data. The three-level hierarchy system has at its lowest level the service centres where technicians are located, who are responsible to restore ESP cases. Service centres are grouped one level up under sectors, which are again grouped under zones as the highest level. It contains columns for the amount of ESP work orders received, the overall percentage of work orders, work order percentage received during work time and overtime, source system data quality as measured by the call centre agents (data creators) at the source system and data quality based on feedback from technicians (data consumers) on work orders.
Source system data quality is measured via a QA process that evaluates 1% of historical call centre system transactional data and expresses it as a quality percentage. Data quality based on technician feedback is determined by dividing the total number of historical work orders at the receiving system by the amount of work orders marked as valid ESP transactions and displaying it as a percentage.
Table 2 reveals that data quality for all hierarchy levels, which data creators measured at the source system, had a very narrow distribution. It consisted of a mean of 80%, a maximum deviation from the mean of 0.2% and a minimum deviation of 0%. Measurement of data quality via technician feedback at the receiving system indicated a mean of 81.3%, with the biggest deviation of 14% at Service Centre 2.B.5 and the closest deviation of 0.1% observed at Service Centre 2.B.6. The measurements were very similar, implying that measurement by data creators confirmed the data quality experience measured from data consumers' feedback. The higher deviation from the mean found within feedback measurements could be attributed to high granularity in the data analysed (i.e. per transaction) compared to the much lower granularity (i.e. monthly) of data creators' measurements.
Comparison of transactional data quality: Source system with feedback
Data quality measured at the source system by the data creators was based on results from a QA process performed on a 1% sample of the total historical ESP transactions for a month. This QA process consumes much time and only 1% of the total transactions could be assessed. The QA process evaluates the extent of call professionalism when data capturers are answering calls, for instance, whether correct steps were followed to identify a customer, interpret his or her fault symptoms, send the fault to the correct department and if the call was concluded professionally. Most scoring relates to transactional data quality and hence this score is used as a proxy for transactional data quality at the source system. Data quality measured at the receiving system via technician feedback was calculated by dividing the total number of historical work orders automatically generated from ESP cases logged by the amount of work orders marked as a valid ESP case.
A comparison of historical transactional data quality measured by data creators at the source system and historical data quality measured by evaluating feedback from technicians on work orders at the receiving system reveals whether feedback is impacted by source system data quality or not. Transactional feedback from field technicians indicates the correctness of work order/transactional data quality if it describes a valid resolution of an ESP.
Descriptive analysis is presented in Table 3 where each financial year's source system transactional data quality and feedback on correct transactions are compared to the average for all years combined. A value higher than the average is denoted with a double dagger, whilst a value lower than the average is marked with a single dagger. The indicated daggers for source system data quality and feedback indicating correct transactions correspond in the financial years 2014-2015, 2015-2016 and 2016-2017.

Figure 6 displays data quality from both source system and transactions, with feedback indicating correct data. Transactional data quality from the source system indicates an upward trend, despite the slump during the 2014-2015 financial year. Data quality based on transactional feedback from the data consumer perspective also displays a general upward trend even though it has more declines than source system data quality. Therefore, on a year-by-year basis, the perspectives on data quality by the data creator and data consumer did not always cohere. Therefore, data creators can focus on improving data quality measurements to ensure its closer reflection of the data consumer's perspective, but this must be considered carefully as the small sample size of the transactions measured by data creators might explain this difference in results.

Correlation analysis between source system data quality (independent variable) and data from transactional feedback (response variable) in Table 4 reveals a weak positive statistically significant (0.01; p = 0.00002) relationship between the two variables. The weak correlation could be influenced by the extensive granularity of data quality measured via technician feedback (e.g. measured per individual work order) versus low granularity of data quality measured at the source system that only analyses 1% sample of transactions via the QA process.

The study also sought to establish whether data quality measured at source has an impact on data quality measured via feedback (i.e. whether the nature of data quality at the source predicted the data quality generated by field technicians).
Logistic regression was used to assess inferentially the relationship between transactional data quality from the data creator (i.e. contact centre) and transactional feedback from the data consumer (i.e. field technician). This tool is preferred as the independent variable, source system data quality is a ratio-scale variable measured in percentages and the response variable, transactional feedback, is a binary value where 1 = correct and 0 = incorrect. The results in Table 5 illustrate that transactional feedback is significantly dependent on source system data quality (Wald statistic = 18.209, df = 1, p = 0.000).

