Services on Demand
Article
Indicators
Related links
-
 Cited by Google
Cited by Google -
 Similars in Google
Similars in Google
Share
South African Journal of Information Management
On-line version ISSN 1560-683X
Print version ISSN 2078-1865
SAJIM (Online) vol.20 n.1 Cape Town 2018
http://dx.doi.org/10.4102/sajim.v20i1.926
ORIGINAL RESEARCH
A South African university's readiness assessment for bringing your own device for teaching and learning
Nkqubela RuxwanaI; Mncedisi MsibiII
IDepartment of Information Technology, Tshwane University of Technology, South Africa
IICouncil for Scientific and Industrial Research, South Africa
ABSTRACT
BACKGROUND: The use of mobile devices for education is rapidly growing, and it is a global phenomenon. The trend of bringing personal mobile devices for learning using the institution's network to access data and other academic material is referred to as bring your own device (BYOD). Most universities in developed countries have implemented this phenomenon to enhance education. However, the rate of BYOD adoption in developing countries is lagging even though the majority of students and staff already own one or more mobile devices and are using them for personal and educational purposes
OBJECTIVES: The study determines the readiness of a South African university to adopt BYOD for teaching and learning. Moreover, the article presents the enabling factors and barriers of BYOD adoption within the university
METHOD: The study followed an interpretivist philosophical stance. A qualitative single-case study was used. Data were collected through questionnaires and thematic analysis was applied
RESULTS: The BYOD readiness levels are low and are hampered both by organisational and technological factors. Key barriers include lack of comprehensive policies to govern the use of these devices, lack of infrastructure, limited top management support for innovations and security complexities, while the key enabling factors included accessibility to mobile technologies, ease of use, relative advantage and convenience
CONCLUSION: Bring your own device offers a suitable platform for mobile-learning (m-learning) in universities. Consideration of the readiness factors, such as adoption strategy, implementation plans, security and device management, skills development, and measures of discipline, is essential
Background of the study
Technology has for a long time been part of teaching and learning as a tool to enhance education (Leidner & Jarvenpaa 1995; Owston 1997; Papert 1973). In today's fast-paced environment and perpetual advances in technology, mobile computing devices are the order of the day. The increased penetration of smart phones and their ownership among the youth within the decade, sees more attention being drawn to smart mobile devices over desktop computers as compared to the past decade. Educators globally are emphasising the need for students to become more creative by incorporating digital tools and the Internet to enhance learning (Pegrum 2009). This increase in smart phone ownership among the youth, particularly in students, has seen universities in developing countries taking notice and capitalising on this to enhance learning. Students are allowed to bring their own smart mobile devices to class to use on the institution's network for learning in a practice called 'bring your own device (BYOD)'. Smart phones have almost the same computing capabilities as desktop computers and some extra features such as voice and video recording, digital camera and other applications that can be used to enhance learning.
Though BYOD has been accepted and is being used to enhance student motivation and learning in tertiary institutions in developed countries (Akin-Adetoro & Kabanda 2015; Attewell 2005; Sweeney 2012), the current body of knowledge reveals limited knowledge about the extent of BYOD readiness and its adoption rates in developing countries. In South Africa, in particular, the concept of BYOD has not been widely explored and there are limited studies indicating the implementation and the extent of BYOD in the education sector. Furthermore, current research studies have been focused on e-learning tools and m-learning, and not addressing how universities in South Africa can capitalise on the increased ownership of mobile devices by students to maximise learning by allowing these devices in classrooms and learning activities. This article will first discuss the notions of BYOD, BYOD in developing countries, BYOD challenges and concerns for education, BYOD challenges and countermeasures for education and BYOD factors to consider. The article also discusses the theoretical approach to the study, research methodology, results discussion, and study conclusions.
Bring your own device concepts
Though definitions of BYOD differ based on whether it is used in the context of work or education, its core purpose is to take advantage of user-owned smart mobile devices to maximise productivity. In the context of a work environment, BYOD refers to the practice that allows users to complete tasks in their organisations by using their personally owned devices and technology to connect to, access data or complete tasks from the organisation's network (Afreen 2014). When the purpose is primarily focused on the use of personally owned devices to facilitate personalised teaching (Kong & Song 2015), BYOD is defined to be in line with education. Bring your own device is defined as the strategy that uses student-owned mobile communication devices (MCDs) to enhance learning (Norris & Soloway 2011; Wittman 2011). These MCDs come embedded with different integral features and apps to use anywhere and anytime and can also be used for the purpose of learning. Bring your own device can also be defined to accommodate both working and learning contexts. In such a case, and as the adopted definition for this study, BYOD refers to 'the practice of people bringing their own laptops, tablets, smart phones, or other mobile devices with them to learning or work environments' (Johnson et al. 2016).