Discussion
A comparison of percentages of transactional data quality at the source system and feedback on correct transactions gave interesting results. Most of the percentages on feedback on correct transactions were higher than those of source system transactional data quality, creating an impression that data from execution of work orders provided a more accurate picture of transactional data quality than data captured at the source. Nevertheless, the differences between these percentages were marginal and were closer to the averages for the years considered. These differences demonstrate the absence of a clear feedback loop from technicians' feedback on transactions to source system data quality, which can compromise the quality of data at the source. Therefore, despite the importance of data management in addressing data quality challenges, sub-optimal data entry affects the operational efficiency and accurate reporting of business operations (Oracle Corporation 2011). Notwithstanding the minor differences between data quality averages measured from feedback data and source system transactional data in Table 3, at least 18.69% (= 100% − 81.31%) to 19.95% (= 100% − 80.05%) of the dispatched work orders should not have been executed. These minor variances cost APGDCO substantially from a resource and reputation perspective as the resource expended, namely, labour hours and vehicle kilometres driven could have been spent on, for example, plant maintenance work. Furthermore, customers would wait longer for their supply to be restored because of invalid ESP calls receiving undue attention. The variances between these perspectives on data demonstrate that transactional data constitute large, complex, unstructured data sets that are hard to deal with using conventional tools and techniques and reflect public institutions' incapacity to optimally unlock value from such data (OECD 2016). Despite these discrepancies between source data quality and feedback data quality, the general upward trajectory of data quality between 2012 and 2017 indicates that APGDCO was striving to use its analytical capabilities to optimise data quality, notwithstanding its institutional constraints surrounding productive usage of data. The prudent use of data analytics is considered instrumental in facts-based strategic decision-making, improving operational efficiency and revenue levels (Singh 2018). However, APGDCO has not sufficiently exploited these data-driven capabilities to increase its profit margins and revenue.
The correlation result demonstrates a positive statistically significant but weak relationship between source system data quality and transactional feedback. This somewhat coheres with the upward trajectory reported in the interaction of source system data quality and transactional feedback - a clear indication that as more correct data quality is captured at the source, technicians are more inclined to execute more correct ESP (which are faults of APGDCO), which results in more feedback of correct transactions executed. This finding could give credence to the claim that data integration and transaction analytics are rendering implementable data-driven insight in a visually interactive (to both data agents and technicians) and iterative, agile manner (OECD 2016). However, accepting this claim contradicts the observation that the persistent albeit marginal discrepancies between source system data quality and transactional feedback are clearly indicative of the failure of APGDCO to exploit technicians' feedback to optimally improve successive data capturing processes. These discrepancies between results of data quality measured from data creators and data consumer perspectives demonstrate that processing big data remains a daunting task for public institutions and cannot guarantee optimal decision-making even though it is instrumental in decision support systems (Alketbi 2014).
The results of regression analysis show that transactional feedback is significantly dependent on source system data quality - that is source data significantly predicts feedback quality. This means the frequency of accurate data captured at the source increases the successful resolution of customer ESPs by field technicians. Apart from accurate data capturing, data consolidation and real-time data synchronisation have potential to improve data quality in organisational operations (Oracle Cloud 2015). This finding supports the view that because decision-making in companies can be foreseen and proactive, the initiation of information collection process earlier means that the timeliness of information should improve the quality of data-driven decision-making (Dillon, Buchanan & Corner 2010).
From a theoretical perspective, the current transactional data system under scrutiny demonstrates an open-loop system as depicted in Figure 7, where:

-
Input is the customer call.
-
Controller function is performed by the contact centre following the case-based reasoning logic.
-
Process such as ESP will be determined via the controlling function.
-
Output is a resultant work order executed by the field technician and feedback captured during the completion of the work order.
As evident in the results of the correlation and regression analyses, an increase in correct transactions captured will result in improved transaction feedback, indicating that correct transactions were captured and executed. To improve the quality of transactional data captured, an FCS with a closed-loop configuration shown in Figure 8 would be invaluable. This configuration is the same as Figure 7, but the feedback of the technician is fed back to the controller.

The application of an FCS in this context is different from the one envisioned by Orr (1998) to update an existing master data record. Updating an incorrect transaction after it was executed will not provide any immediate benefit to the organisation as costs (e.g. on mileage, time and overtime payments) would have already been incurred by the organisation to resolve a customer-side fault. This understanding seems incongruent with the claim that large sets of raw data combined with powerful and sophisticated analytics tools provide insights that improve operational performance of large organisations (Henke et al. 2016). This is because recognition of a mistake may not always translate into pre-emptive and corrective future interventions even though organisations would be expected to learn from past mistakes to enhance the accuracy of their future transactions. However, when organisations learn, such a learning experience which unfolds via feedback is also known as a self-normative FCS (ed. François 2011). In this example, feedback indicating a customer side fault will be fed back to the data creator/contact centre agent. This feedback can then be used to identify the root cause of the incorrectly logged customer-side fault, such as data creator interpretation, issues in the logic of the case-based reasoning questions or customer providing false information.
Managerial implications
The fact that accurate source data predicts technician feedback implies that effective data management through reducing fragmentation and inconsistencies amongst data agents dealing with data collection can contribute to improved data quality in dynamic environments (Lin et al. 2007). Therefore, organisations can stand to improve their operational efficiency, reduce financial misappropriations and waste if their data capturing at the source improves. This implies that managers should commit more financial and intellectual resources towards continuous on-the-job training in data capturing to reduce inaccurate data capturing which leads to multiple technician assignments to resolve ESP caused by customer mistakes, such as overloading of their residential electrical circuit and faulty appliances causing a circuit breaker to trip.
Transactional data quality can also be improved by an FCS, if (1) a mechanism is available to capture feedback and (2) the feedback is integrated back to the controller of the transactional data. This will allow identification of the root cause of poor-quality data and facilitate the reduction in or eradication of future occurrences thereof. As the complexity of a closed-loop system comes at an increased cost, performing a cost-benefit analysis is critical before deciding whether to implement an FCS strategy to improve transactional data quality (Batini & Scannapieco 2016).
The fact that at least 18.69% - 19.95% of the dispatched work orders should not have been executed is indicative of the financial and time cost that can be avoided should appropriate data capturing techniques be applied. As such, customer misinformation must be prevented by requiring data capturers to sufficiently probe customer queries before dispatching technicians to ensure that correct, comprehensive and reliable data are captured at the source. Because the mistakes made by data capturers also contributed to ESP faults, continuous training on data capturing can contribute to the generation of quality data at the source. Moreover, managers and executives should continue to focus on the critical importance of correct data entry as it forms the basis of a successful data management system.
When this happens, the root cause of faulty data entry can be identified and corrective actions and/or learning and application can be facilitated to reduce or ultimately prevent future occurrences of invalid transactions.
Implications for future research
In view of the consistencies (upward improvements in data quality) and discrepancies (technician feedback quality being slightly higher than source-generated data) between data quality measurements from technician feedback and source-generated data, future studies may need to track the sequence of the generation of each perspective/source on data quality (technician-generated and source-generated) and their synchronisation and integration. As Hand (2018) observes, transaction data are special types of administrative data concerned with the sequences of events relating to transactions, their retention in databases and analysis to improve the understanding of organisations' operations. As such, what happens at each stage becomes critical to improve the quality of transactional data.
Data quality improvement costs should always be an important consideration before deciding on an appropriate quality improvement strategy (Batini & Scannapieco 2016). Therefore, even though an FCS has the potential to facilitate transaction data quality improvements, the cost to implement should be carefully analysed before implementation to ensure a positive return on investment (ROI). Future studies can examine the return on investment potential of various FCS and compare it to the improvement in transaction data quality achieved. This is because although an FCS could be initially expensive to establish, the ROI would rise over time of its application. Future studies may also explore methodologies to accurately determine the cost of incorrect transactional data across industries and different businesses and determine at which level of data quality does the cost to improve negate the benefits derived.