Bring your own device in developing countries
Bring your own device is a global phenomenon (Cisco 2012). Countries in the most developed regions have adopted and deployed trusted BYOD models (Attewell 2005; Sweeney 2012). Developing countries are adopting BYOD at high rates, while the least developed countries have not fully understood this paradigm shift (Akin-Adetoro & Kabanda 2015). Within the information systems circle, there have been a lot of research studies on technology adoption, yet few of those have contextualised themselves to suit the investigation of technology adoption in developing countries (Akin-Adetoro & Kabanda 2015). Africa is a continent that houses the least developed countries that suffer from low levels of human development and extreme poverty (Tekin 2012). It experiences challenges in getting integrated into the global economy as it lacks basic infrastructure like roads, electricity and telecommunication (Goedhuys, Janz & Mohnen 2013). There is, however, hope for BYOD adoption even in this region, as it has been proven that mobile devices have increasingly become more affordable over the years.
In the case of South Africa, the economy expanded by only 0.3% in 2016, largely owing to sharply lower output in the agriculture, mining and electricity sectors (IDC 2017). However, the number of mobile phone connections in South Africa was at 85.53 million in 2016 (Shezi 2016). According to Ford and Botha (2010), the mobile device is the most widespread computing device among South African youth. This presents an opportunity for BYOD in South Africa; however it is also essential to consider the challenges and concerns of BYOD in education, presented in the next section.
Bring your own device challenges and concerns for education
In an academic institution, security is not the main challenge but a critical concern to be considered. This is because it is difficult to monitor so many student mobile devices in one place (Hockly 2012). The following are some of the concerns for BYOD in education:
· Equity - Traditionally, institutions provide learning technology to students, whereas BYOD allows students to bring their personally owned devices, creating an imbalance as some students cannot afford these devices. This causes more affluent students to have an unfair advantage over their classmates (Stavert 2013).
· Classroom management - Effective classroom management is a requirement for effective education (Korpershoek et al. 2014). With many different mobile devices in one classroom, it is difficult to manage the proceedings in a classroom-based setting.
· Not the best tool for the task - BYOD may not be the ideal technology for education regardless of the praise it gets; for example, a BYOD model that enables student's choice of device does not have personalised learning as its focus is not to provide each student with the best device for learning but rather whatever their families can afford (Dixon & Tierney 2012).
· IT infrastructure and support - The challenge with moving from an 'already-in-place' technology to an 'unknown' one is the inadequacy of the IT infrastructure and support.
· Bandwidth capacity - The worry with many mobile devices in one area attempting to all gain access to the network is bandwidth exhaustion (Mansfield-Devine 2012).
· Cost - It is not clear whether BYOD reduces financial costs or not. However, some research studies argue that the objective of BYOD is not to save money (Sliep 2014); it should be about delivering education in new ways (Sweeney 2012). The reality is that even though BYOD sees institutions providing fewer technologies and devices for students, 'it does not ipso facto outweigh the cost for upgrading the IT infrastructure' (Sliep 2014).
In order to successfully adopt and implement BYOD for education, there are countermeasures to address these concerns and they are discussed in the next section.
Bring your own device challenges and countermeasures for education
Regardless of the challenges already discussed, there is still a huge potential for BYOD adoption if the proper countermeasures are in place. Below is a discussion of these countermeasures:
· Mobile device management (MDM) - The MDM tool helps the organisation to fully control the devices which are generally supported by application programming interfaces (APIs) of smartphones (Ghosh, Gajar & Rai 2013). Mobile device management suites function like that of a PC's configuration life cycle management (PCCLM) and provide a secure mobile environment.
· Device neutral assignments (DNA): As a countermeasure to the issue of different learning platforms, DNA should be created. Device neutral assignments refer to lessons that can be deployed to any device (Campo 2013).