Because some inconsistencies in data quality may be attributed to organisational difficulties in defining master and transactional data, future studies can examine the different ways in which such data types are defined and characterised in organisations to ensure congruence and consistencies in ways the same data pieces are defined, categorised and assessed by different agents within and outside organisations. Recent literature suggests that the quality of a data set and each of its individual components can be influenced by a number of different factors (e.g. inaccuracy, imprecision in definitions, gaps or inconsistencies in measurements), thus necessitating the development of a context-dependent data quality evaluation framework (Marev et al. 2018). For consistency and believability, consistent representation of data partly depends on the precise characterisation and definition of data dimensions in specific contexts (Batini et al. 2009; Pipino, Lee & Wang 2002).
Conclusion and recommendations
In view of the inconsistencies between data quality measurements from technician feedback and source-generated data, the entire value chain of data generation needs scrutiny. Moreover, Broadridge (2017) recommends increased granularity in consolidated data presentation because granular data often demonstrate that surface-level transactions may be inconsistent with the picture developed from lowest-level detail. Moreover, Alketbi (2014) recommends the development of a complete data quality framework for improved data quality and data-driven decision-making in public organisations. At the level of predictive relations, the positive association between source-generated data and technician feedback data could be indicative of the capacity of tracking different types of data to improve overall data quality. Broadridge (2017) observes that data quality issues are proportionally related to the sequence in which firms tackle data improvement projects (i.e. from valuation or reference, transactional and derived data). Therefore, firms should consider the proper implementation of an FCS to enhance their data quality strategy, as it provides critical information required to drive four of the 12 directives of a continuous improvement programme as suggested by Sebastian-Coleman (2012), namely:
-
Understand data quality as defined by its consumers.
-
Attend to root causes of data issues.
-
Measure data quality.
-
Ensure data producers are kept accountable for the quality of their data.
Acknowledgements
The authors are grateful to the power generation company for availing historical data and to technicians for participating in the interviews
Competing interests
The authors have declared that no competing interest exists.
Authors' contributions
All authors contributed equally to this work.
Ethical consideration
This article followed all ethical standards for research without direct contact with human or animal subjects.
Funding information
This research received funding from the Central University of Technology and the power generation company that cannot be named for anonymity purposes.
Data availability statement
Data sharing may not be possible for this article as some of the pieces of data will expose the name of the institution in which the research was conducted, thus compromising participants' anonymity.
Disclaimer
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of any affiliated agency of the authors.
References
Arun, K. & Jabasheela, L., 2014, 'Big data: Review, classification and analysis survey', International Journal of Innovative Research in Information Security 1(3), 17-23. [ Links ]
Alketbi, O., 2014, Data quality assurance for strategic decision making in Abu Dhabi's public organisations, University of Bedfordshire, Luton.
American Council for Technology-Industry Advisory Council (ACT-IAC), 2015, Data quality: Letting data speak for itself within the enterprise data strategy, Collaboration & Transformation (C&T) Shared Interest Group (SIG) and Financial Management Committee, Fairfax, VA.
Bakshi, U.A. & Goyal, S.C., 2009, Feedback control systems, 2nd edn., Technical Publications, Pune.
Baran, R.J. & Galka R.J., 2016, Customer relationship management: The foundation of contemporary marketing strategy, 2nd edn., Taylor & Francis, New York, NY.
Bärenfänger, R., Otto, B. & Gizanis, D., 2015, Business and data management capabilities for the digital economy White Paper. Capabilities in the digital economy, Competence Centre Corporate Data Quality (CC CDQ), May 2015.
Batini, C., Cappiello, C., Francalanci, C. & Maurino, A., 2009, 'Methodologies for data quality assessment and improvement', ACM Computing Surveys 41(3), 1-52. https://doi.org/10.1145/1541880.1541883 [ Links ]
Batini, C. & Scannapieco, M., 2016, Data and information quality: Dimensions, principles and techniques, Springer, Cham.
Bester, J., 2019, 'The influence of transactional data quality improvements on monetary savings of Eskom distribution, Free State', Master's thesis, Central University of Technology Free State, Bloemfontein. [ Links ]
Biegel, B., Margulies, J., Maggi, G. & Davis, C., 2018, The state of data 2018: A Winterberry Group Report, December 2018, Winterberry Group, New York, NY.
Borek, A., Parlikad, A.K., Webb, J. & Wooda, P., 2014, Total information risk management: Maximizing the value of data and information assets, Elsevier, New York, NY.
Brackstone, G., 1999, 'Managing data quality in a statistical agency', Survey Methodology 25(2), 139-150. [ Links ]
Broadridge, 2017, A practical guide on data initiatives for public and private investments: Establishing data governance and better data management, Broadridge Financial Solutions, New Hyde Park, NY.
Burrows, T., 2014, ITWeb: SA looks to address data quality, viewed 03 January 2018, from https://www.itweb.co.za/content/JOlx4z7kGXY756km.
Cai, L. & Zhu, Y., 2015, 'The challenges of data quality and data quality assessment in the big data era', Data Science Journal 14(2), 1-10. https://doi.org/10.5334/dsj-2015-002 [ Links ]
Dillon, S., Buchanan, J. & Corner, J., 2010, 'Comparing public and private sector decision making: Problem structuring and information quality issues', Proceedings of the 45th annual conference of the ORSNZ, November 2010, pp. 229-237.
Entity Group, 2016, Why not to put transactional data in an MDM hub, viewed 07 November 2018, from https://www.entitygroup.com/wp-content/uploads/2016/05/master_data_management_and-Transaction_data_whitepaper.pdf. https://www.entitygroup.com/wp-content/uploads/2016/05/master_data_management_and-Transaction_data_whitepaper.pdf.
Epstein, E., 2012, Implementing successful building information modeling, Artech House, Norwood, OH.
Experian Data Quality, 2017, The 2017 global data management benchmark report, viewed 01 April 2020, from https://www.experian.com.my/wp-content/uploads/2017/12/2017-global-data-management-benchmark-report.pdf
François, C. (ed.), 2011, International encyclopedia of systems and cybernetics, 2nd edn., Walter de Gruyter, München.
Fürber, C., 2015, Data quality management with semantic technologies, Springer, Wiesbaden.
Grillo, A., 2018, 'Developing a data quality scorecard that measures data quality in a data warehouse', PhD thesis, Brunel University, London. [ Links ]
Hand, D., 2018, 'Statistical challenges of administrative and transaction data', Journal of the Royal Statistical Society: Series A 181(3), 555-605. https://doi.org/10.1111/rssa.12315 [ Links ]
Hagerty, J., 2016, 2017 planning guide for data and analytics, Gartner Technical Professional Advice, Stamford, CT, 13 October 2016.
Haneem, F., Kama, N. & Kazmi, A., 2016, 'Master data identification in public sector organisations', Advanced Science Letters 22(10), 2999-3003. [ Links ]
Henke, N., Bughin, J., Chui, M., Manyika, J., Saleh, T., Wiseman, B. et al., 2016, The age of analytics: Competing in a data-driven world, McKinsey Global Institute, McKinsey & Company, San Francisco, CA.
Holcomb, Z.C., 2016, Fundamentals of descriptive statistics, Routledge, New York, NY.
Infovest, 2018, Introduction to data governance, Rondebosch, Cape Town.
Keller, S., Korkmaz, G., Orr, M., Schroeder, A. & Shipp, S., 2017, 'The devolution of data quality: Understanding the transdisciplinary origins of data quality concepts and approaches', Annual Review of Statistics and Its Application 4, 85-108. https://doi.org/10.1146/annurev-statistics-060116-054114 [ Links ]
Kumar, R., 2014, Research methodology: A step-by-step guide for beginners, Sage, Los Angeles, CA.
Lin, S., Gao, J., Koronios, A. & Chanana, V., 2007, 'Developing a data quality framework for asset management in engineering organisations', International Journal of Information Quality 1(1), 100-126. [ Links ]
Liptak, B.G. (ed.), 2018, Instrument engineers' handbook, volume two: Process control and optimization, 4th edn., CRC Press, Boca Raton, FL.
Marais, H., 2017, 'Assessing the data quality of performance information generated by the health sector in the Breede Valley subdistrict for evidence-based decision-making', Master's dissertation, University of Stellenbosch, Cape Town. [ Links ]
Marev, M., Compatangelo, E. & Vasconcelos, W., 2018, Towards a context-dependent numerical data quality evaluation framework, Technical Report, University of Aberdeen, Aberdeen.
McGilvray, D., 2010, Executing data quality projects: Ten steps to quality data and trusted information, Publishing House of Electronics Industry, Beijing.
McKenzie, S., 2014, Vital statistics: E-book: An introduction to health science statistics, Elsevier Australia, Chatswood, NSW.