· Deploy the appropriate model for your school: Researchers (Dixon & Tierney 2012; Stavert 2013; Sweeney 2012) summarise BYOD models as: (1) tightly controlled models - where students are given the same laptops with the same functions and pre-defined materials, (2) limiting devices based on pre-defined requirements models - where the institution actually specifies the requirements for the mobile device that the student may bring to class and (3) accepting any Internet-ready mobile device models - where students get to bring their own choice of device as long as it can be used for learning and has Internet access.
Bring your own device adoption factors to consider
Though adoption of BYOD in the most developed countries is at higher levels, not all BYOD implementations are a success (Emery 2012). How much worse is it in countries where technological innovations are not as advanced? Most universities in developed countries such as the United States, Australia and New Zealand have already adopted and implemented BYOD (Afreen 2014; Dedeche et al. 2013). It is imperative therefore that careful consideration of BYOD in tertiary education be made for successful adoption of BYOD. There are four categories of factors to be considered when developing an institution-wide strategy to address the utilisation of BYOD. These are policy development, data security, user education and mobile-learning (m-learning):
· Policy development: The starting point for any school wishing to embrace BYOD is defining an acceptable use policy (AUP) (Intel Education 2014). This policy should address issues such as which devices and applications will be or will not be endorsed on the BYOD platform. It further involves considering and managing other sub-factors such as authorised use, prohibited use, systems management, policy violations, policy reviews and limitations of liability (Emery 2012). Many education institutions have allowed some form of BYOD in their campuses mostly in the form of network access control (NAC), without implementing a proper BYOD AUP (Afreen 2014). The development of a BYOD AUP must directly involve users so that central IT can have high visibility into devices at the institution and how they are being used (Mansfield-Devine 2012).
· Data security: Data security is the most critical factor to consider as a measure to support and protect data in an institution-wide BYOD environment. Data security involves consideration of sub-factors such as unauthorised access to data stored on the organisation's network, attacks from malicious software and the ability to impersonate the user (Markell & Bernik 2012). Mobile devices can be a gateway to an organisation's private data if appropriate precautions are not taken in advance. This is confirmed by a NowSecure report in 2016 that 35% of communications sent by mobile devices are unencrypted, business apps are three times more likely to leak log-in credentials than the average app and that games are one-and-half times more likely to include high-risk vulnerability than the average app (Now Secure 2016). In ensuring that mobile devices are secure, sub-factors such as segregating the data, prompting users to register their devices, enabling remote access to devices and implementing data encryption should be considered.
· User education: User learning explains factors involved in the user learning to use mobile devices in a BYOD environment within the institution. These include social media usage, personally identifiable information, strong passwords and privacy settings (Intel Education 2014). User education is concerned with educating users on a new innovation and how to make use of the innovation.
· Mobile-learning: BYOD in education is a practice inspired by the concept of m-learning. The term m-learning is applied to learning exploits using handheld computing devices (Botha, Herselman & van Greunen 2010). It explains education that involves the use of mobile devices anywhere and any time (Kraut 2013). As a base for BYOD in education, m-learning practices must be considered, as the BYOD concept is almost the same and is an extension of m-learning. Mobile-learning was established to enable learners to access learning content using mobile devices even beyond the classroom environment. Bring your own device adopts the same concept and allows smart mobile devices which have added capabilities, such as video and audio recording, global positioning and other apps, to be brought into class for learning purposes.
Theoretical approach
Studies that address technology adoption are not new. Several other studies on BYOD adoption have been conducted to address the concept of BYOD in higher education. For example, one study focused on BYOD in higher education, exploring opportunities and challenges (Afreen 2014), and another focused on BYOD future classroom lab (Attewell 2005). However, these studies focus on BYOD adoption in developed countries; only a few studies have been contextualised to cater for investigations of technology readiness and adoption in developing countries, particularly in the South African context. On this note, the study uses the technology-organisation-environment (TOE) (Tornatzky & Fleischer 1990) in conjunction with the diffusion-of-innovation (DOI) (Rodgers 2003) theories to identify BYOD readiness factors that could affect its adoption in developing countries.
The TOE theory is useful in this study because of its flexibility to select specific variables to assess its factors. Technology-organisation-environment describes the contexts that influence the organisation's adoption of an innovation. These are the technological context, organisational context and environmental context. Of the three contexts, more focus is placed on the organisational and technological contexts as the study's objectives are to ascertain a university's readiness for BYOD adoption based on technology and organisational readiness.
The DOI theory is concurrently used with TOE, given its wide application to address technology adoption at both enterprise level and user level. Certain uncertainties may arise in the process of diffusion and these may affect the adoption process of the innovation (Rodgers 2003). The DOI theory comprises five attributes of innovation that help address these uncertainties but only the following three are used in the study: (1) Relative advantage - which addresses an extent by which an innovation outperforms the product or services it replaces (Rodgers 2003). Bring your own device offers flexibility and mobile devices are portable to carry anywhere and any time which is an advantage as compared to desktop computers. (2) Compatibility - which addresses how an innovation is perceived as being consistent with existing values, past experiences and needs of potential adopters. In the case of this BYOD for education, the practice is not meant to entirely replace desktop computers, but it is meant to be an added technology to be incorporated to work in unison with the existing technology for the sole purpose of learning. (3) Complexity - which addresses the difficulty in understanding and using the new technology. One of the most notable advantages of BYOD is its flexibility and ease of use as users use their own devices that they are already familiar with, meaning that it will not be too steep a task to use even for learning purposes.
Methodology
The study is interpretive in nature and aims to elicit the understanding, experience and perceptions of the participants on the identified factors around the readiness of an institution they are in to adopt BYOD as part of academic processes. This paradigm was found the most suitable for this study's purpose as it helps to focus on fresh, complex and rich descriptions of the phenomenon as it is concretely lived (Finlay 2009), and it further facilitates the understanding of people's perceptions towards events that are external to them (Collins & Hussey 2003; Leedy & Ormrod 2001). They employed a multi-method qualitative research approach, within a single-case study, based on the fact that most variables explored are behaviour related in nature. Qualitative research techniques are used to capture people's viewpoints, subjective explanations, emotions and dynamics, and observations in an environment (Malterud 2012). Data were collected using multi-method collection, which included interviews and questionnaires with the qualitative study paradigm, in a South African university based in Gauteng province. This article presents questionnaire findings which focused mostly on gathering data on the organisational and technological aspects of BYOD as underpinned by the adapted TOE & DOI constructs. Purposive sampling methods were used to select the study participants. A total of 50 questionnaires were distributed among students, academic staff and IT personnel, and out of the 50 participants, only 28 interviews were conducted. Table 1 shows the distribution. The data analysis followed the qualitative data analysis, wherein a thematic analysis technique (Braun & Clarke 2006) was employed to effectively analyse data collected, within the constructs of the conceptualised theoretical framework underpinning the study.

Results
The findings indicate the recognition of the conceptualised readiness factors for BYOD adoption in a South African university, where a priori factors analysed were suitability, discipline, accessibility, relevance, implementation, allowance, strategy and readiness. The summary of findings on key readiness factors of BYOD is presented in Table 2.

As depicted in Table 2, 78% of the entire 50 participants indicate Suitability, which refers to the aspect of how convenient, conducive and simple mobile devices are when used for learning purposes. This number shows a positive result in that participants feel that their devices are suitable enough to be used as a tool for learning. When it comes to the element of Discipline, the findings indicate that participants are not disciplined enough to use their smart mobile devices during class time, as indicated by the low total of 28%. This result is influenced by there being no policy to govern the use of smartphones for students, resulting in students secretly using their devices during class time. Because there is no policy to govern the use of these devices during class time, the secret use causes disturbances to lectures and loss of focus, whereas if there was a policy, this could be controlled. In addition, a significant 70% indicates participants' perceptions on the Challenges that BYOD could pose. This number is influenced by a number of issues which include there currently being no policy for BYOD, there are limited subjects that can be viewed or learnt on smartphones and tablets as their computing power is low compared to desktop computers, the monitor size is small, they cause disturbances in class when they ring, they get lost, there is bandwidth exhaustion, they are vulnerable to hacking and many other challenges. However, regardless of these challenges, the findings reveal that academic staff and IT personnel are already in possession of tertiary-provided smart mobile devices and use these on the institution's network.
Moreover, the element of Accessibility explains the actual access to these smart mobile devices, and the ownership of these devices. A significant 88% of participants have access to these devices. The findings reveal that some own more than one device and use these to conduct school work as well. This is a positive result because as accessibility increases, chances of BYOD adoption also increase. This is influenced by the high smart mobile device penetration among the South African youth. Furthermore, the Relevance element was analysed to assess the current technological set-up in terms of its being relevant to support BYOD. About 56% of participants believe that the current technology can hold BYOD and is relevant enough to handle the transition should there be one. This number is a little over 50%, which is an indication that the current technology can support BYOD, but it is also an indication that upgrades would be required.