Mele, C., Pels, J. & Polese, F., 2010, 'A brief review of systems theories and their managerial applications', Service Science 2(1-2), 126-135. https://doi.org/10.1287/serv.2.1_2.126 [ Links ]
Milham, M.P., 2012, 'Open neuroscience solutions for the connectome-wide association era', Neuron 73(2), 214-218. https://doi.org/10.1016/j.neuron.2011.11.004 [ Links ]
Nazim, M. & Mukherjee, B., 2016, Knowledge management in libraries: Concepts, tools and approaches, Chandos Publishing, Cambridge.
Neely, P. & Pardo, T., 2002, Teaching data quality concepts through case studies, Centre for Technology in Government, Albany, NY.
Nelke, S., Oberhofer, M., Saillet, Y. & Seifert, J., 2015, Method and system for accessing a set of data tables in a source database, U.S. Patent 2015/0066987 A1, 05 March 2015.
Nieuwenhuis, J., 2014, 'Analysing qualitative data', in K. Maree (ed.), First steps in research, pp. 99-103, Van Schaik Publishers, Pretoria.
Oracle Cloud, 2015, The role of data integration in public, private, and hybrid clouds, Redwood Shores, CA.
Oracle Corporation, 2011, Oracle master data management, An Oracle White Paper, September 2011, Redwood Shores, CA.
Organisation for Economic Co-operation and Development (OECD), 2016, 'Using big data in tax administrations', in Technologies for better tax administration: A practical guide for revenue bodies, pp. 47-73, OECD Publishing, Paris.
Orr, K., 1998, 'Data quality and systems theory', Communications of the ACM 41(2), 66-71. https://doi.org/10.1145/269012.269023 [ Links ]
Palavitsinis, N., 2013, 'Metadata quality issues', PhD thesis, Alcalá de Henares, Madrid. [ Links ]
Pipino, L.L., Lee, Y.W. & Wang, R.Y., 2002, 'Data quality assessment', Communications of the ACM 45(4), 211-218. https://doi.org/10.1145/505248.506010 [ Links ]
Rambe, P. & Bester, J., 2016, 'Financial cost implications of inaccurate extraction of transactional data in large African power distribution utility', Problems and Perspectives in Management 14(4), 112-123. https://doi.org/10.21511/ppm.14(4).2016.14 [ Links ]
Rothbad, A., 2015, Quality issues in the use of administrative data records, pp. 3-38, University of Pennsylvania, Philadelphia, PA.
Sebastian-Coleman, L., 2012, Measuring data quality for ongoing improvement: A data quality assessment framework, Elsevier, Waltham, MA.
Silberschatz, A., Korth, H. & Sudarshan, S., 2006, Database system concepts, Higher Education Press, Beijing.
Singh, H., 2018, Using analytics for better decision-making, viewed 01 April 2020, from https://towardsdatascience.com/using-analytics-for-better-decision-making-ce4f92c4a025?gi=ea4ae2c019a2
Skyttner, L., 2001, General systems theory: Ideas and applications, World Scientific River Edge, NJ.
Statistics Divisions of UN/DESA and UN Economic Commission for Europe, 2015, Results of the UNSD/UNECE survey on organizational context and individual projects of big data, Statistics Divisions of UN/DESA and UN Economic Commission for Europe, New York, NY, 03-06 March 2015.
Vermaat, M.E., 2014, Discovering computers and Microsoft Office 2013: A fundamental combined approach, Cengage Learning, Boston, MA.
Wang, R.Y. & Strong, D.M., 1996, 'Beyond accuracy: What data quality means to data consumers', Journal of Management Information Systems 12(4), 5-33. https://doi.org/10.1080/07421222.1996.11518099 [ Links ]
World Economics, 2017, The data quality index (DQI), viewed 03 January 2018, from https://www.worldeconomics.com/Pages/Data-Quality-Index.aspx.
 Correspondence:
Correspondence:
Patient Rambe
prambe@cut.ac.za
Received: 16 July 2019
Accepted: 23 Feb. 2020
Published: 19 May 2020
1 . Because of intense scrutiny from civil society, this state-owned enterprise (SOE) is under pressure owing to its financial losses and allegations of malpractices, and therefore its name has been anonymised as APGDCO.