The Implementation element, on the contrary, was meant to establish if smart mobile devices should be implemented as a permanent part of learning. The findings reveal that only 42% want smart mobile devices to be implemented as a permanent part of learning. This number is lower than 50%, which shows a low response in terms of enthusiasm, and it is influenced by the challenges stated earlier. This, however, does not mean that participants discredit smart mobile devices, but these could be incorporated with current technologies used for learning so as to get the best of results. The Allowance element was analysed to establish the element of users being allowed to use their own or tertiary-provided smart mobile devices. The findings show that a combined 62% of participants concur with using their own devices. The Strategy element was analysed to establish the best method that would need to be employed in the adoption of BYOD. The findings reveal that 33 out of 35 students think the best strategy would be for the institution to capitalise on the fact that almost all the students are already in possession of smart mobile devices and should be allowed to bring them for use in class for learning. The findings also show that 9 out of 10 academic staff believe that smart mobile devices allowed onto the institution's network should meet certain requirements specified by the institution. This is because academic staff use tertiary-provided smart mobile devices which match requirements specified by the institution for their work. Four out of five IT personnel also believe the same. A combined 92% reveal that all these strategies could work in the adoption of BYOD in the South African university environment, with more emphasis on outlining the specifications.
Lastly, the Readiness element of the study was analysed to establish the readiness levels of organisational users and employees to adopt BYOD. The findings reveal that 27 out of 35 students believe that they are ready to adopt BYOD based on the technological capabilities of the smart mobile devices. Seven out of the 10 academic staff believe that they are ready, while three out of five IT personnel also believe the same. A combined 78% of all participants believe that they are ready for BYOD adoption. This number is influenced by the elements discussed prior to the Readiness element. The above discussion is clearly illustrated in Figure 1.
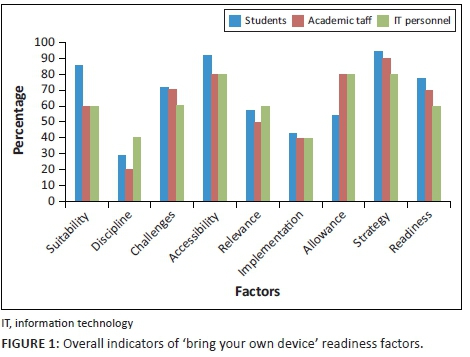
For the institution to be ready for BYOD adoption, both technological and organisational readiness factors must be positive. Organisational readiness explains the preparedness and willingness of employees to adopt BYOD based on the capability of the organisation to absorb the innovation. The findings revealed that employees have some level of expertise in terms of supporting mobile devices that access and use the system. However, the current infrastructure is not equipped with the capability to support an influx of devices that BYOD would bring, exposing it to security vulnerabilities and causing strain on the help desk support. Moreover, the IT policy in place prohibits the use of some of these devices in class for learning as they cause disturbances. Technological readiness on the contrary is associated with the availability of technology infrastructure that is compatible with the use and adoption of BYOD: privacy, security, compatibility and complexity, particularly with respect to alignment with legacy systems (Akin-Adetoro & Kabanda 2015). After analysis, the findings reveal that technological factors such as relative advantage, simplicity, compatibility and innovativeness influence the institution's readiness to adopt BYOD, while organisationally, it is factors like IT policy, IT infrastructure and strategy in terms of top management support that influence the readiness to adopt BYOD. Although the analysis proved positive to some extent, in most aspects in terms of the awareness and willingness to adopt BYOD based on the technological capabilities of smart mobile devices, the standard of preparedness from the organisation in terms of policies development, availability of IT infrastructure and expertise proved to be low. However, this does not discredit universities as not being ready when m-learning already exists because it could be used as a stepping stone towards the adoption of BYOD.
Conclusion
This study was to assess the readiness of South African universities to adopt BYOD for education. The study identifies technological and organisational readiness factors as the major influencers for BYOD adoption. Once all the relevant sub-factors of technological and organisational readiness have been identified and assessed and are all in sync with the objectives of the BYOD in education, that institution is ready to adopt BYOD. Based on the outcome of the findings, it is clear that there is partial readiness in South African universities to adopt BYOD, as notable barriers such as lack of comprehensive policies for mobile device use, lack of supporting infrastructure and unclear strategies and support from top management still linger. It is imperative therefore that those universities consider these factors in order to be ready to adopt and implement the best BYOD successfully.
Acknowledgements
Competing interests
The authors declare that they have no financial or personal relationships that may have inappropriately influenced them in writing this article.
Authors' contributions
N.R. managed the whole authoring process of this article and was the supervisor of the entire study, while M.M. was the researcher of the study and was involved mainly in collecting the data and early writing of the article.
References
Afreen, R., 2014, 'Bring your own device (BYOD) in higher education: Opportunities and challenges', International Journal of Emerging Trends & Technology in Computer Science 3(1), 233-236. [ Links ]
Akin-Adetoro, A. & Kabanda, S., 2015, 'Contextualizing BYOD in SMEs in developing countries', in Proceedings of the 2015 Annual Research Conference of the South African Institute of Computer Scientists and Information Technologists, Stellenbosch, South Africa, September 28-30.
Attewell, J., 2005, Bring your own device: A guide for school leaders, viewed 19 February 2015, from http://fel.eun.org/icwg
Botha, A., Herselman, M. & van Greunen, D., 2010, 'Mobile user experience in an m-learning environment', Proceedings of the 2010 Annual Research Conference of the South African Institute of Computer Scientists and Information Technologists on - SAICSIT' 10, 29-38. https://doi.org/10.1145/1899503.1899507
Braun, V. & Clarke, V., 2006, 'Using thematic analysis in psychology', Qualitative Research in Psychology 3, 77-101. https://doi.org/10.1191/1478088706qp063oa [ Links ]
Campo, S. 2013. Device Neutral Assignments: DNA for BYOD, viewed 08 Oct 2014, from https://www.smore.com/r0um-device-neutral-assignments?ref=lboard
Cisco, 2012, College lowers desktop costs in computer labs by 30 percent with virtual desktops, viewed 15 March 2014, from: https://www.cisco.com/c/en/us/products/collateral/unified-communications/unified-communications-manager-callmanager/case_study_c36-717074.html
Collins, J. & Hussey, R., 2003, Business research: A practical guide for undergraduate and postgraduate students, 2nd edn., Palgrave Macmillan, London.
Dedeche, A., Lajami, S., Le, M. & Liu, F., 2013, Emergent BYOD security challenges and mitigation strategy, The University of Melbourne, Australia, pp. 1-17.
Dixon, B. & Tierney, S., 2012, Bring your own device to school, viewed 06 March 2017, from http://www.microsoft.com/education
Emery, S., 2012, Factors for consideration when developing a bring your own device (BYOD) strategy in higher education, University of Oregon, Eugene, OR.
Finlay, L., 2009, 'Debating phenomenological methods', Phenomenology & Practice 3(1), 6-25. [ Links ]
Ford, M. & Botha, A., 2010, A pragmatic framework for integrating ICT into education in South Africa. IST -Africa, IEEE, Durban.
Ghosh, A., Gajar, P.K. & Rai, S., 2013, 'Bring your own device (BYOD): Security risks and mitigating strategies', Journal of Global Research in Computer Science 4(4), 62-70. [ Links ]
Goedhuys, M., Janz, N. & Mohnen, P., 2013, 'Knowledge-based productivity in "Low-Tech" industries: Evidence from firms in developing countries', Industrial and Corporate Change 23, 1-23. https://doi.org/10.1093/icc/dtt006 [ Links ]
Hockly, N., 2012, 'Technology for the language teacher: Mobile learning', EFL Journals 67(1), 80-84. [ Links ]
IDC, 2017, Economic trends: Key trends in the South African Economic, viewed 28 April 2017, from https://www.idc.co.za/images/2017/IDC_RI_publication_Key-trends-in-SA-economy_31-March-2017.pdf
Intel Education, 2014, BYOD planning and implementation framework, viewed 28 March 2017, from http://www.kI2blueprint.com/sites/defaultifiles/BYOD-Planning-Implementation.pdf
Johnson, L., Adams Becker, S., Cummins, M., Estrada, V., Freeman, A. & Hall, C., 2016, NMC horizon report: 2016 higher education edition, The New Media Consortium, Austin, TX.
Kong, S.C. & Song, Y., 2015, 'An experience of personalized learning hub initiative embedding BYOD for reflective engagement in higher education', Computers & Education 88, 227-240. https://doi.org/10.1016/j.compedu.2015.06.003 [ Links ]
Korpershoek, H., Hams, T., de Boer, H., van Kuijk, M. & Doolaard, S., 2014, Effective classroom management strategies and classroom management programs for educational practice: A meta-analysis of the effects of classroom management strategies and classroom management programs on student's academic, behavioral, emotional, and motivational outcomes, RUG/GION, Groningen
Kraut, R. (ed.), 2013, UNESCO Policy guidelines for mobile learning, UNESCO, Paris, France, viewed 02 June 2017, from http://unesdoc.unesco.org/images/0021/002196/219641e.pdf
Leedy, P.D. & Ormord, J.E., 2001, Practical research: Planning and design, 7th edn., Prentice Hall, Upper Saddle River, NJ.
Leidner, D.E. & Jarvenpaa, S.L., 1995, 'The use of information technology to enhance management school education: A theoretical view', MIS Quarterly 19(3), 265-291. https://doi.org/10.2307/249596 [ Links ]
Malterud, K., 2012, 'Systematic text condensation: A strategy for qualitative analysis', Scandinavian Journal of Public Health 40, 795-805. https://doi.org/10.1177/1403494812465030 [ Links ]
Mansfield-Devine, S., 2012, 'Interview: BYOD and the enterprise network', Computer Fraud & Security 4, 14-17. https://doi.org/10.1016/S1361-3723(12)70031-3 [ Links ]
Markell, B. & Bernik, L., 2012, 'Mobile devices and corporate data security', International Journal of Education and Information Technologies 6(1), 97-104, viewed 15 May 2017, from http://www.naun.org/journals/educationinformation/17-591.pdf [ Links ]
Norris, C. & Soloway, E., 2011, 'Tips for BYOD k12 programs', District Administration 47(7), 77. [ Links ]
Now Secure, 2016, Mobile security report, viewed 20 February 2017, from http://www.nowsecure.com
Owston, R.D., 1997, 'Research news and comment: The world wide web: A technology to enhance teaching and learning?', Educational Researcher 26(2), 27-33. https://doi.org/10.3102/0013189X026002027 [ Links ]
Papert, S.A., 1973, Uses of technology to enhance education, Artificial Intelligence, Condon Lecture Publications, Eugene, OR.
Pegrum, M., 2009, From blogs to bombs: The future of digital technologies in education, UWA, Crawley, WA.
Rodgers, E.M., 2003, Diffusion of innovation, 5th edn., The Free Press, New York.
Shezi, L., 2016, SA's 26.8 million internet users spend almost three hours a day on social media, viewed 18 May 2017, from https://www.htxt.co.za/2016/04/29/the-stuff-south-africa-26-8-mil-internet-users-spend-most-their-time-doing-online/
Sliep, R.M., 2014, The impact of "bring your own device" and "information technology service delivery" on higher education institutions, viewed 05 June 2017, from http://hdl.handle..net/10210/11271
Stavert, B., 2013, BYOD in schools literature review 2013, viewed 12 March 2017, from http://www.dec.nsw.gov.au
Sweeney, J., 2012, BYOD in education: A report for Australia and New Zealand-Nine conversations for successful BYOD decision making, viewed 15 August 2015, from http://1to1sustainmentdeecd.global2.vic.edu.au/files/2013/07/BYOD_DELL-2dtch9k.pdf
Tekin, R.B., 2012, 'Economic growth, exports and foreign direct investment in least developed countries: A panel Granger causality analysis', Economic Modelling 29(3), 868-878. https://doi.org/10.1016/j.econmod.2011.10.013 [ Links ]
Tornatzky, L.G. & Fleischer, M., 1990, The processes of technological innovation, Lexington Books, Lexington, MA.
Wittman, A., 2011, 'BYOD? First get serious about data security', Information Week 1316, 46, viewed 25 March 2016, from http://global.factiva.com/aa/?ref=IWK0000020111114e7be0000a&pp=1&fcpil=en&napc=S&sa_from [ Links ]
 Correspondence:
Correspondence:
Nkqubela Ruxwana
nkqubz@yahoo.co.uk
Received: 03 Nov. 2017
Accepted: 19 Mar. 2018
Published: 26 June 2018














